What Exactly is TDIR?
TDIR stands for Threat Detection and Incident Response. Basically, it’s all about spotting the bad stuff happening in your systems and then dealing with it.
Think of TDIR as your digital security guard. It’s constantly on the lookout for any suspicious activity across your entire network – from your computers and servers to your cloud storage and apps. When it spots something fishy, it alerts your team so they can investigate and tackle the problem.
Now, there are two main parts to TDIR:
First, you’ve got threat detection. This is like having a super-smart alarm system for your digital stuff. It sifts through tons of data from all over your network, looking for anything that seems off. Could be a hacker trying to sneak in, a virus, or even someone inside your company doing something they shouldn’t.
Then there’s incident response. This is what happens after a threat is detected. Your security team jumps into action, figuring out what’s going on and how to fix it. They use special tools to investigate, contain the threat, and clean up any mess it might have made.
Simply put,
Threat Detection:
- Identifying potential security risks
- Monitoring systems for suspicious activities
- Using tools to spot anomalies
Incident Response:
- Planned approach to handle security breaches
- Quick action to contain identified threats
- Steps to recover and prevent future incidents
A lot of TDIR systems come with some fancy features. They often include things like SIEM (which helps manage security info and events) and SOAR (which automates some of the response processes). These tools can also help with other important stuff like keeping track of your system logs and making sure you’re following all the necessary security rules.
Evolution of TDIR
So, here’s the deal. Bad guys are getting smarter, and their tricks are getting more complex. This means it’s getting harder for security teams to spot and deal with threats. Sometimes attackers use brand new ways to break in that no one’s seen before, or they find clever ways to slip past our usual defenses.
And when that happens, security teams need to move fast to limit the damage. But that’s tough when you’re dealing with a threat you’ve never seen before, or when you need to dig through months of data to figure out what’s really going on.
Back in the day, security folks tried to use log aggregation tools for threat detection and response. But let’s be real, it wasn’t great. There’s just too much data these days, and those old-school SIEM solutions can’t keep up. They can’t handle the sheer amount of data that needs to be processed, analyzed, and stored, especially in modern cloud environments.
So, what did security teams do? A lot of them tried to build their own tools. But that’s a whole other can of worms. Building and maintaining your own tools takes a ton of time and resources.
But here’s the good news. In recent years, we’ve seen new solutions pop up that are built for this new world of cloud computing. These new tools treat security like the big data problem it really is. They’re built from the ground up to handle massive amounts of data – we’re talking terabytes of logs every day. They turn all that raw data into a structured format that’s actually useful for real-time threat detection, quick incident response, and thorough investigations.
Now that we’ve got these new high-scale TDIR solutions, security teams can finally tackle a lot of the challenges that used to give them headaches. It’s not perfect, but it’s a huge step forward from where we used to be.
Is TDIR a Security Tool?
Alright, let’s clear up a common misconception about TDIR not being a single product:
Here’s something crucial to understand: TDIR isn’t just one product you can buy off the shelf. It’s more of a holistic approach to security.
These days, TDIR is evolving into what the industry calls “unified security analytics platforms” or “Next-Gen SIEMs”. Fancy names aside, what this really means is that different security tools are coming together in one place. It’s like having all your security gadgets in a single, super-smart control center.
But here’s the kicker – even these advanced platforms aren’t a magic bullet. They work best when they play nice with all the security stuff you’ve already got in place. So, to get the most out of TDIR, you need to think about how it fits into your overall security setup.
