What is MITM Attack?
A man-in-the-middle or MITM is a type of cyberattack where a cybercriminal places themselves between two parties and stealthily intercepts or eavesdrops on their message. Using various techniques, the attackers place themselves in the “middle” of the communication or data transfers while hiding or pretending to be legitimate participants.
This type of eavesdropping poses a serious threat to an organization as it can not only control communication but also manipulate and capture sensitive information in real time. Besides, the attackers not only can relay the data but also send malicious links to both the target in a way that will stay undetected for a long time.
The usual targets of this attack are SaaS applications, e-commerce sites, hospital apps, financial sites and others that require logging. The data obtained during the MITM attack are utilized for different purposes like identity theft, password change or unapproved money transfer.
Sometimes, cybercriminals use the credentials to enter a secure perimeter of a system during an APT attack. Man-in-the-browser is a popular MITM attack where the attackers get entry into the browsers and inject malware through phishing. The primary motive behind such attacks is usually stealing sensitive financial information by eavesdropping on user’s traffic.
Man in the Middle Attack Techniques
When it comes to MITM attacks, cybercriminals involve various types of techniques to accomplish the attack. Here are some common techniques utilized by attackers:
Sniffing
A popular technique utilized by attackers, sniffing is a type of technique where attackers use packet capture solutions to assess packets. Wireless devices with monitoring capabilities are mainly the target of attackers and it allows the threat actors to inspect packets that are restricted to outsiders.
ARP Spoofing
Another popular MITM technique leveraged by cybercriminals is Address Resolution Protocol or ARP spoofing where the IP address of the targeted user is integrated into a MAC address of the malicious server.
When the linking happens with the IP address of the user, all the network from the user’s device is routed through the malicious server, allowing the attackers to interpret all the crucial information.
Packet Injection
To eavesdrop on the communication between two targets, cybercriminals often use packet injection. In this technique, the attacker uses the monitoring mode to push a malicious packet into the data communication stream and then it mixes with the data communication stream of the legitimate user’s communication.
This technique is widely used in conjunction with sniffing so that the attacker can understand how and when they can send the malicious packet.
ICMP Packet Spoofing
ICMP is a part of internet protocol where diagnostic information is communicated between the client and servers. Attackers utilize ICMP packet spoofing where attackers reroute the network traffic to a malicious routing device before it is sent to the intended gateway.
Plus, the traffic received at the gateway is also sent back to the attacker’s MAC address before it is sent to the client.
Session Hijacking
Session hijacking is mostly used to launch MITM attacks on web applications to identify session tokens. Almost every web application creates a temporary session token for the user’s login convenience and uses it throughout the page.
Attackers through sniffing the network traffic identify the token of a user and use it to gain access to the application. Once the attacker has access to the session token, they won’t require spoofing and can easily hijack all the sensitive information.
DNS Poisoning and Spoofing
Attackers use DNS poisoning and spoofing together techniques in this attack to modify the website address record on the DNS servers and the website URL is routed to an IP address of the attacker.
So when the attacker puts up a website address, instead of being directed to the legitimate site the victim is taken to a fake website that impersonates the original one. DNS poisoning helps the attacker to replace the legit URL of the targeted website while spoofing involves redirecting the user to a fake website through a poisoned cache.
SSL Stripping
Modern cybercriminals often use SSL stripping techniques to carry out MITM attacks as HTTPS often comes in the way of DNS spoofing. In SSL stripping, an attacker interrupts the packets of the victim’s network traffic and manipulates the HTTPS-based address request to a specific HTTP equivalent malicious server. Once it is done, the host makes a request to the malicious server, leading to the leakage of all the sensitive information.
