Software Composition Analysis (SCA) Explained!
Software Composition Analysis (SCA) is a method used to identify and manage open-source and third-party components within software applications. It focuses on analyzing the software’s codebase to discover the libraries, frameworks, and modules in use, assessing their licenses, and identifying any known vulnerabilities.
In simpler terms, SCA scans your codebase to answer critical questions like:
- What’s in your code? What open-source components, both direct and indirect dependencies, are being used in your application?
- Are you compliant? Do any of these components have restrictive licenses that could pose legal issues for your project?
- Is it secure? Are there any known vulnerabilities in these components that could put your application at risk?
By providing insights into the software supply chain, SCA empowers developers and security teams to make informed decisions about the components they use, ultimately promoting safer and more compliant software development practices.
What Are the Risks of Using Open Source Components?
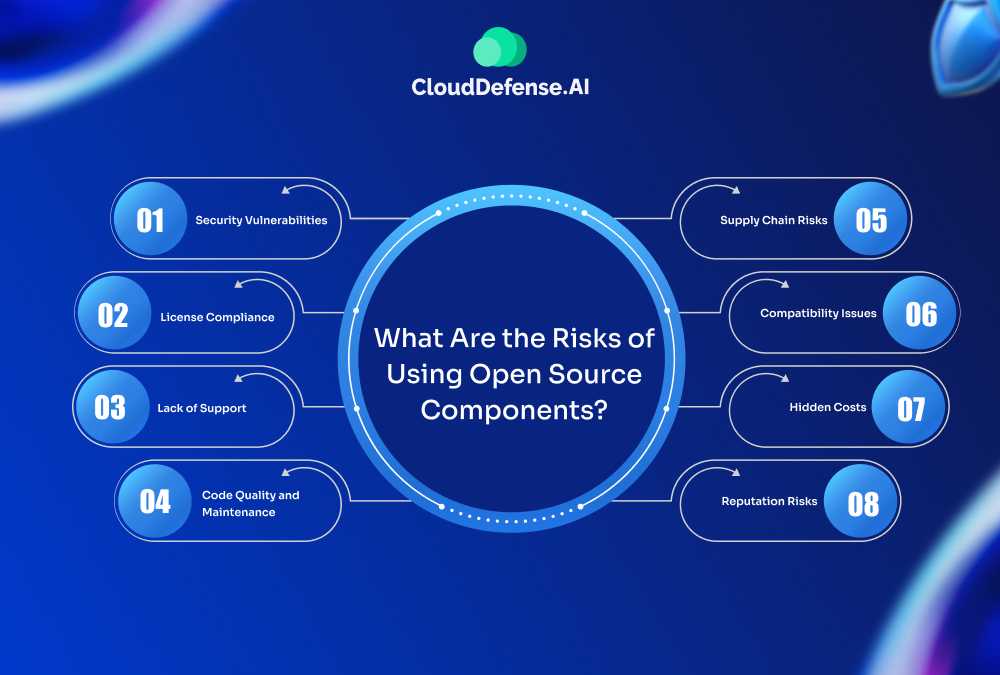
Using open-source components in software development can offer significant advantages, but it also comes with various risks. Here are some key risks to consider:
- Security Vulnerabilities: Open-source components can contain known vulnerabilities that, if exploited, can compromise your application. Regular updates and patches may not always be available, leaving systems exposed.
- License Compliance: Open-source software comes with specific licensing requirements. Failing to comply with these licenses can lead to legal issues, including potential lawsuits or fines.
- Lack of Support: Many open-source projects lack formal support. If you encounter issues, you might have to rely on community forums or documentation, which can be less reliable than dedicated support services.
- Code Quality and Maintenance: The quality of open-source components can vary widely. Some may be well-maintained and regularly updated, while others might be abandoned or poorly documented, leading to technical debt.
- Supply Chain Risks: Dependencies on open-source components can introduce supply chain vulnerabilities. If a component is compromised, it can impact all applications relying on it, potentially leading to widespread security issues.
