What is Zero Trust Application Access (ZTAA)?
Zero Trust Application Access, or ZTAA for short, is a security approach where zero trust is the default. Basically, it means not automatically trusting anyone or anything when it comes to access to apps and data, whether they’re inside or outside the corporate network. Every user, device, application, you name it – they all get treated as potential threats that need verification before getting application access. It’s a strict “never trust, always verify” model applied at the app level.
With ZTAA, organizations secure their essential apps by granting least privilege access and continuously validating every request to connect, regardless of what network or location it’s coming from. The idea is to reduce risk by containing threats and minimizing attack surfaces. ZTAA aligns security with today’s mobile workforce reality instead of relying on those outdated “trust internal networks” strategies.
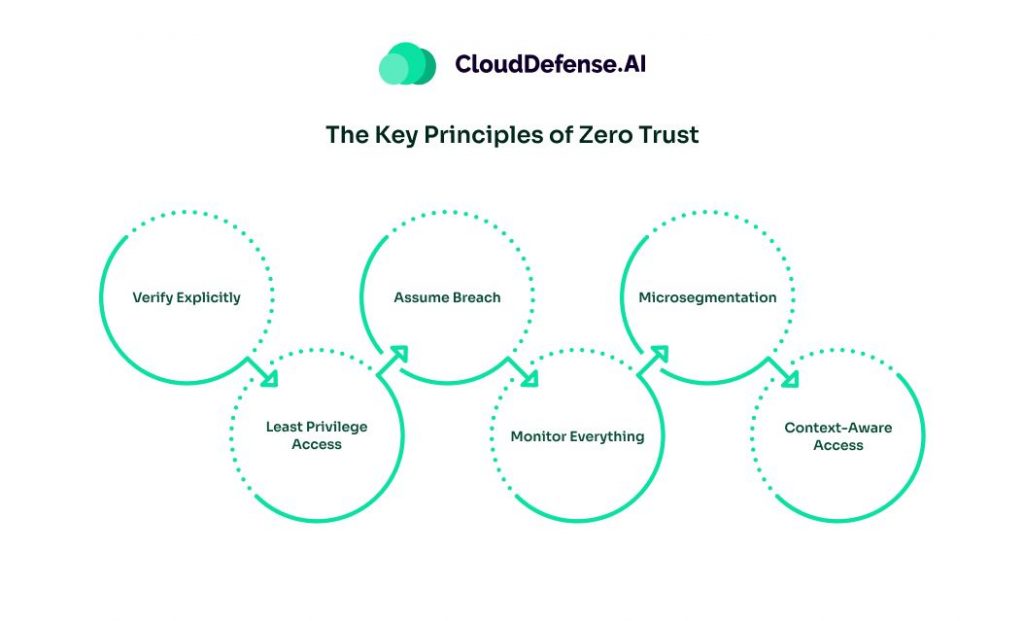
The Key Principles of Zero Trust
Zero Trust is all about taking a hardline “never trust, always verify” approach when it comes to allowing any user, device, or application to access your company’s systems and data. The basic philosophy is that you can’t just blindly trust something or someone based on whether they’re inside or outside your network perimeter.
Nope, with Zero Trust, you treat everyone and everything as potentially untrustworthy by default until they earn access through verification. It operates on some key principles:
Verify Explicitly
Rather than just waving people through based on assumptions, Zero Trust makes you verify the identity and context of every single access request against defined security policies before granting permissions. It’s all about continuous validation at all times.
Least Privilege Access
This one’s pretty straightforward – no more giving people excessive access than what they actually need to do their jobs. Zero Trust is about providing users with just the bare minimum “keys” required for their specific roles and duties. That “need-to-know” approach limits potential damage if credentials get compromised.
Assume Breach
This mindset means your security game plan is designed around the assumption that bad actors have already breached your outer defenses. So instead of just focusing on perimeter security, Zero Trust aims to contain threats and minimize lateral movement through strict access controls and segmentation.
Monitor Everything
To truly enforce Zero Trust, you need full visibility into all the activity happening across your apps, data, and networks. Continuous monitoring and detailed logging/analytics are crucial for effectively spotting threats.
Microsegmentation
This Zero Trust principle involves dividing up your system environments into small, tightly controlled segments to separate workloads and restrict escalated access. It creates secure zones to prevent threats from easily moving laterally.
