What is Web Security?
Web security protects networks, servers, computer systems, and websites from damage, theft, and disruption. It involves measures to defend against internet-based cyberattacks like malware and phishing, using technologies such as firewall inspection, intrusion prevention systems, sandboxing, and URL filtering.
Web security, which includes cloud security and web application security, is not just a shield but a lifeline for businesses. It protects cloud services and web-based applications and extends to protect VPNs. By preventing breaches and data loss, it ensures the uninterrupted operation of businesses.
How does Web Security Work?
Web security operates between an environment’s endpoints and the internet, inspecting traffic and requests in both directions. Utilizing a stack of technologies or a cloud-delivered platform, it provides coverage to prevent policy violations, malware infections, data loss, and credential theft.
Key components include:
- Secure web gateways for threat protection and policy enforcement
- Firewalls/IPS for network security and visibility
- URL filtering for content screening
- Sandboxing for isolating and scanning software
- Browser isolation to prevent data downloads
- DNS controls for monitoring DNS traffic
- Antivirus for detecting and neutralizing threats
- TLS/SSL decryption is used to inspect encrypted traffic.
Together, these technologies create a strong defense against various cyber threats.
Web Security vs. Web Application Security
Often confused with each other, web security and web application security are two different concepts in cybersecurity. Web security involves a broad range of practices and tools designed to protect servers, user endpoints, and the traffic between them and the internet from cyber threats.
It focuses on protecting entire networks and systems from attacks like malware, phishing, and data breaches. In contrast, web application security, also known as website security, specifically targets the protection of public-facing websites. It involves securing web applications from vulnerabilities such as SQL injection, XSS, and remote file inclusion.
While web security covers overall network defense, web application security zeroes in on securing individual websites and their functionalities.
Technologies for Web Security
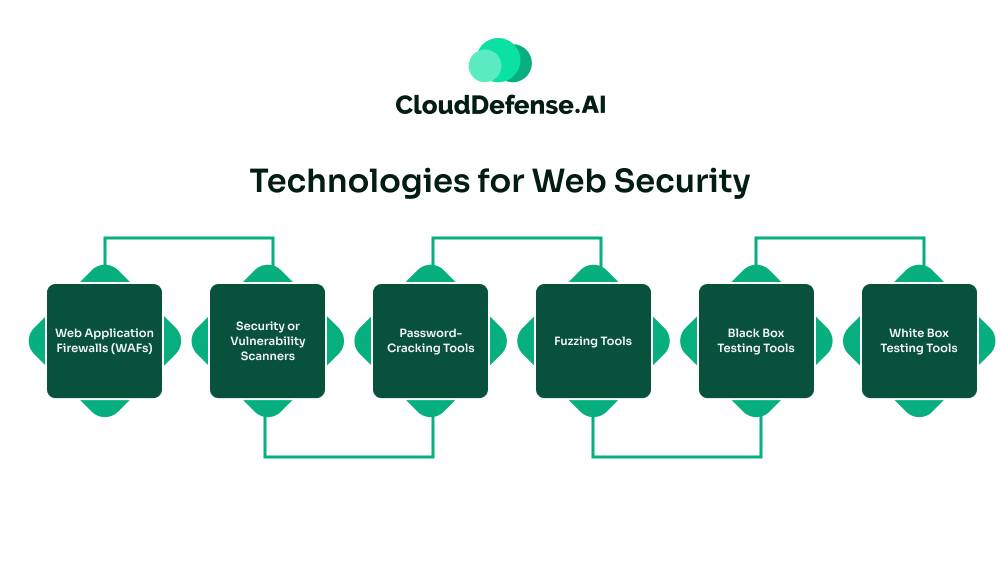
Web security involves a variety of technologies designed to protect web applications, networks, and systems from cyber threats. Key technologies include:
1. Web Application Firewalls (WAFs)
WAFs monitor and filter internet traffic between web applications and the internet, providing protection against threats such as cross-site scripting, SQL injection, and file inclusion. Operating at Layer 7 of the OSI model, WAFs act as secure web gateways but are typically part of a broader suite of security tools.
2. Security or Vulnerability Scanners
These tools automatically scan systems, networks, and applications for security weaknesses. The results help security teams address critical vulnerabilities and reinforce the overall security posture.
3. Password-Cracking Tools
Useful for recovering lost or forgotten passwords, these tools can also help organizations ensure that users follow best practices for password strength and complexity. They can regain control of compromised accounts by resetting passwords.
4. Fuzzing Tools
Fuzzers test software, networks, and operating systems for coding errors that could lead to security vulnerabilities. By identifying and analyzing these errors, developers can address potential security issues during various stages of the software development process.
