What is Network Security?
Network security indicates the technologies, procedures, policies, and devices that are involved in protecting your network and data from cyberattacks, intrusion, and data loss. In other words, it can be described as the set of rules and configurations that are implemented to protect the integrity, accessibility, and confidentiality of the network and data using various technologies.
It is also responsible for safeguarding the traffic and all the network assets residing within the perimeter and at the network edge. Network security covers a wide range of aspects that include access control, antivirus software, network analytics, VPN security, application security, firewall, endpoint security, web security, and others.
Nowadays, almost every organization requires network security to protect themselves from modern cyber threats, which include attacks backed by automation and artificial intelligence. With the addition of IoT in the network and network architecture growing rapidly, overall complexity is increasing day by day.
Modern networks are constantly under threat, and attackers always look for loopholes and vulnerabilities to exploit them. These vulnerabilities are present in different areas that not only include network devices but also data, users, locations and applications. To prevent growing attack vectors and address exploits along with regulatory non-compliance, network security serves as the best solution.
How Does Network Security Work?
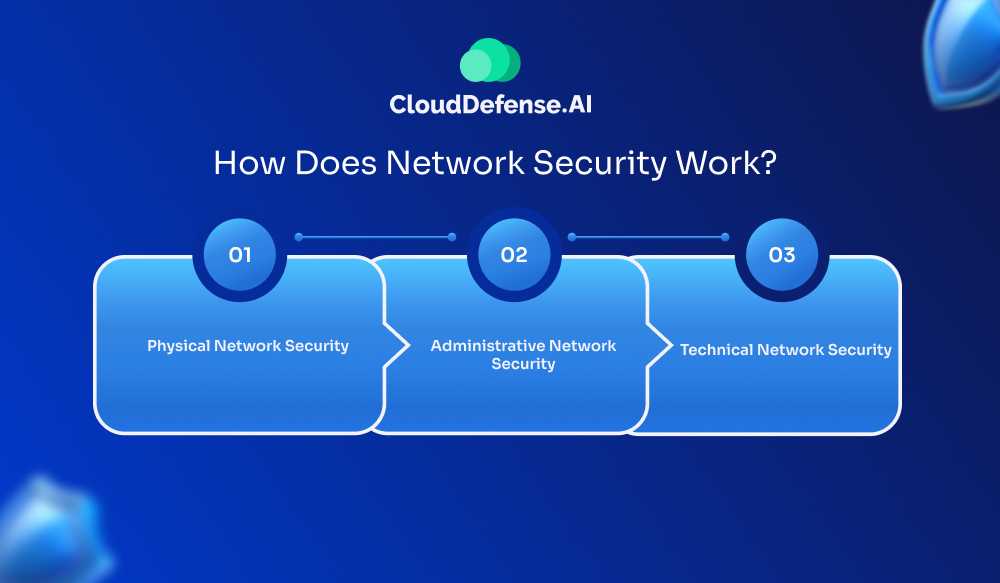
Network security works by combining multiple hardware and software security solutions that create a defense at the network edge and within the network. Every network security is segmented into different layers, and each layer implements specific security policies and controls.
The security teams of the organization are responsible for determining the security strategies, policies, and software that must be implemented to keep each layer safe from unauthorized access and attacks. Every member should follow the security policies implemented for each layer.
Modern network security has evolved greatly as it involves IPS, different firewalls, sandboxes, DNS filters, and many others that work together to safeguard the network. Every network security usually comes with three different controls it includes:
Physical Network Security
Physical network security controls are those that are implemented to prevent attackers from gaining physical access to network components like servers, routers, switches, cabling cupboards, and others. Usually controls like biometric authentication, face recognition, security locks and other devices are utilized for physical network security to prevent unauthorized access.
Administrative Network Security
Administrative network security controls are designed with various security processes and policies to control network accessibility by users throughout the IT environment. It is basically designed to control user behavior that includes the user authentication process, level of access, how security members change the infrastructure, and many others.
