What is Security as Code (SaC)?
Security as Code (SaC) is basically a concept and approach that aims to incorporate security practices and controls into the software development lifecycle from the very beginning. Rather than having some security team do a review right before you ship new code, the developers themselves define security rules and policies as actual code files.
It’s like, you’re already writing code to build out features and functionality. But with SaC, you also write code that lays out your security requirements and run automated tests to verify those requirements are met. These security code artifacts live right alongside your regular application code.
For example, let’s say your app needs to enforce some strong password rules – minimum length, a mix of characters, no common words, the whole nine yards. Instead of just telling devs, “Hey, follow these rules,” you write those rules as code. Then, you integrate that security code into your CI/CD pipeline.
So anytime someone pushes changes for a new password field or updates password functionality, those changes automatically get tested against the predefined password security rules you coded. If the changes violate the rules, the tests fail and that code doesn’t get merged until the issue is fixed.
Benefits of SaC
- Shift-left security, identifying and mitigating risks early in the development lifecycle
- Consistent and automated security checks across the entire software supply chain
- Improved collaboration between development and security teams through shared tooling
- Scalable and repeatable security processes, minimizing manual efforts
- Increased visibility and traceability of security posture throughout the pipeline
- Faster time-to-market by integrating security into the existing development workflows
- Reduced overhead and costs associated with addressing security issues late in the cycle
Components of Security as Code
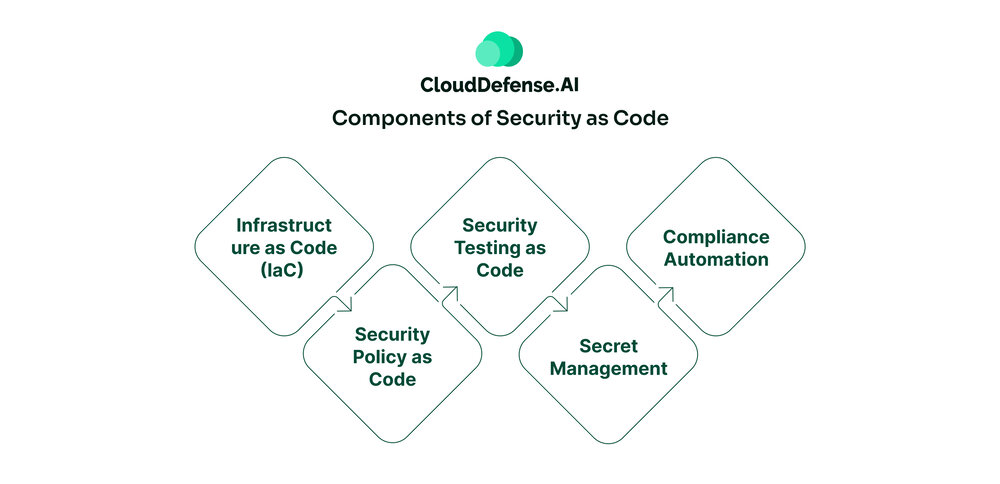
Security as Code brings together several different pieces to really make security an integrated part of how you build and deploy software. It’s like having security checks and guardrails baked into your dev process from start to finish.
Here are some of the main components that make it all work:
Infrastructure as Code (IaC)
This is kind of the foundation. With IaC tools like Terraform or AWS CloudFormation, you define all your infrastructure (networks, servers, etc.) as code files rather than clicking around a console. SaC plugs into this to automatically apply security best practices as you provision resources. Like your IaC scripts could ensure new cloud environments automatically get configured with locked-down security groups and firewalls.
Security Policy as Code
Instead of security being this vague concept, you translate it into explicit code-defined rules and policies. You might use a policy engine like OPA to write these policies in coding languages devs already know. Then you integrate those policies into your pipelines to enforce access controls, encryption standards, approved network configurations, and more across all your environments.
Security Testing as Code
Imagine every code change automatically gets security tested and scanned before it can get merged or deployed. That’s the idea here. You build security scanning tools like static code analysis or website vulnerability scanners directly into your CI/CD pipelines. They’ll flag any sketchy code or potential vulnerabilities in your apps early before they cause problems.
