What is SQL Injection?
SQL injection is a web security vulnerability that occurs when an attacker manipulates the SQL queries an application sends to its database. By exploiting this flaw, attackers can inject malicious SQL code into input fields or request parameters, causing the database to execute unintended commands.
This manipulation can grant unauthorized access to sensitive data, such as user credentials, financial information, or proprietary business records, that the application would typically restrict. SQL injection attacks often exploit poorly sanitized or improperly validated user inputs.
Beyond data retrieval, attackers can use SQLi to modify, delete, or corrupt data, leading to persistent changes in the application’s functionality or content. in severe cases, the attack can escalate, enabling attackers to compromise the database server, gain control of the underlying infrastructure, or launch denial-of-service (DoS) attacks.
Example of SQL Injection Attack
Imagine your website has a search box where users can enter keywords to find products. Behind the scenes, the website takes the user’s search input and drops it directly into a SQL query to the database.
For example, if someone searches for “shirts,” the query might look like:
SELECT * FROM products WHERE name LIKE ‘%shirts%’
Seems harmless, right? But what if a bad guy, and instead of “shirts,” enters:
‘OR ‘1’=’1
Now the full query becomes:
SELECT * FROM products WHERE name LIKE ‘%’ OR ‘1’=’1%’
That “OR ‘1’=’1” part is always true for every product row! So the query will return ALL products in the database, regardless of the name.
Even worse, they could enter something more malicious like:
‘; DROP TABLE products; —
Which would literally wipe out the entire product table!
The core issue is that the application blindly inserts the user input into the SQL query without any validation or sanitization. This allows attackers to inject malicious SQL code and trick the database.
How do SQL Injection Attacks Work?
SQL injection (SQLi) attacks follow a systematic process, allowing attackers to exploit vulnerabilities in a web application or website. Here’s a structured breakdown of how these attacks typically unfold:
Reconnaissance: Identifying a Vulnerable Target
1. Objective: Attackers begin by probing websites or applications for vulnerabilities that could expose them to SQLi.
2. Method:
- Explore forms, URLs, and any inputs that accept user data.
- Input malformed or unusual data to analyze the application’s response.
3. Indicators: Error messages or abnormal application behavior can signal the presence of an injection flaw.
Determining the Attack Vector
1. Key Step: Once a vulnerability is identified, the attacker evaluates the type of SQL injection that can be exploited.
2. Common Vectors:
- Error-Based SQLi: Utilizes database error messages to extract information.
- Blind SQLi: Exploits the vulnerability without returning visible data.
- Union-Based SQLi: Combines results from multiple queries to extract data.
- Second-Order SQLi: Exploits stored input that triggers malicious code later.
- HTTP Header SQLi: Targets headers like User-Agent or Referer.
Crafting and Delivering the Payload
1. Goal: Create a malicious SQL query to manipulate the database.
2. Examples:
- A simple union-based payload:
SELECT * FROM users WHERE username = ‘admin’ OR ‘1’=’1′; - More complex, encoded payloads designed to bypass filters.
3. Execution: Attackers test these payloads in input fields to gain unauthorized access or manipulate data.
Exploiting the Database
1. Data Extraction: If successful, attackers may:
- View restricted data (e.g., user credentials, payment information).
- Modify or delete data.
- Escalate privileges to gain administrator-level access.
2. Advanced Exploitation: In some cases, attackers may compromise the underlying server or other infrastructure.
Maintaining Access and Covering Tracks
- Persistence: Attackers work to maintain access for future exploitation.
- Hiding Evidence: Steps are taken to erase logs or obscure malicious activity, making detection more difficult.
The SQLi attack process typically involves reconnaissance, vector identification, payload delivery, exploitation, and maintaining access. By leveraging vulnerabilities, attackers can gain unauthorized control over databases, posing significant risks to the security of applications and user data.
