What is SOC 2 Compliance?
SOC 2 compliance is a set of security standards for organizations that manage sensitive customer data, ensuring they maintain strict controls over data privacy and protection.
What SOC 2 Compliance Does:
- Ensures data security, privacy, and confidentiality.
- Verifies integrity of systems and processes.
- Protects against unauthorized data access.
- Monitors and audits data handling regularly.
- Promotes transparency and accountability in data management.
History of SOC 2 Compliance
SOC 2 (System and Organization Controls 2) was developed by the American Institute of Certified Public Accountants (AICPA) in 2011. It was created to help service organizations safeguard the privacy and confidentiality of customer data, particularly in the growing field of cloud computing.
SOC 2 evolved from the earlier SOC 1 framework, which focused on financial controls, expanding its focus to include criteria related to security, availability, processing integrity, confidentiality, and privacy.
Over the years, SOC 2 Compliance has become a widely recognized standard, especially for SaaS (Software as a Service) companies, as it helps build trust between organizations and their customers by proving adherence to rigorous data security practices.
Why SOC 2 Compliance Matters?
SOC 2 compliance is critical because it’s about trust. When customers share sensitive data, they need to know it’s in good hands. By meeting SOC 2 standards, a company shows it takes security seriously — protecting that data from leaks, hacks, or misuse. Without it, the risk of breaches and reputational damage skyrockets.
In today’s world, data protection is non-negotiable. For businesses in tech, healthcare, or finance, SOC 2 Compliance isn’t just a luxury, it’s a requirement. If you’re not compliant, you’re falling behind.
And as breaches get more sophisticated, that’s a dangerous place to be. SOC 2 compliance signals to clients that your business can be trusted with their most sensitive information, and that’s priceless.
What is a SOC 2 Audit?
A SOC 2 audit is an assessment where an independent auditor checks whether a company’s controls meet SOC 2 Compliance standards for data security, availability, confidentiality, and more. Unlike other frameworks that come with strict, one-size-fits-all rules, SOC 2 Compliance gives companies the flexibility to build their own security controls based on the Trust Services Criteria that best fit their operations.
After the audit, the auditor issues a report detailing the company’s compliance status. Whether the company passed or not, the report will outline the auditor’s findings. There are a few possible outcomes:
- Unqualified: The company passed the audit, everything is in line.
- Qualified: The company passed, but there are some areas that need improvement.
- Adverse: The company didn’t pass the audit.
- Disclaimer of Opinion: The auditor couldn’t determine a clear answer due to insufficient data.
In short, a SOC 2 audit is a way to prove that the company isn’t just talking the talk but actually walking the walk when it comes to data security.
SOC 2 Principles Explained
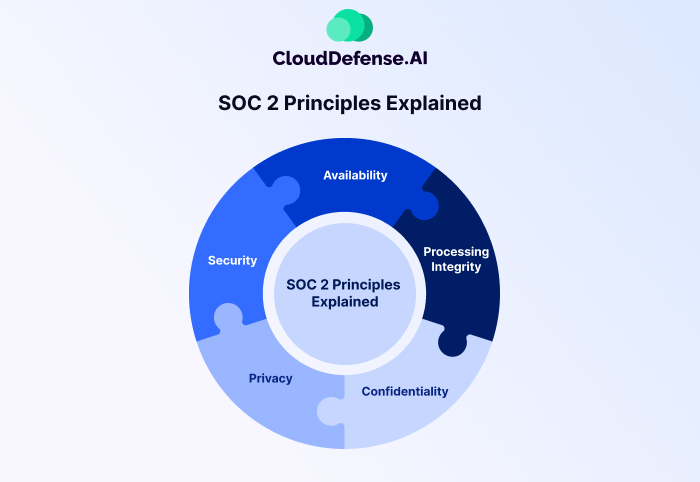
SOC 2 Compliance is built around five key principles. Let’s break them down in simple terms. If you’re wondering how these principles actually affect your business, you’re in the right place. These principles help ensure that your company is protecting customer data and managing it with care. Here’s what they are:
1. Security: How Safe Is Your Data?
Security is the foundation of SOC 2 Compliance. This principle focuses on keeping systems protected from unauthorized access, both physically and digitally. You might ask yourself, “How do we ensure our systems are safe?” Well, think about firewalls, encryption, and access controls. These are basic tools that prevent hackers from breaking into your systems. It’s about making sure your digital doors stay locked.
