What Is Threat Detection & Response?
Threat Detection and Response (TDR) is a powerful cybersecurity approach designed to find and stop threats fast. It’s about identifying dangerous activities, analyzing them, and taking action before they can do damage. Simple, effective, and absolutely necessary in today’s digital world.
What TDR Does:
- Detects hackers, malware, and anything that doesn’t belong in your system.
- Analyzes data and activity to uncover hidden risks.
- Pulls together information from all corners of your network for a full picture.
- Focuses on the biggest threats first, no wasting time on small stuff.
- Takes quick, decisive action to stop attacks in their tracks.
- Keeps your systems safe and your business running smoothly.
- TDR is the smart choice for staying ahead of cybercriminals. It’s about being proactive, being strong, and never letting your guard down.
Threat Detection and Threat Response: Breaking It Down
Understanding Threat Detection and Response starts with looking at its two core parts. These are not just buzzwords—they define how organizations fight back against cyber threats every single day.
Threat Detection
Threat detection is about finding the bad actors and suspicious activities in your network before they cause damage. This isn’t guesswork; it’s highly strategic and technical.
Here’s how it works:
- Monitors your systems 24/7 for unusual behaviors or unauthorized access attempts.
- Uses advanced tools like machine learning and threat intelligence to spot attacks, even the sneaky ones.
- Correlates logs and data from endpoints, servers, and cloud environments to catch patterns humans can’t see.
- Flags vulnerabilities, misconfigurations, or other gaps in your defenses.
Without effective detection, you’re operating blind. You’re waiting for a disaster to strike, and by then, it’s too late. Threat detection ensures you always know what’s happening in your environment.
Threat Response
Threat response is what happens after a threat is detected. It’s where action meets strategy—where you stop an attack from becoming a breach.
What does response look like?
- Identifies the severity of the threat to decide what needs immediate action.
- Isolates affected systems to contain the attack and prevent further spread.
- Removes malicious software, blocks attackers, or locks down compromised accounts.
- Keeps stakeholders informed with clear, actionable updates.
- Learns from the incident to improve defenses and avoid future attacks.
Threat response is where organizations prove their resilience. It’s not just about stopping the bad guys; it’s about ensuring they don’t come back.
Why Both Matter Together?
Threat detection without response is like seeing a storm and doing nothing to prepare. Threat response without detection is like cleaning up the mess after the storm—too little, too late. Together, they form the foundation of a strong cybersecurity strategy, keeping you ahead of modern threats.
Common Threats Addressed by TDR Solutions
TDR solutions are tough on threats. They target the real issues businesses face today, threats that can destroy a system if left unchecked.
- Malware: Malware comes in many forms—viruses, ransomware, trojans. TDR spots it and stops it before it does any damage.
- Phishing Attacks: Cybercriminals try to trick your people into giving up sensitive info. TDR detects phishing attempts quickly, protecting your company from costly mistakes.
- Insider Threats: Not all threats come from the outside. Sometimes, it’s someone inside the company. TDR monitors internal activity to catch misuse of access rights.
- Advanced Persistent Threats (APTs): These attacks are sneaky and long-term. TDR tracks suspicious patterns to find these threats before they can do serious harm.
- Zero-Day Exploits: Hackers target vulnerabilities no one knows about yet. TDR catches these threats by analyzing behavior, not just looking for known signatures.
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks: These attacks flood your system with traffic to crash it. TDR detects and blocks unusual activity to prevent downtime.
- Unauthorized Access: Hackers try to break in using stolen credentials. TDR flags unauthorized attempts and stops them cold.
With TDR, you have a solution that doesn’t just react—it stops these threats before they even have a chance to hurt your business. Simple. Effective. Reliable.
Why Do You Need Threat Detection and Response?
You need Threat Detection and Response because cyber threats are real, and they’re everywhere. They don’t wait for the right moment—they strike when you least expect it. Here’s why TDR is critical for your business:
Threats are evolving
Attackers are always finding new ways to get in. Malware, ransomware, phishing, and other types of attacks are getting more sophisticated. You need a system that adapts to these changes and spots threats in real-time.
Speed Matters
A delay in detecting a breach can cost you. The faster you catch the problem, the less damage is done. TDR allows you to respond immediately, limiting the impact and getting back to business faster.
Protects your data
Your data is your most valuable asset. TDR solutions help protect it from unauthorized access, theft, or loss. It’s about keeping your sensitive information safe from those who want to take it.
Detects the undetected
Some threats are hidden. Hackers know how to cover their tracks, making it hard to spot them. TDR uses advanced techniques to detect these stealthy attacks before they cause major issues.
Minimizes downtime
Downtime means lost revenue, lost productivity, and potential customer dissatisfaction. TDR quickly isolates and neutralizes threats, keeping your systems running smoothly.
Improves compliance
Many industries have strict security regulations. TDR helps you meet these standards by continuously monitoring your systems and providing detailed reports on your security status.
Peace of mind
Cyber threats are constantly evolving. With TDR in place, you can rest easy knowing your business is protected. You have the tools and processes to stop threats before they disrupt your operations.
