What is Infrastructure as Code (IaC)? IaC Defined
Infrastructure as Code (IaC) is the process of automating Infrastructure configuration by managing and provisioning the system through machine-readable files, instead of using manual configuration methods.
IaC primarily functions by using multiple pre-made configuration files. The system automatically uses these configuration files to cater to development needs. This process is fast and makes it easy to provision.
If we go by the Infrastructure as Code definition, we can tell you that automating the configuration of your infrastructure aids your enterprise in functioning more efficiently. It saves money and time while producing greater software deployment output.
What is IaC Scanning – Definition
At its core, IaC scanning is about addressing cloud configuration issues in the code itself, rather than in deployed cloud resources. It’s important to understand that IaC doesn’t represent the actual infrastructure but rather the blueprint for it. So, IaC security isn’t about “securing IaC” per se. Instead, it ensures that the code is configured to provision secure resources when deployed.
Now, to keep your infrastructure code secure, you gotta do a few things:
- Identify vulnerabilities: Detect potential security flaws in your IaC scripts.
- Automate checks: Run regular scans to ensure continuous security.
- Fix issues early: Address problems in the code before deployment.
- Ensure compliance: Verify that your code meets security standards and policies.
This method is a game-changer compared to the old-school way of doing things. Back in the day, security teams only looked at issues after resources were deployed and manually set up. IaC scanning flips that script, putting the focus on catching issues in the code itself before they hit production.
When it comes to cloud security, it’s mostly about keeping the important stuff locked down and making sure customer data doesn’t end up in the wrong hands. Every cloud platform has its own set of “best practices” and rules to follow. And on top of that, your company probably has its own specific policies based on what you’re doing and what kind of setup you have.
Cloud security usually means keeping an eye on access to important services and protecting customer data. With each cloud platform and resource having its own security rules and benchmarks, plus your company’s specific policies, IaC scanning helps you build security right into your code. It’s like getting ahead of problems before they even hit your live environment.
Challenges of IaC
IaC has simplified the complex provisioning and management process of Infrastructures. Even with the many benefits, there are a few aspects of working with IaC that may introduce the system to security issues.
1. Image Vulnerabilities While Configuring Templates
While provisioning infrastructures, developers choose to use images in IaC templates. These open up vulnerabilities in the infrastructure if the images aren’t obtained from a secured registry. For configuring the infrastructure, developers often include security keys, IP addresses, and access codes in the IaC template. Anyone who manages to gain access to the system using the vulnerabilities can choose to make use of this sensitive information.
2. Configuration Drift
Configuration drift occurs mainly when an IaC is active and changes are made in the configuration. This causes the unchangeability of cloud infrastructure to be broken and opens the grounds for more human errors. This can be ignored by simply not making any changes once an infrastructure has been provisioned. In case changes need to be made, a new infrastructure should be made with the desired configurations.
3. Untagged Assets
Often a lot of resources remain untagged when IaC is operating. Also known as ‘ghost assets’ are hard for developers and quality testers to detect and manage. Moreover, these resources often act as a vulnerability that becomes hard to mitigate. Tagging these ghost resources is essential in ensuring a secure and efficient infrastructure.
Why is IaC Scanning Crucial?
IaC is pretty much the standard in development these days, helping teams roll out cloud resources fast and consistently. But let’s be real—it’s not without its risks. Gartner even says that by 2025, 99% of cloud security failures will be the user’s fault, mostly due to misconfigurations.
Skipping out on IaC scanning leads to:
- Uncontrolled network access: Without proper checks, anyone could access your sensitive resources.
- Data breaches from poor permissions: Misconfigured permissions can open the door to unauthorized data access.
- Unencrypted data exposure: Failing to encrypt storage systems puts your data at risk of being compromised.
- Credential leaks: Hardcoded credentials in your IaC files can be easily exploited by attackers.
With developers constantly under the pump to push out new features, it’s easy to skip over these security checks. That’s why IaC scanning that doesn’t bog down your developers is a non-negotiable way of keeping your security tight.
Think about it: infrastructure code is just like any other code—it needs testing. But who’s got the time to sift through templates manually? Even if you’re up for it, human error is always lurking around the corner. That’s where IaC scanning tools step in. They automate the whole process, making sure every line of your code is locked down and secure.