2. Availability: Is Your Service Always On?
SOC 2 Compliance isn’t just about preventing security breaches; it also ensures that your systems are up and running when your customers need them. Ever used a service that’s always down or super slow? Frustrating, right? Availability focuses on ensuring your systems are dependable, minimizing downtime, and offering customers a smooth, reliable experience. This principle asks, “Is your service there when it’s supposed to be?”
3. Processing Integrity: Is Your Data Being Processed Correctly?
Processing integrity means making sure that the data you handle is processed accurately and in the right order. Imagine ordering something online, and the system misplaces your order. Not ideal, right? That’s what this principle addresses—ensuring that all systems operate as intended without errors. It’s all about precision and getting things right the first time.
4. Confidentiality: Who Has Access to Your Sensitive Data?
Confidentiality is about keeping sensitive data safe from those who shouldn’t see it. Let’s be real—personal and financial info is incredibly valuable, and protecting it is non-negotiable. Think of it like a safe. This principle ensures that only authorized people have access to confidential information, making sure that customer data isn’t shared with the wrong eyes. It’s about keeping your promises to your clients that their data will be kept private.
5. Privacy: Are You Respecting User Privacy?
This one’s straightforward: Are you handling your users’ personal information responsibly? With data privacy laws tightening worldwide, respecting user privacy is more important than ever. It’s not just about protecting data; it’s about respecting users’ rights and making sure their personal details are used in a way they’ve agreed to. It’s about trust—ensuring that when customers give you their data, they know exactly what you’ll do with it.
Who Needs a SOC 2 Report?
If you’re in a business where data security matters—pretty much every industry these days—you probably need a SOC 2 Compliance report. Here’s who really benefits:
- Tech Companies: SaaS, cloud services, or anyone who handles a lot of sensitive data needs to prove they take security seriously. Think about all the sensitive information you’re storing—clients need to know you’ve got it covered.
- Healthcare Providers: Health data isn’t just sensitive; it’s critical. So, if you’re managing patient info or working with healthcare organizations, SOC 2 is a must to stay compliant and build trust.
- Financial Services: Whether you’re a bank, an insurance company, or any fintech startup, handling financial data requires top-tier protection. SOC 2 Compliance is what tells clients you’re doing it right.
- E-commerce Businesses: If you’re dealing with online transactions, payment processing, or storing customer data, SOC 2 gives your customers peace of mind. After all, who wants to buy something online if they’re not sure their card info is safe?
- Third-Party Vendors: If your business relies on partners for things like data storage or IT services, they’ll want to know you’re SOC 2-compliant. It’s about trust.
- Startups and Growing Companies: When you’re scaling, showing that you’ve got security locked down is critical. Investors and clients expect it.
- Big Companies with Client Requirements: If your clients demand high standards for data security, SOC 2 is the way to meet those needs and stay competitive.
Bottom line: if you’re managing sensitive information or dealing with any kind of client data, SOC 2 Compliance is a necessary step to show that you’re taking security seriously. It’s about trust, compliance, and keeping your operations in check.
What are the Benefits of a SOC 2 Audit?