How Does Threat Detection and Response Work?
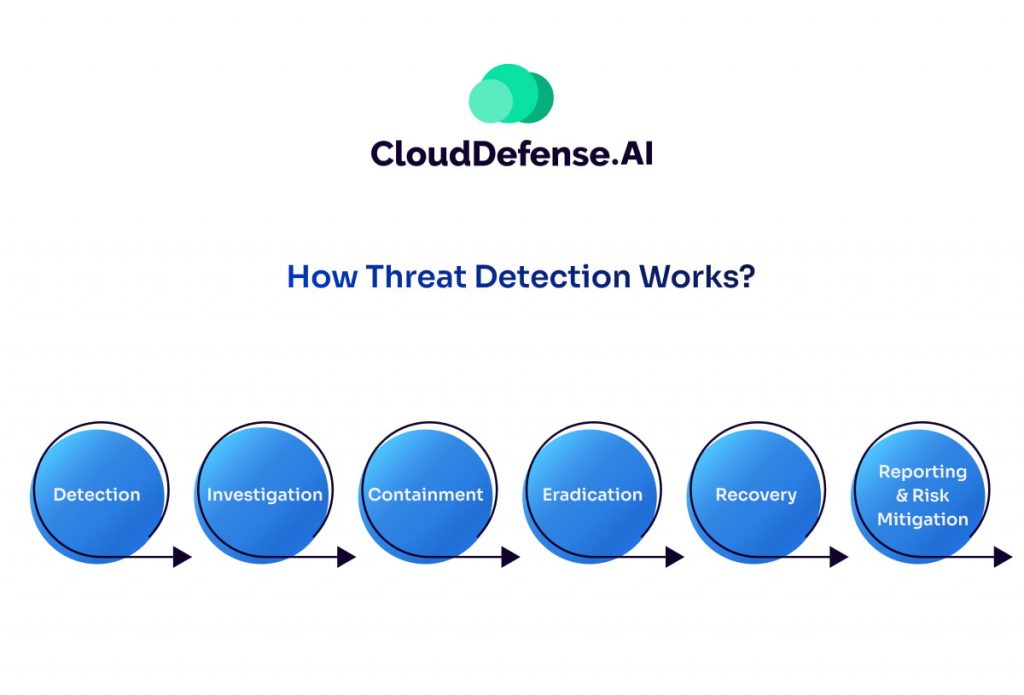
Every organization needs a strong, clear strategy to handle cyber threats. That’s where threat detection and response come in. It’s not just about reacting after something goes wrong—it’s about setting up a system that actively prevents, detects, and responds to threats before they do major damage.
Here’s how it works, step by step:
Continuous Monitoring
Most companies set up a Security Operations Center (SOC) to take charge of cybersecurity. The SOC is the brain of your operations, a dedicated team (sometimes outsourced) that monitors security 24/7. They track threats, analyze data, and ensure the company is protected. Their job isn’t just reacting; they’re always looking for emerging threats, vulnerabilities, and ways to stay ahead.
Using Threat Intelligence and Tools:
The SOC relies on advanced technology and threat intelligence to spot issues. They track everything happening in your network, from endpoints to cloud environments. When something looks suspicious, they dive deep to identify it, whether it’s an active threat or a potential future risk.
Once the SOC identifies a threat, they take these steps to neutralize it. And that’s where the threat detection parts come in. Here are the steps:
Detection:
Security tools monitor your systems nonstop, checking endpoints, identities, networks, apps, and the cloud. These tools detect any unusual activity, flagging risks like unauthorized access or malware. Cyber threat hunters also manually look for threats that might evade automated systems.
Investigation:
Once a threat is detected, the SOC team verifies if it’s real. They use AI and advanced tools to dig into the details—how did it get in? Which part of the business is affected? Is it a minor issue or a full-blown breach? They analyze the data to get a complete picture.
Containment:
The next step is to stop the threat from spreading. If a cyberattack is in progress, the team isolates the affected devices, users, or networks. This is a critical step because preventing the attack from spreading can save you from much bigger damage.
Eradication:
Once the threat is contained, it’s time to remove it completely. The team hunts down the root cause of the issue, evicting the hacker or malware from the system entirely. They also fix the vulnerabilities that allowed the attack to happen in the first place, ensuring it doesn’t happen again.
Recovery:
After cleaning up, the team ensures that the environment is safe to return to normal. They carefully bring any isolated systems back online, making sure the threat is completely gone and that everything is secure.
Report:
After the situation is under control, the team documents what happened and reports the incident to key company leaders, executives, and even the board if needed. They explain what was found, what was done, and how the company can prevent similar issues in the future.
Risk Mitigation:
Finally, the team takes steps to make sure the breach doesn’t happen again. They analyze the entire process, looking for lessons learned and ways to improve security measures. They’ll update protocols, improve monitoring, and implement new strategies to make your system stronger going forward.
