What is a White Hat Hacker?
A white hat hacker, also known as an ethical hacker, is a professional who uses their hacking skills to identify and address security vulnerabilities in hardware, software, or networks. Unlike malicious hackers, white hat hackers operate within the boundaries of the law and adhere to ethical guidelines. Their goal is to enhance security by discovering and fixing weaknesses before they can be exploited by cybercriminals.
In white hat hacking, hackers may have diverse backgrounds, including some who were once black hat hackers but have since turned to ethical practices. The distinction between hackers of white hat hacking and black hat hacking is reminiscent of old Western films, where heroes wore white hats and villains wore black hats.
Ethical hackers only search for vulnerabilities with proper authorization. They conduct their research on open-source software, their own systems, or systems they have been granted permission to examine. Many also participate in bug bounty programs, where companies reward individuals for identifying and reporting security flaws. This proactive approach helps improve cybersecurity and protect sensitive information from potential threats.
Difference between White, Black, and Gray Hat Hackers
Other than white hat hackers, there are two different types of hackers that operate. Black hat hackers exploit security vulnerabilities for personal gain, often selling exploits to the highest bidder and causing harm without regard for legality.
They operate with malicious intent, seeking financial gain or disruption. Gray hat hackers, on the other hand, fall between the two extremes. While they may access systems without permission, their goal is typically to fix vulnerabilities rather than exploit them for profit.
Although they operate without authorization, gray hat hackers usually have good intentions and aim to improve overall security.
| Factor | White Hat Hacker | Black Hat Hacker | Gray Hat Hacker |
| Motive | Improve security | Personal gain | Highlight security flaws (good intentions) |
| Method | Identifies and fixes vulnerabilities | Exploits vulnerabilities | May access system without permission |
| Authorization | Operates legally and with permission | Operates without authorization | Operates without formal authorization |
| Ethical Stance | Follows legal and ethical guidelines | Ignores legality and ethics | Ethical stance varies, often in a legal gray area |
Benefits of White Hat Hacking

White hat hacking, also known as ethical hacking, brings a multitude of benefits to organizations, individuals, and society at large. These benefits underscore the importance of proactive and ethical approaches to cybersecurity.
1. Enhanced Security
In white hat hacking, hackers play a crucial role in identifying vulnerabilities and weaknesses in an organization’s digital infrastructure. By uncovering these flaws, they help organizations strengthen their security measures, ensuring that sensitive data and systems are protected from malicious cyber threats.
2. Proactive Defense
Ethical hacking allows organizations to adopt a proactive stance in their cybersecurity efforts. By identifying and addressing potential risks before they are exploited by cybercriminals, organizations can prevent security breaches and mitigate potential damage. This forward-thinking approach is essential in today’s rapidly evolving threat landscape.
3. Regulatory Compliance
Many industries are governed by stringent cybersecurity regulations. Regular security assessments conducted by white hat hackers help organizations comply with these regulatory requirements. This not only prevents legal penalties and fines but also ensures that the organization adheres to industry best practices.
4. Enhanced Trust and Reputation
Organizations that prioritize cybersecurity and engage with white hat hackers to maintain strong security measures earn the trust of customers, partners, and stakeholders. This trust translates into a stronger reputation and can lead to increased business opportunities and customer loyalty.
5. Cost Efficiency
Early identification and remediation of security vulnerabilities can lead to significant cost savings. Data breaches can be extremely costly, involving legal fees, regulatory fines, remediation expenses, and loss of business due to reputational damage. By addressing security issues proactively, organizations can avoid these substantial costs.
6. Knowledge Sharing
In white hat hacking, The findings of white hat hackers are often shared within the cybersecurity community. This collaborative approach enhances security practices and raises awareness across various industries. The shared knowledge contributes to a collective improvement in cybersecurity standards and defenses.
7. Education and Training
In white hat hacking, hackers also play a vital role in educating and training employees on security best practices. By fostering a culture of cybersecurity awareness, they ensure that all members of an organization understand their responsibilities in maintaining a secure environment. This education is crucial for preventing human error, which is often a significant factor in security breaches.