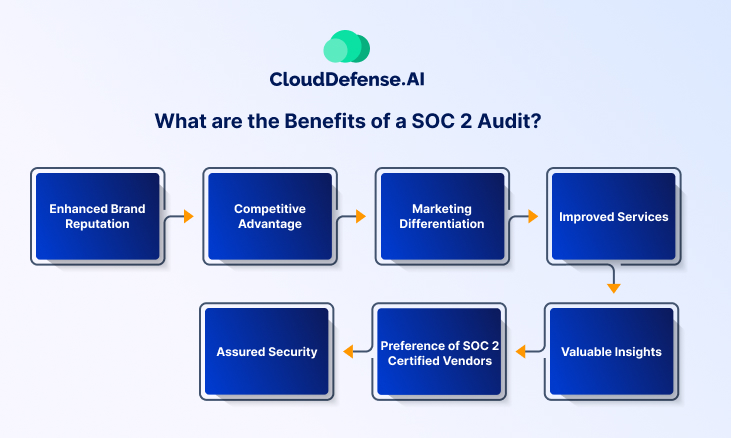
SOC 2 compliance stands as a crucial assurance to all stakeholders involved with a company. Below, you can find seven benefits of SOC 2 audits, highlighting their significance for organizations dedicated to upholding data integrity and trust.
Enhanced Brand Reputation
Achieving SOC 2 compliance demonstrates to customers and clients that your organization takes data security seriously, bolstering credibility and enhancing brand reputation in the marketplace.
Competitive Advantage
Holding a SOC 2 Compliance certification sets your business apart from competitors by showcasing your commitment to security and compliance, making you a preferred choice for clients seeking trustworthy vendors.
Marketing Differentiation
SOC 2 Compliance certification is a powerful marketing tool, allowing you to differentiate your organization from others in the market by showcasing adherence to rigorous security standards that others may not meet.
Improved Services
Undergoing a SOC 2 audit enables your organization to identify and address cybersecurity risks more effectively, leading to improved security measures and operational efficiency.
Assured Security
SOC 2 compliance assures clients that your organization has implemented robust security measures to prevent breaches and protect their data, fostering trust and confidence in your services.
Preference of SOC 2 Certified Vendors
Many businesses prefer to work with SOC 2 certified vendors, giving your organization a competitive edge and increasing opportunities for business growth and partnerships.
Valuable Insights
Through the SOC 2 audit process, your organization gains valuable insights into its risk and security posture, vendor management practices, internal controls, and regulatory compliance efforts, enabling informed decision-making and continuous improvement.
SOC 2 Type 1 vs. Type 2
You’ve probably heard the terms SOC 2 Type 1 and SOC 2 Type 2, but what’s the difference? Let’s break it down simply.
SOC 2 Type 1:
Think of SOC 2 Type 1 as a snapshot of your security practices at a specific moment in time. It’s like taking a picture of your systems and processes to show you’ve got things in place to meet SOC 2 standards. Type 1 focuses on whether your controls are designed correctly to meet the Trust Services Criteria. But here’s the catch: it doesn’t verify if they actually work over time. It’s more about showing that you’ve built the right security foundations.
SOC 2 Type 2:
SOC 2 Type 2 goes beyond just the design of your controls—it’s a report on how well those controls are working over a period of time, typically 6 to 12 months. This is where the real test happens. Type 2 audits show whether your security processes and systems are not just in place, but effective over time. This is the gold standard for most clients because it proves consistency and reliability, not just intent.
Key Difference: Time and Consistency
Type 1 shows that you’ve got things set up properly, while Type 2 shows that you’ve been maintaining those standards over time. Type 2 is often seen as more robust because it shows that your systems and controls aren’t just theoretical—they’re practical and effective in real-world conditions.
Which One Do You Need?
If you’re just starting out or need to get compliant fast, Type 1 is a great starting point. But if you’re looking to build trust over time and prove that your systems are consistently secure, Type 2 is the gold standard.
SOC 1 vs SOC 2 vs SOC 3
SOC 1, 2, and 3 serve unique purposes in compliance assessments. SOC 1 centers on internal financial controls, whereas SOC 2 and 3 evaluate controls related to Trust Services Criteria. While SOC 2 reports are detailed and confidential, typically shared with selected parties under NDA, SOC 3 offers a public-facing summary of SOC 2’s attestation.