- Compatibility Issues: As open-source components evolve, updates can introduce compatibility issues with your existing codebase, leading to unexpected bugs or system failures.
- Hidden Costs: While open-source components are often free to use, there may be hidden costs related to integration, maintenance, and potential security audits that can impact overall project budgets.
- Reputation Risks: Utilizing poorly regarded or insecure open-source components can affect your organization’s reputation, particularly if a breach occurs due to vulnerabilities in these components.
Why is SCA Important?
Imagine you’re developing a new web application, and, like many developers, you decide to leverage open-source libraries to speed up the process. You integrate a popular third-party framework to handle user authentication.
But here’s the catch: a few months ago, a severe vulnerability was discovered in that exact framework, and attackers are now using it to steal user data from any app that hasn’t been patched.
If you’re not actively monitoring your software’s components, you might not even know your application is at risk. This is where Software Composition Analysis (SCA) becomes crucial. SCA tools scan your codebase, flagging outdated or vulnerable components and alerting you to licensing issues. This way, you can address these risks before they become a problem.
Without SCA, you’re essentially flying blind. You could be exposing your users’ data, your company’s reputation, and even your compliance status without realizing it. SCA provides visibility and control, allowing you to build secure, reliable applications confidently
How Does Software Composition Analysis Work?

Software Composition Analysis (SCA) tools are like your vigilant security guard for open-source components, helping you spot and fix potential issues before they cause trouble. Here’s a quick breakdown of how it works:
1. Identifying All Components
SCA tools scan your application’s code to identify every open-source component in use. This goes beyond the libraries you directly add; it also uncovers transitive dependencies—those hidden components brought in by other libraries. It checks everything from package managers and source code to container images, binary files, and even the Software Bill of Materials (SBOM), providing a comprehensive map of what’s in your code.
2. Checking for Vulnerabilities
Once the components are identified, the tool cross-references them with databases like the National Vulnerability Database (NVD) or other trusted sources. It compares the versions you’re using with those flagged in vulnerability reports. If there’s a known security issue in your code, SCA will highlight it, showing you exactly where you’re exposed.
3. License Compliance
Not all open-source licenses are created equal. Some come with conditions that might conflict with your organization’s policies. SCA tools analyze the licenses of each component to ensure you’re not unknowingly violating any legal obligations or restrictions, helping you steer clear of potential legal headaches.
4. Actionable Fixes
It’s not just about identifying problems; SCA tools also provide solutions. They suggest patches, updates, or even alternative components to fix vulnerabilities. Plus, they offer insights on how to mitigate risks, making it easier to keep your software secure without starting from scratch.
5. Seamless Integration
SCA tools can plug into your existing development environment, whether it’s your CI/CD pipeline or version control system. This means you get real-time alerts and can address issues as they pop up during development, instead of dealing with them after your code is already out in the wild.
Did you know?
In 2023, cyberattacks on open-source software (OSS) supply chains skyrocketed to over 245,000— a 280% increase from the previous year! That’s more than double the total attacks from all previous years combined. Hackers targeted popular ecosystems like JavaScript, Java, .NET, and Python, looking to exploit vulnerabilities in these widely used frameworks. It’s a powerful reminder of how critical it is to stay cautious when using open-source components.