Secret Management
Dealing with sensitive credentials and secrets is always a pain. With SaC, you use tools like Vault or AWS Secrets Manager to store secrets in a secure place. Your pipelines can then fetch secrets on-demand during deployments instead of leaving them lying around in plaintext files.
Compliance Automation
Maintaining security compliance is a whole process, but SaC can help streamline it. You can actually map them to specific compliance requirements like PCI or HIPAA. Then you’ve got an automated paper trail showing policies were consistently enforced across all your environments.
How to Implement SaC?
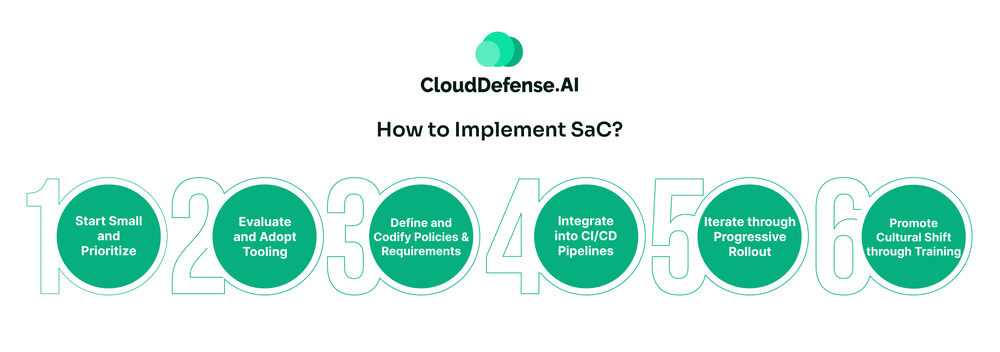
So you’re intrigued by this whole Security as Code thing and want to give it a try. Where do you even start with implementing it? Here’s a high-level overview of some of the key steps:
Start Small and Prioritize
You don’t need to boil the ocean right away. Pick one area of your app or infrastructure that has high security impact and start there. Maybe it’s securing your cloud environments with Infrastructure as Code. Or locking down secrets management. Or automating security testing for a critical service. Prioritize based on risk.
Evaluate and Adopt Tooling
There’s no one-size-fits-all SaC toolchain. You’ll need to evaluate and adopt the right tools for your roles, environments, and processes. For infrastructure security, you might use Terraform or AWS CDK. For policies, OPA or GitHub CodeQL. For secrets, HashiCorp Vault or Azure Key Vault. Don’t forget licensing and support costs.
Define and Codify Policies & Requirements
This is the critical part. You have to translate all those security requirements and compliance controls into actual machine-readable policies and rules. Maybe it’s password complexity rules or network segmentation policies. Use the policy-as-code tools to write these out.
Integrate into CI/CD Pipelines
Here’s where the actual work happens. Now you start plugging all those security rules, tests, and scans into your CI/CD pipelines and git repositories. Every code change and deployment needs to gate on passing these automated security checks.
Iterate through Progressive Rollout
Don’t try to convert everything to SaC at once. Iterate by securing one app, one environment, and one pipeline at a time. Check for gaps, get feedback, and fine-tune your tooling and processes. It’s a journey!
Promote Cultural Shift through Training
Ultimately, SaC is as much about the process as it is about technology. You need to educate your teams on security best practices, why these controls are important, and get organizational buy-in. Make it just how you build software securely.
Key principles of SaC
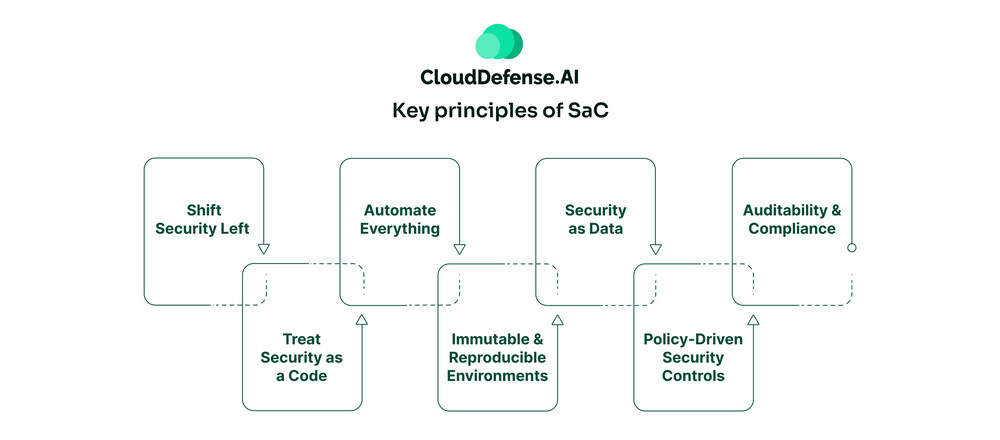
At its core, Security as Code is all about making security an inherent part of how you build and ship software, not an afterthought. A few key principles really define this approach:
Shift Security Left
The goal is to bake security in from the very start of the development lifecycle, not tack it on at the end. You want to find and fix security flaws in your code, configs, and environments as early as possible when they’re easier to address. Shifting security left saves you from costly rework down the line.
