What Is Network Segmentation?
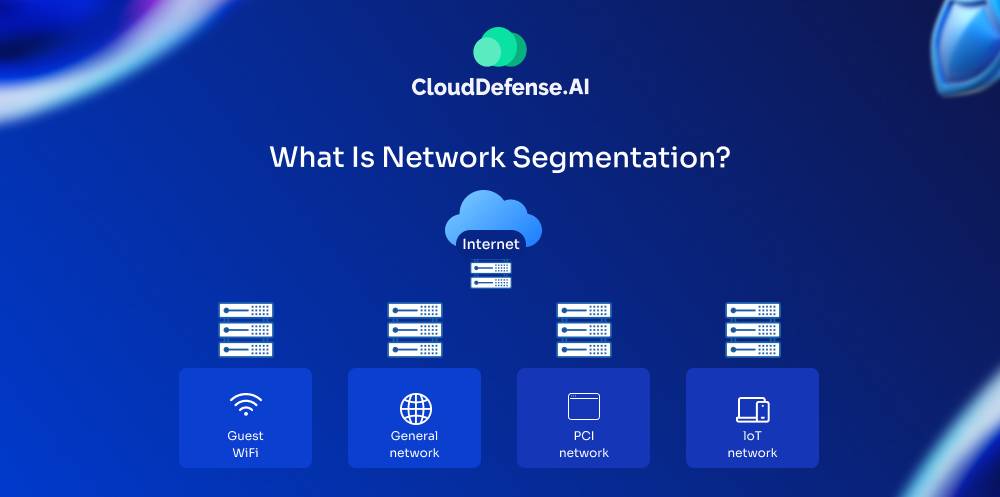
Let’s consider your company’s network as a big open office space – everyone and everything is connected and can access each other freely. While convenient, it also means one security breach or network issue could spread like wildfire through the whole place unchecked.
The network segmentation concept is like putting up dividers and partitions to create separate work areas or neighborhoods within an office space. You’re basically sorting things into different zones based on requirements, security levels, or operational roles.
For example, you might have one zone for the finance team dealing with highly sensitive data, another for regular employees, and maybe a separate visitor’s area. With segmentation, you control exactly who and what can access each zone. If there’s an issue in one area, it’s contained and can’t jump easily to the other zones.
It’s not just about security, though. Segmentation reduces congestion and bottlenecks by containing traffic flows within their respective zones. It’s a smart way to organize your network infrastructure logically based on operations, security needs, or even physical locations.
The methods can vary, but the idea is to use firewalls, VLANs, access control lists, and other security controls to draw those logical boundaries and divide your network into tighter neighborhoods. It’s a vital part of modern network security and management.
Key Benefits of Network Segmentation
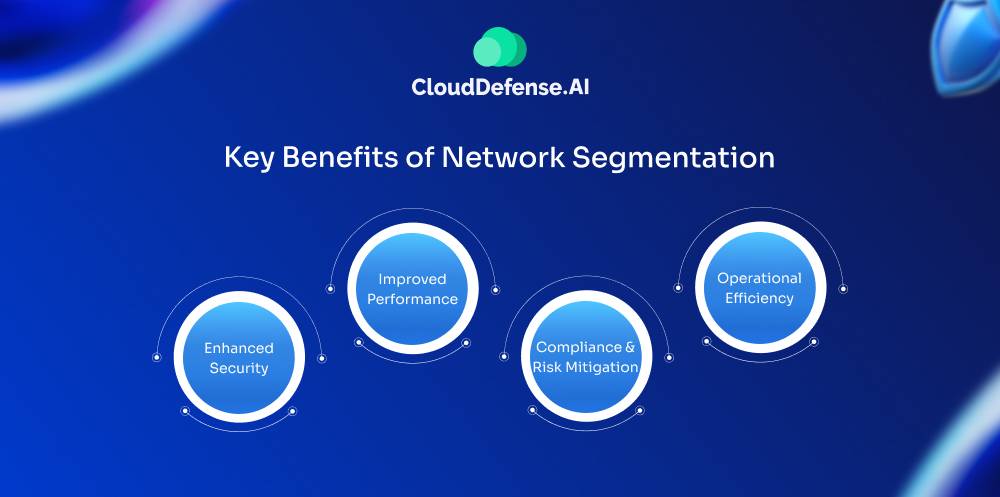
Enhanced Security
As we already discussed, one of the main reasons why network segmentation is so important is for security. Without dividing your network into parts, if a hacker or malware gets into your network, they can potentially go sideways and harm other systems and information all over your whole computer setup. Segmentation contains threats to their specific segment, preventing further spread.
It allows you to enforce stringent access controls for sensitive segments like financial databases or servers hosting confidential data. Only authorized users and devices that belong in that protected zone can talk to these vital resources. This significantly reduces your attack surface.
Improved Performance
In an unsegmented or “flat” network, broadcast traffic from every device is sent throughout the whole network infrastructure. When this network is divided into segments, it helps to limit the noise from these broadcasts, thus improving the overall performance and reducing traffic jams.
It also allows you to have more detailed control over the use of bandwidth. With this control, you can make certain vital operations get more bandwidth than other less important ones, rather than having to handle non-important traffic for all over the network.
Compliance and Risk Mitigation
Many regulatory standards like PCI-DSS, HIPAA, etc. require adequate segmentation of networks handling sensitive data. Proper network zoning helps organizations meet these compliance requirements.
Segmentation also helps to decrease possible dangers by keeping any problems or breaks within a certain separate part, reducing the effect on the rest of the system.
