Ever experienced that inner tug-of-war when faced with clicking on a link? Your gut feeling might stop you from being tricked by URL phishing, a sneaky trick used by cybercriminals to steal sensitive information.
URL phishing scams people by making fake links look real, often copying well-known legitimate companies. They do this to trick users into giving away personal info like usernames and passwords, a method that is called credential harvesting. URL phishing can be a malicious leech for your system, that can be destructive for your company’s data.
Keep reading to learn more about URL phishing and also receive insight on how to protect yourself from falling victim to it.
What is URL Phishing?
URL phishing, also known as phishing through emails, is a cybercriminal activity where malicious actors send emails or messages containing links to fake websites. These links appear legitimate but lead to malicious sites designed to steal personal information, like login credentials or financial data. Victims are tricked into entering sensitive details, which are then captured by the attackers for corrupt purposes.
How does URL Phishing Work?
URL phishing functions by exploiting trust and urgency to deceive users into giving off their personal information. In this social engineering method, cybercriminals craft convincing emails resembling legitimate reputable entities, often featuring urgent requests or lucrative offers. These emails contain links leading to official websites but are actually redirecting to fraudulent malicious websites.
Upon clicking, victims are directed to fake web pages where they’re asked to input personal or financial details under false pretenses, such as updating account information or verifying identity. The urgency presented by the hacker forces the victim to act hastily without verifying the page.
In some cases, the fraudulent URL briefly redirects to a genuine site after obtaining information, hiding the phishing attempt. Phishing pages can also mimic password reset forms or software updates, tricking users into unwittingly providing credentials or downloading malware.
URL Phishing Techniques
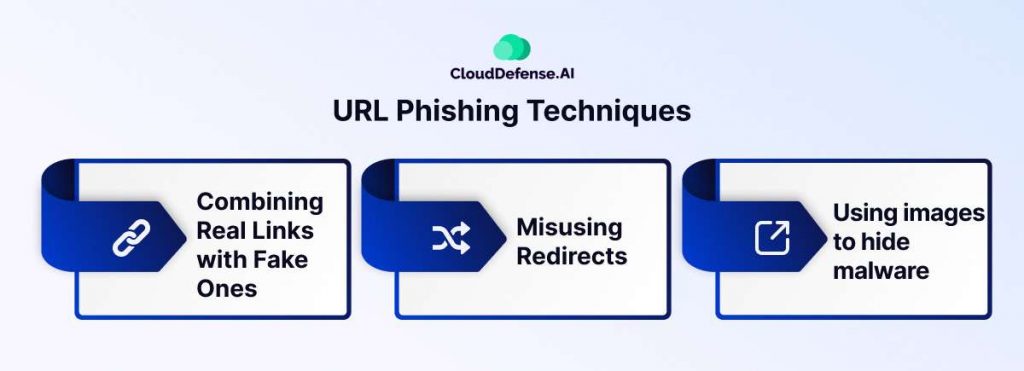
URL phishing techniques involve various strategies aimed at deceiving unsuspecting users into clicking malicious links and divulging sensitive information.
Combining Real Links with Fake Ones.
Cybercriminals blend legitimate links within emails to bypass basic security measures. By including authentic URLs alongside malicious ones, such as leading to a trusted website like irs.gov followed by a deceptive link, perpetrators exploit users’ trust and evade detection.
Misusing Redirects
Phishers manipulate redirects to initially direct users to legitimate pages, masking their malicious intent. After users provide credentials or interact with harmful content, they’re redirected to genuine sites, creating a false sense of security and concealing the phishing attempt.
Using images to hide malware
To evade text-based filters, cybercriminals employ images containing malware-laden text. By camouflaging malicious content within images, they circumvent detection and increase the likelihood of successful phishing attacks.
How to Identify if a URL is safe?
