What is WAAP?
WAAP stands for Web Application and API Protection. Pretty self-explanatory, right? So basically, WAAP is a suite of cloud-based security services that secure the web apps and APIs that are the lifeblood of your business operations.
Alright, let’s break it down. Web apps? We’re talking about those programs accessed over the internet through a browser or mobile app interface. APIs? They enable different software components to communicate and share data seamlessly.
Now, why do they need protection? Well, these critical assets are prime targets for cybercriminals looking to exploit vulnerabilities and gain unauthorized access or disrupt operations via injection attacks, cross-site scripting, credential stuffing, you name it.
So, in a nutshell, WAAP is your web app and API’s guard, keeping the bad guys at bay and ensuring your online business runs smoothly and securely.
Why Do Traditional Defenses Leave Your Web Apps Vulnerable?
Traditional Web Application Firewalls (WAFs) have served us well but were built for a different era, focusing mainly on protecting websites and basic web apps. But nowadays, with APIs and complex web applications running the show, those legacy solutions are like bringing a knife to a gunfight.
Traditional WAFs rely heavily on signature-based detection, which means they can only catch known threats. But in today’s threat front, where new attack vectors are popping up left and right, that’s like trying to hit a moving target with a blindfold on.
Not to mention, these outdated systems struggle to keep up with the scale and complexity of modern web apps and APIs. They lack the ability to handle the sheer volume of traffic and the intricate logic behind these applications, leaving critical vulnerabilities wide open.
Let’s not forget about firewalls. Yeah, they’re good at blocking traffic based on ports and protocols, but attackers these days can mimic legit traffic patterns and slip right through those basic filters. It’s like they’ve got an all-access pass.
And API security? Traditional WAFs were never designed with APIs in mind, leaving a massive blind spot that attackers are all too happy to exploit.
Bottom line, relying solely on these legacy solutions is like leaving the front door wide open for cyber criminals. It’s time to level up your security game with a dedicated WAAP solution that’s built for the modern web app and API landscape.
How Does WAAP Works?
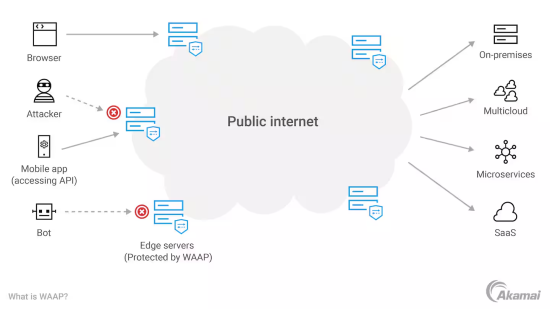
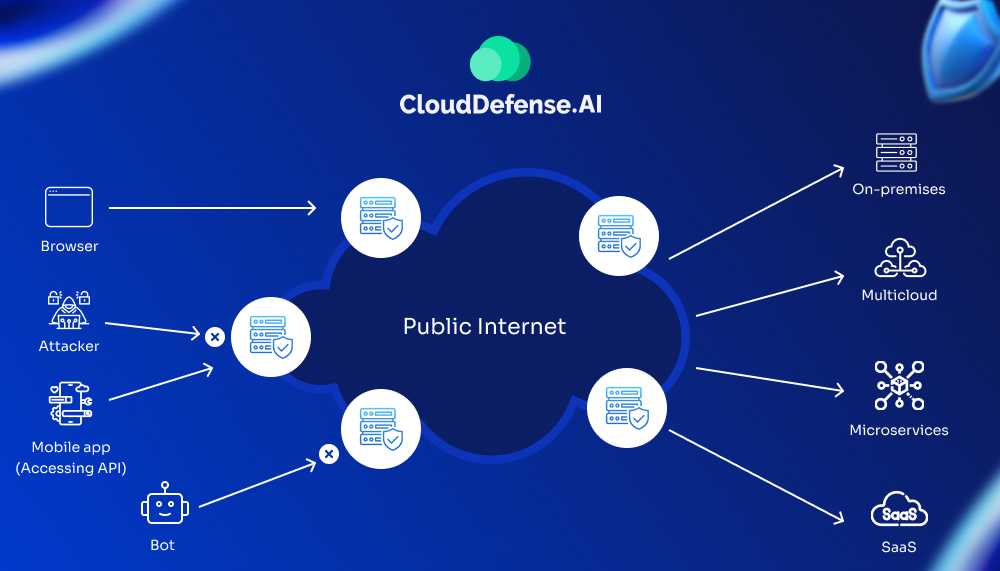
WAAP operates at the edge servers, creating a robust layer of protection for applications hosted across various environments such as on-premises, multicloud, microservices, and SaaS. Here’s how it filters and manages traffic:
- User Access (Browser and Mobile App): Legitimate traffic from users via browsers and mobile apps is allowed to pass through the edge servers, which are protected by WAAP. This traffic reaches the application securely after being inspected for any anomalies or threats.