Types of MITM Attack
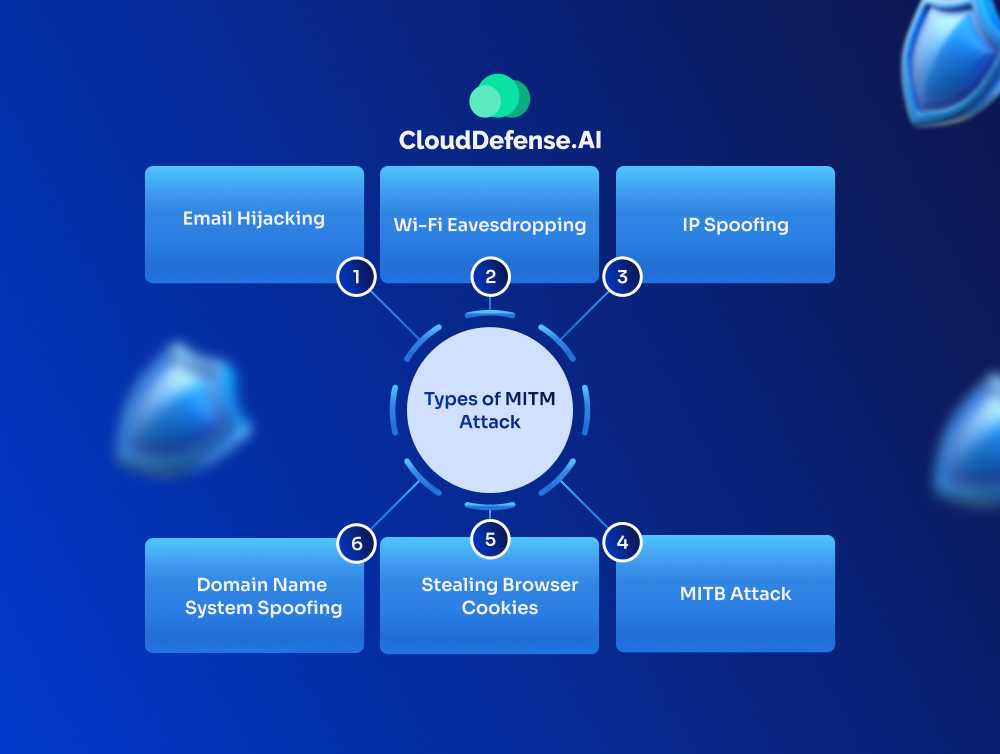
A man-in-the-middle attack is not based on a single type and depending upon the circumstances, the attacker may launch a different type of MITM attack. Here are some popular MITM attack types that you might come across:
Email Hijacking
Email hijacking is a popular MITM attack type where attackers get access to the email of financial institutes like banks and other institutes having access to specific sensitive data required by the attacker. Once the attacker gets access to the email, they can monitor all the communication happening between the client and the financial institute.
On many occasions, the attacker masquerades as the bank’s email address and sends emails to customers asking them to send financial credentials or sometimes money. In this type of attack, social engineering serves as the key to success.
Wi-Fi Eavesdropping
Wi-Fi eavesdropping is another well-known MITM attack type where public Wi-Fi users are tricked into connecting to a malicious Wi-Fi network. The attackers usually trick the user by setting up the name of the Wi-Fi to a name that resembles a famous or any nearby business.
The Wi-Fi network might be named a “Free Public Wi-Fi Network” or a generic name where the users aren’t asked to enter any password. Once the victim gets connected to the malicious Wi-Fi, the cybercriminal can monitor the victim’s web activity, gain login credentials, scrape payment information or get access to other sensitive data.
The only way to prevent this MITM attack type is to properly assess the Wi-Fi network or prevent auto-connecting to public Wi-Fi.
IP Spoofing
A popular MITM attack type utilized by attackers is IP spoofing where the attacker modifies the IP address of a website or email address to mask it. When a user hits the website, they share sensitive information with the website thinking it is a legit website and ultimately the information gets transferred to the attacker. It is a common attack type where users are often tricked into opening the altered website set up by the attackers.
Domain Name System Spoofing
In this type of MITM attack attackers utilize various techniques to alter the domain name of a legit website so that users are redirected to a fake website. The website is crafted to look similar to a legit website and users browse them thinking they are interacting with a trusted site. Not only do they put login credentials but they often put payment card details to make some purchases, enabling attackers to capture all the sensitive details.
Stealing Browser Cookies
Browser cookies are an important aspect of web browsing as they store the required information about a website to enhance the browsing experience. Cookies are stored locally in the device carrying a lot of information including credentials, texts, and others. However, this type of MITM attack is accomplished with other MITM attack techniques.
The attackers may utilize one technique to gain access to the device and then launch this MITM attack on the browser cookies. When the attackers gain access to the browsers, they can retrieve a variety of sensitive information including passwords, card details, images, and other sensitive information.
MITB Attack
MITB attack is a unique type of MITM that exploits the internet browser security flaws to help attackers achieve their malicious intention. This type of attack generally involves desktop worms, SQL injection attacks, trojans and other malware.
These malware are mostly utilized to extract financial information by intercepting financial data communication happening between client and bank sites. Some of the attacks are utilized to steal passwords of bank accounts or other financial accounts. While some of the malware scripts are designed in such a way it helps attackers to move money illegally and alter the receipt of the transaction details.