Benefits Of Software Composition Analysis(SCA)
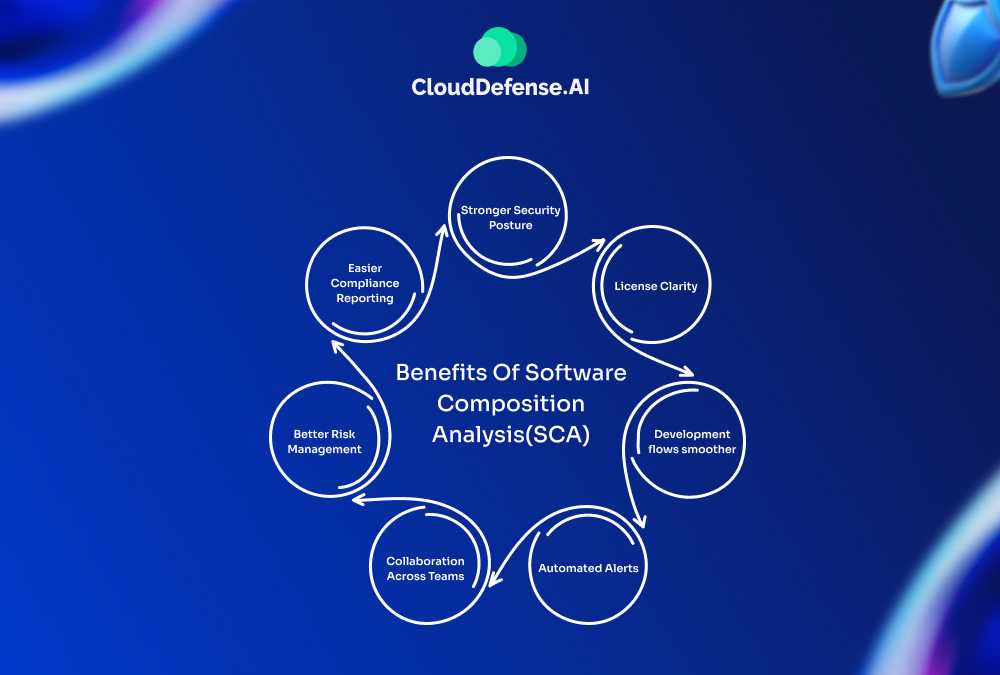
When you incorporate Software Composition Analysis (SCA) into your development workflow, you can experience benefits that go beyond just security.
- Stronger Security Posture: SCA helps you catch known vulnerabilities in open-source components, giving you the chance to fix these issues before they can be exploited. This proactive stance means you’re reducing the risk of data breaches and protecting sensitive information.
- License Clarity: Navigating the licensing maze becomes simpler. Open-source software comes with a variety of licenses, and keeping track of them can be tricky. SCA tools help clarify which licenses apply to the components in your application, ensuring compliance and saving you from potential legal headaches down the road.
- Development flows smoother: SCA provides developers with a comprehensive view of the libraries they’re using, allowing them to make informed choices. This knowledge reduces technical debt and sidesteps complications that could derail progress.
- Automated Alerts: Many SCA tools come with automated alerts that notify you about vulnerabilities. This means you can act quickly to fix issues instead of scrambling when a problem arises
- Collaboration Across Teams: SCA encourages teamwork among different groups like engineering, security, and compliance. When everyone is on the same page about the components being used and their risks, it leads to better decision-making and a unified approach to software security.
- Better Risk Management: With a clearer picture of open-source components and their risks, you can make smarter decisions about how to handle vulnerabilities. This leads to a more robust approach to risk management, contributing to the overall success of your projects.
- Easier Compliance Reporting: Generating a Software Bill of Materials (SBOM) gives you a clear view of all the open-source components in your application. This not only helps with compliance but also simplifies reporting during audits, making it easier to demonstrate that you’re playing by the rules.
How SCA Helps to Prevent Supply Chain Attacks
Open-source projects that are being used in supply chains are vulnerable to cyber-attacks. Threat actors use supply chain attacks to inject malicious code into the open source components.
When supply chain software runs these malicious components, exploits open up, resulting in cyber attackers getting access to the system.
SCA scans all resources the application is dependent on to detect any potential vulnerabilities that can be judged as risky for the whole supply chain. Helping to identify bad libraries created or manipulated by threat actors.
Software Composition Analysis (SCA) Challenges
Just like any other security components in the industry, there are some challenges that enterprises using SCA face.
- Open-Source Components Using Other Third-Party Resources: A lot of third-party resources have dependencies of their own, which go much deeper into the source code. These indirect dependencies can be harder to identify.
- Managing Vulnerabilities: It is important to make sure that the vulnerability databases are constantly updated with each new vulnerability being discovered. An outdated database still keeps the application at risk even after using SCA security tools.