Skipping out on IaC scanning is like leaving your car unlocked with the keys in it. Eventually, something’s gonna go wrong. To keep your cloud setup safe and sound, IaC scanning isn’t just a nice-to-have—it’s a must.
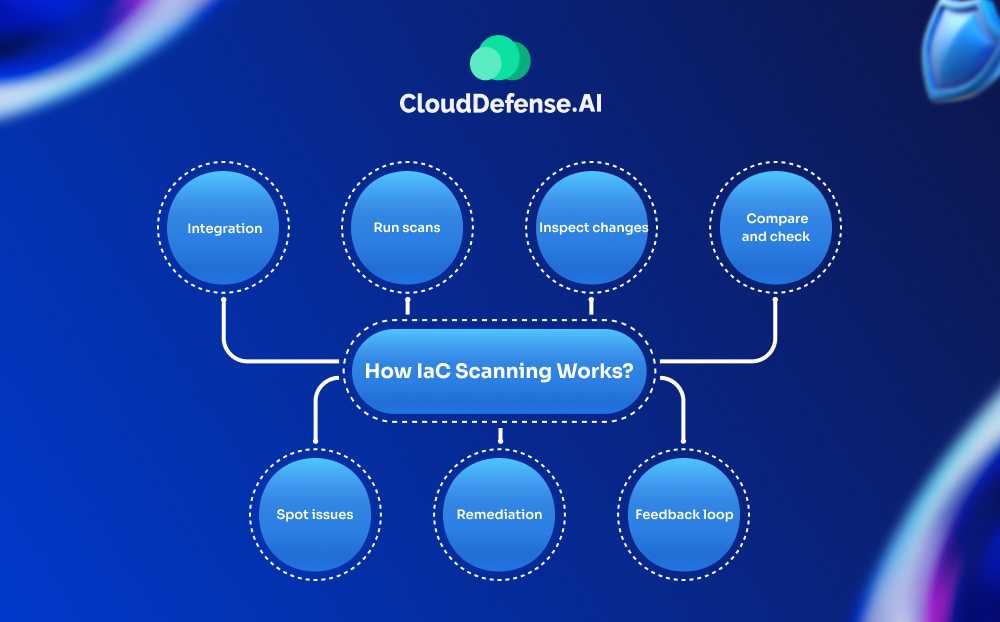
How IaC Scanning Works?
So, for ages, tech folks have been using tools like SCA (software composition analysis) and SAST (static application security testing) to check their code for bugs and security holes. But here’s the thing – most of these tools weren’t really built with IaC scripts in mind. They were more focused on regular app code, you know?
That’s why we ended up needing special tools just for scanning IaC stuff. But no matter which IaC scanner you’re using, the basic idea is pretty much the same.
Here’s how it goes down:
1. Integration: First off, you plug the IaC scanner into your development workflow. It’s like adding an extra step before you build anything.
2. Run scans: Then, this scanner goes to town on your IaC templates. It’s looking for any config errors or security no-nos. It’s pretty smart—it can spot when you’ve made changes to the infrastructure that don’t match up with the original template.
3. Inspect changes: Here’s where it gets interesting. The scanner takes all the bits and pieces of your IaC—templates, modules, files, you name it—and compares them against a list of security rules and best practices. It’s like having a really picky proofreader but for your infrastructure code.
4. Compare and check: After that, it starts hunting for anything that’s missing or just not quite right. Maybe you forgot to set a variable, or some setting doesn’t meet the legal requirements. The scanner catches all that stuff.
5. Spot issues: If it finds any problems, it lets your DevSecOps team know right away. This is clutch because it means you can fix these issues before you actually deploy anything. It’s like catching a mistake in your shopping list before you leave for the store, instead of realizing you forgot something important when you’re already cooking.
6. Remediation: Once vulnerabilities are identified, take action to fix them. This could mean updating your IaC scripts or using verified, modular code snippets to bolster your infrastructure’s security.
7. Feedback loop: Create a feedback loop to continuously refine your IaC scanning policies and processes. This ongoing improvement process helps adapt to new threats and keeps security practices sharp.
