Definition — What Exactly is Remote Code Execution (RCE)?
Let’s consider a scenario: you’re using your favorite app, and out of nowhere, a hacker takes control of it—running their code instead of what’s intended. That’s Remote Code Execution (RCE) in a nutshell.
Why is this so dangerous? Because once inside, hackers can steal sensitive data, install malware, or even take over entire networks. RCE vulnerabilities are often the result of poorly secured software or unpatched systems. And here’s the shocking part: RCE attacks can happen without any action from the user.
Breakdown of the key terms:
Let’s simplify the jargon to help you understand Remote Code Execution better:
- Execution: Simply put, it’s the act of running the code. Once executed, the attacker gains control over the system.
- Remote: This means the attack happens over the internet or a network. The hacker doesn’t need physical access to your device.
- Code: Refers to instructions that computers follow to perform tasks. In RCE, hackers run their own malicious instructions instead of legitimate ones.
RCE Real-Word Example: The Microsoft Exchange Server Vulnerability
Let’s talk about a real-world example to show how dangerous Remote Code Execution (RCE) can be. In 2021, a massive RCE vulnerability was discovered in Microsoft Exchange Server—and it affected thousands of organizations worldwide.
What Happened?
Hackers exploited this vulnerability to attack thousands of organizations. The breach impacted over 30,000 businesses in the U.S. alone, with hundreds of thousands of servers around the world at risk. The attackers could gain full access to email accounts, steal sensitive data, and install malware on the servers.
Here’s how it unfolded:
The issue was found in Microsoft Exchange Server, which many companies rely on for email. Hackers used this flaw to send malicious code to the server, which then automatically executed. This gave them control over the server, allowing them to access emails and other confidential information. It was a massive problem because the attack didn’t require any user action, like clicking on a link or downloading a file.
Impact
- 30,000+ organizations affected in the U.S.
- 250,000 servers around the world at risk
- Over $1 billion in damages from the breach
This is just one example, and RCE vulnerabilities can be found in various software programs, including web browsers, media players, and even productivity suites like Microsoft Office.
How Remote Code Execution (RCE) Attacks Work
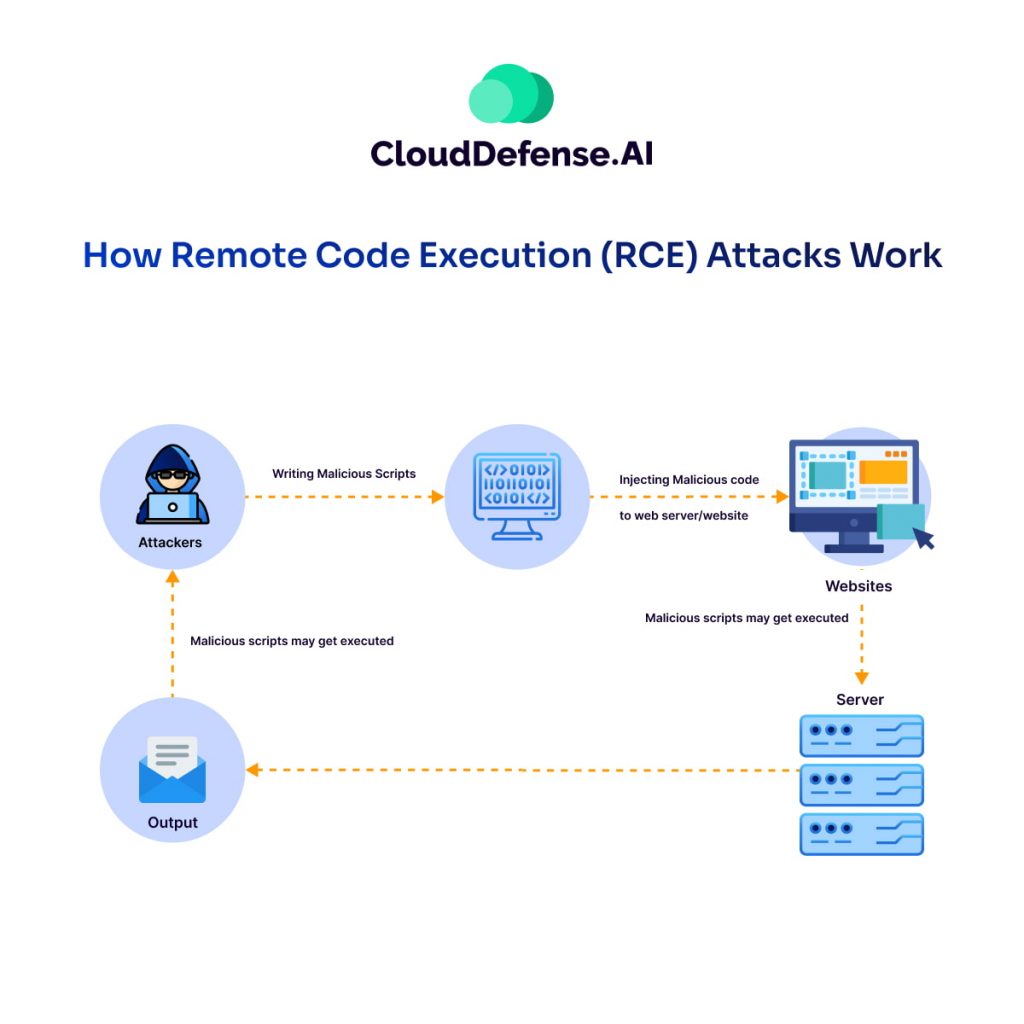
An RCE attack happens when a hacker takes advantage of a vulnerability in software or a system to run their own code remotely. Here’s how it typically plays out:
- Identifying a Vulnerability: Hackers start by scanning systems or applications for weak points—flaws in the code or unpatched software. These vulnerabilities act as entry points for their attack.
- Sending Malicious Code: Once they find a way in, the attacker delivers their malicious code. This could happen through a crafted URL, a malicious file, or even a network request.
- Executing the Code: The system or application unintentionally runs the attacker’s code, granting them control. From there, they can steal data, plant malware, or perform other harmful activities.
- Escalating Privileges: Once inside, hackers often escalate their privileges, allowing them to access critical system resources. At this point, they can control the entire system remotely.
What are the Impacts of RCE Attacks?
