What is Web Filtering?
Web filtering is a cybersecurity mechanism that controls and restricts access to online content based on predefined policies. It works by analyzing web traffic and blocking or allowing URLs based on factors like domain reputation, content category, or security threats.
What it does:
- DNS Filtering: Blocks access at the domain level before the connection is even made. Think of it as cutting off access before danger strikes.
- URL Filtering: Evaluates specific web addresses and prevents access to blacklisted sites.
- Content Inspection: Scans page content in real-time to detect malware, phishing attempts, or policy violations.
- Category-Based Filtering: Restricts access to specific categories (e.g., adult sites, gambling, or social media).
- Keyword-Based Filtering: Blocks pages containing specific restricted words or phrases.
- AI & Threat Intelligence Filtering: Uses machine learning and real-time threat databases to detect evolving cyber threats.
Why Does This Matter?
Without web filtering, your system is an open door for cyber threats. Consider this:
- Productivity drain? Unrestricted access to non-work-related sites results in lost efficiency.
- Ransomware infections? One clicks on a malicious ad, and you’re compromised.
- Data breaches? Employees accessing phishing sites can expose sensitive data.
- Regulatory fines? Lack of compliance with industry policies can lead to legal consequences.
How Web Filtering Evolved?
Back in the day, controlling internet access was simple—block a few sites, set some firewall rules, and call it a day. But as the web expanded and cyber threats became more sophisticated, those basic methods fell apart. Hackers got smarter, and businesses needed better ways to filter web traffic without breaking workflows.
The Early Days
- IP-Based Blocking – IT teams manually blocked individual IPs. The problem? Attackers could just switch IPs and bypass restrictions.
- Basic Firewalls – These could allow or deny access based on static rules, but they couldn’t see beyond surface-level traffic.
- Manual URL Blacklists – Companies kept lists of banned websites, but these needed constant updates and couldn’t stop emerging threats.
It was reactive security—by the time a threat was recognized and blocked, damage was often already done.
The Shift to Smarter Web Filtering
As cyber threats became more dynamic, security had to keep up. Instead of just blocking known bad sites, modern web filtering evolved to analyze, predict, and prevent threats in real time. Here’s what changed:
- DNS Filtering – Instead of blocking a single site, this stopped access at the domain level, cutting off phishing and malware before they reached users.
- AI-Powered Threat Detection – Instead of relying on static blacklists, machine learning could spot dangerous sites based on behavior patterns.
- Cloud-Based Filtering – With remote work and BYOD (Bring Your Own Device), filtering had to move beyond office networks. Cloud filtering made security flexible and scalable.
Why This Evolution Matters
Think about it—would you trust a security system from 15 years ago to protect your business today? Probably not.
- Static blacklists struggle to keep up with the speed at which new malicious websites appear.
- Basic firewalls lack the intelligence to detect phishing, malicious ads, or zero-day exploits.
- Manual filtering is impossible to scale in today’s cloud-first, remote-work-driven environment.
Web filtering is no longer just about blocking content—it has become a critical component of cybersecurity, productivity, and compliance. Without it, organizations leave themselves exposed to data breaches, ransomware attacks, and regulatory fines.
Different Types of Web Filtering

Web filtering isn’t a one-size-fits-all solution. There are different ways to filter web content, and each method serves a specific purpose. The way a filtering system works depends on what it blocks, how it applies rules, and where it operates. Let’s break it down.
How Web Filters Decide What to Block
1. Allow Listing (Whitelisting)
This is the strictest type of filtering. Only pre-approved websites are accessible, and everything else is blocked by default. It’s commonly used in highly controlled environments like government offices and financial institutions. While it ensures security, it can be inconvenient if employees need access to new websites that aren’t on the list.
2. Block Listing (Blacklisting)
This works in the opposite way. Instead of blocking everything except approved sites, it allows unrestricted access except to websites that are known to be harmful or inappropriate. Businesses often use block lists to prevent employees from accessing phishing sites, malware-infected pages, or time-wasting platforms like social media. The downside? It requires constant updates since new threats emerge all the time.
3. Content and Keyword Filtering
Instead of just looking at the website’s address, this method scans the actual content of a webpage. If it detects certain words, images, or code patterns that match restricted categories (like adult content or malware scripts), it blocks access. This is useful for stopping harmful sites that may not yet be on a blacklist.