The cool part about all this is that it’s happening right in the middle of your development process. You’re not waiting until everything’s built and running to check for problems. And let me tell you, this approach saves a ton of time and stress compared to the old way of doing things.
Instead of scrambling to fix security issues after your infrastructure is already up and running, you’re nipping those problems in the bud. It’s pretty slick when you think about it!
Benefits of Infrastructure as Code (IaC) Scanning
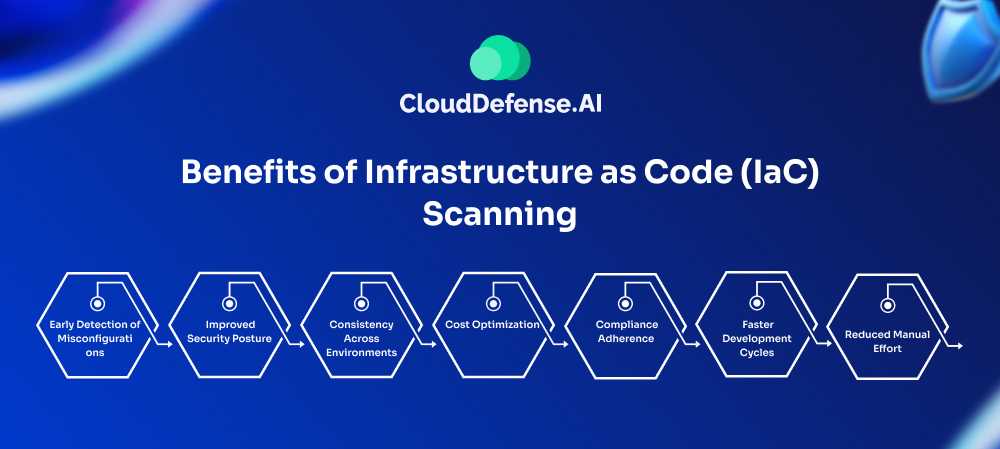
1. Early Detection of Misconfigurations
IaC scanning is like having a built-in safety net for catching mistakes before they hit production. Imagine your dev team accidentally making a database open to everyone in their Terraform script. With IaC scanning, that glaring mistake gets flagged during the code review. This lets you fix it before it ever sees the light of day, saving you a lot of headaches and time that would otherwise be spent dealing with problems after deployment.
2. Improved Security Posture
Running IaC scans is like getting a thorough check-up for your infrastructure. Say you’re setting up a new VPC with AWS CloudFormation, and your template is missing crucial network controls or using outdated encryption. Proper IaC scanning will call out these issues, ensuring your setup follows the latest security standards. This means fewer holes for attackers to exploit and a stronger defense overall.
3. Consistency Across Environments
With IaC scanning, you get a consistency like clockwork. Let’s say your site uses Ansible playbooks to manage infrastructure. By scanning these playbooks, you make sure that the same security settings, monitoring, and resource setups are applied everywhere—dev, staging, and production. This cuts down on environment-specific quirks and makes troubleshooting a whole lot easier.
4. Cost Optimization
IaC scanning can also save you some serious cash. Picture a startup using Terraform on Google Cloud Platform and accidentally setting up way too many high-end instances for low-traffic services. An IaC scan spots this before anything gets deployed, so you can adjust your resources and avoid wasting money. This means you spend only what you need and get the most bang for your buck.
5. Compliance Adherence
Staying compliant is a breeze with IaC scanning. Take a healthcare company using CloudFormation templates—an IaC scanner can check these templates against HIPAA requirements, making sure everything from encryption to access controls is spot on. This not only helps avoid compliance headaches but also makes audits smoother with clear documentation of your compliance efforts.
6. Faster Development Cycles
IaC scanning speeds up your development like nothing else. If your DevOps team is working with Kubernetes manifests, integrating scanning into your CI/CD pipeline means each change is automatically validated. This way, issues get flagged and fixed fast, letting you roll out updates quicker without getting bogged down by manual reviews.