Context-Aware Access
Not all access requests are created equal. Zero Trust considers the full context – user identity, location, device posture, resource requested, etc. – before allowing or denying access based on dynamic risk scoring and policies.
The idea is to create a robust, risk-based access approach that secures today’s distributed environments without killing users’ productivity. It flips the old “trust but verify” model on its head for a more resilient security posture aligned with the mobile/hybrid cloud era.
So, in essence, Zero Trust takes away all those excessive trust assumptions that cybercriminals just love to exploit, and makes you earn access through continuous verification instead. It’s a refreshing security revamp, even if it does require a bit of an organizational mindset shift!
How Does Zero Trust Application Access (ZTAA) Work?
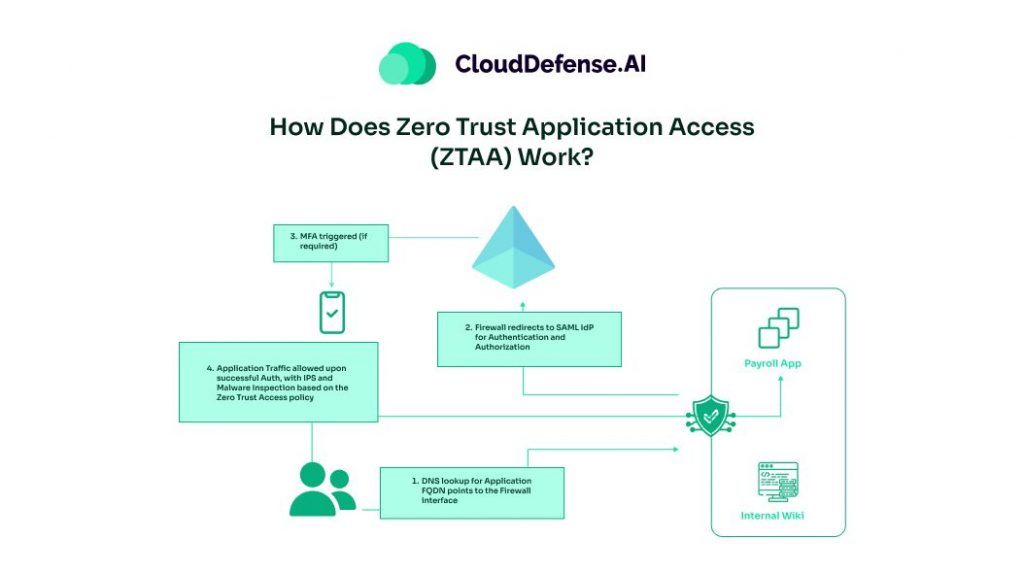
ZTAA operates by adhering to the core zero-trust principle – never implicitly trust any user, device, or network, even if they are internal to the organization. All-access requests go through rigorous verification on a case-by-case basis via the ZTAA access broker. Access controls follow the least privilege model, only granting an account or entity the bare minimum application permissions required for its role.
The process works like this: When a user or device attempts to access an application, their request gets routed through the ZTAA broker. The broker evaluates the request against defined policies and security posture checks before deciding whether to approve or deny access. Factors like user identity, device posture, location, etc. are continuously inspected and risk-scored.
Only if all requirements are met is the strictly scoped application access granted for that session. This ensures secure, controlled access to apps from any location or device without implicit trust. The limited, continuously verified access helps contain breaches and reduces the attack surface. ZTAA effectively implements zero trust at the application layer for consistent, risk-based enforcement aligned with modern workforce models.
