The modern workplace is no longer confined to the four walls of an office. With the increasing popularity of smartphones, tablets, and laptops, employees are increasingly working remotely, accessing sensitive company data from wherever they are. This mobility, while offering a plethora of benefits, also presents a significant challenge for IT departments: security.
This is where Mobile Device Management (MDM) comes in. MDM is a powerful tool that allows IT admins to securely manage and control the devices that access company data. But what exactly is MDM, and how can it benefit your organization? In this blog post, we’ll delve into the world of MDM, exploring its functionalities, advantages, and how it can empower your business to thrive in today’s mobile-centric world.
What is Mobile Device Management (MDM)?
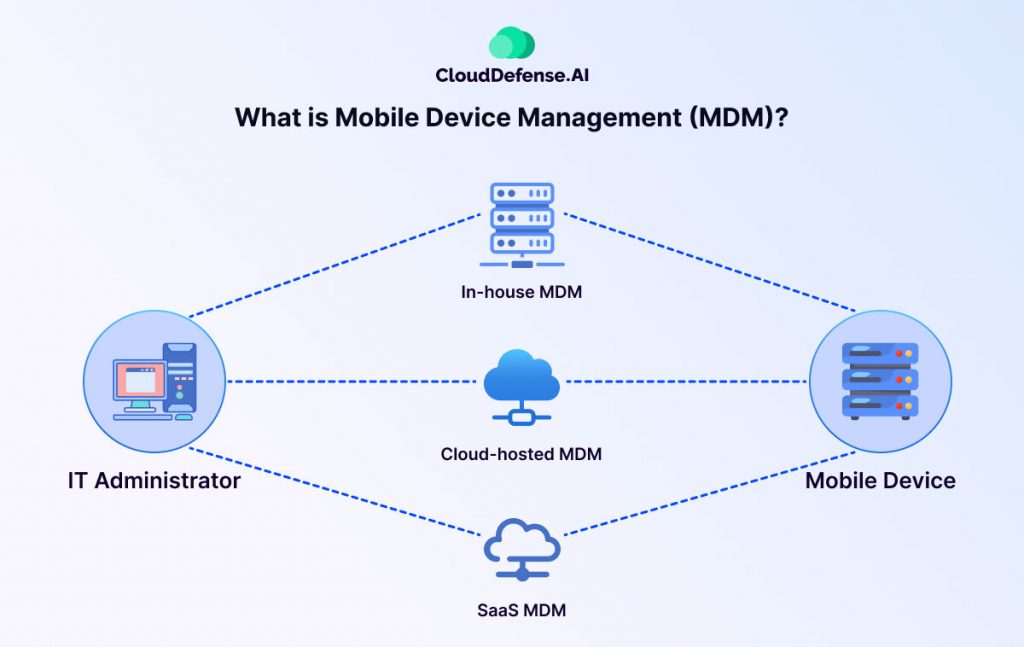
Mobile Device Management, or MDM, is the IT administrator’s toolbox for overseeing the mobile devices that access company data. This includes smartphones, tablets, and even laptops in some cases. MDM focuses on two key areas: security and functionality.
An MDM solution acts as a central hub, keeping track of important details about each device like its model, operating system, and serial number. This information helps IT maintain an inventory and identify potential security risks. MDM also plays a key role in app management, determining which applications employees can install and use for work purposes. This ensures that only authorized and secure apps have access to company data.
Perhaps most importantly, MDM offers remote security features. If a device is lost or stolen, IT can remotely lock it down or even wipe all company data to prevent unauthorized access. MDM can even track the location of devices, providing an extra layer of security and control.
Why Mobile Device Management (MDM) is Crucial?
The convenience of a mobile workforce goes hand-in-hand with significant security challenges. With employees accessing corporate data on personal devices, the potential for breaches and leaks increases. This is where MDM steps in, offering a vital layer of protection for your organization. Here’s why MDM is no longer optional in today’s mobile-centric world:
Security Imperative: Mobile devices, by their very nature, are more susceptible to loss, theft, or hacking compared to traditional desktops. MDM mitigates these risks by enforcing security measures like strong passwords, data encryption, and remote wipe capabilities. In the unfortunate event of a device compromise, MDM empowers IT to take swift action, preventing unauthorized access to sensitive data.