White Hat Hacking Tools and Techniques
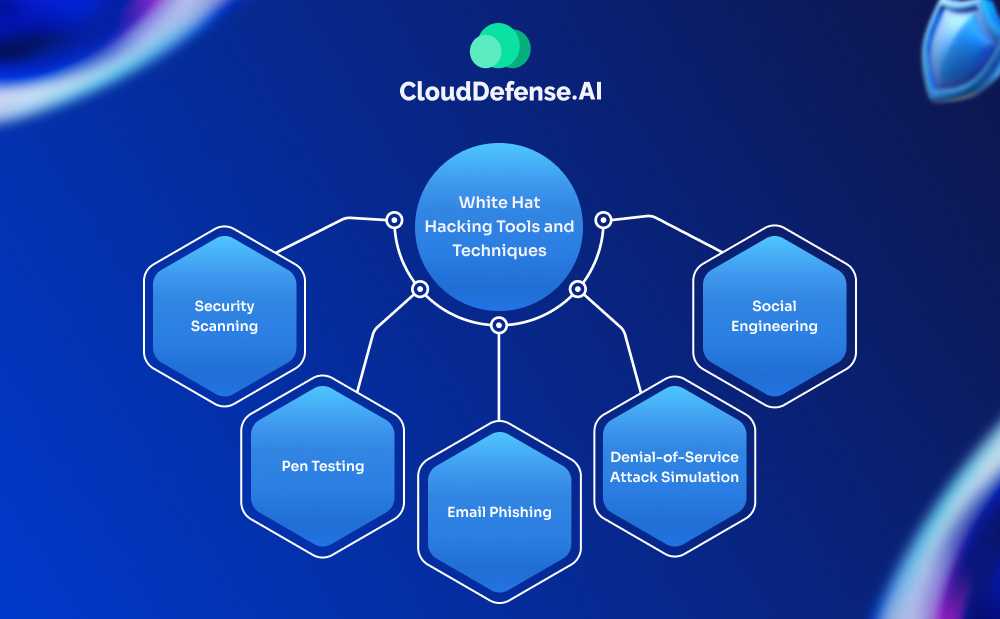
In white hat hacking, hackers employ a range of tools and techniques to assess and enhance the security of an organization’s systems. By using methods similar to those of black hat hackers, but with the intent to improve security, white hat hackers provide invaluable insights into potential vulnerabilities and threats. Here are some common tools and techniques used in ethical hacking:
1. Security Scanning
Ethical hackers utilize various automated tools to identify known vulnerabilities within systems. Tools like the Metasploit Framework and Nikto are open-source options that help in pen testing and scanning for web application vulnerabilities. Additionally, commercial tools such as Acunetix and Netsparker are employed to detect and address vulnerabilities in web applications.
2. Pen Testing
Penetration testing involves ethical hackers using their skills to pinpoint potential entry points and system weaknesses. They then attempt to infiltrate the organization’s network or systems to demonstrate how an attacker could exploit these vulnerabilities. This method helps organizations understand and bolster their defenses against real-world attacks.
3. Email Phishing
In white hat hacking, hackers conduct controlled anti-phishing campaigns to uncover and rectify vulnerabilities within an organization’s email system. By simulating phishing attacks, they can identify weaknesses in how employees handle suspicious emails. This proactive approach helps prevent actual phishing attacks, which aim to trick recipients into divulging sensitive information or clicking on malicious links.
4. Denial-of-Service Attack Simulation
Ethical hackers can simulate DoS attacks to test an organization’s response and readiness. These attacks temporarily disrupt or degrade the performance of systems, making them unavailable to users. By experiencing a simulated DoS attack, organizations can develop and refine their response plans to minimize the impact of actual attacks.
5. Social Engineering
In white hat hacking, hackers hackers employ social engineering techniques to evaluate the security awareness of an organization’s personnel. These techniques exploit human nature and trust, attempting to deceive employees into breaching security protocols or revealing confidential information. By understanding how employees might respond to such attacks, organizations can improve training and awareness programs.
How to Become a White Hat Hacker?
Becoming a white hat hacker involves a blend of formal education, practical skills, certifications, and ethical commitment. A strong starting point is obtaining undergraduate or graduate degrees in computer science, information security, or mathematics, as these fields provide a strong understanding of technical concepts essential for cybersecurity.
Beyond formal education, hands-on practice is crucial; aspiring white hat hackers should set up personal lab environments and use platforms like Hack The Box or TryHackMe to hone their skills. Staying updated with the latest cybersecurity news and engaging in industry discussions helps maintain awareness of emerging threats and techniques.
Certifications significantly enhance credibility and expertise; obtaining credentials like the Certified Ethical Hacker (CEH) from EC-Council, recognized by the U.S. Department of Defense, or various Global Information Assurance Certification (GIAC) certifications, such as GIAC Penetration Tester or GIAC Exploit Researcher and Advanced Penetration Tester, is highly beneficial.
Final Words
White hat hacking stands out as a crucial element in the ongoing battle against cyber threats. These ethical hackers use their skills to protect and enhance security measures, ensuring that our digital spaces remain safe. It’s a field that requires a blend of technical expertise, continuous learning, and a strong ethical backbone.
For those intrigued by the world of cybersecurity, white hat hacking offers an exciting and rewarding path. So, whether you’re an individual with a passion for problem-solving or an organization keen on strengthening its defenses, white hat hackers are the guardians you can rely on.







