Definition – What Is Unified Endpoint Security?
At its core, Unified Endpoint Security is about consolidating multiple security capabilities into a single solution to protect all the endpoints in your environment. Endpoints refer to any device that connects to your network – laptops, desktops, mobile devices, servers, and even IoT gadgets.
Traditionally, organizations had to deploy and manage separate security products for different purposes like antivirus, firewalls, encryption, and threat detection/response. But that approach created security silos and visibility gaps. UES takes an integrated approach by unifying those capabilities into one comprehensive platform.
The key components typically included in a UES solution are:
- Anti-malware/antivirus to detect and prevent known and unknown malware.
- Host-based firewalls and web filtering.
- Encryption for data-at-rest and in-transit.
- Endpoint detection and response (EDR) for continuous monitoring and analysis.
- Automated response capabilities like quarantining, killing processes, etc.
UES provides administrators with centralized visibility and control across all endpoints by combining these capabilities into a single agent on the endpoint and a unified management console. Such an integrated approach allows for faster threat detection, coordinated response actions, and consistent security enforcement everywhere.
Features of Unified Endpoint Security
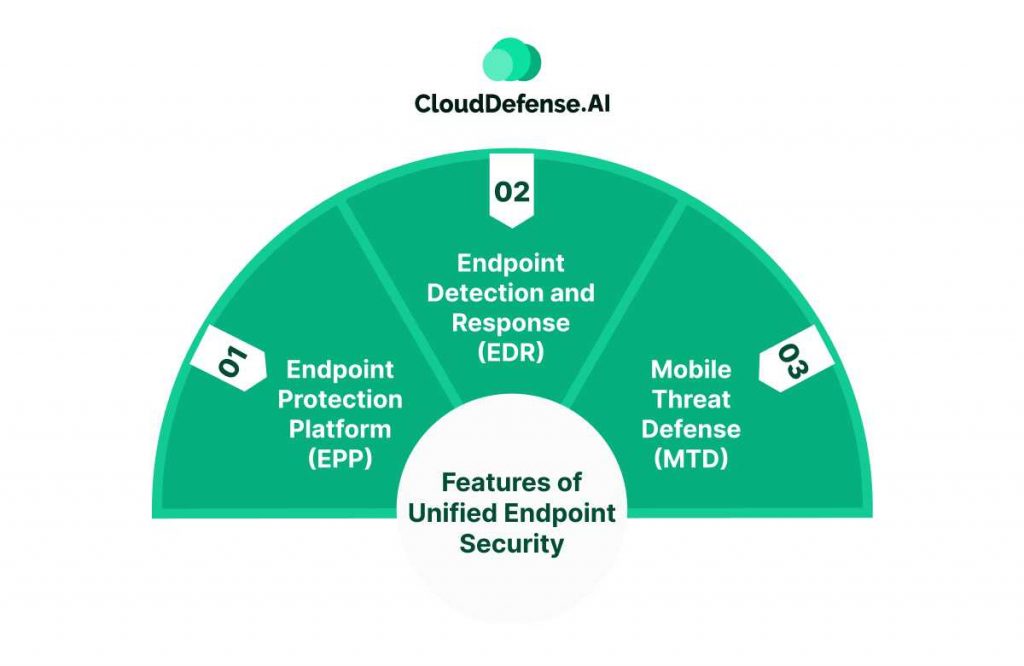
Unified Endpoint Security (UES) combines and integrates several key security components into a single platform, providing centralized management through one pane of glass. The major components that UES typically incorporates are:
Endpoint Protection Platform (EPP)
This includes traditional endpoint security capabilities like anti-malware scanning, application whitelisting/blacklisting, host-based firewalls, web filtering, data encryption and device control policies.
Endpoint Detection and Response (EDR)
EDR provides continuous monitoring and collection of endpoint data to detect and analyze advanced threats. It enables security analytics, threat hunting, root cause analysis and automated response actions like process termination.
Mobile Threat Defense (MTD)
As mobile devices proliferate, MTD capabilities protect against mobile threats like malicious apps, device exploits, network attacks and non-compliant configurations specifically for smartphones and tablets.
By unifying EPP, EDR and MTD functionality under a single UES agent and management console, organizations gain:
- Centralized visibility across all endpoint types
- Consolidated security policy enforcement
- Coordinated threat prevention, detection and response
- Streamlined security operations and less complexity
- Reduced overhead from multiple different product consoles
The convergence of these capabilities into an integrated UES platform provides a cohesive and comprehensive approach to endpoint risk management and threat protection
The Compelling Advantages of a UES Solution
We’ve gone over what each of those endpoint security components like EPP, EDR and MTD bring to the table. But you might be thinking – why go through the hassle of integrating all that under one roof? Here’s the deal – implementing a true UES solution packs some serious advantages that make it well worth the effort.
For starters, it solves one of cybersecurity’s biggest headaches – alert overload and lack of visibility caused by disjointed security tools. A whopping 59% of organizations cited this as a major challenge, according to Forrester. So, by unifying everything into one pane of glass, UES eliminates that chaos. You get complete clarity into threats across your entire endpoint landscape.