Operational Efficiency
From an operational standpoint, network breakdown makes things more logical and straightforward. You can put together groups of users, apps, servers, etc., into specific segments based on their roles, access requirements, and IT management needs.
This method makes things easier to manage, give access, apply rules, and fix issues within each separated area compared to a difficult wide network.
Types of Network Segmentation
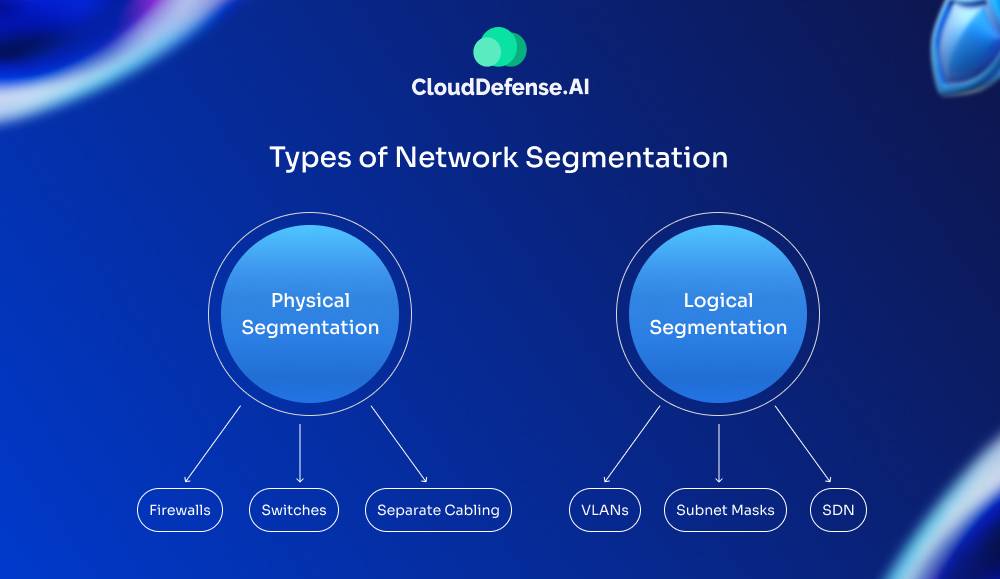
There are two main approaches to network segmentation, each with its own advantages and considerations:
Physical Segmentation
This method creates isolated network segments using dedicated physical hardware. Here’s a breakdown of the key components:
- Firewalls: These work like gatekeepers, managing the traffic flow between different parts of a network. They check both incoming and outgoing data packets to make sure only permitted traffic can go through.
- Switches: These smart tools decide the route for data packets traveling in a network. When it comes to physical segmentation, switches are set up to block any unauthorized communication between different parts of the network segments.
- Separate Cabling: Using separate physical cables can form totally isolated network parts, providing the maximum safety level for physical security.
Logical Segmentation
This approach leverages software-based solutions to create virtual sub-networks within the existing physical infrastructure. It’s a more flexible and scalable approach compared to physical segmentation. Here are the prominent methods:
- Virtual Local Area Networks (VLANs): VLANs logically group devices in a physical network based on things like department, job function, or security needs. They act as virtual walls and control the flow and conversation between different VLANs.
- Subnet Masks: The process of subnetting splits a big network address block into smaller parts, these parts are called subnets. This method gives more detailed control over how IP addresses are assigned and who gets access to a part of the network.
- Software Defined Networking (SDN): SDN is a way to manage networks by programming methods. It lets network managers set and keep rules for dividing the whole network space through software, which gives more chances to change and automate things.
Who Needs Network Segmentation?
The real question is, who doesn’t need it these days? Network segmentation is pretty much a must-have for organizations of all sizes and across all industries. Here are the questions to ask yourself:
- Does your organization deal with sensitive data, like financial records, healthcare information, or intellectual property?
- Do you have a network with a mix of devices, including desktops, laptops, servers, and Internet of Things (IoT) gadgets?
- Is your business required to comply with industry regulations or data privacy laws?
If you answered yes to any of these questions, then your network could benefit from segmentation. Here’s why:
Any Business Handling Sensitive Data
If your organization deals with sensitive customer information, financial records, healthcare data, intellectual property, etc., you can’t afford to have that data exposed across an open, flat network. Segmentation allows you to silo off and lock down access to only those authorized systems and users.
Companies Facing Compliance Mandates
Various industry regulations like PCI-DSS, HIPAA, GDPR and more have strict requirements around network segmentation and access controls. Proper segmentation helps organizations meet these compliance obligations.
Enterprise Networks
Large enterprise environments with multiple departments, global offices, and diverse technology stacks really benefit from logical segmentation. It provides more organized, granular control while enhancing security.
Cloud Environments
As businesses increasingly move workloads to the cloud, provider-native segmentation tools like AWS VPCs and Azure VNETs allow them to replicate on-premises micro-segmentation in the cloud.
Operational Technology Networks
Manufacturing facilities, utilities, oil/gas operations etc. rely on operational technology (OT) networks. Segmenting these industrial control systems from the corporate IT network is crucial for safety and security.
Even smaller businesses and home networks can leverage segmentation capabilities in modern routers/firewalls to separate personal devices from IoT gadgets or guest networks.
Final Words
At the end of the day, reducing attack surfaces and limiting breach fallout is a universal need. This is why network segmentation has become an indispensable practice for any environment where security, compliance, and operational efficiency are priorities. Basically, it’s a must-have for any business that doesn’t want to get hacked and lose all its precious info. Its like saying “not today” to cyberattacks and creating a more secure digital crib for your business.