Where Web Filters Apply Their Rules
1. DNS Filtering
This method blocks websites at the domain level. It works by intercepting the request before the user even connects to the site. Because it operates at the network level, it’s effective for stopping phishing attempts, malware infections, and unauthorized browsing without slowing down internet performance.
2. URL Filtering
Here, the system checks the full web address of the requested page and compares it against a database of allowed or blocked URLs. URL filtering is useful for controlling specific types of websites, like preventing access to YouTube while still allowing Google searches. However, since URLs change frequently, it requires constant updates to remain effective.
3. Deep Content Inspection
Unlike DNS and URL filtering, which focus on addresses, this method looks at what’s actually inside the webpage. It scans text, scripts, and embedded files to detect malicious elements. This type of filtering is essential for businesses that handle sensitive data, as it helps prevent data leaks and sophisticated cyber threats.
Where Web Filtering Happens
1. Client-Side Filtering (On-Device)
This type of filtering is installed directly on a user’s computer, phone, or tablet. It ensures security even when the device is outside the corporate network. While effective for remote workers, it can sometimes be bypassed if users disable or uninstall the software.
2. Server-Side Filtering (Network-Based)
Instead of being applied to individual devices, this type of filtering works at the network level, either through on-premise hardware or a cloud-based security service. All internet traffic is routed through a filtering system that enforces policies consistently. This is ideal for companies that need centralized control, but it requires careful setup to avoid disrupting legitimate traffic.
What’s the Best Type of Web Filtering?
There’s no single answer. It depends on what you need.
- If security is the top priority, allow listing and DNS filtering provide the strictest control.
- If the goal is productivity, URL filtering and content inspection can help reduce distractions.
- If employees work remotely, client-side filtering or cloud-based solutions offer the best coverage.
Most organizations use a combination of these methods to balance security, efficiency, and ease of use. The key is to find the right mix that protects users without making web access frustrating.
How Web Filtering Works
Web filtering isn’t just about blocking websites—it’s a real-time security measure that analyzes, categorizes, and controls internet traffic to protect users and data. Modern web filtering solutions use a combination of technologies to ensure safe browsing while maintaining business efficiency.
1. Domain Name System (DNS) Filtering
- Blocks access to malicious or unwanted websites at the DNS level before a connection is even established.
- Prevents phishing, malware, and command-and-control (C2) communications without slowing down network performance.
- Works outside the corporate network, securing remote and hybrid work environments.
2. URL and Content Filtering
- URL Filtering: Compares requested web addresses against a database of known harmful or inappropriate sites.
- Content Filtering: Analyzes page content in real-time, detecting suspicious scripts, misleading ads, and hidden malware.
- Category-Based Filtering: Allows organizations to block entire categories (e.g., adult content, gambling, social media) based on policies.
3. Deep Packet Inspection (DPI)
- Goes beyond just URLs—examines actual data packets to detect threats hidden in encrypted traffic.
- Identifies malware downloads, keyloggers, and attempts to exfiltrate sensitive data.
- Essential for businesses handling financial transactions, healthcare data, and intellectual property.
4. Artificial Intelligence (AI) & Machine Learning (ML)
- AI-powered web filtering detects zero-day threats by analyzing web behavior patterns.
- Uses ML models to continuously learn and adapt, identifying new phishing sites and malware-infected domains faster than traditional methods.
- Reduces false positives, ensuring legitimate business sites aren’t mistakenly blocked.
5. Cloud-Based vs. On-Premise Web Filtering
- Cloud-Based Filtering: Scales easily, ideal for remote work, and doesn’t require additional hardware.
- On-Premise Filtering: Offers deeper control for industries with strict compliance needs but requires constant updates and maintenance.
Why Web Filtering is More Than Just Blocking Websites
Think of modern web filtering as a proactive security shield, not just a restriction tool.
- It prevents cyberattacks before they happen, reducing IT workload.
- Ensures compliance with regulations like GDPR, HIPAA, and CCPA.
- Improves productivity by limiting distractions while allowing access to necessary business tools.