- Different Languages, Different Dependency Handling: All applications are not developed using the same language, and therefore they also differ in how they handle their dependencies. An effective SCA tool should have a good understanding of different languages and how dependencies are deployed to identify any vulnerabilities.
Best Practices of Software Composition Analysis (SCA)
Here are some best practices that you can follow to overcome the challenges of using SCA.
Automating SCA Scans:
Automating your SCA scans is important to ensure an efficient workflow for your developers. It provides your developers with real-time updates on any existing vulnerabilities as well as tips on how you can fix them.
Shift Security Left in the SDLC
It’s crucial to bring security into the development process as early as possible. By integrating SCA tools from the start of the Software Development Life Cycle (SDLC), you can catch vulnerabilities and license issues while the code is being written, not after it’s already live.
This early detection saves time and money, reducing the cost of fixing issues and keeping the development process smooth.
Automate Policy Enforcement
Consistency is key, and automation is your best friend here. Set up automated policies within your SCA tool so it runs regular checks in your CI/CD pipeline. If a serious vulnerability or license issue is found, it can stop a build before it goes any further. This way, security checks are baked into your workflow without slowing things down or relying on manual oversight.
Stay on Top of Updates
Open-source components can quickly become outdated or unsupported, leading to potential security gaps. Make it a habit to regularly monitor the libraries you use, staying alert for new vulnerabilities. Set up a process to routinely update to the latest secure versions. By doing this, you’re not just fixing what’s broken—you’re preventing future issues.
Choosing a SCA Tool That Is Compatible With Your Developers:
Some software composition analysis tools can be hard to operate, which makes it difficult for developers to use. Consider choosing a tool like CloudDefense.AI that is user-friendly and compatible with other security assets that you have in your company.