Types of SQL Injections
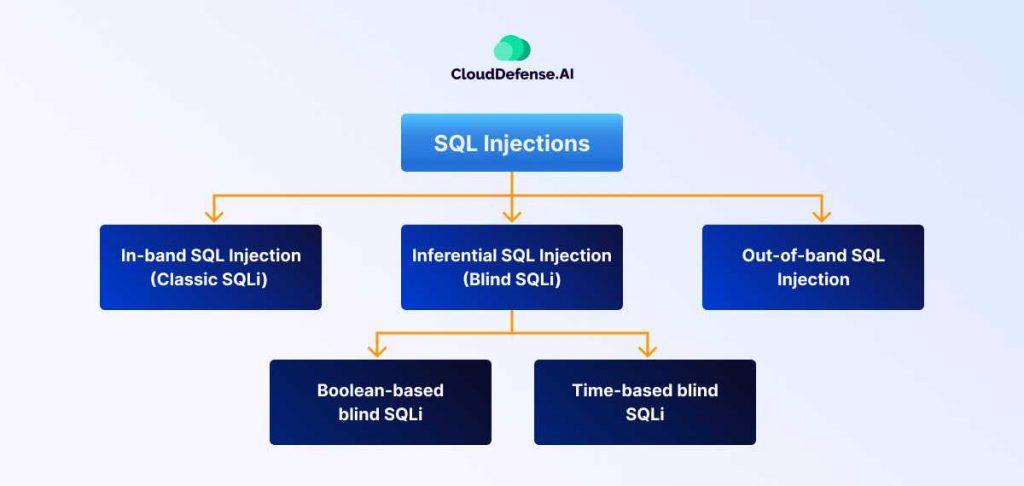
SQL injections can be broadly classified into three main categories based on how the attacker retrieves information from the database and the level of feedback they receive:
In-band SQL Injection (Classic SQLi)
In this type of SQLi, the attacker injects malicious code that directly yields results within the web application’s response. This is the most common and straightforward type of SQL injection.
Here’s a common example of an in-band SQL injection exploiting a login form:
Imagine a login form where the username and password are submitted to the server. A vulnerable application might build a login query like this:
SELECT * FROM users WHERE username = ‘$username’ AND password = ‘$password’;
An attacker can try injecting a username like ‘ OR ‘1’=’1′– (single quotes are used to escape the closing quotation mark). This modifies the SQL query to:
SELECT * FROM users WHERE username = ” OR ‘1’=’1′–‘ AND password = ‘$password’;
Since any value evaluated as true (including ‘1’=’1′) is true, the attacker bypasses authentication regardless of the password entered.
Inferential SQL Injection (Blind SQLi)
In blind SQL injection, the attacker cannot directly see the results of their injected code within the web application’s response. Instead, they rely on observing the application’s behavior (like error messages or response timings) to infer information about the database.
Blind SQLi is further divided into two subcategories:
- Boolean-based blind SQLi: The attacker uses techniques to craft queries that return a boolean (true/false) response. By observing the application’s behavior based on the truth value, the attacker can gradually extract information like characters in a password or the presence of specific data.
- Time-based blind SQLi: The attacker introduces delays into the SQL query execution time (e.g., using a function that forces the database to wait). By measuring these delays, the attacker can infer information about the database.
Out-of-band SQL Injection
Out-of-band SQL injection is a less common type of attack where the attacker uses the database server to communicate with an external server under their control. This enables them to exfiltrate data or even launch further attacks on the system.
Out-of-band SQLi typically relies on functionalities like database file writes or leveraging specific database features to establish communication channels. Due to these requirements, it’s not as frequently exploited as other SQLi techniques.
