What is KSPM?
Kubernetes Security Posture Management (KSPM) is a holistic way to secure Kubernetes clusters and workloads, which are complex environments that can be vulnerable to various threats. It involves a set of processes and tools designed to:
- Continuously monitor the cluster for vulnerabilities, misconfigurations, and suspicious activity.
- Detect and address potential security risks on time.
- Enforce security policies and ensure adherence to compliance requirements.
- Automate security tasks to streamline operations and reduce human error.
KSPM is crucial because even a single misconfiguration or unpatched vulnerability in a Kubernetes cluster can lead to a major security breach. By automating various security tasks, KSPM helps organizations:
- Reduce the risk of human error and oversight.
- Improve the efficiency of their security operations.
- Maintain compliance with relevant security regulations.
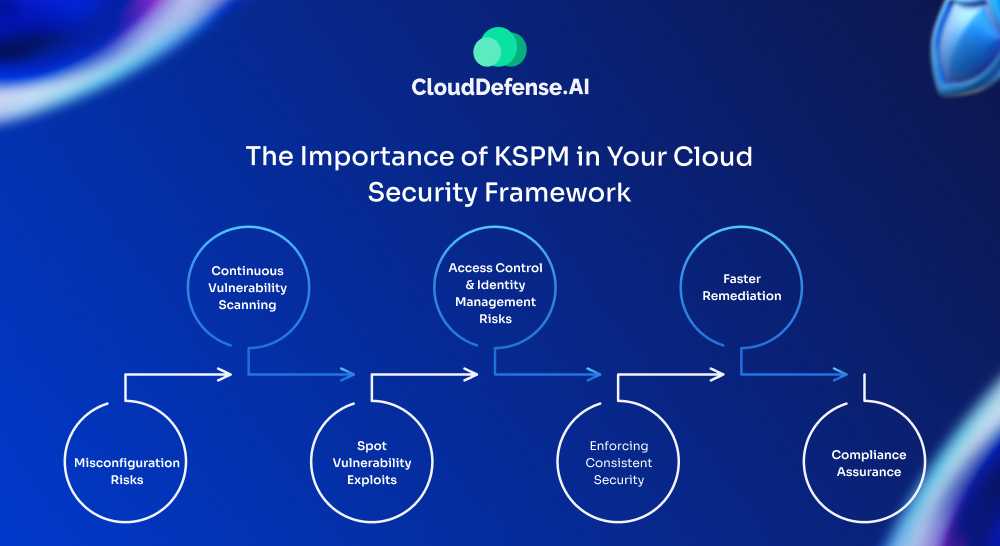
The Importance of KSPM in Your Cloud Security Framework
Imagine you’ve meticulously built a microservices application using containers, orchestrated perfectly by Kubernetes. It’s efficient and scalable, and everything is running smoothly. But a tiny oversight lurks beneath, waiting to be exploited.
For instance, let’s say a developer accidentally adds an extra comma in a YAML file that defines network policies. What seems like a minor error might inadvertently grant unauthorized access to a container, risking sensitive data or even disrupting critical services. This is where KSPM steps in, constantly patrolling your clusters for these hidden weaknesses.
Let’s see how KSPM plays out in a real-world scenario:
Misconfiguration Risks
Misconfigurations are a common source of security gaps. Even a small error, like incorrect network policies or improper resource limits, can lead to significant vulnerabilities. KSPM helps identify and rectify these common misconfigurations before they can be exploited, ensuring your environment remains secure.
Continuous vulnerability scanning
Nowadays, cyber threats are constantly evolving to be more sophisticated than ever before. New vulnerabilities pop up in container images, misconfigurations sneak in, and attackers develop novel methods to exploit weaknesses. KSPM serves as your early warning system, continuously scanning for these threats and ensuring your defenses remain robust and up-to-date.
Spot Vulnerability Exploits
Security vulnerabilities can lurk anywhere. For example, imagine a critical vulnerability found in a popular logging library used in your container images. If you don’t patch it promptly, attackers could exploit it to gain entry into your cluster and deploy harmful code. KSPM keeps an eye out for these vulnerabilities, integrating with patching tools to automatically update vulnerable container images, which helps close the window for potential exploitation.
Access Control and Identity Management Risks
Managing access control and identities in a Kubernetes environment can be tricky. If roles and permissions are misconfigured, it could allow unauthorized users access to critical resources. KSPM helps enforce strict identity and access management policies, ensuring that only the right people have access to what they need, and nothing more.
Enforcing Consistent Security
Maintaining consistent security across multiple Kubernetes clusters can be challenging. KSPM helps by allowing you to define organization-wide security policies. These policies become the gold standard for all your clusters, ensuring a baseline level of security is always in place.
For example, a policy might dictate that all container images must be scanned for vulnerabilities before deployment. KSPM continuously monitors for violations of these policies, alerting you to any deviations, so non-compliant deployments are prevented.