Technical Network Security
Technical network security is implemented to protect the traffic that moves across or the data that is stored in the network. This security control focuses on protecting data from cyber attackers and also prevents data access from employees who intend to use it for malicious purposes.
The working of network security is dependent on two processes: authorization and authentication. Authentication is a security process that checks and verifies whether a particular user belongs to the network and offers entry to the right users.
On the other hand, authorization determines the level of access that the authenticated user must have. The authorization process evaluates the user’s role and, depending upon that, provides permission level.
Benefits of Network Security
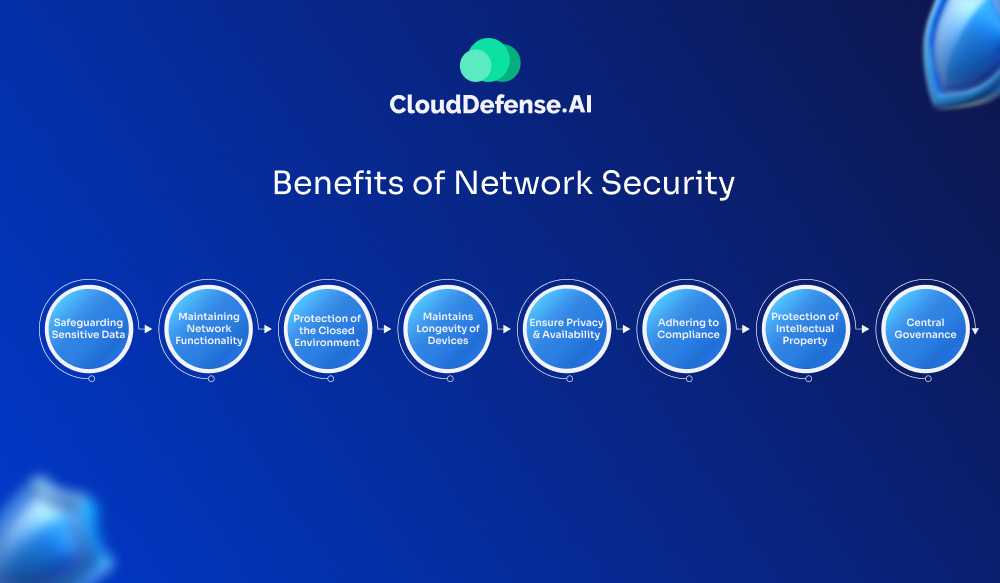
The massive shift in modern services and the adoption of cloud technologies has made network security a necessity for modern organizations. As the number of cyber threats is increase and network infrastructure is getting complex, network security is crucial in today’s time. Here is how you can benefit from network security:
Safeguarding Sensitive Data
A network of an organization carries a lot of data that not only resides there but also moves in and out of the network all the time. It usually contains a lot of sensitive information, like an organization’s financial data and customer information, which, if leaked, can jeopardize the business. Network security implements technologies and controls that prevent unauthorized access of those data.
Maintaining Network Functionality
Network security is responsible for maintaining network functionality of a business and ensures everything performs the way they should be. It protects all the configurations and prevents unauthorized changes by employees as a sudden drop in performance can hamper the continuity of business workflow.
Protection of the Closed Environment from the Internet
With implementation of network security, it enables the organization to have a closed environment which is protected from external threats and the internet. It plays an important role in protecting the private network and keeping all the threats at bay.
Maintains Longevity of Devices
Network security is responsible for safeguarding the network devices from all kinds of cyberattacks like DDoS, hacktivism, malware and others. As a result, the network gets better longevity, and they can last for a long time.
Ensure Privacy and Availability
Organizations that handle a lot of customer information must adhere to CIA triads, which ensure confidentiality, integrity, and availability of the customer data on the network. Network security through its robust controls and policies protects the data from attackers and malicious usage from insiders and ensures the organization’s reputation remains intact.
Adhering to Compliance
Many organization have to comply with various data privacy regulations when they use customer information. Network security helps organizations to comply with strict data regulation guidelines while protecting the data from unauthorized access.