- Bot and Attack Traffic Detection: WAAP identifies and blocks unwanted traffic, such as malicious bots and attackers attempting to exploit vulnerabilities. This filtering process happens at the edge, where WAAP’s security mechanisms can detect and stop these threats before they reach the application.
- Protection Across Environments: Once traffic is verified, WAAP routes it securely to the appropriate backend environment, whether it’s on-premises, in a multi-cloud setup, within microservices, or in SaaS platforms. This ensures applications are accessible to legitimate users while remaining shielded from cyber threats.
Why is WAAP Security a Must-Have?
We just went over how traditional security solutions are falling behind when it comes to protecting your web apps and APIs. That’s where WAAP steps in as a must-have in your cybersecurity arsenal.
In-Depth Traffic Analysis
Traditional firewalls are stuck in the stone age, filtering traffic based on protocols and ports. But here’s the kicker—attackers are using the same web ports and protocols as your legit users. HTTP(S)? They’re all over it. You need to get granular, and that’s where WAAP shines. It digs deep, separating the wheat from the chaff in your traffic.
360-Degree DDoS Defense
DDoS attacks are a nightmare, hitting your apps and APIs from all angles – application layers, network level, you name it. WAAP’s got your back with round-the-clock protection against every flavor of DDoS, no matter how sophisticated these attacks get.
Encrypted Traffic Inspection
Encryption is a double-edged sword – it protects data privacy, but attackers can hide malicious content within encrypted traffic. Legacy solutions are blind to this, but WAAP solutions can inspect TLS connections, uncovering threats disguised in encrypted traffic.
Minimize Your APIs Attack Surface
APIs are the new prime target for hackers, and traditional solutions might not cut it. WAAP solutions automatically identify and mitigate vulnerabilities, including those outlined in the OWASP Top 10 API threats, keeping your APIs secure and minimizing the attack surface.
Tackling Web App Complexity
Let’s face facts: web apps are intricate, and attackers exploit every nook and cranny to stash their malicious payloads. Your run-of-the-mill IDS/IPS? It’s out of its depth. The security inspection these systems offer is a drop in the bucket. WAAP, on the other hand, goes full CSI on your web traffic.
Core Capabilities of Web Application and API Protection
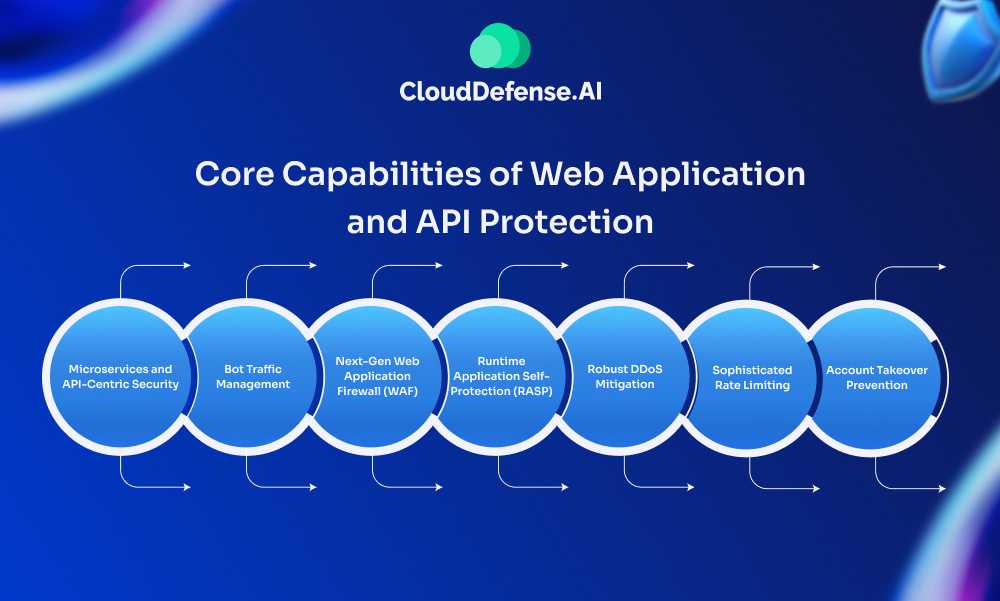
Microservices and API-Centric Security
Security is built into each microservice or API. This creates a secure perimeter around individual components. The WAAP understands the context and data of each service, allowing for precise security controls.