Faster Remediation
KSPM goes beyond simply identifying vulnerabilities. It can integrate with vulnerability management and patch management tools. Upon detecting a critical vulnerability, KSPM can trigger automated patching processes, ensuring your clusters are swiftly updated and protected against known exploits. This automation streamlines remediation and significantly reduces the risk window associated with vulnerabilities.
Compliance Assurance
Many organizations are subject to strict security regulations, such as PCI-DSS or HIPAA. KSPM simplifies compliance by providing detailed reports and audit trails on your Kubernetes security posture. This allows you to demonstrate adherence to regulatory requirements with greater ease.
| Did you know? More than 380,000 open Kubernetes API servers are currently exposed on the Internet, making up 84% of all Kubernetes API instances visible globally. |
Essential Components for Secure Kubernetes
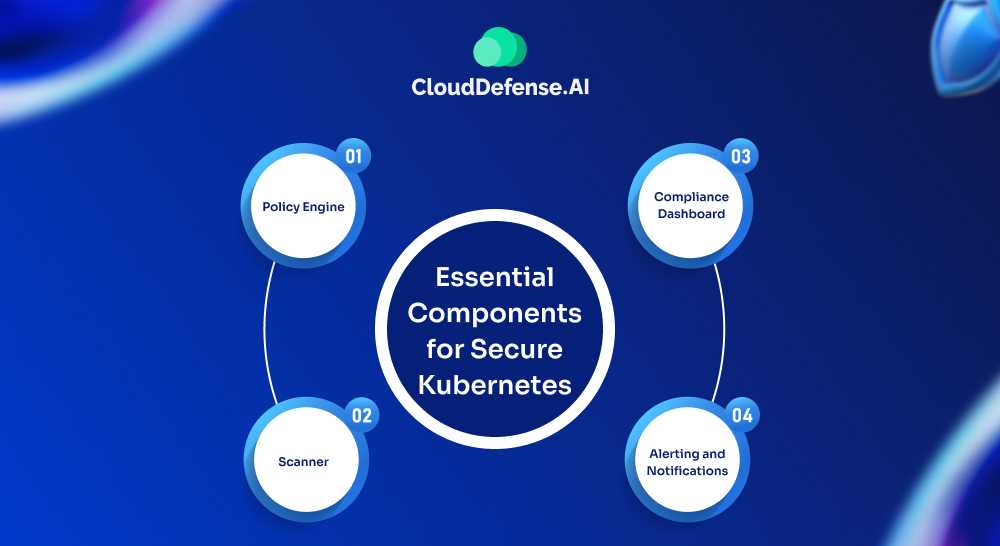
KSPM tools offer various features and functionalities, but most commonly include the following key components:
Policy Engine: This policy engine is like the main control center for a KSPM solution. It sets and controls the security rules that the KSPM tool will apply. These rules can cover different parts of Kubernetes safety, like controlling who can access the network, setting security levels for pods, and managing permissions with RBAC (which means deciding roles for users).
Scanner: The scanner’s job is to continuously scan the Kubernetes cluster and its workloads to identify any deviations from the established security policies defined by the policy engine. When it scans, it may involve inspecting configurations, container images, and workload activity for vulnerabilities, misconfigurations, and suspicious behavior.
Compliance Dashboard: The compliance dashboard provides a centralized view of the security posture of the Kubernetes cluster. It visualizes the results of the KSPM scans, pointing out the areas where the cluster is compliant or non-compliant with the defined security policies. This way, security teams can quickly identify and prioritize potential security risks.
Alerting and Notifications: KSPM solutions typically integrate alerting and notification systems to promptly inform security teams about detected policy violations or suspicious activities within the Kubernetes cluster. These alerts can be sent via various channels, such as email, SMS, or integrated security information and event management (SIEM) platforms.
In addition to these core components, KSPM solutions may also offer other functionalities, including:
- Remediation capabilities: KSPM tools can recommend or even automate remediation actions to address identified security vulnerabilities or misconfigurations.
- Integration with other security tools: KSPM solutions can integrate with other security tools like vulnerability scanners, container image registries, and cloud workload protection platforms (CWPP) to provide a comprehensive security posture across the entire cloud-native environment.
| Read more: If you’re new to Kubernetes or want to better understand the foundation of a secure container environment, check out our comprehensive article on Kubernetes Clusters. |
How does KSPM Work?