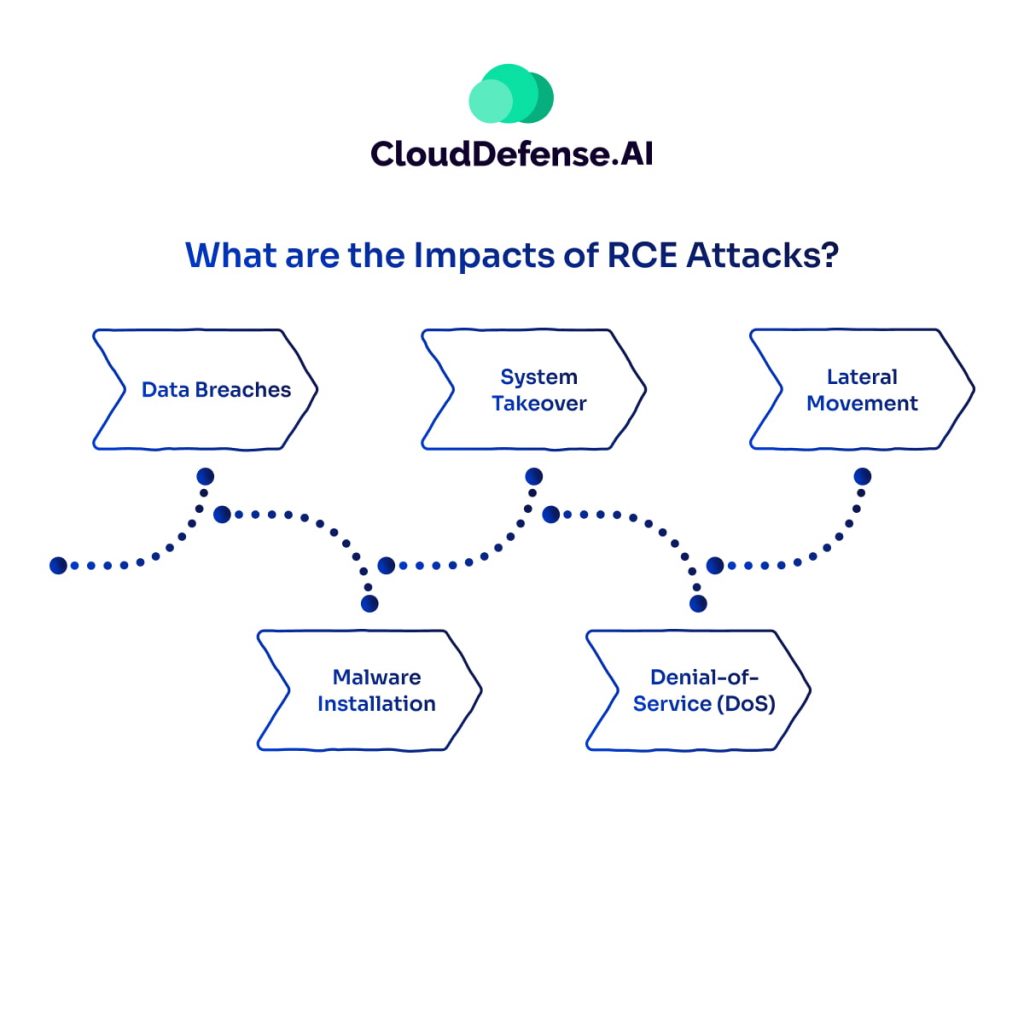
An RCE attack can trigger a chain reaction of issues, often resulting in severe consequences for organizations. Here’s what typically happens:
| Impact | Description |
| Data Breaches | Hackers can access and exfiltrate sensitive data, including customer details, internal documents, and financial records. This often leads to compliance violations, legal trouble, and customer mistrust. |
| System Downtime | Once attackers gain access, they can disable critical systems. This forces businesses to halt operations, causing significant revenue loss and productivity setbacks. |
| Denial of Service (DoS) Attacks | In some cases, RCE attacks are used to launch DoS attacks. Hackers flood the system with traffic, rendering services unavailable. This intensifies the disruption and adds another layer of complexity to recovery efforts. |
| Malware Deployment | RCE vulnerabilities are a common entry point for installing ransomware, spyware, or other harmful software, leading to further exploitation of the system. |
| Financial Losses | The costs of an RCE attack can escalate quickly. These include incident response, system repairs, data recovery, regulatory fines, and potential lawsuits. Some breaches cost organizations millions of dollars. |
| Reputation Damage | Public exposure of a security breach damages an organization’s credibility. Losing customer trust is a long-term problem that can take years to recover from. |
Types of RCE Attacks
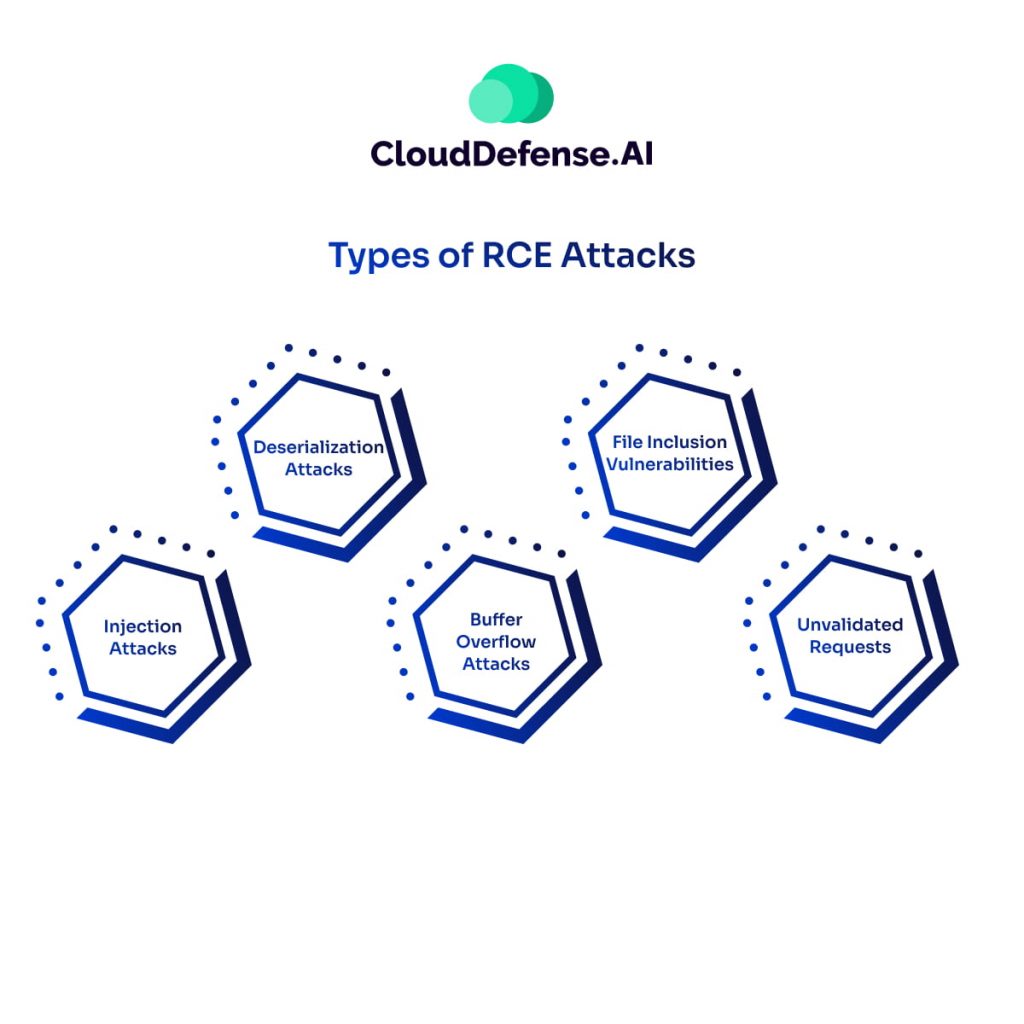
RCE attacks come in various forms, each exploiting different vulnerabilities in software. Here’s a breakdown of some common types:
- Injection Attacks: These are some of the most common RCE attacks. Here, attackers inject malicious code into user inputs processed by an application. The code can then be executed by the program, granting unauthorized access. Examples include:
- SQL Injection: Injects malicious code into database queries to manipulate data or gain unauthorized access to databases.
- OS Command Injection: Injects code into system commands, tricking the operating system into executing arbitrary commands.
- XSS (Cross-Site Scripting): Injects malicious scripts into web pages, which can then be executed by users’ browsers, potentially stealing data or redirecting users to malicious websites.
- Deserialization Attacks: These attacks exploit vulnerabilities in how applications handle serialized data. Serialization is the process of converting data structures into a stream of bytes for storage or transmission. If an application doesn’t properly validate deserialized data, attackers can inject malicious code that gets executed when the data is deserialized.
- Buffer Overflow Attacks: In some cases, attackers can exploit buffer overflows, which occur when more data is fed into a program than it can handle. This can overwrite existing memory locations and inject malicious code.
- File Inclusion Vulnerabilities: These vulnerabilities occur when applications read the contents of external files based on user input. Attackers can exploit this by crafting a specially crafted filename containing malicious code that gets executed when the application tries to read the file.
- Unvalidated Requests: Software that doesn’t properly validate user input can be tricked into processing malicious code. For example, a web application that doesn’t sanitize user search queries might be vulnerable to RCE attacks if a user enters a specially crafted search string containing malicious code.
