What is Kubernetes Runtime Security?
Kubernetes runtime security is about protecting your containerized applications while they’re actively running. It’s the layer of defense that ensures malicious actors can’t exploit your infrastructure or data during live operations.
Unlike static security measures, runtime security focuses on detecting, responding to, and preventing threats in real time, ensuring the stability and integrity of your workloads.
What it does:
- Monitors live container workloads for anomalies.
- Detects and mitigates runtime vulnerabilities in real time.
- Identifies unauthorized access or suspicious activity.
- Prevents privilege escalation and lateral movement.
- Ensures compliance with security policies during operations.
In Kubernetes environments, this becomes critical due to the dynamic and distributed nature of containers and microservices. Runtime security involves monitoring workloads, identifying anomalies, and addressing vulnerabilities that could compromise your systems.
What is Kubernetes and Kubernetes Cluster?
Kubernetes is an open-source container orchestration platform designed to automate the deployment, scaling, and management of containerized applications. It ensures applications run efficiently and reliably, even in complex environments.
Kubernetes Cluster is the infrastructure where Kubernetes operates. It consists of:
- Control Plane: Manages the cluster’s overall state and schedules workloads.
- Worker Nodes: Run the containerized applications.
- Pods: The smallest deployable units in Kubernetes, hosting your containers.
- Networking Components: Enable communication between nodes and external systems.
Together, Kubernetes and its cluster form the backbone of modern cloud-native architectures, enabling scalability, flexibility, and high availability for containerized workloads.
Why Kubernetes Runtime Security Matters?
1. Real-Time Threat Detection
Kubernetes environments are fast-moving and unpredictable. Workloads are constantly being created, modified, or terminated, which creates openings for potential threats. Runtime security ensures that any suspicious activity is identified and stopped immediately, preventing breaches before they escalate.
2. Addressing Zero-Day Vulnerabilities
Zero-day vulnerabilities are a serious issue—they’re flaws in software that nobody knows about until they’re exploited. Traditional security measures often miss them. Kubernetes runtime security provides the real-time visibility needed to detect and mitigate these threats as they arise.
3. Meeting Compliance Standards
Regulations like GDPR, HIPAA, and PCI-DSS require robust security for systems handling sensitive data. Runtime security helps organizations stay compliant by actively monitoring and enforcing security policies during live operations.
4. Protecting Critical Microservices
Kubernetes relies heavily on APIs and microservices. These components are frequent targets for attackers looking to exploit weaknesses. Runtime security ensures these critical assets are monitored and protected continuously.
5. Preventing Downtime and Losses
Security incidents can disrupt operations and lead to significant financial losses. Runtime security minimizes these risks by keeping systems stable and operational, even in the face of active threats.
Kubernetes Runtime Security Challenges and Risks
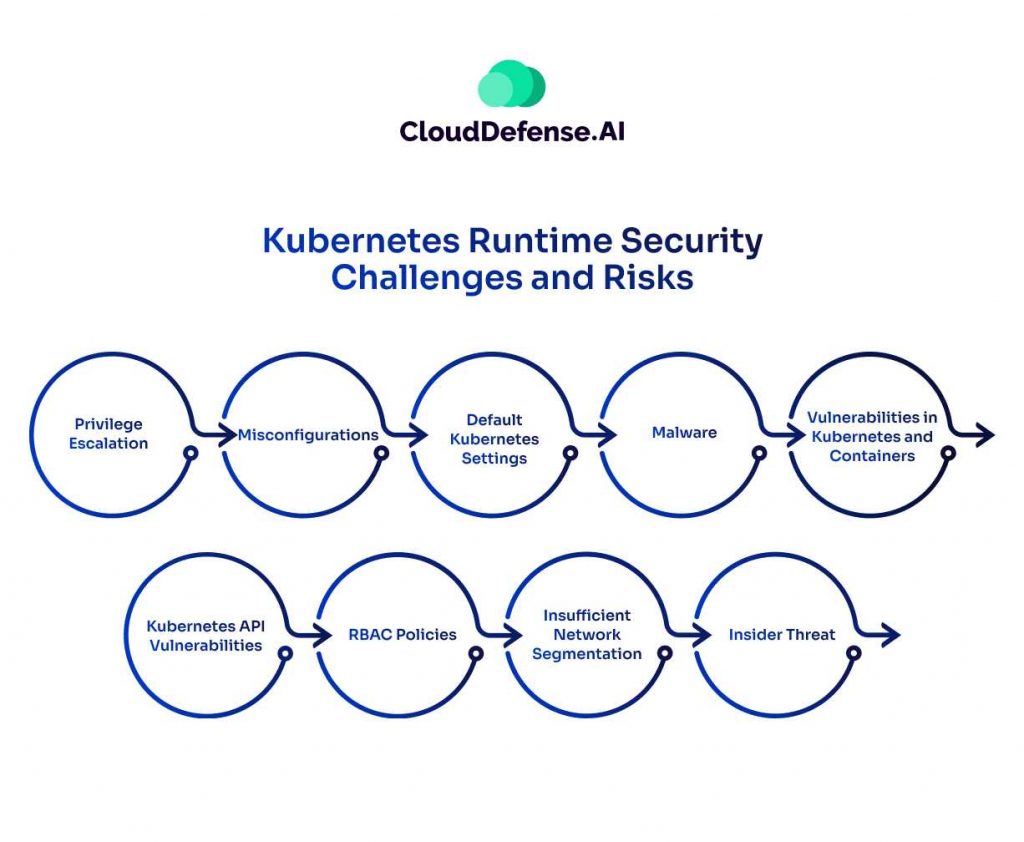
1. Complexity of Kubernetes Environments
Kubernetes is powerful but complicated. It involves multiple components—pods, nodes, services, and containers—each with its own security needs. The constant changes in a Kubernetes environment make it hard to maintain a clear view of everything happening, which can create security gaps.