Even Microsoft recommends consolidated security to reduce complexity, and they’re not wrong. UES massively lightens the operational load on your likely overwhelmed security teams. Instead of switching context between separate EPP, EDR, and MTD solutions, they have one seamless workflow to secure endpoints. No more swiveling between a maze of monitors.
From an ROI perspective, UES also lets you streamline costs. Why pay for disparate endpoint security products when you can invest in one comprehensive UES platform? You’re cutting down on the number of solutions to purchase, integrate, update and manage. Those cost efficiencies can be huge for resource-constrained organizations.
Then there are the security benefits of UES’ unified capabilities itself – coordinated visibility, centralized enforcement of policies/controls, automated response actions and more. Rather than running endpoint security in silos with gaps, UES provides an integrated fabric of defense fortifying your entire endpoint arsenal.
So, the bottom line? Implementing UES abolishes that overly complex, blindspot-ridden approach where endpoint security falls through the cracks. With unified management and hardening of all your distributed endpoints, you’re giving your teams the upper hand to proactively detect and shut down threats before they can propagate. In today’s hostile cyber battles, having that fully geared unified security force is a decisive competitive advantage.
Why is Unified Endpoint Security Crucial?
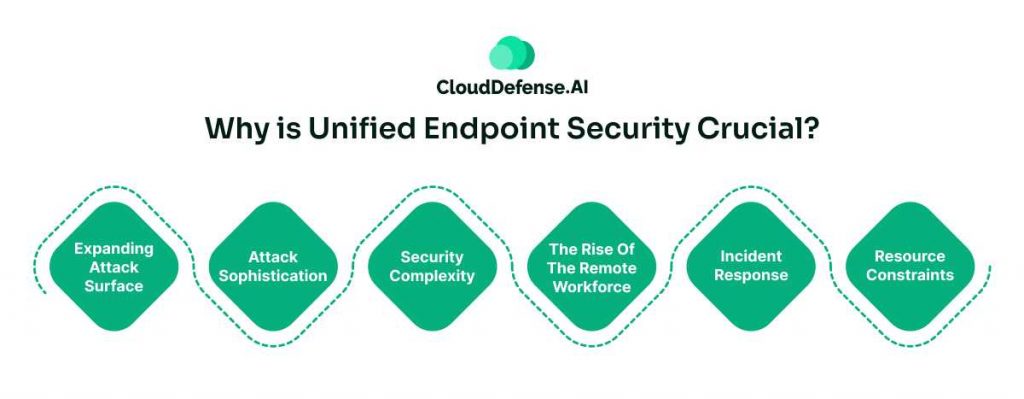
Expanding Attack Surface
Let’s be real – with cyber crooks constantly switching up their game, relying on old school antivirus just isn’t going to cut it anymore. Sophisticated malware, ransomware and those persistent attackers have forced us to level up our endpoint security game. For starters, we’re dealing with more endpoints than ever connecting to our networks – smartphones, tablets, IoT devices, cloud workloads…you name it. Securing that ever-expanding attack surface is like a juggling act on steroids.
Attack Sophistication
Meanwhile, the bad guys keep one-upping their attacks with file-less malware, obfuscation tricks and multi-pronged campaigns meant to bypass our traditional defenses. A unified, coordinated counterattack is crucial.
Security Complexity
Then there’s the complexity nightmare of piecing together separate security tools for antivirus, firewalls, encryption, threat detection and so on. Running all those disparate consoles is a headache waiting to happen, with visibility gaps that clever attackers will inevitably slip through.
The Rise of the Remote Workforce
With more employees working remotely, the corporate network perimeter has become porous. UES provides centralized security management, ensuring all devices – wherever they are – are protected.
Incident Response
Speaking of attacks, when one inevitably hits, we need to be able to detect, investigate and contain it blazing fast across all endpoints. Unified visibility is make-or-break for coordinating an effective incident response. Just a little too late, and an attack can spiral out-of-control in seconds.
Resource Constraints
Finally, let’s acknowledge that security teams are stretched thin enough as it is. UES simplifies ops by consolidating those fragmented capabilities into one integrated solution to rule them all. Less cowboy-style juggling multiple tools equals more time to actually focus on protection.
UES tackles these pressing challenges head-on by unifying all those endpoint security components. Think of it as securing that endpoint frontier with an impenetrable force-field while also giving defenders the big-picture oversight to swiftly rally against any incoming siege. In today’s cyber wild west, you need UES as your trusty arsenal.