Protection of Intellectual Property
Intellectual property serves as a key ingredient to organization’s success and getting the edge over its competitors. Network security makes sure all the access to intellectual property related to business strategy, services, and others are completely secured.
Central Governance
When you implement network security in your organization, it gives your team, especially network administrators the ability to control network access from a central dashboard. It provides the team with a 360-degree view of the network which helps in reducing the overall attack vector.
What Types of Threat Does Network Security Prevent?
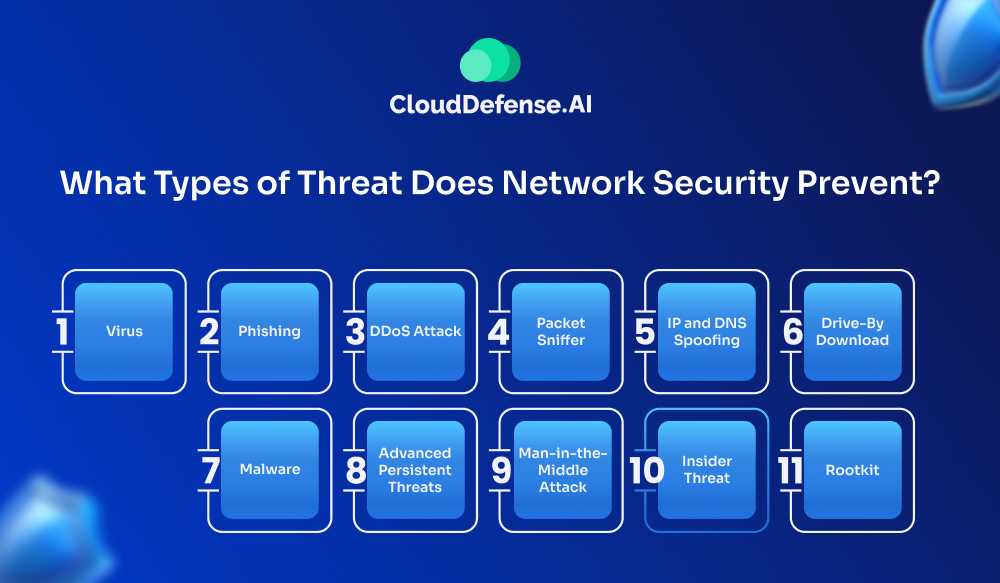
Network security safeguards the vast network of an organization from a broad range of cyber threats and ensures the organization operates smoothly without interruption. The types of threat it prevents are:
Virus
Network security proactively protects an organization’s network from different types of viruses that are usually delivered to destroy all network data. Usually, a virus enters the network as an executable file, and once it is executed, it can spread by replicating itself and infecting all the files throughout the network.
Malware
Malware serves as one of the favorite mediums for attackers to breach a network and infect every data in it. An attacker can launch various types of malware attacks depending upon their malicious intent. Usually, cyber attackers use malware to secretly steal an organization’s data, destroy specific data types, or disrupt the whole operation. On some occasions, malware is used to disrupt devices connected to the network.
Phishing
Another popular threat type that network security prevents is phishing. In this type of attack, the cybercriminals trick users into clicking malicious links or downloading attachments that when executed performs various malicious functions. Network security prevents users from interacting with such malicious links or files.
DDoS Attack
Abbreviated as distributed denial of service attack, attackers widely use this form of attack to disrupt the network of an organization and deny users of using various resources. It floods the network with messages or packets, causing it to slow down. However having a network security can help organization avert such a situation as this security solution filters all the messages or connection requests.
Advanced Persistent Threats
APTs are modern cyber-attacks that are widely targeted at networks of organizations where the attacker gains access to the network and stays undetected for a long time. Usually this type of attack is launched to steal all the sensitive information from the network without raising any suspicion. In most APT attacks, the attackers maintain a long-term presence to covertly consume information, and they are mainly directed to large organizations.
Packet Sniffer
Network security also proactively defends attacks like packet sniffing where a passive receiver intercepts the wireless transmission and creates copies of every packet that passes through the network. Usually the packets that move across the network of an organization carries sensitive information and captures all the packets for illicit means.