2. Container Isolation Gaps
Containers are meant to be isolated from one another. However, flaws in the container runtime or misconfigurations can break this isolation. When that happens, attackers can move between containers and gain access to sensitive data or other parts of the system.
3. Weak Network Segmentation
Proper network segmentation is essential for limiting the reach of attacks. Unfortunately, many Kubernetes setups fail to segment networks effectively. Without this level of protection, attackers can access more of the system than they should, making the impact of a breach much larger.
4. Limited Security Tools
While Kubernetes has some built-in security features, they often aren’t enough on their own. Many organizations rely on third-party security tools, but not all of them are suited to the real-time demands of Kubernetes. Without the right tools, it’s easy to overlook threats or miss vulnerabilities.
5. Human Error and Misconfigurations
Many Kubernetes environments are managed by developers or system administrators who may not have a strong background in security. As a result, they may make mistakes or misconfigure settings—like giving containers too many permissions—that leave systems exposed.
6. Expanding Threat Rates
The security landscape is always shifting. New vulnerabilities are discovered regularly, and attack methods change quickly. Keeping up with these threats requires continuous monitoring and constant updates to security practices.
How Kubernetes Runtime Security Addresses These Risks?
Kubernetes runtime security is the answer to the growing challenges of securing containerized environments. It’s crucial for keeping your infrastructure safe, especially as systems grow more complex. The threats are real, and the speed at which they evolve means you need a solution that works in real-time.
Kubernetes runtime security provides exactly that: constant, active monitoring to keep threats out and protect your critical applications. Here’s how it tackles the most common challenges.
1. Real-Time Monitoring for Complex Environments
Kubernetes environments are complicated, no doubt about it. But with the right runtime security in place, you get visibility into everything that’s happening across your system. This constant monitoring lets you spot problems right away and act fast, preventing small issues from becoming big ones. You need real-time protection, and that’s exactly what runtime security delivers.
2. Better Container Isolation
Isolation is key in a containerized system. If containers aren’t properly isolated, it’s easy for attackers to move between them. Kubernetes runtime security works by constantly checking for vulnerabilities and misconfigurations that might break isolation. If something’s wrong, it’ll be caught and stopped immediately. This ensures that even if one container is breached, the rest are protected.
3. Stronger Network Segmentation
Network segmentation is essential for minimizing damage in case of a breach. Many Kubernetes setups don’t have strong segmentation, but with runtime security, you can enforce tighter controls. It ensures that only the right services communicate with each other, limiting the potential for unauthorized access. Simple but effective.
4. Integrated Security Tools
Security doesn’t work unless everything is integrated and working together. Kubernetes runtime security makes sure all your tools are in sync and operating at their full potential. With automated policies and real-time monitoring, it catches vulnerabilities at runtime and ensures your system stays secure without any gaps. It’s a comprehensive approach—no weak links.
5. Minimizing Human Error
Human error is always a risk, especially when you’re dealing with a complex system like Kubernetes. But runtime security minimizes this risk by automating checks and sending alerts when something goes wrong. Misconfigurations are fixed quickly, and you don’t have to worry about someone overlooking a security flaw. It makes the process smoother and more reliable.