Potential Consequences of SQLi Attacks
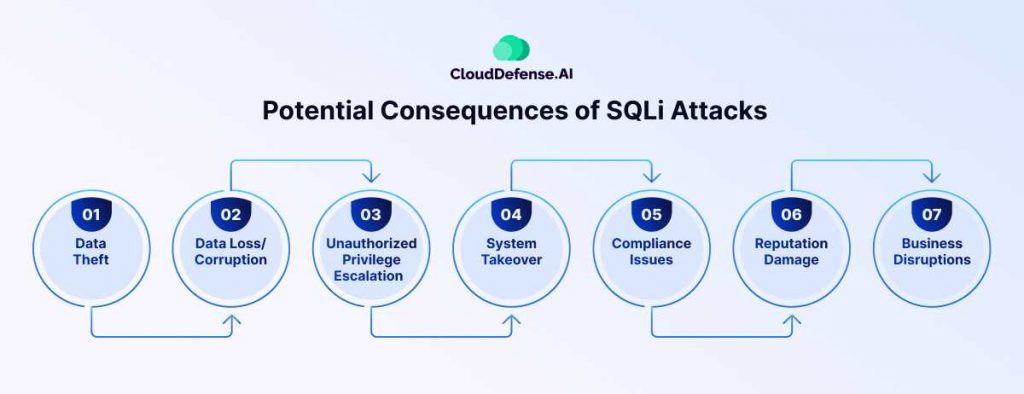
A successful SQL injection can have devastating impacts, both for the target organization and the individuals whose data is compromised. The potential consequences include:
Data Theft
This is one of the primary goals of SQLi – extracting sensitive data directly from the database. Customer records, financial information, intellectual property, authentication credentials…nothing is off limits. Data is the lifeblood of most businesses, and having it stolen can be crippling.
Data Loss/Corruption
Besides extraction, attackers can maliciously modify or straight up delete data stored in the backend database via injection attacks. Wiping out transaction logs, user accounts, vital records – this sabotage can bring operations to a grinding halt.
Unauthorized Privilege Escalation
Some SQLi payloads allow attackers to gain admin-level permissions, giving them complete control over the database and potentially the entire application stack running on the server.
System Takeover
Advanced injections may provide enough of a foothold for full system compromise, allowing the installation of rootkits, backdoors, and other malware to persist access indefinitely.
Compliance Issues
For regulated industries like healthcare and finance, a data breach from SQLi could violate major compliance requirements like HIPAA or PCI-DSS, resulting in hefty penalties.
Reputation Damage
Brand trust and customer loyalty plummet when private data is exposed and systems are visibly compromised. The PR fallout from a major SQLi incident can linger for years.
Business Disruptions
Extended database downtown, lost transactions, denial of service – these operational disruptions translate directly into lost revenue and productivity if systems are crippled.
So in summary, while the injected payload itself may be small, the potential blast radius of a successful SQL injection attack is massive – from total data compromise to full system ownership and compliance chaos. It’s a threat that must be taken extremely seriously.
Best Practices to Prevent SQLi Attacks
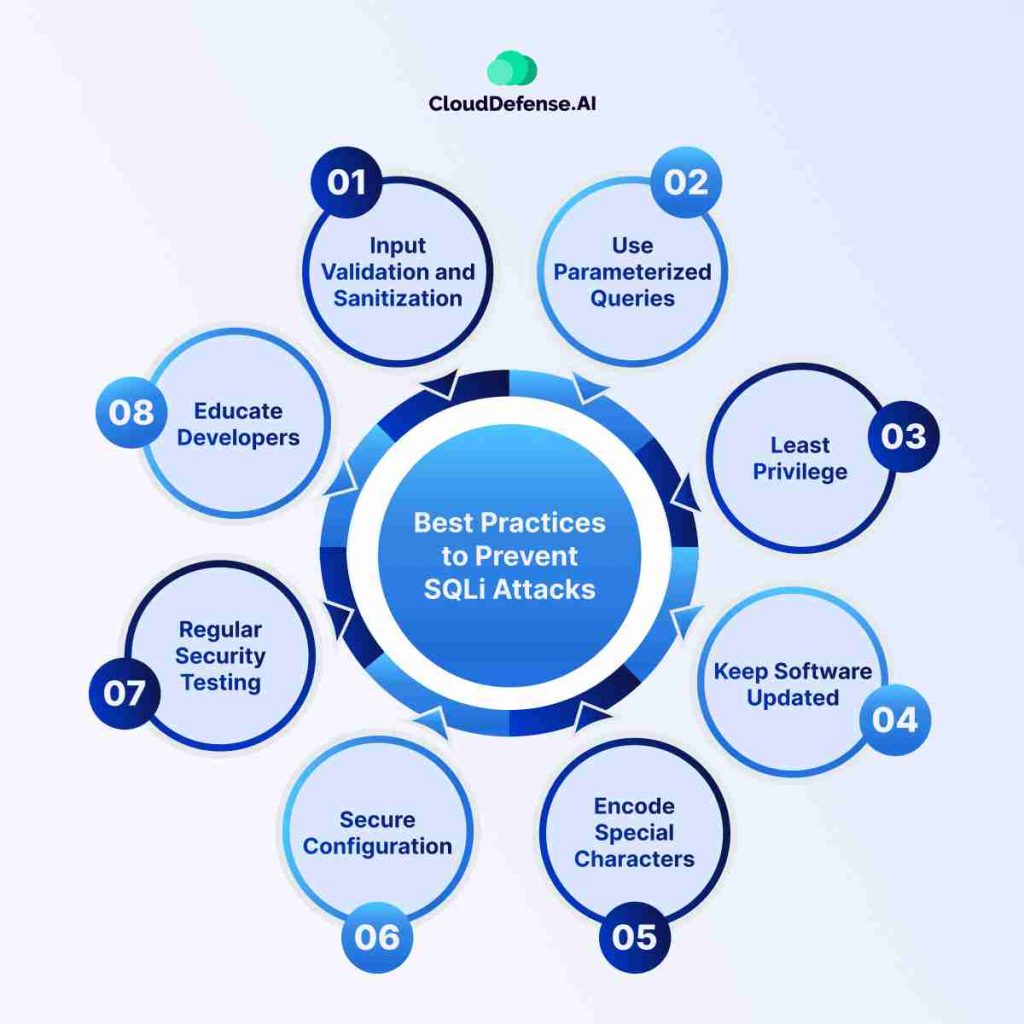
Protecting against SQL injection attacks requires a proactive approach that combines secure coding, system configuration, and continuous monitoring. The following best practices are essential to minimize vulnerabilities and ensure your applications and databases are resilient against SQLi threats.
- Input Validation and Sanitization: This is the first line of defense. Always validate and sanitize all user input before incorporating it into database queries. This means examining the data to ensure it conforms to the expected format (e.g., only numbers for a numeric field) and removing any potentially harmful characters that could be used for SQL injection.