Here’s a concise breakdown of their differences:
| SOC 1 | SOC 2 | SOC 3 | |
| What it Reports on? | Internal controls over financial reporting | Security, Processing, Integrity, Availability, and Privacy Controls. | Similar to SOC 2 but easier to understand for the general public. |
| Who Uses it? | User auditor and their controller office. | Shared under NDA. | Available publicly to anyone |
| Evaluation Timeline | SOC 1 Type 1 happens at a certain point in time. SOC 1 Type 2 financial audit happens over a period of time. |
SOC 2 Type 1 happens at a certain point in time. SOC 2 Type 2 compliance audit happens over a period of time. |
SOC 3 report is only available in Type 2. The audit takes place over a period of time. |
| When to Get? | If the company’s activities affect the clients’ financial reporting. | If the company processes other types of data and not financial data. | If the customers look for transparency on the security control of a company. |
| Reporting | Provides a standard report that attests to compliance. | Provides a standard report that attests to compliance. | A marketing report that can be used to prove that SOC 2 compliance is available. |
Who Can Perform a SOC Audit?
When it comes to SOC audits, not just anyone can walk in and give you a stamp of approval. It’s a specialized job, and it requires a qualified professional who knows the ins and outs of SOC 2 standards.
Certified Public Accountants (CPAs)
The go-to experts for SOC audits are Certified Public Accountants (CPAs), but not just any CPA will do. You need one who is specifically licensed and has experience in performing SOC audits. These CPAs have the technical knowledge to evaluate your controls against the Trust Services Criteria and ensure you’re compliant.
Independent Third-Party Auditing Firms
SOC audits are typically conducted by independent firms that specialize in IT and security audits. These firms employ CPAs who have deep experience in SOC 2 and cybersecurity best practices. They work with you to evaluate your systems and controls, ensuring an unbiased, thorough audit.
Why Does Independence Matter?
Independence is key. An audit needs to be impartial and objective. That’s why these audits are done by external parties—not by anyone directly involved with your business operations. You want a fresh, neutral perspective to assess how well your systems actually protect data, not just how they’re designed to.
SOC 2 Audit Checklist
- Define Trust Services Criteria (TSC): Security, Availability, Confidentiality, Processing Integrity, Privacy
- Document Current Controls: List all security, availability, confidentiality, processing, and privacy controls
- Identify Gaps: Review current controls against SOC 2 requirements
- Implement Required Controls: Address any identified gaps and adjust policies or systems as needed
- Ensure Employee Training: Verify staff is trained on SOC 2 policies and procedures
- Review Third-Party Vendors: Assess any third-party relationships and ensure their compliance
- Conduct Risk Assessment: Identify and address potential risks in your systems
- Prepare for the Auditor: Gather all necessary documentation and evidence to support your controls
- Perform Internal Testing: Test your controls internally to ensure they’re functioning as expected
- Schedule the Audit: Arrange for a certified CPA or third-party auditor to conduct the SOC 2 audit
- Address Audit Findings: Review the audit report and address any weaknesses or improvements noted
This checklist will keep you on track for a smooth and successful SOC 2 audit process.
SOC 2 Compliance with CloudDefense.AI
You already know how important it is to achieve SOC 2 compliance for handling sensitive customer data, and instilling trust among your clientele. With CloudDefense.AI’s cutting-edge multi-cloud compliance management system, compliance becomes easy to manage.
We help you stay compliant by automatically assessing your resources against various industry standards. Tailor security practices with custom policies and frameworks, generating comprehensive reports instantly. With support for 20+ compliance frameworks including GDPR, HIPAA, and ISO, including SOC 2, CloudDefense.AI ensures comprehensive compliance from a single dashboard. Book a free demo with us now to test out our powerful compliance management tool and see for yourself!