Kubernetes Security Posture Management (KSPM) is a vital part of a Cloud-Native Application Protection Platform (CNAPP). It gives organizations the insights and control they need to secure their container environments. Let’s break down the key stages of KSPM and see how it enhances security:
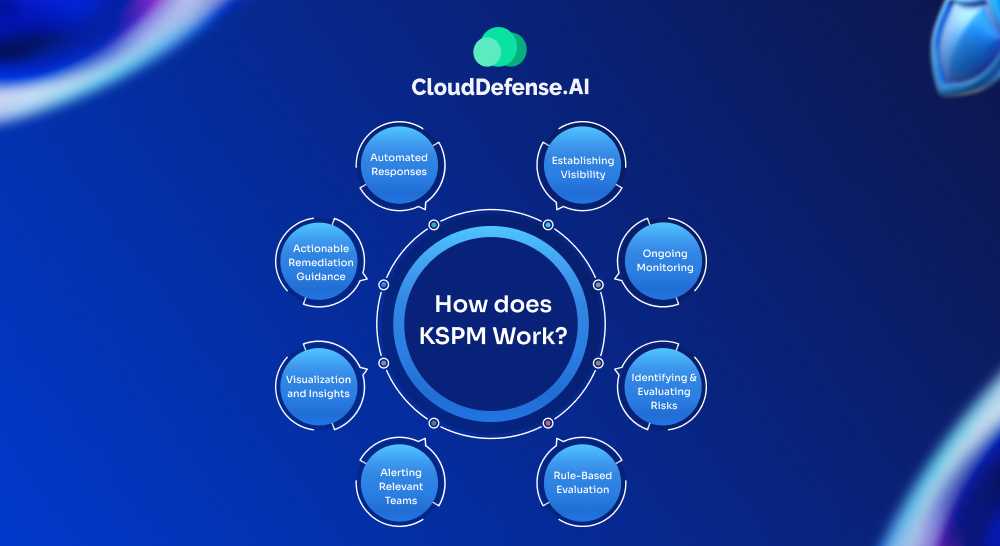
1. Establishing Visibility
The first step in KSPM is all about visibility. It’s crucial to have a comprehensive understanding of your Kubernetes cluster. This involves mapping out every component—like nodes, pods, and services—to see how they interact. By doing this, your team can identify potential vulnerabilities and gain insights into the overall security landscape. It’s like having a detailed map that shows you where the risks lie.
2. Ongoing Monitoring
Next, KSPM emphasizes the importance of continuous monitoring. Cyber threats evolve rapidly, and KSPM keeps pace by regularly scanning your Kubernetes ecosystem. It gathers data on various security aspects, such as misconfigurations and vulnerable container images. This ongoing surveillance means you won’t be caught off guard; instead, you’ll always be informed about the state of your security.
3. Identifying and Evaluating Risks
Once the data is in, KSPM analyzes it to pinpoint risks and vulnerabilities. This step is crucial; it compares your current configurations against recognized industry standards and best practices. If there are areas that need attention—whether due to misconfigurations or outdated practices—you’ll know about them right away. This assessment allows your team to prioritize actions based on real, tangible risks, making security management far more effective.
4. Rule-Based Evaluation
KSPM operates based on a set of well-defined rules that guide security practices. These rules address different areas, including access management, network policies, and container security.
By applying these rules to the collected data, KSPM can highlight any deviations from established best practices. If something is amiss—like a misconfigured access policy—you’ll be alerted, allowing your team to take corrective action before issues escalate.
5. Alerting Relevant Teams
Timely alerts are a hallmark of effective security management. KSPM is designed to notify the right teams as soon as it detects potential security threats or configuration errors.
For instance, if sensitive data is found in a container that shouldn’t have access to it, the appropriate development or operations team will receive an alert right away. This ensures that issues are addressed promptly, reducing the risk of a data breach.
6. Visualization and Insights
Understanding your security posture becomes much easier with KSPM’s visualization tools. It provides dashboards and reports that offer a clear view of your Kubernetes environment. With these visual insights, your team can easily interpret security metrics and compliance statuses.
This feature is particularly useful for stakeholders who need to grasp complex data quickly and make informed decisions based on what they see.
7. Actionable Remediation Guidance
KSPM doesn’t just stop at identifying issues; it also provides practical steps for remediation. When it spots vulnerabilities or policy violations, KSPM offers concrete recommendations tailored to your specific situation.
Whether you need to adjust access controls, refine network settings, or change configurations, the guidance is actionable and straightforward, making it easier for your team to respond effectively.
8. Automated Responses
Another powerful aspect of KSPM is its ability to integrate with automation tools. When security threats are detected, KSPM can automate responses, applying patches or enforcing security policies based on predefined rules. This capability helps streamline the remediation process, allowing your team to focus on more strategic tasks rather than getting bogged down with manual interventions.
| Read more: We’ve curated a comprehensive Kubernetes Security Checklist to safeguard your Kubernetes environment—check it out now! |
KSPM vs. CSPM
While both KSPM and CSPM (Cloud Security Posture Management) play vital roles in securing your cloud infrastructure, they address distinct aspects and cater to different needs. Here’s a breakdown of their key differences:
Scope:
- KSPM: Focuses solely on the security of “Kubernetes clusters”. It ensures the secure configuration, vulnerability management, and compliance of containerized environments orchestrated by Kubernetes.
- CSPM: Offers a broader spectrum of security management across your entire “cloud environment”. This includes securing cloud resources like virtual machines, databases, storage, and networking components, along with Kubernetes clusters if deployed in the cloud.