Key Components of a UES Solution
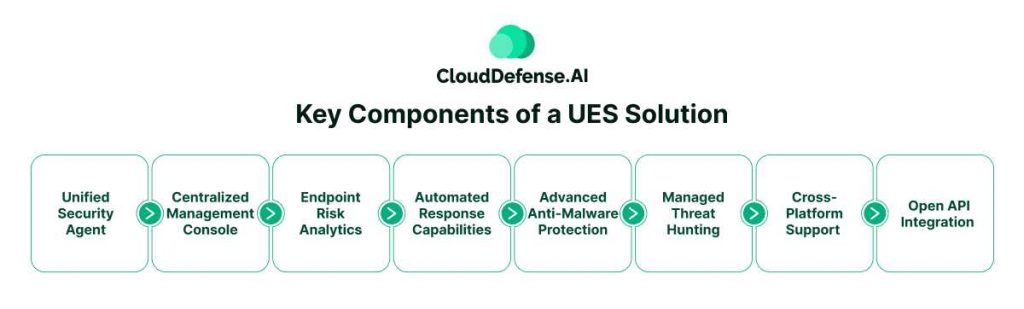
Unified Security Agent
At the core of UES is a single lightweight agent that resides on every managed endpoint – laptops, servers, mobile devices etc. The agent integrates and coordinates all the security capabilities like EPP, EDR, MTD, firewall, encryption and more. It provides comprehensive endpoint hardening and protection.
Centralized Management Console
Instead of wrestling with multiple consoles, UES gives you a glorious single pane of glass for managing security across your entire endpoint universe. From this command center, you can dole out security policies, monitor threat events, and coordinate containment actions seamlessly. Full visibility into what’s happening on every endpoint, all in one place.
Endpoint Risk Analytics
With the insights pulled from those unified agents, UES becomes a threat intelligence mastermind. It constantly analyzes and scores the risk level of each endpoint based on detected threats, vulnerabilities, misconfigs, and other shadiness. The highest risk machines get automatically prioritized so you can swiftly deal with the critical dangers first.
Automated Response Capabilities
But UES doesn’t just detect and relay information, it can automatically take action too. Preconfigured security playbooks allow it to instantly contain threats by isolating compromised devices, terminating malicious processes mid-execution, blocking sketchy connections and more. It’s an automated security ninja preventing attacks from escalating.
Advanced Anti-Malware Protection
Forget those old antivirus sigs, UES brings an arsenal of advanced anti-malware techniques. Machine learning models analyze code for the slightest evil intent. Behavior monitoring detects malware making shady moves. Sandboxing executes files in a confined environment to analyze them safely. Layered protection to punish even the most obfuscated, file-less malware.
Managed Threat Hunting
For the ultra-robust UES solutions, you get managed threat hunting as well. The vendor’s security super-sleuths proactively monitor your environment 24/7, analyze odd behaviors and go deep undercover to sniff out even the sneakiest attack campaigns that may be lying in wait.
Cross-Platform Support
No matter what operating systems or devices make up your environment – Windows, Mac, Linux, iOS, Android, UES has it covered. This cybersecurity bodyguard defends all your endpoints regardless of platform or form factor.
Open API Integration
Of course, UES plays nicely with others too. Open APIs allow it to integrate and share threat intelligence with other enterprise security tools like SIEMs, firewalls, identity systems and more for a coordinated threat response across your security stack.
Should You Implement a UES Solution? It’s Time to Unify Your Defenses
Feeling overwhelmed by managing a patchwork of security tools? Are your security alerts flooding your inbox, making it hard to identify real threats? If so, a Unified Endpoint Security (UES) solution might be your knight in shining armor.
Here’s why UES could be a game-changer for your organization:
- Security Headaches? Gone! UES simplifies security management by consolidating tools under one roof. No more juggling multiple platforms and policies.
- See the Bigger Picture: Gain a centralized view of your entire device landscape, from desktops to mobiles. Identify vulnerabilities and take action before they become breaches.
- Stop Threats in Their Tracks: UES offers a layered defense, combining prevention, detection, and response. Block malware, identify suspicious activity, and neutralize threats before they cause damage.
- Save Time and Money: Reduce the time and resources spent managing separate security solutions. UES streamlines operations and saves you money in the long run.
- Compliance Made Easy: Enforce consistent security policies across all devices, simplifying compliance with data security regulations.
So, is UES right for you?
Consider these factors:
- Security Complexity: Struggling with multiple security tools? UES can simplify your life.
- Visibility and Control: Do you have a clear view of your device security posture? UES provides centralized control and visibility.
- Resource Constraints: Is your IT team overloaded? UES streamlines management, freeing up valuable resources.
- Compliance Requirements: Do you need to comply with data security regulations? UES simplifies compliance management.
Ready to Get Started? Here’s Your Action Plan:
- Evaluate Your Needs: Identify your organization’s specific security challenges and goals.
- Research UES Solutions: Explore different UES vendors and features that align with your needs and budget.
- Conduct a Pilot Project: Start with a pilot program on a limited set of devices to test the UES solution and ensure smooth integration.
- Develop a Deployment Plan: Create a comprehensive plan for deploying the UES solution across your entire organization.
- Train Your Team: Educate your IT team and users on the new UES platform and security policies.
Final Words
Don’t let your organization become the next cybercrime headline. The current threat front is a digital battlefield, and fragmented security leaves your data vulnerable. Therefore it’s time to unify your defenses, gain complete visibility, and neutralize threats before they escalate with a Unified Endpoint Security solution. The future of your organization depends on it. Act now, before it’s too late.