7. Reduced Manual Effort
Automating IaC scanning takes a huge load off your shoulders. Imagine a cloud ops team managing hundreds of AWS accounts. Instead of manually checking every CloudFormation or Terraform file, IaC scanning automates the review process. This frees up your team to focus on more strategic tasks while keeping your infrastructure in line with all the required standards.
How CloudDefense.ai Helps in IaC Security
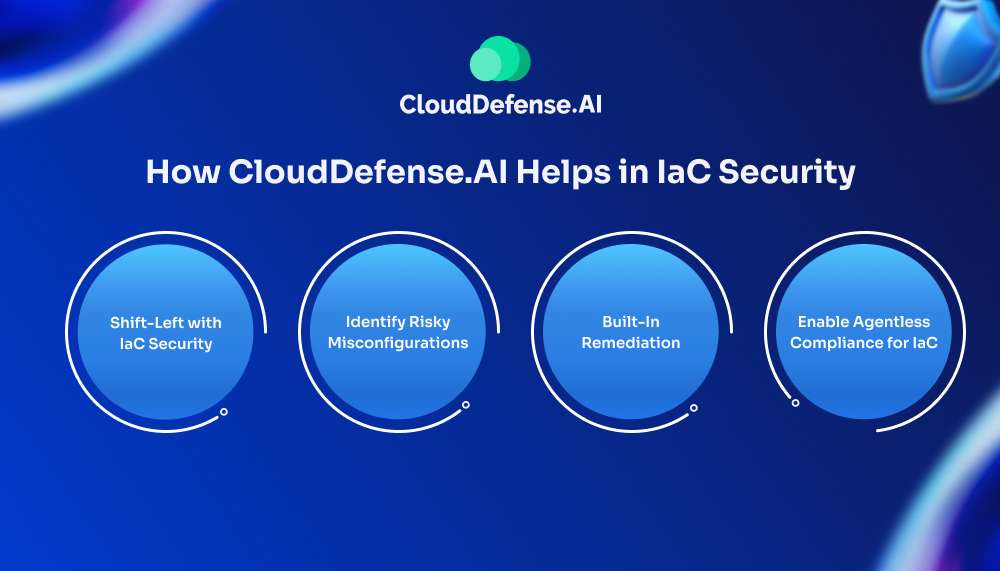
Shift-Left with IaC Security
CloudDefense.ai makes IaC security a breeze by catching issues early in the CI/CD pipeline. With its advanced scanning capabilities, you can spot and fix errors in your infrastructure code before they ever reach production.
This means fewer vulnerabilities and a smaller attack surface for your applications. Plus, CloudDefense.ai integrates policy as code and scanning directly into your CI/CD process, ensuring automated guardrails that cover every part of your development lifecycle.
- Integrate policies: Automate compliance checks and enforce security rules.
- Detect misconfigurations: Identify and correct risky setups before deployment.
- Fix issues early: Resolve critical security alerts with precision.
Identify Risky Misconfigurations
CloudDefense.ai seamlessly integrates with your CI/CD workflows to scan IaC scripts, like Terraform and CloudFormation, early on. You’ll get an early warning on any potential security issues, so you can tackle them before they blow up into bigger problems.
We help you prioritize risks according to industry standards or your own policies, giving your developers straightforward insights to fix what needs fixing—fast.
Built-In Remediation
When something goes wrong, CloudDefense.ai has your back with built-in remediation tools. Whether you need automated fixes or a bit of guided help, these tools help you sort out misconfigurations and other risks without breaking a sweat. This means you can quickly get everything back on track and ensure your infrastructure stays aligned with security best practices—no costly mistakes, no drama.
Enable Agentless Compliance for IaC
The platform’s got agentless scanning, meaning you can hit those compliance targets without a lot of setup or overhead. It continuously scans your IaC against industry benchmarks—like PCI-DSS, CIS benchmarks, SOC 2, and more—keeping you on the right side of the rules. Audit and compliance teams will love how easy it is to spot and fix policy gaps during development, reducing the risk of compliance issues and keeping things running smoothly.
Ready to see CloudDefense.ai in action? Book a free demo and check out how our IaC security solutions can speed up your development, boost your security, and keep you compliant. We’ll walk you through all the cool features and show you how to lock down your infrastructure from start to finish.