- Use Parameterized Queries: Parameterized queries are a secure way to construct SQL statements. Instead of building the query string by concatenating user input directly into the SQL code, use placeholders for the data. The database server then handles inserting the data securely into the query. This prevents malicious code from being interpreted as part of the SQL statement.
- Least Privilege: Grant database accounts the minimum privileges required to perform their designated tasks. For instance, if an application only needs to read data from specific tables, avoid granting it update or delete permissions. This way, even if an attacker gains access to a compromised account, the potential damage is limited.
- Keep Software Updated: Ensure your database software and web application frameworks are up-to-date with the latest security patches. These patches often address known vulnerabilities that attackers might exploit.
- Encode Special Characters: When pulling data from the database to display on your site, make sure to encode those special characters properly. We don’t want angle brackets, quote marks or other sneaky stuff getting misinterpreted as HTML and opening up cross-site scripting (XSS) issues alongside potential SQLi.
- Secure Configuration: Follow recommended security practices when configuring your database server. Disable unnecessary features and functionalities that could introduce vulnerabilities. Additionally, use strong passwords for database accounts and avoid using generic accounts like “sa” or “admin”.
- Regular Security Testing: Regularly conduct security assessments of your web applications to identify and address potential SQL injection vulnerabilities. There are automated tools available to assist with this process, but manual penetration testing can also be valuable.
- Educate Developers: Developers who understand the dangers of SQL injection and how to prevent it are less likely to introduce vulnerabilities into their code. Provide training and resources to developers on secure coding practices and best practices for building applications that are resistant to SQL injection attacks.
Final Words
The alarming reality of SQL injection attacks should shake organizations to their core. This stealthy technique provides hackers with a direct pipeline into your most precious data reserves. With just a few lines of malicious code, they can extract, manipulate, or obliterate everything, from customer records to financial data.
Also, the examples in this article must serve as a deafening wake-up call. SQL Injection is widespread, successful, and utterly avoidable with robust security practices. Harden your defenses now or inevitably join the thousands affected annually.