Examples of Man in the Middle (MITM) Attack
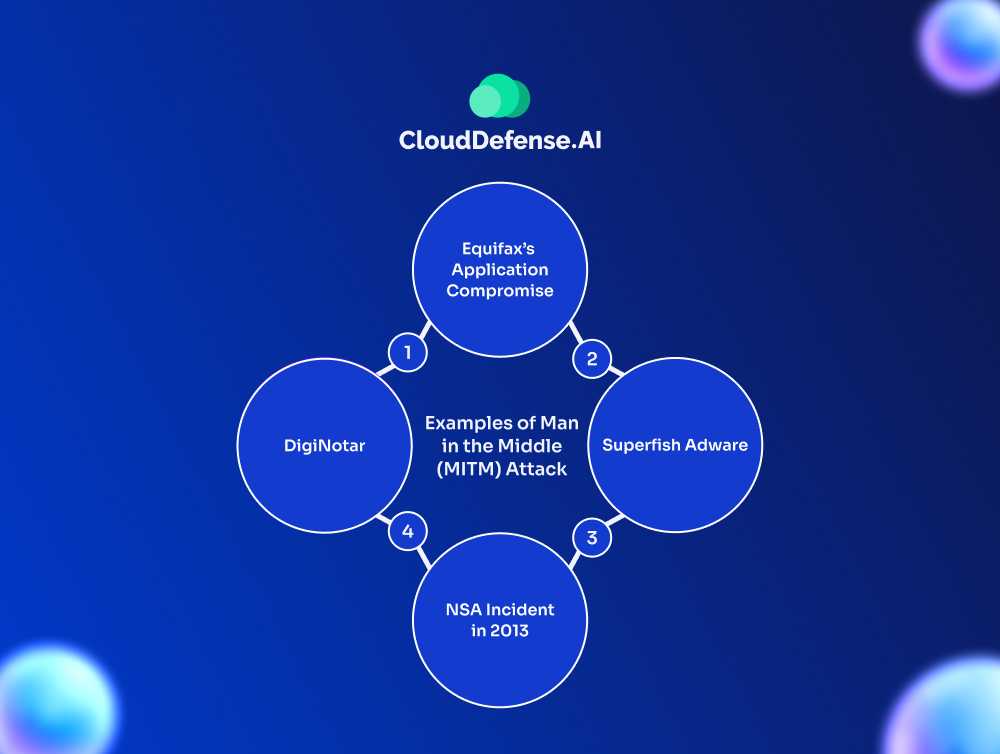
MITM attack is an age-old form that started before the internet and over the years it has evolved with the technology. Like other attacks, it has an adverse effect on enterprises and users and can cause serious financial damage. Here are some examples of MITM that caused significant impact on enterprises:
Equifax’s Application Compromise
In 2017, Equifax, which is a huge credit report agency faced a huge data breach that leaked the financial information of 150 million in the US. The breach mainly occurred due to security and the IT team’s negligence in patching a known vulnerability.
To help customers know whether they were impacted, the organization also launched a website called “equifaxsecurity2017” after the attack. Once the breach occurred, it was also discovered that the mobile app Equifax wasn’t using HTTPS and it enabled hackers to eavesdrop on the financial data of users while they accessed their accounts.
Superfish Adware
Another major example of an MITM attack was Superfish adware that was pre-installed in Lenovo computers. In 2015, Lenovo rolled out a large batch of computers installed with Superfish Visual Search and this exposed all the users to MITM attacks. This adware injected advertisements into the encrypted web traffic while the user browsed any site and altered the SSL certificate.
As a result, the attackers were able to monitor all the web activity of the users on the Chrome or Internet Explorer browsers along with their login data. However, after finding out about the breach, Microsoft and McAfee coordinated with Lenovo to roll out an update to remove the Superfish adware.
DigiNotar
DigiNotar is a well-known MITM incident where the cybercriminals got access to 500 certificates of well-known websites including Google. The cybercriminals utilized the MITM attack where they manipulated users into putting their credentials on a fake website posing as a legit one. The attack happened in 2011 and as DigiNotar had to go through a huge financial crisis after the breach, the organization filed for bankruptcy.
NSA Incident in 2013
In 2013, the National Security Administration was exposed by Edward Snowden who leaked documents showing the NSA pretended to be Google to intercept all the traffic.
While working as a consultant in the NSA, Edward Snowden found out that the NSA used an MITM attack with an SSL spoofing technique to gather the search records of all Google users, especially citizens of the USA. The release of the document created a huge storm in the country as it is illegal to carry out domestic spying on US citizens.