Bot Traffic Management
WAAP systems differentiate between users and bots. They stop malicious bots from scraping content, launching DDoS attacks, or attempting account takeovers. At the same time, they let legitimate bots (like search engine crawlers) access the site.
Next-Gen Web Application Firewall (WAF)
Next-gen WAFs work at the application layer to block a broad range of attacks. They use AI and behavioral analysis to identify and stop threats without relying only on known attack patterns. This means they can catch new, unknown attacks that traditional WAFs might miss.
Runtime Application Self-Protection (RASP)
RASP integrates directly into the app’s runtime environment. It monitors the app’s behavior and can immediately detect and block attacks in real time. This inside-out approach gives RASP context about the app’s operations, leading to more accurate threat detection.
Robust DDoS Mitigation
These solutions defend against application-layer and network-layer DDoS attacks. They can handle high-volume attacks by quickly scaling up resources. This keeps apps, APIs, and microservices running even under heavy assault.
Sophisticated Rate Limiting
WAAP tools track and limit the rate of requests to prevent abuse. They look at factors like IP addresses, user sessions, and API keys to identify and block users or systems making too many requests. This stops performance problems caused by excessive traffic.
Account Takeover Prevention
These systems monitor login attempts across web and mobile apps. They detect when attackers try to use stolen usernames and passwords. By analyzing login patterns and user behavior, they can spot and stop unauthorized access, even when the credentials are valid.
How to Evaluate Cloud WAAP Services?
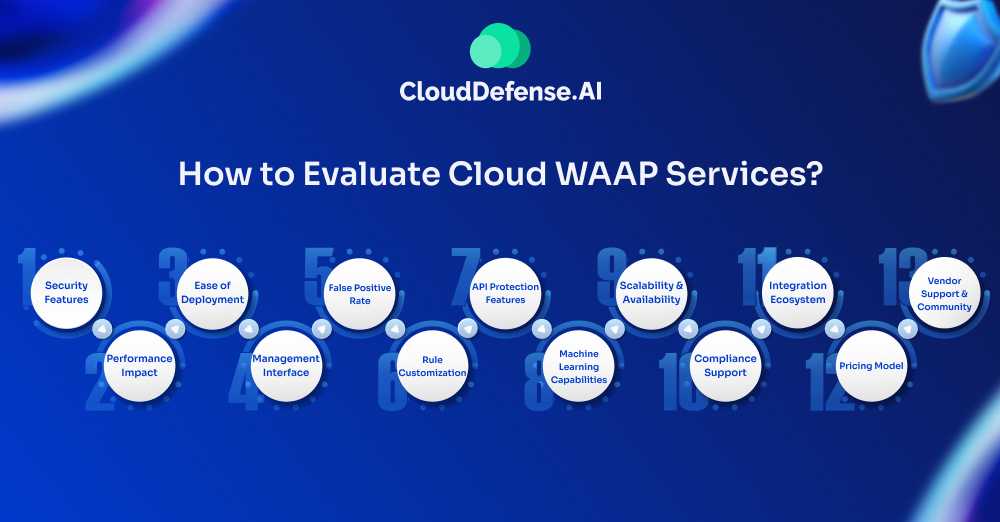
Security Features
This is your top priority. Look for a WAAP solution that offers comprehensive protection against a wide range of threats. Here’s what to consider:
- Threat Coverage: Does the WAAP service protect against common threats like SQL injection, XSS, DDoS attacks, zero-day vulnerabilities, and API security threats?