5. Black Box Testing Tools
These tools test systems without prior knowledge of their internal workings, mimicking the actions of potential attackers. They help evaluate how systems respond to unexpected user actions and can identify performance issues and reliability concerns.
6. White Box Testing Tools
In contrast to black box testing, white box testing involves examining the internal structure, design, and coding of software. These tools help developers identify and rectify coding errors that could introduce security vulnerabilities, ensuring efficient data flow within applications.
Threats to Web Security
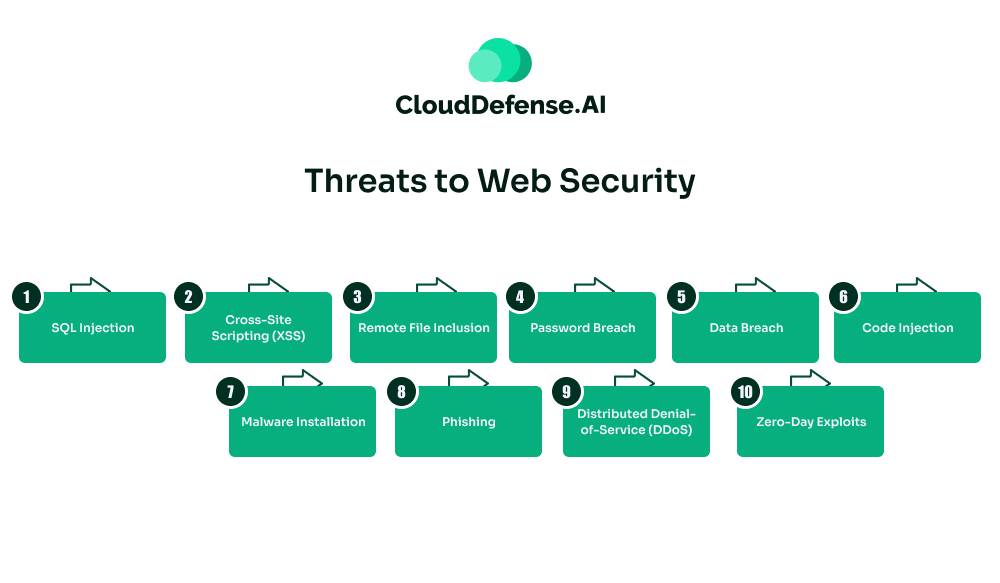
Web security faces numerous threats that can compromise the integrity, confidentiality, and availability of systems and data. Some of the most prevalent threats include:
1. SQL Injection
Attackers exploit vulnerabilities in database query handling to inject malicious SQL statements. This can lead to unauthorized access to sensitive data, alteration or deletion of database contents, and privilege escalation on the database server.
2. Cross-Site Scripting (XSS)
XSS vulnerabilities allow attackers to inject malicious client-side scripts into web pages. These scripts can steal user cookies, hijack sessions, or perform actions on behalf of the user, leading to unauthorized access to critical data.
3. Remote File Inclusion
This occurs when attackers exploit vulnerabilities in web applications to include and execute remote files. By manipulating input paths, attackers can upload and run malware, such as backdoor shells, from external domains.
4. Password Breach
Hackers often gain access to web resources through stolen or weak passwords. Techniques like password spraying, where common passwords are tried repeatedly, and keylogging, where keystrokes are recorded, are commonly used to breach accounts.
5. Data Breach
When sensitive or confidential information is exposed to unauthorized parties, it constitutes a data breach. These breaches can result from hacking, human error, or intentional disclosure, leading to the misuse or sale of the exposed data.
6. Code Injection
Attackers use input validation vulnerabilities to inject and execute malicious code. This code can alter the behavior of software and systems, creating security weaknesses and enabling further attacks.
7. Malware Installation
Once installed on a network, malware can cause significant damage, such as stealing data, encrypting files for ransom, or spreading to other systems. Effective web security must detect and prevent malware installation.
8. Phishing
Phishing attacks involve sending deceptive emails to trick users into revealing personal information or clicking on malicious links. These attacks often serve as the initial step in larger cyber attacks, such as credential theft or malware distribution.
9. Distributed Denial-of-Service (DDoS)
DDoS attacks flood servers or networks with excessive traffic, causing service disruptions. These attacks can severely impact business operations, leading to revenue loss and decreased availability of services.
10. Zero-Day Exploits
Newly discovered vulnerabilities, known as zero-day exploits, are particularly dangerous as they can be exploited before security patches are available. Organizations must stay vigilant and employ advanced detection methods to mitigate these risks.