6. Keeping Up With Evolving Threats
The threats out there are constantly changing, but Kubernetes runtime security keeps up. With continuous updates and ongoing monitoring, it adapts to new vulnerabilities and attack methods. This ensures your system is always ready for whatever comes next, keeping you ahead of the curve and your environment secure.
Best Practices for Kubernetes Runtime Security
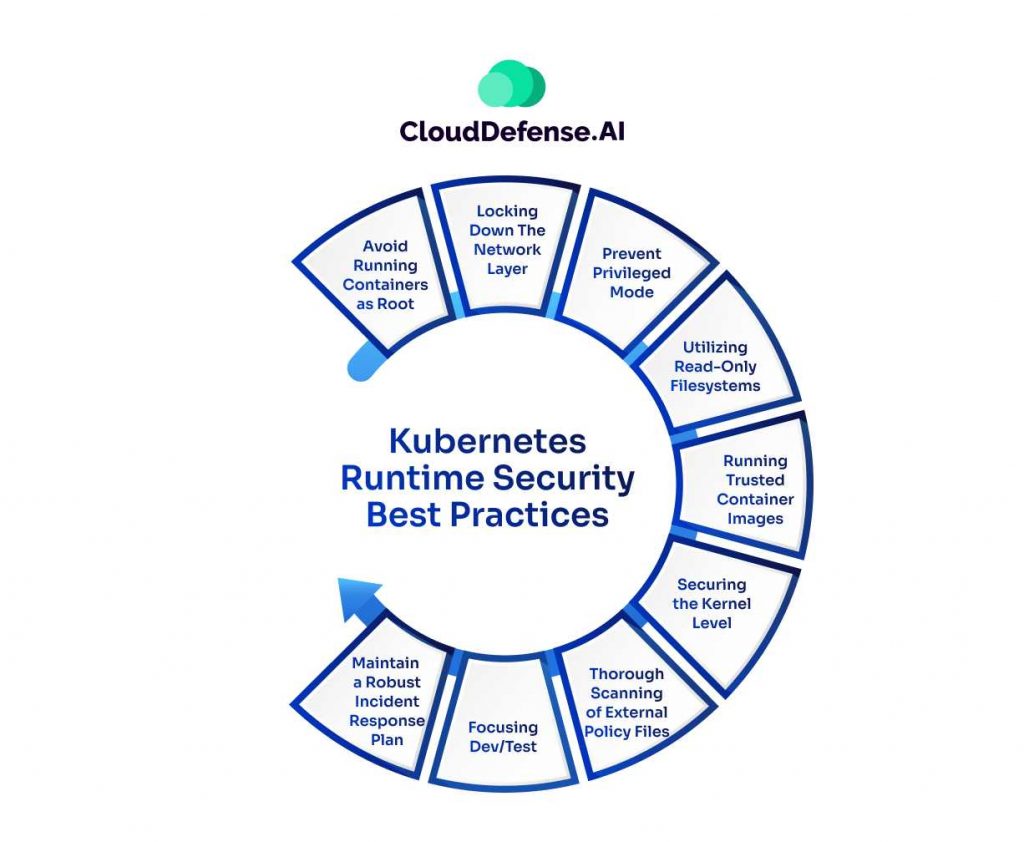
Kubernetes security is something you can’t ignore. It’s not just about throwing a few tools in place and hoping for the best. You need a strategy that works at every level. Let’s focus on the essentials—the practices that will help you protect your systems and make sure you’re one step ahead of any potential threat.
1. Restrict Access to What’s Necessary
The first thing you need to remember: not every user or service needs full access. Limit permissions to only what’s necessary. Make sure that users, services, and even containers can only do what they’re supposed to. It’s simple, but it makes a huge difference. If there’s no reason for someone to have access to a sensitive resource, don’t give it to them.
2. Control Access With RBAC
If you’re not using Role-Based Access Control (RBAC), you’re missing out. It’s a must for controlling who gets access to what. You can define who has what role, and control their ability to perform actions based on that. This is your way of preventing unnecessary access and making sure everything stays secure.
3. Monitor Everything
If you’re not tracking activity, you’re leaving yourself open to risk. Regularly monitor your Kubernetes environment. This means logging everything—user actions, system processes, you name it. Auditing your activity means that if something goes wrong, you’ll know about it immediately. And that gives you the chance to react fast.
4. Use Network Policies Wisely
Network policies are your way to control how traffic flows between containers. Without proper network segmentation, your entire system could be exposed. By controlling which pods can talk to which services, you reduce the chance of lateral movement in case of an attack. It’s about making sure that only trusted connections get through.