Real-time Remote Code Execution Attack Vulnerabilities
Here are some of the notable RCE vulnerabilities discovered in recent years, along with their CVE (Common Vulnerability Enumeration) identifiers:
- Log4Shell (CVE-2021-44228): This critical vulnerability in the widely used Apache Log4j logging library sent shockwaves through the cybersecurity world in December 2021. It allowed attackers to remotely execute arbitrary code on affected systems with minimal effort. Due to Log4j’s prevalence, this vulnerability had a widespread impact.
- Microsoft Word RTF Vulnerability (CVE-2023-21716): As mentioned earlier, this 2023 vulnerability resided in Microsoft Word’s Rich Text Format (RTF) parser. Attackers could embed malicious code within an RTF document, which would then be executed upon opening, potentially granting them complete control over the victim’s machine.
- SolarWinds Supply Chain Attack (CVE-2020-10271): This wasn’t a classic RCE vulnerability, but it leveraged a vulnerability in SolarWinds Orion software to deliver malicious code updates to unsuspecting customers. This large-scale supply chain attack compromised numerous organizations.
- WannaCry Ransomware Attack (CVE-2017-0143): The infamous WannaCry ransomware attack of 2017 exploited a vulnerability in Server Message Block (SMB) allowing attackers to remotely execute malicious code and encrypt data on vulnerable systems. This attack caused significant disruption to businesses and organizations worldwide.
- Heartbleed Bug (CVE-2014-0160): The Heartbleed bug was a serious vulnerability in the OpenSSL cryptographic library that enabled attackers to steal sensitive information from the memory of vulnerable servers. While not a classic RCE in the sense of code execution, it did allow attackers unauthorized access to critical data.
How to Mitigate and Prevent RCE Attacks
RCE attacks can do major damage, but they’re avoidable. Here’s what you need to do to keep your systems secure, whether you’re a developer or running an organization.
For Developers:
- Sanitize Your Code: Always validate and sanitize data before letting it interact with your system. If you don’t, you’re opening a door for attackers.
- Update Everything: Old code is a prime target. Always use the latest versions of frameworks, libraries, and dependencies. Vulnerabilities get patched—keep things current.
- Secure Authentication: Require strong logins. Two-factor authentication (2FA) is an easy win that can stop many attacks right in their tracks.
- Limit Access: Don’t give users or systems more access than they need. If someone gains unauthorized access, limiting their permissions helps minimize damage.
- Test Early and Often: Run security tests regularly. Use tools to catch vulnerabilities before they become a problem. It’s much cheaper to fix bugs early than to deal with the fallout later.
For Organizations:
- Patch Everything: Apply updates as soon as they’re available. Many RCE attacks exploit known vulnerabilities, which are often patched in new versions of software.
- Use Web Application Firewalls (WAFs): WAFs block malicious input before it reaches your systems. Think of it as an extra layer of protection that can stop attacks before they even start.
- Monitor Systems: Set up real-time monitoring for unusual behavior. If you spot odd activity early, you can prevent a lot of damage.
- Use Intrusion Detection Systems (IDS): IDS alerts you when someone’s trying to break in. Responding fast can make all the difference.
- Train Your Team: Security is everyone’s job. Educate your team to recognize threats and follow best practices for handling sensitive data and access.
- Backup Your Data: Always have recent backups. If things go wrong, you’ll be able to recover quickly and reduce downtime.
Being proactive is the key to stopping RCE attacks. Developers need to write secure code, and organizations must stay vigilant and keep everything up-to-date.
Final Thoughts
RCE attacks are serious, but with the right practices, you can prevent them. By being proactive—keeping software up to date, writing secure code, and monitoring for unusual activity—you can stop these attacks before they happen.
For organizations looking to improve their security posture, CloudDefense.AI offers a comprehensive solution that helps detect and prevent threats like RCE vulnerabilities in real time. Our AI-powered CNAPP platform simplifies threat detection, enabling businesses to respond faster and minimize risks. Don’t wait until it’s too late. Sign up for a free demo today and see how we can help you build a stronger security posture against RCE attacks and other evolving cyber threats.