Functionalities:
- KSPM: Specializes in:
- Kubernetes-specific vulnerability scanning: Analyzes container images and cluster configurations for vulnerabilities specific to the Kubernetes ecosystem.
- Misconfiguration detection in YAML files: Identifies errors and non-compliant settings within Kubernetes configuration files.
- Network security analysis within Kubernetes clusters: Monitors network activity for suspicious behavior and potential breaches.
- CSPM: Provides a wider range of functionalities, including:
- Cloud resource security assessment: Evaluates the security posture of various cloud resources beyond Kubernetes.
- Compliance management: Assists in meeting industry regulations and compliance standards across the entire cloud environment.
- Cloud IAM (Identity and Access Management) monitoring: Ensures proper access controls and permissions for cloud resources.
Deployment:
- KSPM: Can be deployed on-premises or in the cloud, wherever your Kubernetes clusters reside.
- CSPM: Primarily designed for cloud environments, often offered as a service by cloud providers or as standalone solutions.
Here is the table for your easy understanding:
| Feature | KSPM | CSPM |
| Scope | Secure Kubernetes clusters | Secure the entire cloud environment (including Kubernetes clusters deployed in the cloud) |
| Functionalities | Vulnerability scanning, misconfiguration detection, network security analysis (specific to Kubernetes) | Cloud resource security assessment, compliance management, IAM monitoring, broader range of security functionalities |
| Deployment | On-premises or in the cloud | Primarily cloud-based (offered as a service or standalone solution) |
| Ideal for | Organizations primarily concerned with securing their Kubernetes clusters | Organizations requiring comprehensive cloud security management |
| Used in conjunction with | CSPM for organizations with significant cloud deployments and hybrid environments | KSPM for organizations focused on Kubernetes security within a broader CSPM strategy |
What should you look for in a KSPM solution?
Choosing the right KSPM solution is essential for safeguarding your cloud-native applications. To maximize the benefits of KSPM, it’s crucial to see how it fits within a CNAPP.
A CNAPP seamlessly integrates various security measures, offering a unified approach that combines preventative strategies with real-time threat detection. With that in mind, let’s explore the key features you should look for in a KSPM solution:
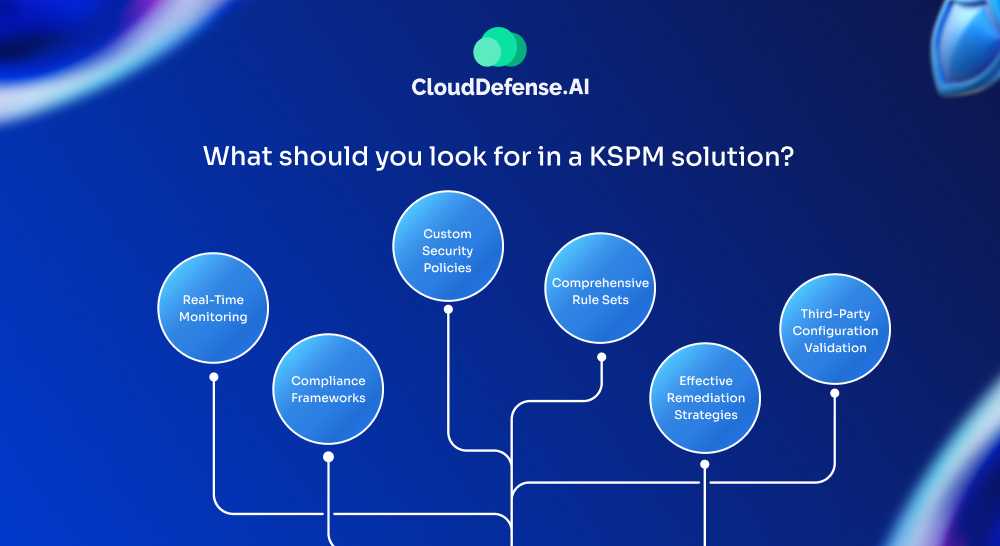
1. Real-Time Monitoring
Select a KSPM tool that offers continuous monitoring of your Kubernetes environment. This feature should provide instant visibility into important elements like RBAC settings, workloads, and cluster nodes. Quick detection of potential security threats ensures that your team can respond before issues escalate. For instance, check whether the solution can verify that APIs are properly secured with bearer tokens for effective RBAC management.
2. Compliance Frameworks
A solid KSPM solution should include built-in assessments for major industry compliance standards, including CIS benchmarks, GDPR, HIPAA, and PCI-DSS. The ability to generate detailed reports and offer practical recommendations for compliance is vital. For example, the KSPM should be able to check for TLS encryption on ingress controllers to meet necessary regulatory requirements.