Man-in-the-Middle Attack
Man in the middle attack specifically targets networks of organizations with the intent of intercepting traffic within the network. In this type of attack, the attacker monitors and captures the information that passes through the network. In some attacks, the attackers even get to control the information.
IP and DNS Spoofing
Another type of threat that network security prevents is IP and DNS spoofing. In DNS spoofing, the attackers get into the network and corrupt the DNS data to insert a malicious cache. As a result, when a user searches, the server comes up with the wrong IP address.
Insider Threat
Insider threat is a serious threat to network security because in this type of threat employees or stakeholders with internal access compromises the network security unintentionally or maliciously. Usually insider threats are carried out for malicious purposes like financial gains, sabotage, or disruption of the business workflow.
Drive-By Download
Drive-by download is a unique type of attack where an user at the endpoint of a network unintentionally downloads malicious code and exposes the whole network to attack. This type of malicious code doesn’t need to be executed, and it can exploit any vulnerability present in a network device. Once it affects one device, it slowly infects other devices in the network.
Rootkit
Network security also helps in preventing rootkits which are designed in such a way that it gives attacks unauthorized access to the network. Before it completely controls your network, it first captures all the credentials and disables the antivirus at the endpoint device. Usually rootkits come through malicious software and when you install it, rootkits spread across the network.
Types of Network Security
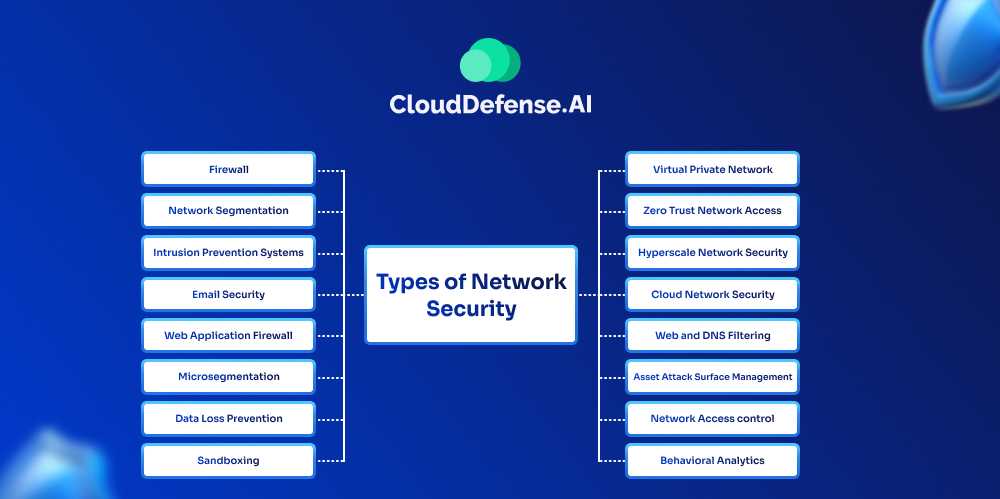
When you decide to choose network security, you will come across different types, and they are:
Firewall
A firewall is a popular network security type that monitors and controls all the traffic going in and out of the network, backed by predefined rules. It inspects all the data pockets moving in the networks and prevents internal from external and untrusted networks. Most of the network security is dependent on firewalls, especially next-gen firewalls, whose aim is to prevent block malware and application layer attacks.
Network Segmentation
Network segmentation is another network security type that creates a boundary among network segments depending upon the assets having the same function or role.
In most cases, the internal network of the organization is segmented from the internet, thus threats outside the network are prevented from infecting the internal network carrying sensitive data. Some organization even cause segmentation in their internal network to improve the overall access control.
Intrusion Prevention Systems
Also known as IPS, this type of network security identifies and blocks all the potential and known threats before it can infect the network or edge devices. The intrusion prevention systems assess a huge amount of threat intelligence data to block malicious activity, abnormal behavior and track the progression of potential malware across the network.