TDIR Lifecycle Process
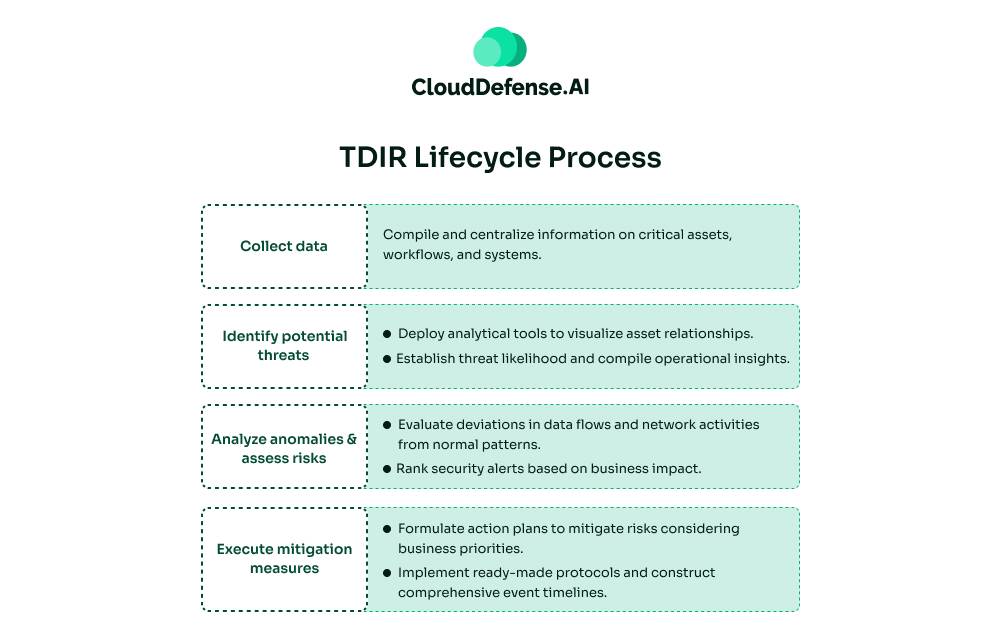
The TDIR lifecycle boils down to four main steps. Each step builds on the previous one, creating a comprehensive approach to handling cybersecurity threats.
1. Data Gathering: First, we collect all relevant info about our valuable assets, operations, and processes. This data comes from various sources – predefined ones, integrations, and cloud platforms.
2. Threat Detection: Next, we put our detection tools to work. We map out our assets, figure out our risk profile, and get a handle on the business context. Tools like MITRE ATT&CK help us gauge how severe the risks are and understand the whole process better.
3. Incident Investigation: This is where we dig deeper. We look at new data to see how network traffic and data transmission are behaving compared to what we expect. We also use business context to figure out which alerts need our attention first.
4. Response Execution: Finally, we craft and implement a solid response plan. This plan aims to cut down risks based on what we know about our business. We use ready-made playbooks for specific types of incidents and create timelines for all our IT assets to keep track of what’s happening.
Why is TDIR Crucial?
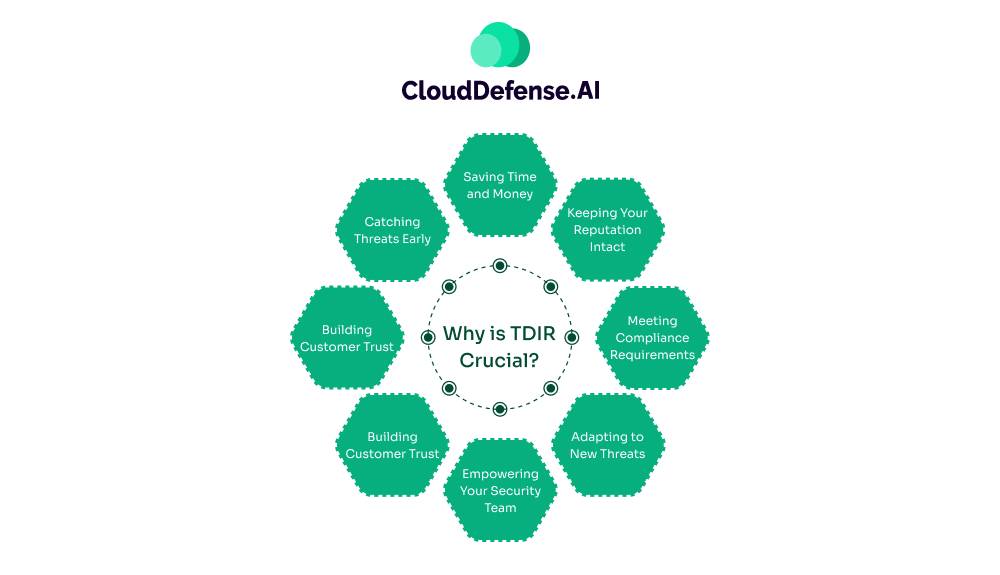
Catching Threats Early
Look, the sooner you spot a threat, the better off you are. TDIR helps you catch potential problems before they blow up into full-blown crises. It’s like nipping trouble in the bud before it can do real damage to your systems or data.