How To Detect Man in the Middle Attack
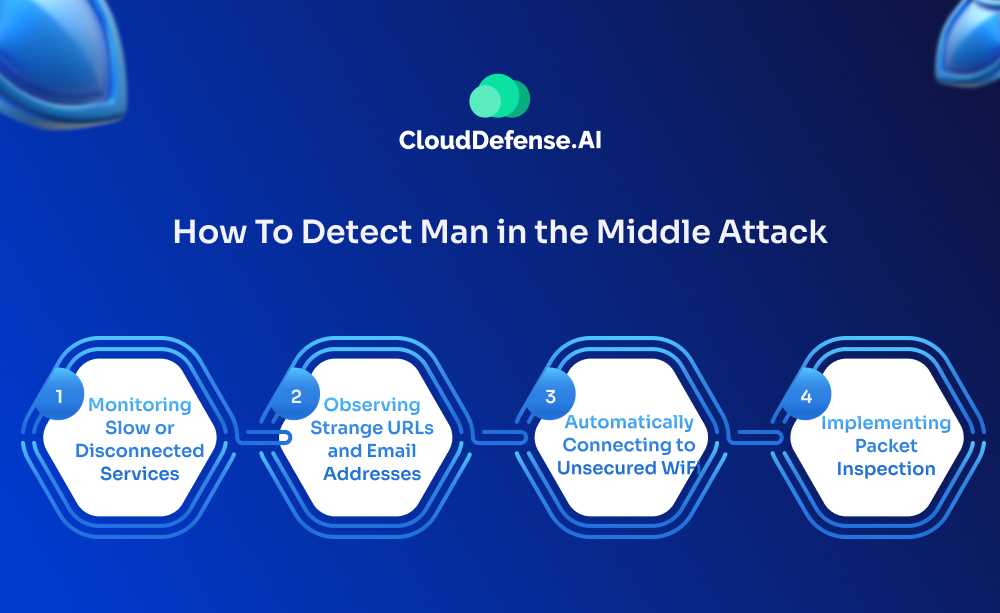
Detecting MITM attacks can be a tough affair as cybercriminals have become sophisticated with their techniques. However, identifying MITM in the early stage enables the security to quickly and easily mitigate the issue. Here are some useful methods that will help in detecting MITM attacks:
Monitoring Slow or Disconnected Services
When a user tries to log in to their account and gets timeout every time they try to connect, then it is an indication of MITM. It is possible the attacker is interrupting the login to interpret the login credentials of the users.
In another instance, a user may come across a service or website which is slow and not performing in a similar way as the actual website. Such an indication could be the website is spoofed and the attacker is trying to gain sensitive data.
Observing Strange URLs and Email Addresses
While browsing any website, if you find subtle changes in the characters of address but the site is similar to the original one, then it is a clear indication of DNS spoofing. Cybercriminals often create websites identical to the original website, especially financial sites, to lure victims into entering financial details.
When visiting any financial website, you should carefully examine the web address. Attackers often do email hijacking where they use a similar domain to impersonate a legitimate email address and trick you into sending sensitive information. The best way to avoid it is to thoroughly examine the origin and the email address before replying.
Automatically Connecting to Unsecured WiFi
If your device automatically gets connected to an unsecured WiFi without asking for any passcode, then it could mean it is a trap for an MITM attack. The attacker will use the WiFi to monitor the network to interpret financial data or other sensitive information and gain access to it.
Even if you don’t perform banking transactions using WiFi, the attacker can send malicious code to your device and eavesdrop on all the messages and chats. Attackers to launch MITM often offer free WiFi services to victims with names similar to any nearby business and in return, they observe all their online activity.
Implementing Packet Inspection
Apart from observing signs of MITM attacks, enterprises can launch deep packet inspection techniques to monitor the network traffic to find vulnerabilities.
This packet inspection technique will help you detect events like intercepting network traffic, outsider scanning and other activity. When you detect such events, then it could mean your network has been compromised and someone is monitoring all your online activity.