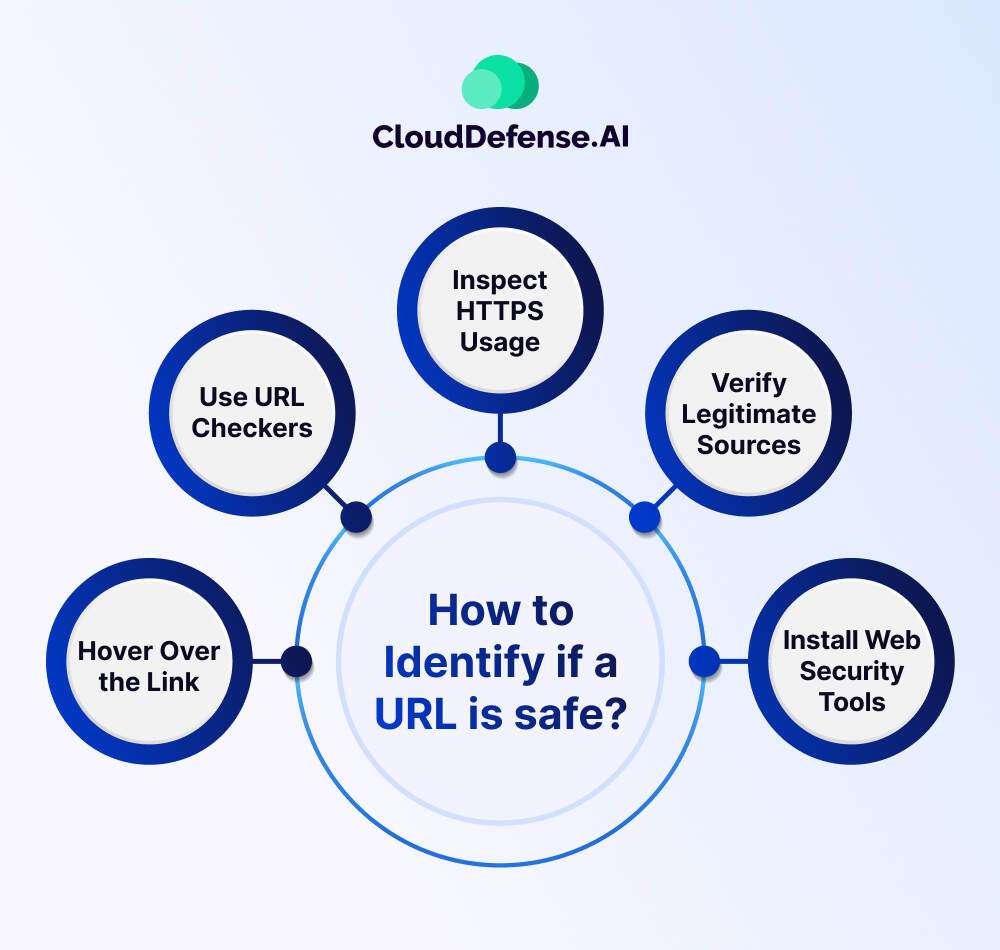
Before clicking on a link that you receive from an anonymous source, it is best to go through a few layers of checks. Here are five effective methods to determine if a link is safe before clicking:
Hover Over the Link
Hover your mouse cursor over the link to reveal the underlying URL. This preview allows you to verify if the displayed text matches the actual destination. Watch out for discrepancies, as cybercriminals often disguise malicious links with legitimate-looking text.
Use URL Checkers
Utilize online URL checkers such as Google Transparency Report or VirusTotal to assess the safety of a link. Copy and paste the link into the checker to receive an instant analysis of its reputation and legitimacy. Ensure you securely copy the link to avoid accidental clicks.
Inspect HTTPS Usage
Check if the website URL begins with “HTTPS” instead of “HTTP”. The presence of HTTPS indicates a secure connection, encrypting data transmission and protection against eavesdropping. Look for a padlock icon in the browser’s address bar to confirm secure browsing.
Verify Legitimate Sources
Seek confirmation from trusted sources, such as official websites or reputable security tools, regarding the link’s authenticity. Explore reviews, testimonials, or safety reports to validate the credibility of the website before clicking.