Now that we know the technology behind web filtering, we’ll now see how it actually works:
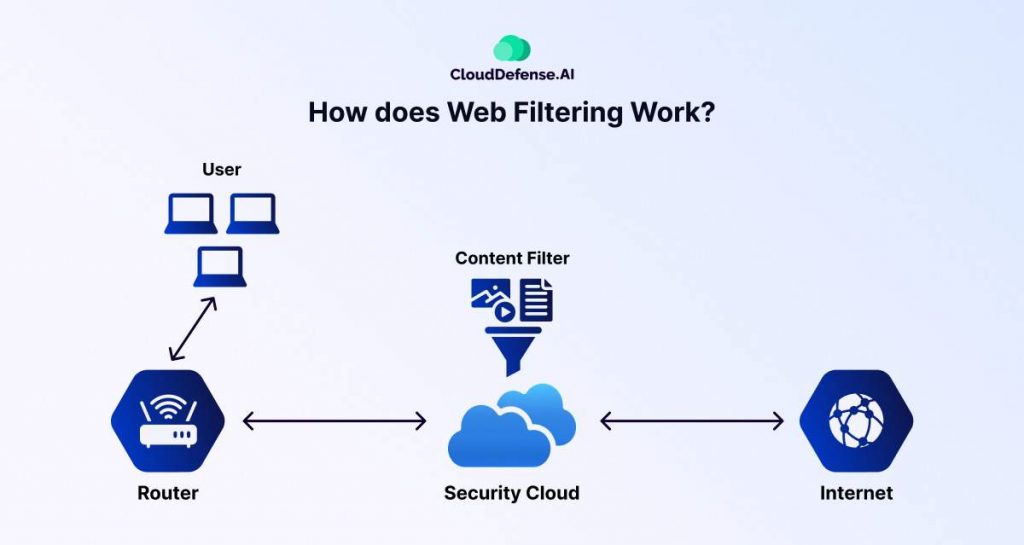
- User Access Request: A user attempts to access a website using a device like a laptop or desktop.
- Traffic Passes Through the Router: The request first goes through the router, which directs it to the internet.
- Security Cloud & Content Filtering
- Instead of directly reaching the internet, the request is routed through a security cloud that applies content filtering policies.
- The security cloud evaluates the request based on predefined rules, such as allow/block lists, website categories, and security threats.
- Filtering Decision
- If the website is safe and permitted, the request is approved, and the user gets access.
- If the website is malicious or restricted, access is blocked, and the user is prevented from visiting it.
- Final Connection to the Internet: Once the request passes security checks, it is sent to the internet, retrieving the website content for the user.
This process ensures that harmful or unproductive websites are blocked before they reach the user’s device, making web browsing safer and more controlled.
Implementing Web Filtering: A Step-by-Step Guide
Setting up web filtering isn’t just about blocking harmful sites—it’s about securing your network, improving productivity, and maintaining compliance. Here’s how to do it effectively:
1. Define Your Filtering Goals
- Do you want to block malicious websites, restrict social media during work hours, or enforce compliance policies?
- Identify the categories of sites to be blocked (e.g., adult content, gambling, phishing sites, malware-hosting domains).
2. Choose the Right Web Filtering Method
- DNS Filtering: Blocks access at the domain level before the request reaches the website.
- URL Filtering: Restricts specific web addresses.
- Content Filtering: Scans webpage content in real-time and blocks inappropriate or dangerous material.
- Application-Level Filtering: Controls access to specific web applications like YouTube or Facebook.
3. Select the Right Solution
- Hardware-Based Filtering: Deploy firewalls with built-in web filtering capabilities.
- Software-Based Filtering: Install security software on endpoints for local filtering.
- Cloud-Based Filtering: Use cloud security solutions to filter traffic remotely without on-premises hardware.
4. Implement Filtering Policies
- Set rules for different user groups (e.g., employees, students, guests).
- Customize policies based on business needs—strict policies for work devices, flexible ones for personal use.
5. Integrate with Security Systems
- Connect web filtering with firewalls, SIEM tools, and endpoint security for a multi-layered defense.
- Enable real-time threat intelligence to automatically block newly discovered malicious sites.
6. Monitor and Fine-Tune
- Regularly review logs and reports to analyze browsing trends and detect anomalies.
- Adjust rules based on evolving threats and organizational needs.
7. Educate Users
- Inform employees or users about web filtering policies and why they exist.
- Train them on safe browsing practices and how to handle blocked website requests.
Bottom Line
A well-implemented web filtering system isn’t just about restrictions—it’s about enhancing security, boosting productivity, and ensuring compliance while keeping users protected. With evolving cyber threats and productivity challenges, having a smart filtering strategy ensures a safer digital environment without unnecessary restrictions.
The key is balance—effective policies, the right tools, and continuous monitoring. When done right, web filtering becomes an invisible yet powerful layer of defense, keeping users safe while enabling seamless online experiences.