- Advanced Features: Does it offer additional features like bot management, web application firewalls (WAF), and intrusion detection/prevention systems (IDS/IPS)?
- Data Loss Prevention (DLP): Is data encryption included for sensitive information both at rest and in transit?
Performance Impact
Assess how the WAAP affects your application’s speed and responsiveness. Look for services with minimal latency. Test the WAAP under various load conditions to see how it handles traffic spikes. Check if it offers caching or content delivery network (CDN) features to improve performance.
Ease of Deployment
Evaluate how quickly you can set up and configure the WAAP. Some services offer simple DNS changes or reverse proxy setups. Others might require more complex integrations. Consider whether it supports your current infrastructure and deployment methods (e.g., containers, serverless).
Management Interface
The dashboard should be intuitive and provide clear visibility into threats, blocked attacks, and system health. Look for customizable reports and real-time alerts. Check if it offers role-based access control for your team.
False Positive Rate
A low false positive rate is crucial. Too many false alarms lead to alert fatigue and can disrupt legitimate traffic. During your evaluation, monitor how accurately the WAAP distinguishes between actual threats and benign anomalies. See if it allows easy tuning to reduce false positives.
Rule Customization
While pre-built rulesets are useful, you need flexibility to create custom rules. Assess how granular the rule creation process is. Can you target specific URLs, parameters, or headers? How easy is it to test and deploy new rules?
API Protection Features
If you have APIs, dig into the WAAP’s API-specific capabilities. It should support OAuth, API keys, and JWT for authentication. Check if it can automatically discover and map your APIs, detect schema changes, and protect against API-specific threats like excessive data exposure or broken object-level authorization.
Machine Learning Capabilities
Evaluate how the service uses ML to adapt to your application’s traffic patterns. It should learn what’s normal for your apps and flag deviations. This helps catch zero-day attacks and reduce manual tuning.
Scalability and Availability
The WAAP must scale with your traffic without manual intervention. Look at its global presence and how it handles traffic distribution. High availability is non-negotiable; check uptime guarantees and redundancy measures. Here’s what to consider for future growth:
- Scalability: Can the WAAP service accommodate an increase in traffic and users as your business grows?
- Deployment Options: Does it offer flexible deployment models (e.g., on-premise, cloud, hybrid) to fit your existing infrastructure?
- Multi-Cloud Support: Does the service integrate seamlessly with different cloud providers if you use a multi-cloud environment.
Compliance Support
If you’re in a regulated industry, the WAAP should help meet compliance requirements (PCI DSS, HIPAA, etc.). It should offer features like data masking, audit logs, and compliance-specific reports.
Integration Ecosystem
Consider how well it integrates with your existing tools. Does it work with your SIEM, ticketing system, or CI/CD pipeline? Native integrations save time and improve your security workflow.
Vendor Support and Community
Assess the quality of documentation, support response times, and the availability of training resources. A strong user community can also be valuable for sharing best practices and troubleshooting.
Pricing Model
Understand the pricing structure. Is it based on bandwidth, number of applications, or features used? Watch out for hidden costs like extra charges for SSL/TLS inspection or bot management. Make sure the pricing aligns with your usage patterns and budget.
Final Words
The stakes in web application security have never been higher. Cyber threats are evolving at an alarming rate, and traditional defenses are crumbling under the onslaught. Without a strong WAAP solution, your organization’s network is a cake walk for sophisticated attackers.
The consequences of a breach can be catastrophic—financial ruin, reputational damage, and legal nightmares. Don’t wait for disaster to strike. Act now. Rigorously evaluate and implement a cloud WAAP service that meets your needs. The clock is ticking, and your adversaries aren’t slowing down. Protect your digital assets before it’s too late. Your business’s survival may depend on it.