Standardized Environment: With a diverse range of devices accessing company resources, maintaining consistency can be a challenge. MDM ensures a standardized mobile environment by controlling app installations, enforcing security configurations, and ensuring devices stay updated with the latest security patches. This uniformity simplifies IT management and reduces the risk of vulnerabilities.
Reduced Risk of Data Breaches: Lost or stolen devices can be a nightmare, but with MDM, you can remotely lock them down or wipe all corporate data, minimizing the risk of a costly data breach.
Compliance Enforcement: Many industries have strict regulations regarding data security and privacy. MDM plays a vital role in ensuring compliance with these regulations by enforcing access controls and data protection measures.
By keeping IT administrators in control of mobile devices, MDM helps organizations avoid hefty fines and reputational damage associated with data breaches.
Increased Productivity: MDM can streamline workflows by enabling remote deployment of applications and updates, keeping employees productive wherever they work.
Reduced IT Burden: MDM simplifies device management for IT admins, allowing for centralized control over software updates, security configurations, and troubleshooting.
How Mobile Device Management (MDM) Works?
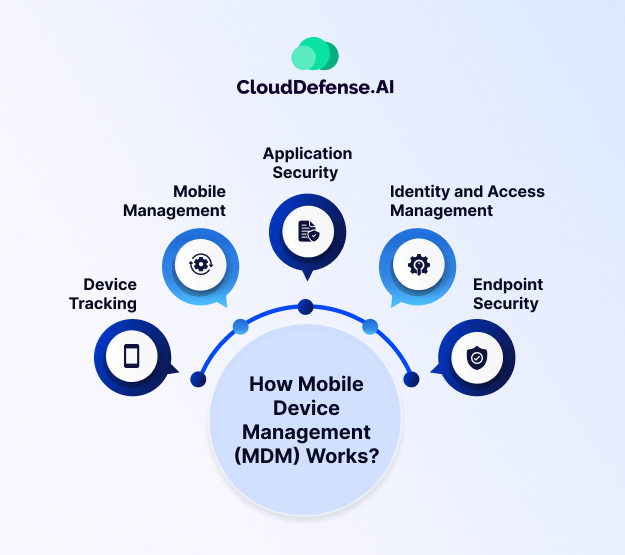
Behind the scenes of mobile workplaces, MDM acts like a silent conductor, keeping everything running smoothly and securely. While MDM isn’t a single piece of software, it relies on software as a key element. Think of it as a comprehensive solution with three parts working together:
- MDM Server: This is the central hub, allowing IT to remotely provision devices, setting them up with the necessary apps, configurations, and security features.
- Processes: MDM isn’t just about the tech. It also involves defined procedures for how devices are enrolled, accessed, and used. These procedures ensure consistency and compliance.
- Security Policies: These are the rules of the road, dictating things like password strength, approved apps, and data access limitations. Strong policies are vital for keeping company information safe.
So how does this translate into everyday use? Imagine a company offering employees the option to use their phones for work. MDM would create a secure work profile on the phone, granting access only to authorized work apps and data. This keeps personal and professional information separate while adhering to company security guidelines.
MDM goes beyond simple setup. It also acts as a security guardian. The software can monitor devices for suspicious activity and malware, while features like remote wipes allow IT to erase all company data from lost or stolen devices. This prevents sensitive information from falling into the wrong hands.
MDM policies are the foundation for this secure environment. These answer key questions like whether cameras should be disabled by default or if certain devices must be tracked via GPS. By establishing clear guidelines, MDM ensures everyone is on the same page when it comes to mobile device use within the organization.
Core Components of MDM Solutions
MDM solutions come equipped with a variety of tools to tackle different aspects of security and control. Here’s a breakdown of some key components:
Device Tracking
This goes beyond simply knowing where your devices are. MDM allows IT to monitor device health, track app usage, and troubleshoot issues remotely. Think of it as a real-time control center for your mobile fleet. Additionally, MDM can identify and report devices that are out of compliance or pose a security risk. If a device goes missing, IT can remotely lock it down or even wipe all company data to prevent unauthorized access.