How to Prevent Man in the Middle Attacks
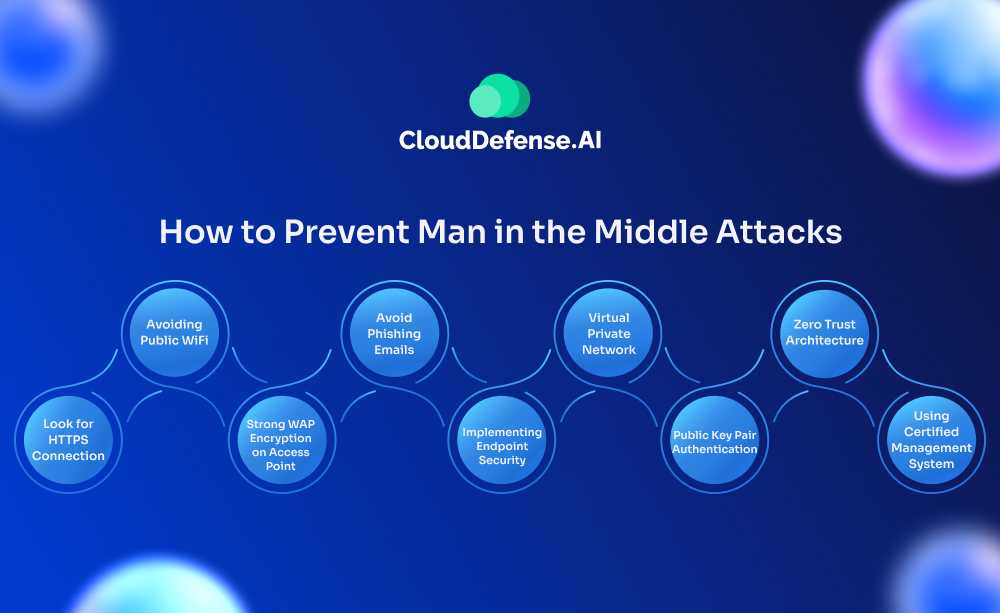
When it comes to preventing MITM attacks, it requires your team to take a holistic approach where they need to implement best practices and technologies. Here are mitigating controls that your team can utilize to protect the enterprises and their users from MITM attacks:
Look for HTTPS Connection
Whenever you are trying to browse any website, make sure it has HTTPS indicated in its web address. Many websites show padlock signs before the website address which indicates the website is completely secured.
You should completely avoid using a website that doesn’t have an HTTPS indication in the web address as it indicates the website is insecure. To secure your online activity from an MITM attack, you can use DNS over HTTPS which encrypts the DNS request.
Avoiding Public WiFi
Most of the time, public WiFi serves as a medium to carry out MITM attacks so free WiFi might seem lucrative but you should avoid using it. Attackers often use the free WiFi as a trap to lure users who have minimal cyber awareness and monitor their activity.
Strong WAP Encryption on Access Point
It is important to use robust WAP or WEP encryption mechanisms on wireless access points as it will prevent attackers from entering your wireless network and eavesdropping on your activity. If you don’t use WAP or WEP encryption, then the attacker may use brute force to enter the network and start with an MITM attack.
Avoid Phishing Emails
It is important that you avoid opening emails that originated from unknown sources. Attackers craft these emails to trick users into opening them and direct them to download malicious code or open a malicious site.
Usually, these phishing emails look like emails coming from a legitimate source like a bank or accountant but you have to be careful by assessing their origin. Through email, the attacker tricks users into sending financial details or opening links that redirect users to a fake website where they are asked to enter login credentials or download software on their device.
Implementing Endpoint Security
Endpoint serves as an easy source to spread malware for executing MITM attacks. Enterprises should employ robust endpoint security that would not only prevent attackers from breaching the endpoint but also eliminate the chance of spreading malware.
Using anti-malware programs and proper endpoint security from vendors will help in strengthening security at the endpoint.
Virtual Private Network
Another way to prevent MITM attacks is by using a VPN that encrypts your network connectivity and all the online activity. It becomes really useful when the user connects to an unsecured WiFi network or hotspot as it hides everything and jeopardizes the MITM attack.
The encryption of VPN is so strong that when an attacker breaches the network, they won’t be able to eavesdrop or interpret the messages. It would be best to make a norm in your organization that remote workers should log in using a corporate VPN.
Public Key Pair Authentication
Most MITM attacks involve spoofing techniques to interpret communication between two victims. Implementing public key pair authentication at different layers of the IT stack can help enterprises eliminate spoofing. It will enable your employees to learn about the authenticity of the thing with whom they are communicating.
Zero Trust Architecture
Enterprises should emphasize implementing Zero Trust architecture because it is based on principles of network segment that plays a crucial role in defending against MITM attacks. What Zero Trust architecture does is that it segregates networks into secured segments during an MITM attack and isolates the security incident to minimize further impact of lateral movement.
Using Certified Management System
Another effective way to prevent MITM attacks is by enforcing an automated certified management system that would manage SSL certificates. It generally serves as a centralized management that remediates expired SSL certificates and prevents them from getting utilized for SSL spoofing.
Conclusion
With time, attackers are getting sophisticated with man-in-the-middle (MITM) attacks and causing serious damage to enterprises. From hijacking and spoofing to using advanced eavesdropping techniques, attackers are coming up with numerous ways to put themselves in between users and services.
To help you know about the attack, we have come up with this article where we have discussed all the details regarding the MITM attack and what necessary preventive steps you should take to prevent the attack. Not only have we covered how you can detect MITM attacks and types but also how you can prevent them.