3. Custom Security Policies
The ability to create and customize security policies tailored to your organization’s unique needs is crucial. Look for a KSPM solution that allows you to set up access control, network, and container security policies. This customization helps ensure consistent application of security measures across your Kubernetes landscape, making it easier to manage risks.
4. Comprehensive Rule Sets
A good KSPM solution should come with a robust collection of built-in security rules covering critical areas like authentication, authorization, and network security. Check if the solution can assess and enforce pod security policies for all namespaces in your Kubernetes setup. This proactive approach helps identify vulnerabilities and aligns with industry best practices.
5. Effective Remediation Strategies
Your KSPM solution should not only identify vulnerabilities but also provide clear, actionable steps for remediation. Look for features that automate certain remediation processes or guide your team through resolving security issues quickly. This will help minimize risks and ensure your Kubernetes environment remains secure.
6. Third-Party Configuration Validation
In many cases, organizations integrate Kubernetes with various third-party tools. A KSPM solution that can validate configurations and YAML files for these integrations is essential. This capability ensures that any third-party tools meet your security standards before being deployed in your production environment.
KSPM Best Practices: Optimizing Your Kubernetes Security Posture
KSPM is a powerful tool for safeguarding your containerized environments, but to maximize its effectiveness, following best practices is crucial. Here are some key recommendations:
1. Implement Continuous Monitoring
- Schedule regular scans to identify vulnerabilities, misconfigurations, and policy violations promptly. Don’t rely on manual scans – set them to run automatically.