Types of Detection and Response Solutions
Given complex security conditions, organizations need specialized tools to detect and respond to various types of threats. Different environments—endpoints, networks, and cloud systems—require tailored solutions to address the specific risks associated with them. Below is a comparison of the four main types of detection and response solutions: EDR, CDR, NDR, and XDR.
| Solution | Focus Area | Key Features | Best For |
| EDR | Endpoints (Desktops, Laptops, Servers) | Monitors activity on devices, detects suspicious behavior, isolates infected devices, automated response | Protecting individual devices from malware, ransomware, and attacks on endpoints |
| CDR | Cloud Environments (Infrastructure, Apps, Data) | Monitors cloud setups, user access, and data flow. Secures cloud resources against unauthorized access | Safeguarding cloud infrastructure from misconfigurations and cloud-specific risks |
| NDR | Network Traffic | Tracks and analyzes network activity, identifies data movement, detects lateral attacks | Keeping an eye on threats moving across the network, including data exfiltration and hidden attacks |
| XDR | Multi-environment (Endpoints, Network, Cloud) | Combines data from EDR, NDR, and CDR for a full view. Faster detection, automated responses | Offering integrated security across all environments for faster response and better protection |
Each of these solutions targets a different area of your cybersecurity. When combined, they provide a powerful defense system that catches threats wherever they arise—on devices, across your network, and in the cloud.
Threat Detection and Response Best Practices

TDRs are essential components of any organization’s cybersecurity strategy. Effective practices not only help prevent potential breaches but also ensure swift and efficient mitigation when incidents occur. Here are some best practices that you can follow to get the best out of your TDR tool.
Regular Training
Cybersecurity awareness should be ingrained across all levels of an organization. While the SOC team plays a pivotal role, every employee must be equipped to recognize and respond to potential threats. Regular training programs not only sensitize the workforce to common attack vectors like phishing campaigns but also keep security professionals aware of threats and response protocols.
Continuous Improvement
Every security incident offers valuable lessons. Post-incident evaluations help identify strengths and weaknesses in the organization’s response procedures, facilitating ongoing improvements. Solutions like XDR help with this iterative process by incorporating post-incident analysis into the response workflow, thereby ensuring that each incident contributes to enhancing the organization’s security posture.
Collaboration and Communication
Effective threat detection and response hinge on collaboration and communication within the security team and across departments. Team members need to share insights, compare assessments, and work together to address potential threats promptly. Furthermore, collaboration with other departments can enhance threat detection capabilities and streamline incident response efforts.
Incident Response Planning
When a security incident occurs, time is of the essence. An incident response plan delineates clear steps for containment, eradication, and recovery, minimizing guesswork and ensuring a coordinated response. Moreover, such plans extend beyond technical aspects, offering guidance on communication with stakeholders, compliance with regulations, and legal considerations.
AI Integration
using AI is becoming increasingly prevalent in cybersecurity. AI-powered solutions like SIEM and XDR enhance threat detection by synthesizing data from disparate sources, correlating alerts, and automating response actions. These technologies enable organizations to detect and mitigate cyber threats faster and more effectively.
How Can CloudDefense.AI Help?
CloudDefense.AI provides advanced threat detection and response capabilities tailored specifically for modern cloud environments. The platform is designed to deliver real-time visibility and protection, ensuring organizations can rapidly detect, investigate, and mitigate both known and emerging cyber threats across their cloud infrastructure.
With a combination of AI-driven detection techniques and comprehensive monitoring, CloudDefense.AI helps organizations stay ahead of sophisticated attacks that target cloud systems, services, APIs, and identities.
Key capabilities of CloudDefense.AI include:
- Continuous cloud activity monitoring to provide full visibility across cloud services, workloads, and identities.
- Real-time threat detection powered by AI and behavioral analysis to identify anomalies, suspicious activity, and potential breaches.
- Misconfiguration detection to identify improperly secured cloud assets, reducing exposure before attackers can exploit vulnerabilities.
- Correlation of real-time signals to connect events across different parts of the cloud environment and uncover coordinated attack patterns.
- Risk-based prioritization to ensure the most critical threats — those with the highest potential impact — are addressed first.
- Graph-driven investigation tools to visualize attack paths, impacted assets, and attacker movements, enabling faster and more precise response.
- API security assessments to identify and mitigate risks related to exposed, misconfigured, or insecure APIs.
CloudDefense.AI’s strength lies in its ability to prioritize threats based on an organization’s unique cloud architecture and operational risk profile, ensuring security teams are focusing their time and resources on the most pressing vulnerabilities and incidents.
For organizations looking to improve cloud threat detection and response, CloudDefense.AI offers a comprehensive, purpose-built solution that combines advanced technology with practical visibility and response tools. To see how CloudDefense.AI can enhance your security operations, book a free demo today.
Conclusion
Threat detection and response is a core requirement for any organization serious about protecting its data, infrastructure, and reputation. As threats evolve, businesses need modern, adaptive solutions that provide real-time visibility, proactive detection, and rapid response. With advanced platforms like CloudDefense.AI, organizations can stay ahead of threats, reduce risk exposure, and strengthen their overall security posture across cloud and hybrid environments.