Saving Time and Money
When you’ve got a solid TDIR setup, you’re not wasting time chasing false alarms or scrambling to fix problems after they’ve already caused havoc. This means your team can work more efficiently, and you’re not bleeding money on costly clean-ups after an attack.
Keeping Your Reputation Intact
Let’s face it, data breaches are embarrassing. They can tank your company’s reputation faster than you can say “cybersecurity.” With TDIR, you’re less likely to end up in the news for all the wrong reasons.
Meeting Compliance Requirements
Depending on your industry, you might have to follow strict rules about data protection. TDIR helps you stay on top of these requirements, so you’re not caught out when the auditors come knocking.
Adapting to New Threats
Hackers are always coming up with new tricks. TDIR isn’t static – it evolves to spot and deal with new types of threats as they emerge. This means you’re not stuck relying on outdated security measures.
Empowering Your Security Team
Good TDIR tools give your security folks the information they need to make smart decisions quickly. It’s about equipping your team to be proactive, not just reactive, when it comes to security.
Building Customer Trust
When clients know you’re serious about protecting their data, they’re more likely to trust you. Solid TDIR practices show you’re committed to keeping their information safe.
Best Practices for Threat Detection, Investigation, and Response (TDIR)
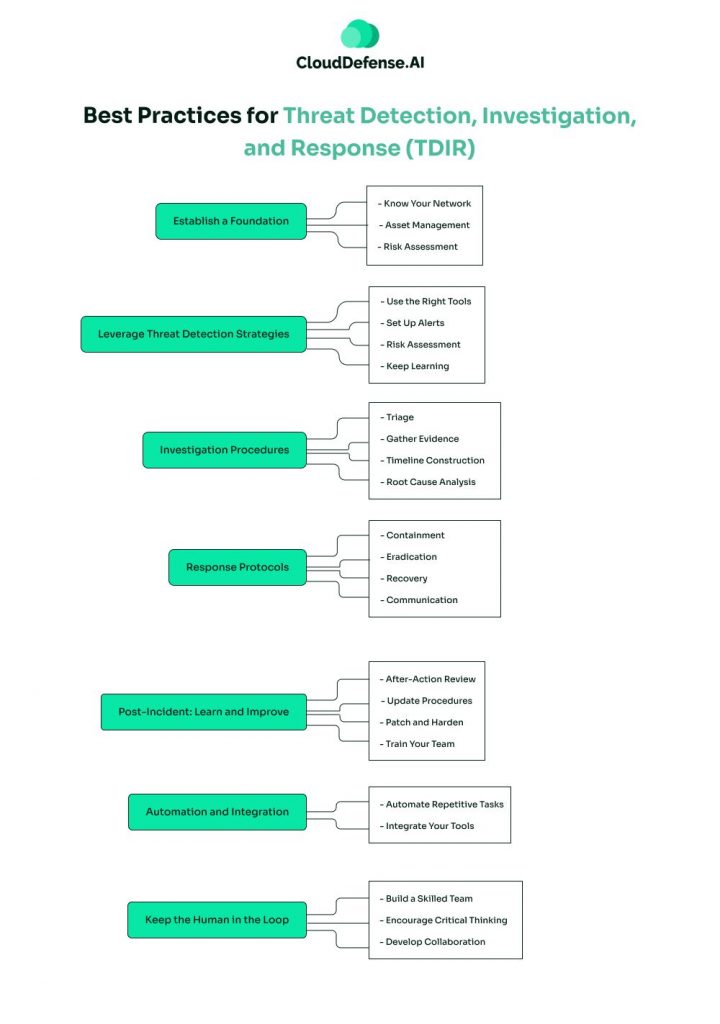
1. Establish a Foundation
Look, before you dive into the nitty-gritty of TDIR, you need to get your basics straight. This means:
- Know Your Network: Get familiar with what’s normal in your environment. You can’t spot the weird stuff if you don’t know what’s supposed to be there.