- Integrate continuous scanning into your CI/CD pipeline to identify and address security issues early in the development lifecycle.
2. Prioritize and Remediate:
- Don’t get overwhelmed by vulnerability reports. Categorize risks based on severity and prioritize addressing critical vulnerabilities first.
- Leverage KSPM’s integration with remediation tools to automate patching processes and fix misconfigurations whenever possible.
- Establish clear remediation timelines and track your progress to ensure timely resolution of security issues.
3. Leverage Compliance Features:
- Utilize KSPM’s compliance reporting capabilities to demonstrate adherence to industry regulations and security standards.
- Automate compliance reporting to streamline audits and simplify the process of maintaining compliance.
4. Stay Updated:
- Ensure you’re using the latest version of KSPM to benefit from the newest features, vulnerability databases, and security best practices.
- Regularly update container images within your clusters to address newly discovered vulnerabilities and ensure they use the latest secure versions of software dependencies.
5. Integrate with CI/CD Pipeline:
- Integrate KSPM scans into your CI/CD pipeline to identify and address vulnerabilities early in the development lifecycle, before deployment to production environments.
6. Promote Collaboration and Awareness:
- Raise awareness about KSPM within your organization and educate developers, security teams, and operations personnel on its functionalities.
- Encourage collaboration between development and security teams to integrate security considerations throughout the software development lifecycle.
- Regularly review KSPM reports and findings with relevant stakeholders to ensure everyone is informed about the security posture of your Kubernetes environment.