Email Security
Email security is widely implemented to protect the email accounts and contents from external threats. Email serves as a primary target for most attackers and they use various social engineering tactics to deliver malicious code or software that will eventually infect the system. Usually this type of network security makes sure the emails are free from malicious links or files that could breach the network.
Web Application Firewall
With the focus on filtering, monitoring, and blocking HTTP traffic flow moving in and out of the web service, WAF makes sure attackers can’t exploit vulnerabilities in web applications. It constantly monitors all the HTTP traffic and prevents threat actors from launching SQL injection, cross-site scripting, or file inclusion.
Micro Segmentation
Micro segmentation is a highly effective network security where security architects split the network into different segments and define security controls for each segment. Due to micro segmentation, it becomes easier to deploy flexible security policies inside the data center through network virtualization technology.
It is widely implemented to safeguard individual virtual machines with security controls. Moreover, IT administrators also can deploy security policies to separate workloads and improve overall security posture.
Data Loss Prevention
DLP or data loss prevention is a well-known network security methodology that utilizes best security practices and technologies to prevent sensitive data from getting exposed to the outside world. It employs a specific methodology that makes sure PII and customer data from unauthorized access in the network.
Sandboxing
It is a specialized network security that opens files or executes codes in an isolated environment on the host machine. When a file is opened or a code is executed, the security team monitors the process for any malicious behavior and prevents any kind of threat from getting into the network. When the network security detects any malware or virus, it immediately blocks the malicious code or files before it reaches the network.
Virtual Private Network
VPNs create a secure passage for sensitive information to be transferred to the internet by encrypting the connection to the network. The secure passage created by VPN is completely encrypted, and it ensures all the data moving to and from it are completely protected.
The increase in work-from-home culture and employees using insecure networks for browsing the internet from the endpoint is leaving the organization’s network completely vulnerable. However VPN solves the issue by completely encrypting the transmission.
Zero Trust Network Access
ZTNA is an effective network security based on zero trust security model that ensures users should have access to only those resources that they need to accomplish their defined role. Basically it offers granular access to the users to the application who only needs permission to perform their role.
Hyperscale Network Security
Hyperscale network security has become a necessity for modern organization as it enables them to scale the security architecture according to the demand. Through this network security, organization can scale up or down the architecture. Most importantly, it promotes integration of network and computational resources to fully utilize hardware resources.
Cloud Network Security
Last few years, industries have seen a huge migration to cloud platforms and it has made cloud network security a necessity. It comprises a huge amount of a lot of policies, technologies, and processes that is implemented to safeguard IP, services, applications and confidential data. It creates a secured perimeter to safeguard the network from cloud-based threats.
Web and DNS Filtering
Domain Name System and web filtering is a popular network security solution designed to prevent domain-based and URL-based attack. The DNS filtering helps in preventing DNS hijacking, and tunneling while URL filtering prevents users and devices from opening malicious links. This type of network security also helps organization to deploy acceptable-use policies which ensure any harmful contents can’t affect the network.
Asset Attack Surface Management
Attackers often target network assets to compromise the whole network of an organization. Asset attack surface management serves as a vital network security type that automatically discovers all the network IoT, IT and OT assets and assesses them for any possible threat. It also enables the security team to analyze the security controls and infrastructure for any kind of misconfiguration or other issues.
Network Access control
Network access control takes care of all the access to an organization’s network and ensures that only authenticated devices can enter the network. NAC assesses the authentication of the devices and provides access only when it caters to compliance policies. If any device fails to meet the compliance policies or authentication, it is quarantined and denied access.
Behavioral Analytics
It is a unique type of network security solution that assesses activity in the network and blocks any activity having unusual patterns. It automatically detects any abnormal activity pattern that deviates from the normal behavior. As a result, security teams can identify possible threats that might impact the network.
Final Words
Network security serves as one of the primary pillars of modern cybersecurity of an organization. It not only helps in securing the sensitive customer data and assets from various threats but also ensures optimum network performance by eliminating any overhead expense.
An organization with proper network security also enables the expansion of security infrastructure and ability to function from anywhere without getting affected by cyberthreats.