Importance of Web Security
Web security is essential for protecting an organization’s digital assets and ensuring the smooth operation of its business processes. It involves a combination of tools and strategies that work together to defend against a wide range of cyber threats, such as malware, phishing, credential theft, and advanced persistent threats (APTs). These threats continuously evolve, seeking to exploit vulnerabilities in both on-premises and cloud infrastructures.
The importance of web security lies in its ability to prevent unauthorized access, data breaches, and disruptions caused by cyber attacks. A comprehensive web security strategy includes regular updates and patches to maintain the effectiveness of security tools. Additionally, proactive measures, such as monitoring for APTs and configuring cloud resources correctly, are crucial for identifying and containing threats before they can spread.
Beyond technical solutions, web security also involves educating users on best practices to avoid common pitfalls, such as falling victim to phishing scams or mishandling sensitive information. By combining strong cybersecurity infrastructure with user awareness and training, organizations can create a multi-layered defense that significantly reduces the risk of cyber incidents.
Web Security Challenges
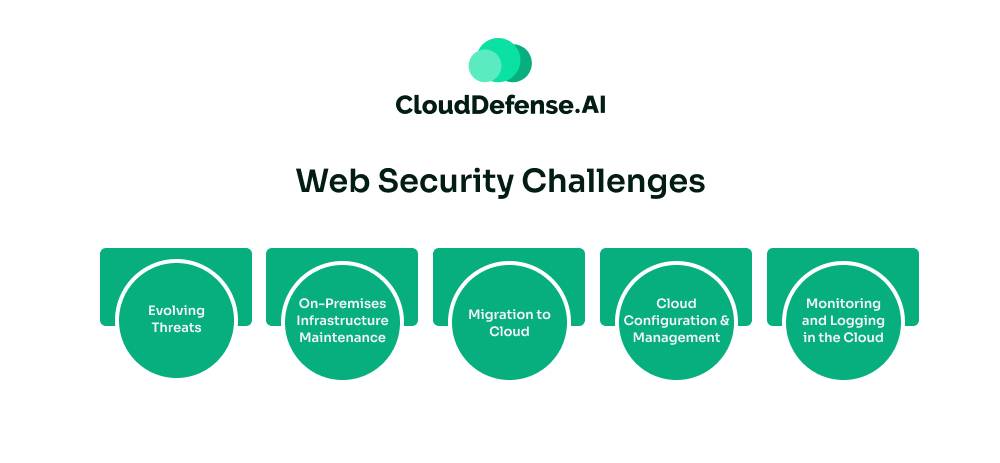
Web security faces several evolving challenges that administrators must address to protect their enterprises from cyber threats effectively. Despite advanced cybersecurity strategies, the dynamic nature of these threats means that risks can never be entirely eliminated. Here are the primary challenges of web security:
1. Evolving Threats
Cyber threats constantly adapt to bypass new cybersecurity measures. This includes sophisticated malware, phishing schemes, and zero-day exploits that exploit unpatched vulnerabilities. Keeping up with these evolving threats requires continuous vigilance and updating of security protocols.
2. On-Premises Infrastructure Maintenance
Traditionally, enterprises have relied on on-premises infrastructure for cybersecurity, which involves protecting against malicious websites, credential theft, social engineering, insider threats, website vulnerabilities, phishing emails, and malware. However, maintaining this infrastructure demands constant monitoring, patching, and updating, which can be resource-intensive.
3. Migration to Cloud
As organizations move their infrastructure to the cloud to reduce overhead, they encounter new challenges. While cloud services offer scalability and flexibility, they also introduce vulnerabilities, especially if administrators lack experience in managing cloud resources. Misconfigurations in cloud settings are a primary factor in these new vulnerabilities, often leading to data breaches and security incidents.
4. Cloud Configuration and Management
Proper configuration and management of cloud resources are crucial to preventing security lapses. Administrators must ensure that cloud environments are correctly set up and that security measures such as encryption, access controls, and network security groups are properly implemented.
5. Monitoring and Logging in the Cloud
Effective monitoring and logging are essential for detecting and responding to security incidents in real-time. Administrators need to configure these tools correctly to stay compliant with regulatory requirements and to have visibility into potential attacks. Failure to do so can result in undetected breaches and data loss.
Final Words
Web security is a vital shield protecting your Internet presence from relentless cyber threats. You can see by now how effective security measures can be the difference between smooth operations and catastrophic breaches.
Embracing web security is not just a technical necessity but a crucial step in protecting your business’s future. Stay vigilant, stay updated, and prioritize your web security to ensure your assets remain safe and immune to new threats.