Install Web Security Tools
Enhance your online safety by installing reliable cybersecurity software like AVG AntiVirus FREE. These tools offer real-time protection against malicious links, phishing attempts, and malware infections, ensuring a secure browsing experience.
How To Identify URL Phishing?
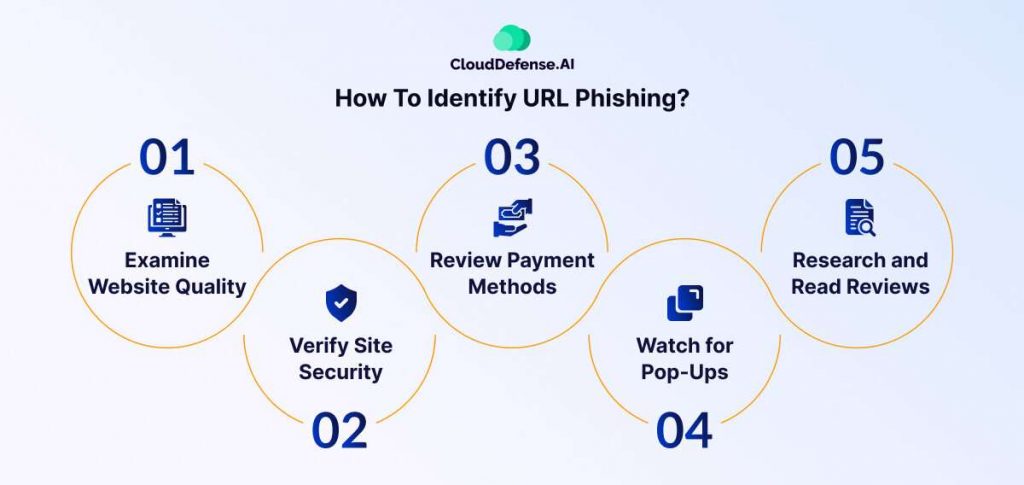
Identifying URL phishing requires a keen eye for some irregularities and red flags. Here’s how to spot potential phishing attempts:
Examine Website Quality
Legitimate businesses invest in professional website design with high-quality graphics and error-free content. Phishing websites often appear substandard, with broken English, grammar mistakes, and low-resolution images. The lack of a “contact us” page or missing contact details further raises suspicion.
Verify Site Security
Browsers may warn of insecure connections when visiting phishing sites. Look for security alerts like “insecure connection” and check for the padlock icon indicating encryption. Secure connections protect sensitive information and prevent unauthorized access.
Review Payment Methods
Legitimate websites accept standard online payment methods like credit cards or PayPal. Beware of phishing sites requesting bank transfers, as these are often irreversible. Never make purchases via bank transfer on unfamiliar websites.
Watch for Pop-Ups
Phishing scams may use pop-up windows to solicit personal information. Be cautious of immediate pop-ups asking for usernames or passwords, especially on unverified sites. Only enter information on trusted, secure websites.
Research and Read Reviews
Before making purchases or providing personal details, research the company and check its reputation. Look for reviews from credible sources and watch for common indicators of fake feedback, such as similar writing styles or very recent reviews.
How can CloudDefense.AI Protect you from URL Phishing?
CloudDefense.AI provides cybersecurity solutions that help protect you and your company against URL phishing attacks. With its advanced threat detection capabilities, CloudDefense.AI identifies and mitigates phishing attempts, protecting users from accessing malicious URLs.
Through innovative technologies like HackerView™ and real-time threat intelligence, CloudDefense.AI monitors for suspicious URLs, ensuring users are alerted to potential threats before they can cause harm.
Moreover, CloudDefense.AI’s risk-based prioritization gives organizations the power to focus on addressing critical phishing threats first, minimizing the risk of data breaches and financial losses.
With its user-friendly interface and expert support, CloudDefense.AI enables organizations to navigate complex security challenges with ease, effectively defending against phishing attacks and ensuring the security of their digital assets.
Stay ahead of cyber threats and protect your organization’s data and infrastructure effortlessly with CloudDefense.AI. Book a free demo to get hands-on experience right now!