ZTAA vs ZTNA: Key Differences
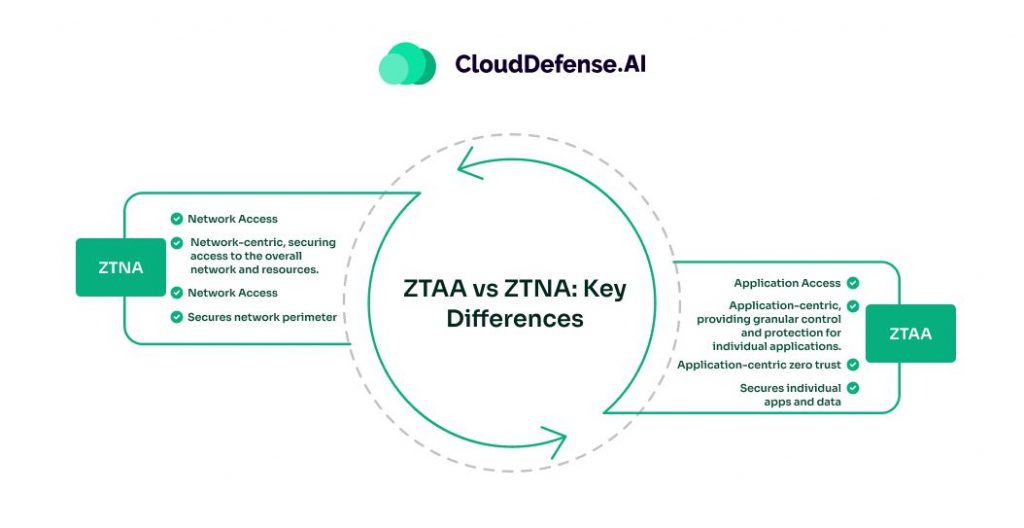
Zero Trust Network Access (ZTNA) and Zero Trust Application Access (ZTAA) are two related but distinct concepts, both falling under the broader zero trust security model. While they share the “never trust, always verify” philosophy, they differ in their areas of focus.
ZTNA, as the name suggests, is all about securing access to the network itself. It’s like having a really strict security guard at the entrance who only lets people in based on their credentials and the absolute minimum access they require – nothing more, nothing less. Traditional remote access solutions like VPNs used to just wave people in with a general pass, leaving the whole place open to potential troublemakers.
ZTAA, on the other hand, takes that zero trust mindset a step further by applying those tight access controls directly to individual applications. Even if you make it past the security guard and into the house (the network), you still need proper verification to enter each VIP room (the apps) based on your specific privileges.
Think of it this way: ZTNA guards the front door, while ZTAA secures all the rooms inside. A comprehensive zero trust remote access solution incorporates both network-level and application-level safeguards for maximum security.
Here’s a quick table summarizing the key differences:
| Feature | ZTNA | ZTAA |
| Focus | Network Access | Application Access |
| Function | Network-centric, securing access to the overall network and resources. | Application-centric, providing granular control and protection for individual applications. |
| Approach | Network-centric zero trust | Application-centric zero trust |
| Scope | Secures network perimeter | Secures individual apps and data |
Complementary Solutions:
While ZTNA and ZTAA have distinct functions, they are not mutually exclusive. A true Zero Trust remote access solution often integrates both ZTNA and ZTAA as part of a comprehensive Zero Trust Access (ZTA) framework. ZTA offers a layered approach, securing both the network perimeter (ZTNA) and individual applications (ZTAA).
The Advantages of Zero Trust Application Access (ZTAA)
ZTAA brings a much-needed security revamp that aligns with how we work and access apps today. Implementing solid zero-trust principles at the application layer, provides some serious advantages over traditional access models:
Tighter Security
With ZTAA, there’s no more relying on the myth of a trusted network interior. Every user, device, and application access attempt is scrutinized and verified before allowing connections. This massively reduces the attack surface and limits breach impact if credentials get compromised.
Improved Visibility
ZTAA solutions give you comprehensive visibility into all application access activity across your environment from a central control plane. It’s like having a security camera watching every door instead of just guarding the main entrance.
Granular Access Controls:
Rather than granting broad, excessive permissions, ZTAA strictly enforces least-privilege access by allowing only the minimum app capabilities required for each user’s role. This principle of least privilege is a core tenet of zero trust.
Consistent Policies
With ZTAA, you can define and consistently enforce granular access policies across all your applications and resources, regardless of where they reside – cloud, on-prem, containerized, you name it. No more security silos.
Scalable for Modern IT
ZTAA is built for today’s mobile, hybrid cloud reality. It secures app access seamlessly across distributed users, devices, and hybrid/multi-cloud environments without restricting productivity.
Reduced Complexity
By collapsing secure app access into a unified, identity-centric approach, ZTAA can potentially reduce the number of tools and complexity involved compared to traditional application security stacks.
Final Words
As modern application development evolves, so too must our approach to security. Zero Trust Application Access offers a powerful response to the ever-growing threats. Overall, with ZTAA’s rigorous verification process, organizations gain a significant edge, minimizing attack surfaces and protecting sensitive data. While ZTAA requires a shift in mindset, the benefits are undeniable. In today’s world, “never trust, always verify” isn’t just a motto; it’s a necessity. ZTAA provides the tools to make it a reality.