Making SCA a Part Of The CI/CD Pipeline:
Security isn’t just the job of one team—it’s something everyone should be involved in. Make sure your development and security teams are on the same page and working closely together. Clear communication and shared goals around security help ensure that SCA is embedded in the development process and treated as a priority across the board.
CloudDefense.AI’s Approach to SCA
CloudDefense.AI takes Software Composition Analysis (SCA) to the next level, offering a well-rounded, powerful solution for open-source risk management. Here’s how we make a difference:
Comprehensive Coverage
CloudDefense.AI scans your entire software ecosystem, leaving no stone unturned. Whether it’s source code, container images, or dependencies you didn’t even know existed, it provides full visibility into every component in your stack.
Highly Accurate Results
No more guessing games. CloudDefense.AI delivers precise SCA results, minimizing false positives so you can focus on real issues. You’ll know exactly what vulnerabilities and licensing risks are present, saving time and reducing unnecessary fixes.
Deep Visibility into Vulnerabilities and License Risks
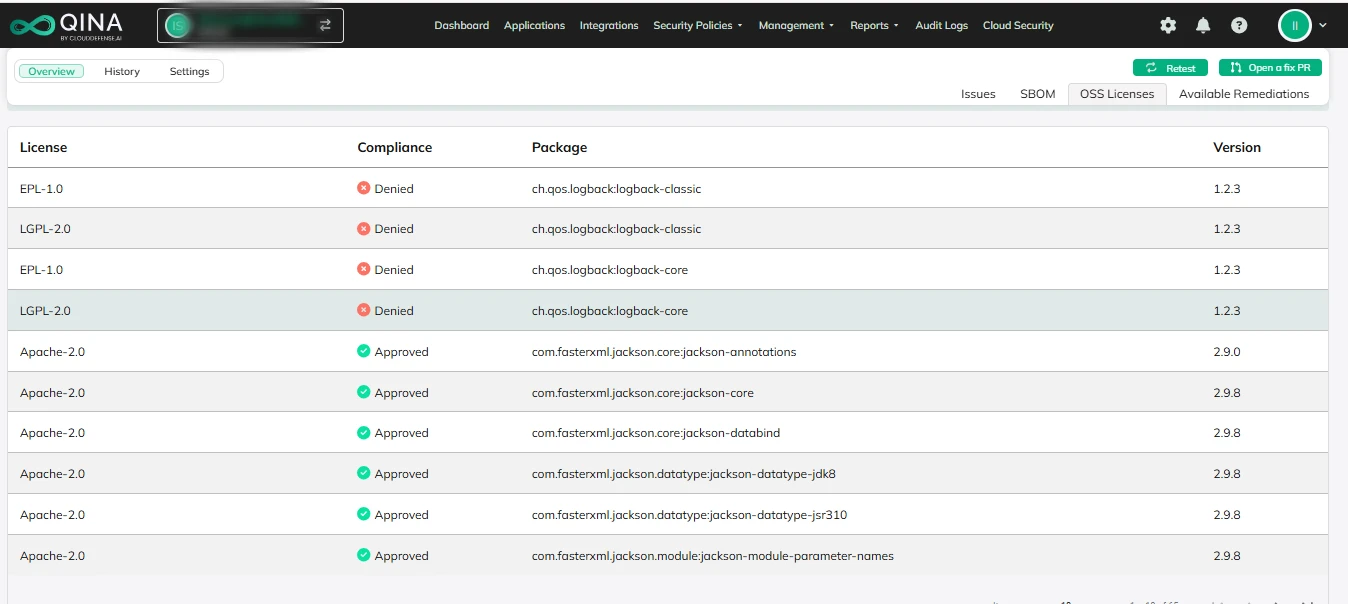
Their tool dives deep into the open-source libraries you use, offering clear insights into any vulnerabilities or legal risks associated with your components. You’ll get comprehensive reporting, giving you the clarity you need to stay secure and compliant.
Smart Integration into Your Workflow
CloudDefense.AI smoothly integrates into your CI/CD pipeline, allowing for real-time monitoring without disrupting your development process. It keeps everything running efficiently while staying on top of potential risks.
Actionable and Prioritized Remediation
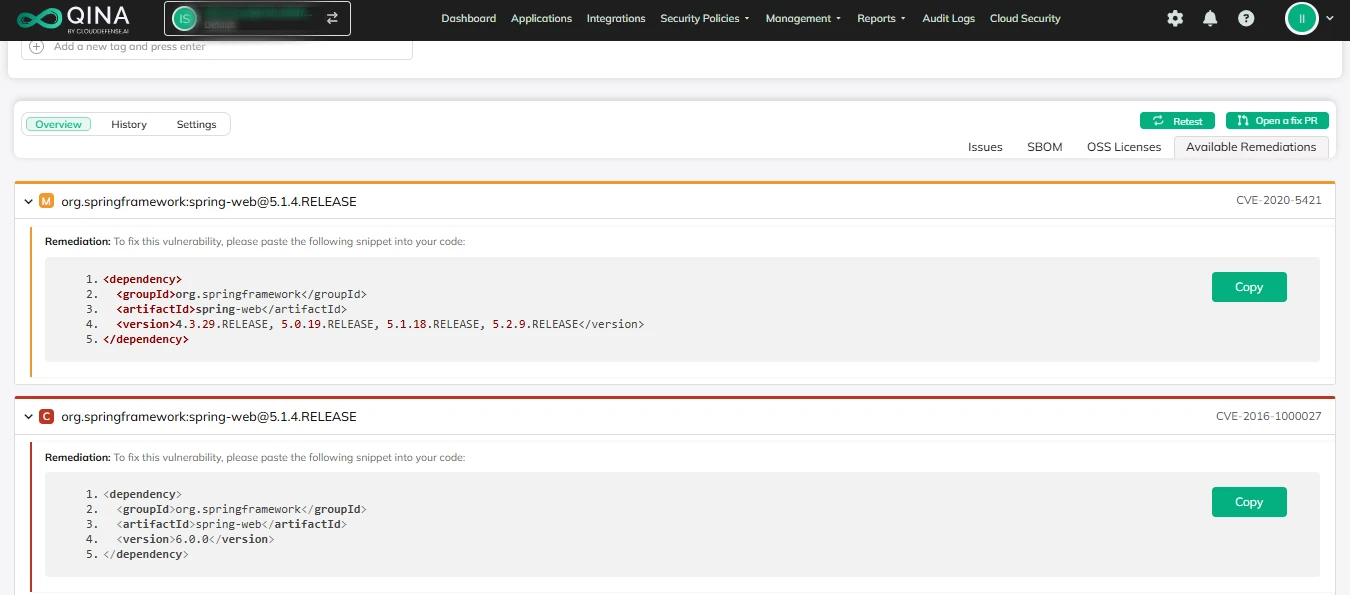
Not only does CloudDefense.AI tell you where the problems are, but it also provides clear, actionable steps to resolve them. Plus, it prioritizes remediation based on the exploitability of vulnerabilities, so you’re addressing the most critical issues first.