Treat Security as a Code
Just like devs write application code, security requirements and controls should be defined as machine-readable code artifacts that can be automatically validated. Security policies, test cases, compliance rules – they all get versioned and reviewed like regular code.
Automate Everything
Manual security reviews and audits don’t cut it. SaC is all about automating security checks and integrating them into your CI/CD pipelines and deployment workflows. Every change should be gated by automated security testing and policy validation.
Immutable & Reproducible Environments
With Security as Code, you want environments that are provisioned and configured in an immutable way from trusted deployment artifacts. Scripting everything as code makes environments reliably re-creatable in a secure, compliant state.
Security as Data
Not everything has to be coded! SecurityOps tooling allows you to codify and manage security data – vulnerabilities, misconfigurations, exceptions – in structured formats. This formalizes how you track and respond to security issues.
Policy-Driven Security Controls
Rather than hardcoding specific security controls all over your codebase, you define high-level security policies centrally as code. Automated enforcement of these policies gets applied across apps, infrastructure, etc.
Auditability & Compliance
With all security checks and controls formally codified and automated, you get a robust audit trail for compliance. It’s much easier to demonstrate and report on adherence to security standards.
Security as Code Technologies: Building Blocks of Secure Development
Modern development moves fast and so do security threats. That’s why “Security as Code” is essential. It’s about integrating security directly into your development process so that issues are caught early and fixed fast.
Below are the key technologies that make it all work:
- SAST (Static Application Security Testing): This tool scans your code and spots potential security vulnerabilities or coding blunders that could leave you exposed. SQL injection, cross-site scripting, buffer overflows—you name it, SAST will spot it before it even has a chance to cause trouble.
- SCA (Software Composition Analysis): Open-source components and third-party libraries make your development easy, but they can also be a security risk if you’re not careful. SCA helps you keep track of all those add-ons, identifying any potential vulnerabilities, licensing issues, or outdated versions that could turn into trouble.
- Vulnerability Scanning: This is a constant lookout for known security vulnerabilities in your apps, systems, or networks. It compares your setup against a massive database of security threats and gives you a heads-up on any potential risks, along with some solid advice on how to fix them.
- Infrastructure as Code (IaC) Security: Your infrastructure code is like the blueprint for your digital fortress, and IaC security makes sure there are no security flaws or compliance issues in those plans before you start building.
- Container Security: Containers are all the rage these days, but they can be a security nightmare if you’re not careful. Container security tools will scan those for vulnerabilities, enforce security policies, and keep a watchful eye on the container runtime to make sure nothing sketchy goes down.
- Secrets Management: Sensitive information like API keys and database credentials is like the keys to the network. Secrets management helps you keep those keys safe and sound by securely storing, rotating, and managing them throughout the development lifecycle and deployment environments.
CloudDefense.AI has all these security features as code technologies rolled into one single platform. We provide you with the tools and expertise to automatically scan, analyze, and secure your code, infrastructure, containers, and secrets from start to finish.
Final Words
To wrap this up, Security as Code is the real deal—a game-changer for anyone who wants to keep their codebase, infrastructure, and sensitive data locked down tight. With these powerful tools and practices, you can catch security issues early, automate vulnerability checks, and ensure compliance from the get-go.
And let’s be real, in today’s threat environment, you can’t afford to overlook security. So, embrace security as code, and rest easy knowing your digital assets are protected. Stay safe out there, and keep coding like a pro!