- Asset Management: Keep tabs on all your devices and systems. If you don’t know it exists, you can’t protect it.
- Risk Assessment: Figure out what’s most important to your organization and what bad guys might want. Focus your efforts there.
2. Leverage Threat Detection Strategies
- Use the Right Tools: Get yourself some good security information and event management (SIEM) software, intrusion detection systems (IDS), and endpoint detection and response (EDR) tools. They’re your eyes and ears.
- Set Up Alerts: Configure your tools to flag suspicious activity. But be smart about it – too many alerts and you’ll get overwhelmed.
- Monitor 24/7: Threats don’t sleep, so your detection shouldn’t either. Set up round-the-clock monitoring.
- Keep Learning: Stay on top of new threat intel and adjust your detection methods accordingly.
3. Investigation Procedures
So you’ve spotted something fishy. Now what? Time to investigate:
- Triage: Quickly assess how serious the threat is. You don’t want to waste time on false alarms.
- Gather Evidence: Pull logs, network traffic data, and anything else that might be relevant.
- Timeline Construction: Piece together what happened and when. This helps you understand the scope of the incident.
- Root Cause Analysis: Figure out how the attacker got in and what they were after.
4. Response Protocols
- Containment: Stop the attack from spreading. This might mean isolating systems or blocking certain traffic.
- Eradication: Get rid of the threat. Remove malware, close vulnerabilities, the whole nine yards.
- Recovery: Get your systems back to normal. Restore from backups if needed.
- Communication: Keep stakeholders in the loop. Let them know what happened and what you’re doing about it.
5. Post-Incident: Learn and Improve
The threat’s gone, but your job isn’t over:
- After-Action Review: Break down what happened, what worked, and what didn’t.
- Update Procedures: Use what you learned to improve your TDIR process.
- Patch and Harden: Fix any vulnerabilities you found and strengthen your defenses.
- Train Your Team: Share lessons learned with your staff. The more they know, the better prepared you’ll be next time.
6. Automation and Integration
Let’s face it, you can’t do everything manually:
- Automate Repetitive Tasks: Use playbooks and scripts to handle routine investigations and responses.
- Integrate Your Tools: Get your different security systems talking to each other. It’ll make your life a lot easier.
7. Keep the Human in the Loop
Tech is great, but don’t forget the human element:
- Build a Skilled Team: Invest in training and hiring good people. They’re your most valuable asset.
- Encourage Critical Thinking: Tools are great, but sometimes you need human intuition to spot tricky threats.
- Develop Collaboration: Get your security team working closely with IT, legal, and other departments. You’re all in this together.
Remember, TDIR isn’t a one-and-done thing. It’s an ongoing process. Keep at it, keep learning, and keep improving. That’s how you stay ahead of the bad guys.
Conclusion
TDIR isn’t a walk in the park. It’s tough, it’s complex, and it never really ends. But if you stick to the best practices and are proactive, you’ll be in good shape to handle whatever threats come your way. Remember, it’s all about being prepared, staying vigilant, and learning from every incident. Keep your tools sharp, your team sharper, and never stop improving your process. TDIR is an ongoing process. You’ll face new challenges, but each one is a chance to get better. With a strong TDIR strategy, you’re not just defending against threats – you’re building a more resilient organization.