False Positive Management
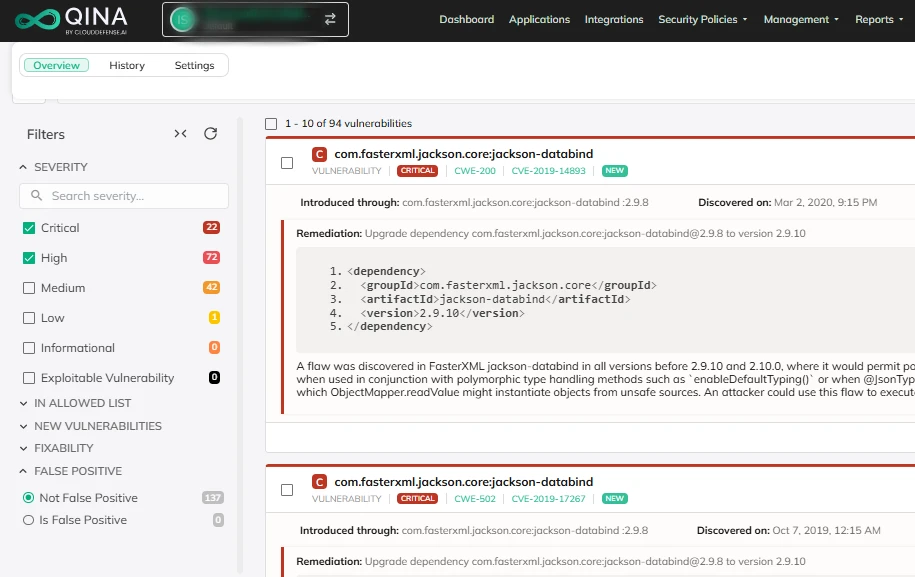
With built-in false positive management, CloudDefense.AI ensures you’re not wasting time chasing irrelevant alerts. It filters out noise, so you’re always working with accurate data.
FAQ
Who uses Software Composition Analysis solutions?
SCA solutions are utilized by a wide range of users, from individual developers to large enterprises, to detect any underlying vulnerabilities in open-source components. It is also used to manage software licenses that are required for compliance checks.
What are the future trends of Software Composition Analysis?
SCA is currently in use, as there is steady growth in the number of people using it. With more developers and security professionals becoming aware of the benefits, the software composition analysis market size is projected to double by 2027.
How to Choose a Software Composition Analysis Tool?
There are four major factors that you should consider when deciding on an effective software composition analysis tool. These include “Continuous monitoring”, “Language support”, “Integration”, and “Quality of Support”.
Conclusion
Throughout this article, we’ve covered the essentials of Software Composition Analysis (SCA)—why it’s so important, how it works, and what best practices can make the difference in securing your software. From spotting vulnerabilities early to automating compliance checks, SCA is all about making sure your open-source components don’t become a weak link. If you’re serious about tightening up your security, CloudDefense.AI offers an SCA tool built to do just that. Interested in seeing how it can work for your team? Book a free demo and find out how it can help protect your software without slowing you down.