Wrapping up: CloudDefense.AI’s KSPM Approach
Kubernetes Security Posture Management (KSPM) is an essential tool for securing Kubernetes clusters, but it should be viewed as part of a larger security strategy. When integrated with a comprehensive platform like CloudDefense.AI’s Cloud Native Application Protection Platform (CNAPP), KSPM becomes even more powerful. This approach enhances your overall security posture, giving you a deeper, more unified defense against potential threats.
Complete Visibility Across Your Environment
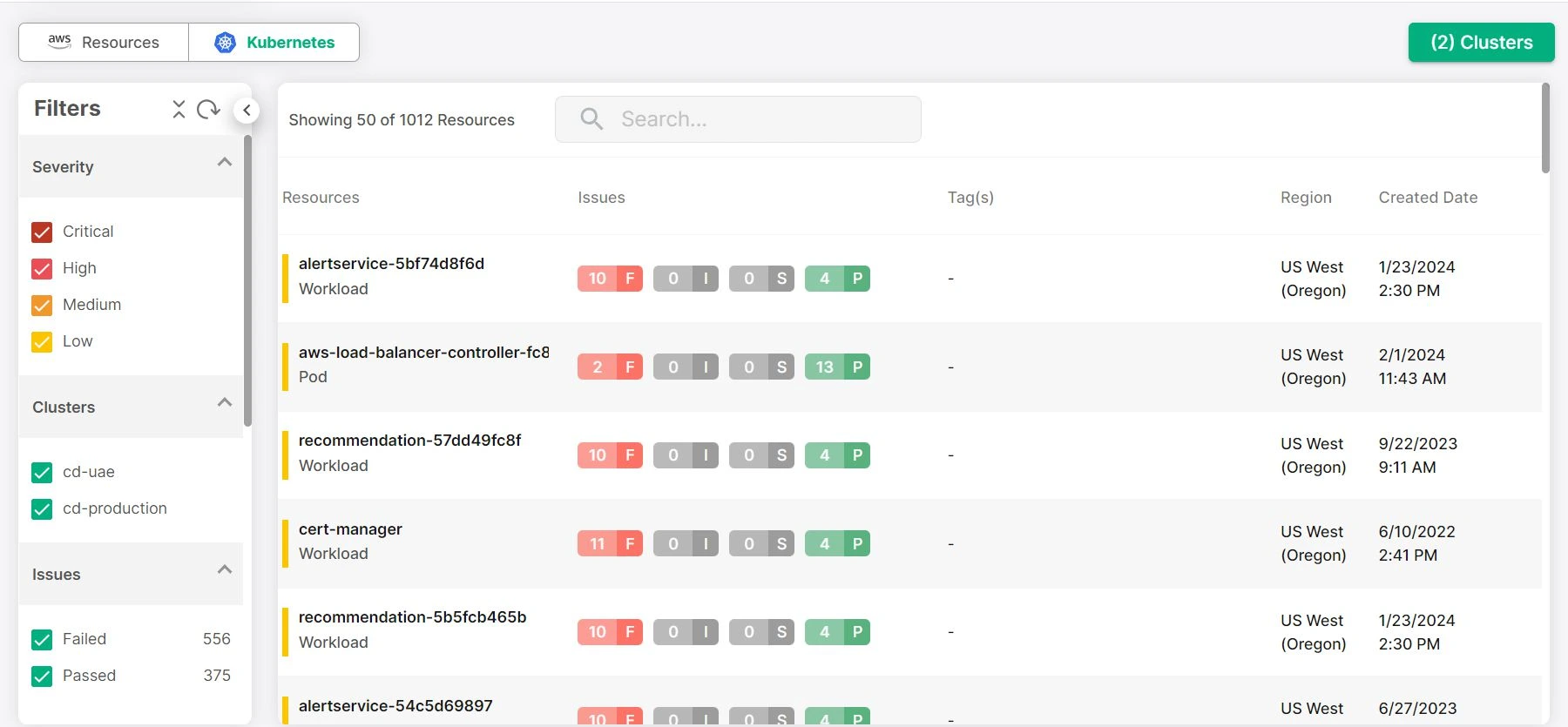
CloudDefense.AI provides a holistic view of your cloud-native infrastructure. This allows for accurate and informed decisions about your Kubernetes security, from risk assessments to mitigation strategies. With everything connected, you’re not left in the dark about the status of your clusters and services.
Thorough Kubernetes Risk Assessment
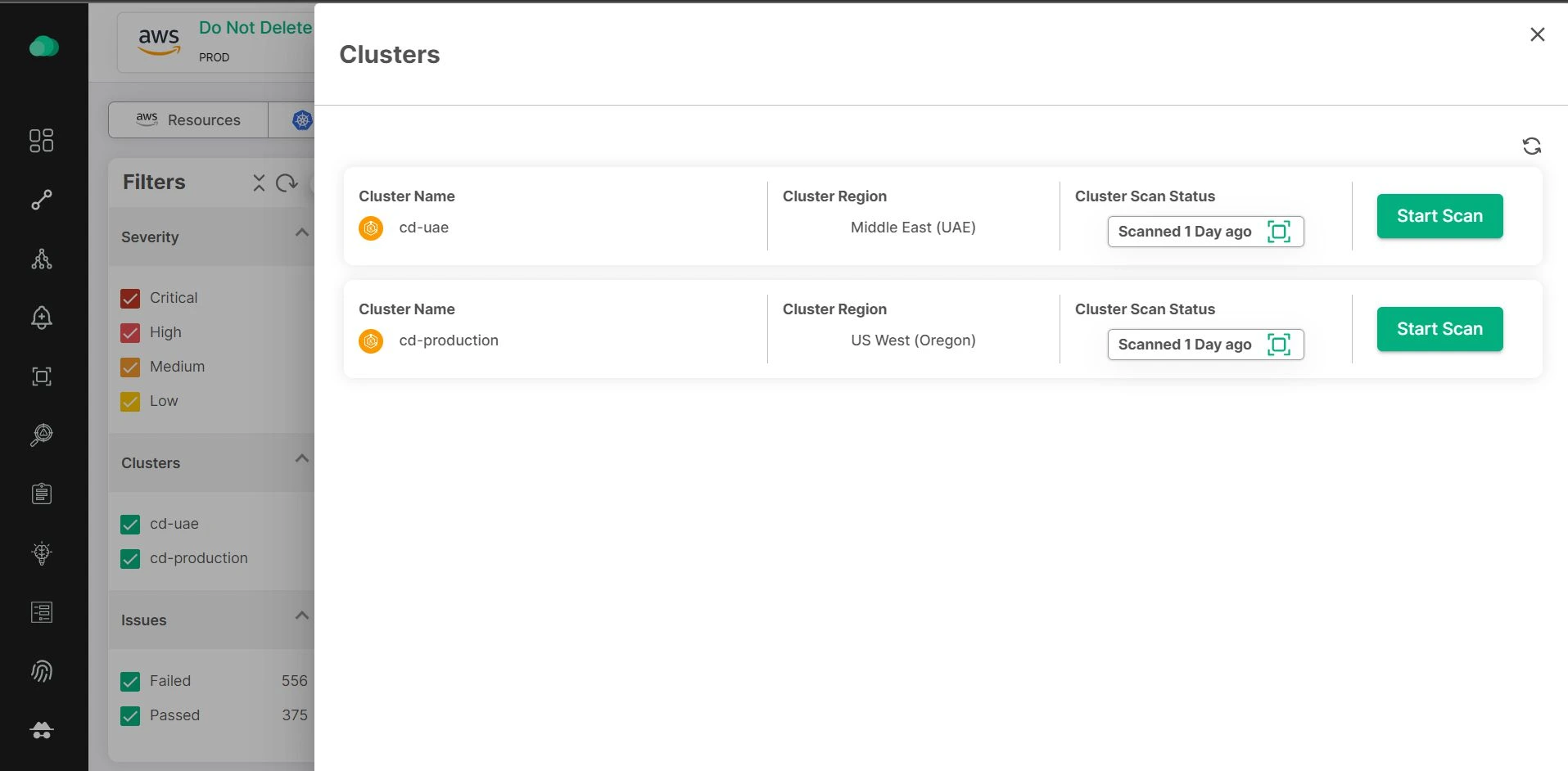
CloudDefense.AI offers in-depth assessments tailored to your Kubernetes environment. By analyzing the unique components of your clusters, the platform provides insights into potential risks and vulnerabilities, enabling you to prioritize remediation efforts effectively.
Context-Aware Security
CloudDefense.AI understands the bigger picture. It collects and analyzes data from across your cloud-native space, offering context-driven real-time security insights. This approach helps reduce false alarms and ensures you’re addressing real threats instead of wasting time on irrelevant issues.
Built-in & custom rules
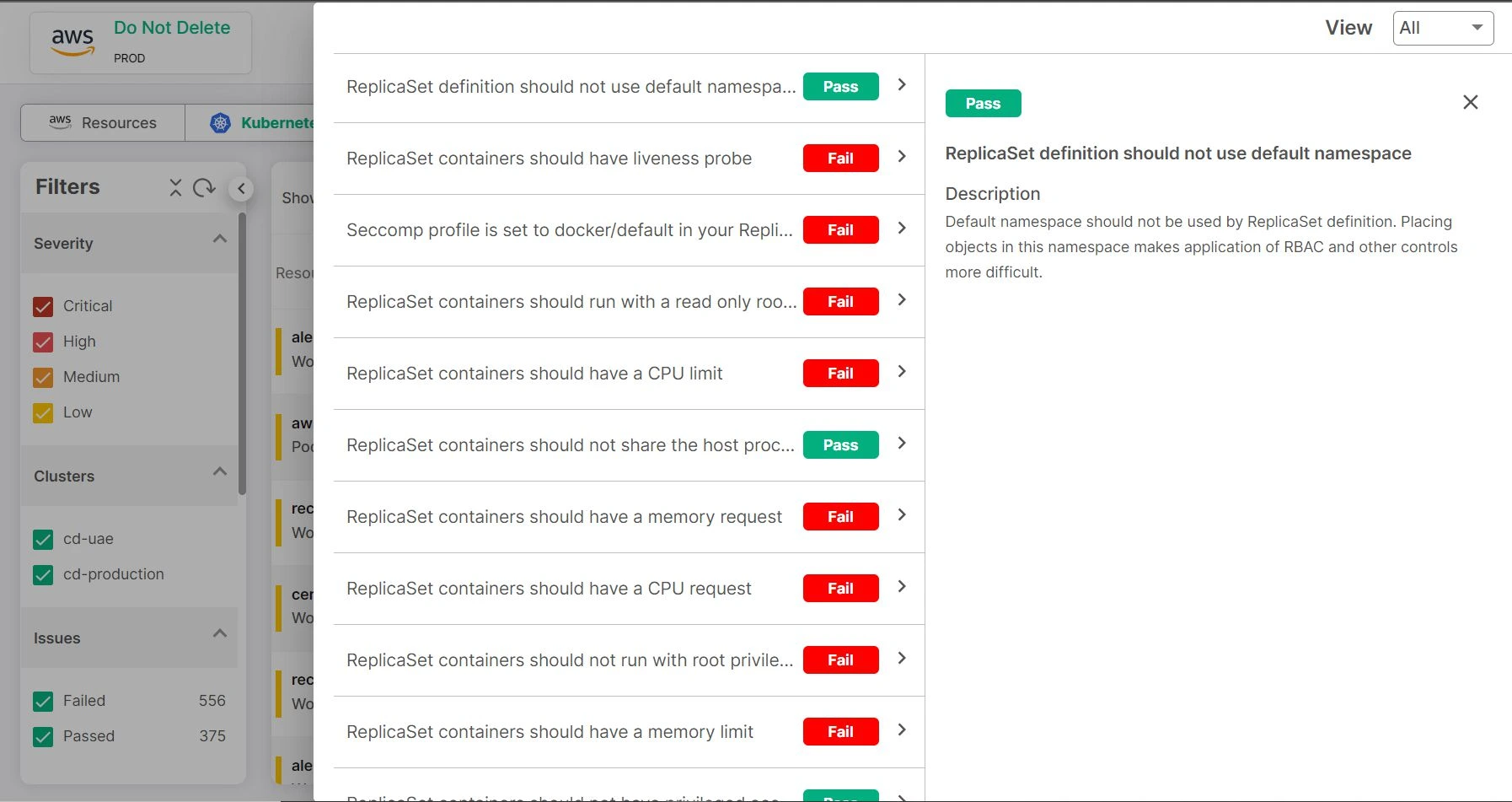
CloudDefense.AI enforces security policies throughout your entire cloud-native infrastructure, from containers and Kubernetes to microservices. Both built-in and custom rules are applied consistently, ensuring your security measures are uniform and effective across all layers of your stack.