5. Keep Everything Updated
You can’t afford to leave outdated containers or images running. Period. Regularly scan them for vulnerabilities and make sure they’re up to date. If there’s a vulnerability, patch it. And keep your containers locked down—this is the foundation of your security.
6. Harden the Container Runtime
Your container runtime is the engine of your Kubernetes environment. If it’s not secure, nothing else matters. Make sure the runtime is configured properly and running the latest, most secure version. Hardening the runtime means fewer ways for attackers to get in.
7. Set Resource Limits
If your containers are running wild and taking too many resources, you’ve got a problem. Set resource limits to control what each container can consume. This helps prevent denial of service attacks and ensures one container doesn’t bring down the whole cluster.
8. Implement Real-Time Monitoring Tools
You need real-time security monitoring tools. There’s no room for delays. These tools will scan your Kubernetes environment constantly and alert you to anything suspicious before it becomes a problem. It’s not about reacting after the fact—it’s about stopping things before they escalate.
9. Scan Continuously for Vulnerabilities
Don’t just scan once and forget about it. Make vulnerability scanning a regular part of your security process. Your containers, your clusters—everything should be checked regularly. The sooner you catch a vulnerability, the sooner you can fix it. Stay on top of things, and you’ll stay ahead of potential attacks.
10. Shift Left for Security
Security shouldn’t be something that comes after development. It should be built into your process from the start. A shift-left approach means addressing security in the early stages of development. This helps catch issues before they reach production. When you do this, you save time, effort, and a lot of risk.
CloudDefense.AI: A Comprehensive Solution for Kubernetes Security
As cloud computing rapidly transforms, securing Kubernetes environments has become non-negotiable for businesses. This is where CloudDefense.AI makes a difference.
CloudDefense.AI is a top-tier security platform that goes far beyond traditional security methods. It provides a unified approach to cloud security, offering a solution that is specifically designed to handle Kubernetes environments efficiently and securely.
CloudDefense.AI’s Unique Security Features for Kubernetes Runtime
CloudDefense.AI stands apart because of its deep focus on securing Kubernetes from all angles. This integrated solution covers everything from vulnerability management to real-time threat detection, ensuring that your Kubernetes infrastructure is always protected.
Vulnerability Management
CloudDefense.AI makes vulnerability management easy and proactive. With CloudDefense.AI, there’s no need for external agents or complicated scans. The platform scans your cloud environments—whether they’re virtual machines, containers, or serverless applications—identifying vulnerabilities at every level. By continuously checking for weaknesses across your infrastructure, CloudDefense.AI ensures you can address potential security issues before they become major problems.
Container & Kubernetes Security
CloudDefense.AI provides specialized security for containers and Kubernetes, allowing teams to deploy containerized apps with the confidence that security won’t be compromised. The platform secures Kubernetes environments at every stage of the development lifecycle, from building to real-time operation. With CloudDefense.AI, you get full visibility and control over your containers and cloud infrastructure, meaning security is built into the process, not tacked on later.
Cloud Threat Detection and Response
CloudDefense.AI provides real-time monitoring and threat detection tailored for Kubernetes environments, identifying suspicious activity across pods, containers, and clusters. Using behavior analysis and threat intelligence, it detects unauthorized access, privilege escalation, and container breakouts. Automated responses contain threats instantly, ensuring fast mitigation with minimal disruption to your cloud-native applications.
Policy Enforcement and Compliance
With CloudDefense.AI, enforcing security policies across Kubernetes environments is simple and automated. It offers prebuilt policy templates for standards like NIST, PCI-DSS, HIPAA, and CIS, ensuring compliance from development through production. Centralized governance and automated audits ensure consistent security while simplifying compliance reporting for regulatory needs.
Supply Chain Security
CloudDefense.AI secures your Kubernetes software supply chain by continuously scanning container images, Helm charts, and IaC templates for vulnerabilities and misconfigurations. Integrated into CI/CD pipelines, it blocks insecure components from reaching production and maintains a detailed SBOM, providing full visibility into dependencies and rapid response to emerging supply chain threats.
Conclusion
Kubernetes security is complex, but CloudDefense.AI simplifies it by bringing all essential protections into one platform. From scanning containers for vulnerabilities to enforcing policies and detecting threats in real time, it covers the full security lifecycle. It also helps businesses stay compliant and secure their supply chains, which is critical as attacks increasingly target open-source components. With CloudDefense.AI, teams gain visibility and control without disrupting workflows, making it easier to manage Kubernetes security proactively rather than scrambling to react after something goes wrong.