Mobile Management
MDM goes beyond just tracking. It streamlines the entire mobile device lifecycle for IT. This includes provisioning new devices, deploying operating systems and essential applications, and ensuring all devices are configured securely. MDM also simplifies troubleshooting, allowing IT to diagnose and fix issues remotely.
Application Security
Not all apps are created equal, especially from a security standpoint. MDM empowers IT to leverage app wrapping technology. This creates a secure container around approved work applications. Within this container, IT admins can define access controls. These application security controls might restrict features like data copying, pasting, or sharing, ensuring sensitive information stays protected. Additionally, they can enforce user authentication requirements to access these work apps.
Identity and Access Management (IAM)
Who has access to what? IAM is a critical component of MDM, ensuring only authorized users can access sensitive company data on mobile devices. Features like single sign-on (SSO) streamline login processes, while multi-factor authentication adds an extra layer of security. IAM also allows for role-based access control, restricting access to data and functionalities based on an employee’s role within the organization.
Endpoint Security
MDM goes beyond just smartphones and tablets. It encompasses the entire mobile device ecosystem, including wearables, IoT sensors, and even laptops. Endpoint security features like antivirus software, network access control, and URL filtering work together to create a robust defense against cyber threats. This ensures all devices accessing the corporate network are protected, regardless of their form factor.
Best Practices for Mobile Device Management
Mobile Device Management (MDM) is a powerful tool, but like any technology, it’s only as effective as the strategy behind it. Here are some best practices to ensure your MDM solution delivers maximum security and efficiency:
Craft a Clear and Comprehensive Policy: Develop a clear MDM policy that outlines acceptable device usage, security protocols, and user responsibilities. This policy should address areas like password complexity, app installation restrictions, and lost/stolen device reporting procedures. Communicate this policy clearly to all employees and ensure everyone understands their role in keeping company data secure.
Embrace Automation: MDM solutions offer a wealth of automation features. Utilize them! Automate tasks like device enrollment, security policy enforcement, and software updates. This frees up IT resources and ensures consistent security across all devices.
Prioritize Strong Passwords and Multi-Factor Authentication (MFA): Weak passwords are a hacker’s dream. Enforce strong password requirements and implement multi-factor authentication for an extra layer of security. MFA adds a verification step beyond just a password, like a fingerprint scan or a code sent to your phone, making it much harder for unauthorized access.
Keep Software Up-to-Date: Outdated software is vulnerable to security exploits. Configure MDM to enforce automatic updates for operating systems and approved applications. This ensures all devices have the latest security patches and bug fixes, minimizing the risk of breaches.
Develop a BYOD (Bring Your Own Device) Strategy: With the increasing popularity of BYOD programs, establish clear guidelines for how employees can use their devices for work purposes. MDM can help enforce BYOD policies by creating secure work containers on personal devices and restricting access to sensitive data.
Leverage Containerization for Secure App Management: MDM’s app wrapping capabilities are your friend. Utilize containerization technology to create secure workspaces for approved applications. This isolates work data from personal data and enforces access controls, adding an extra layer of protection.
Train Your Employees: Educate your workforce on best practices for mobile security. Train them to identify phishing attempts, avoid suspicious downloads, and report lost or stolen devices immediately. Empowered employees become your first line of defense against cyber threats.
Regularly Monitor and Audit: Don’t set it and forget it! MDM solutions offer detailed reports on device activity, security threats, and compliance. Regularly review these reports to identify potential issues and ensure your MDM policies are being followed.
By following these best practices, you can leverage your MDM solution to its full potential. This will create a secure and productive mobile work environment, keeping your organization’s data safe and your employees connected.
Conclusion
The mobile revolution has already transformed how we work. MDM has emerged as an essential tool for organizations to navigate this mobile landscape securely. MDM goes beyond just managing devices; it empowers IT to enforce security policies, streamline mobile deployments, and create a productive work environment for your mobile workforce.
When you understand the core functionalities of MDM, implement best practices, and establish clear policies, you can leverage the power of mobility with confidence. MDM is the key to unlocking a world where secure and flexible work practices go hand-in-hand. So, embrace the mobile future and empower your workforce to thrive, all while safeguarding your organization’s valuable data.