Simplified Security Management
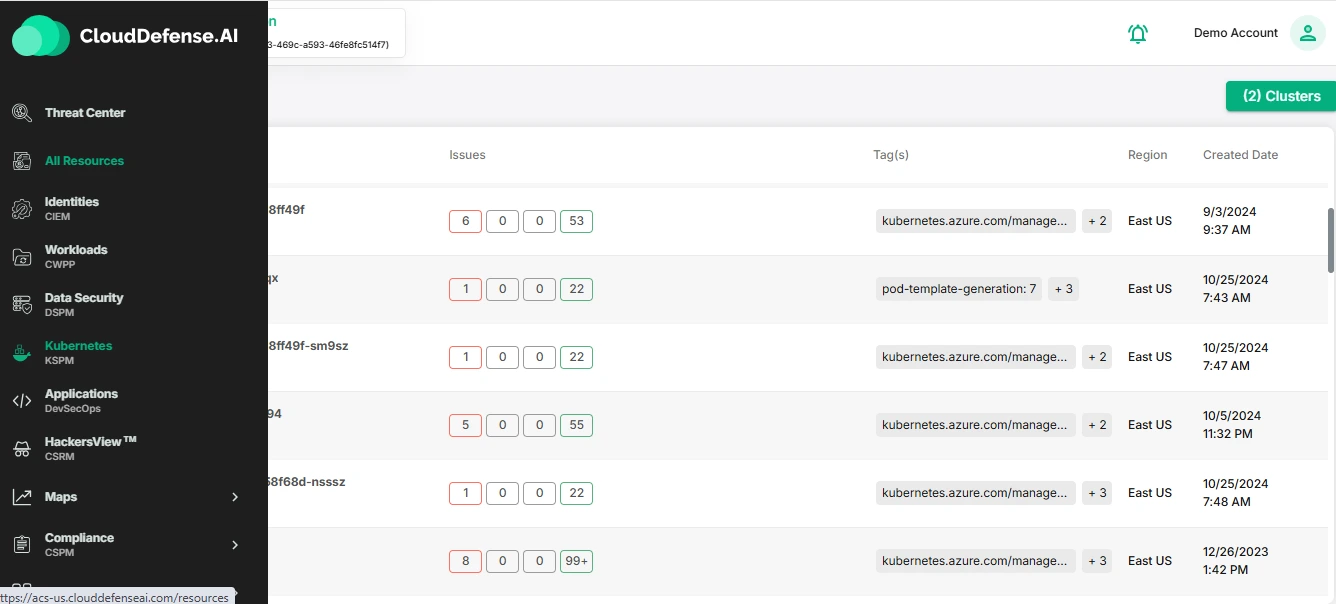
Managing security across multiple tools can be complex and time-consuming. By integrating KSPM into CloudDefense.AI’s CNAPP, you streamline security management. Everything is unified into one framework, making updates, monitoring, and management simpler and more efficient. This allows you to focus on bigger strategic security goals rather than dealing with individual security tools.
Risk Correlation and Prioritization
CloudDefense.AI uses advanced graph-based risk correlation to help you identify and prioritize the most critical threats. This data-driven approach ensures you’re addressing the most pressing issues first, reducing risk and enhancing the overall security of your cloud-native environment.
Overall, CloudDefense.AI offers a comprehensive CNAPP solution that seamlessly integrates KSPM. This empowers organizations to:
- Automate security and compliance across Kubernetes clusters.
- Secure all container workloads, achieving zero-trust security.
- Protect workloads across any cloud environment.
- Automate security and threat detection throughout the application lifecycle.
Ready to explore how CloudDefense.AI can elevate your Kubernetes security posture? Sign up for a free demo and discover how it empowers you to secure your containerized applications and data effectively.







