What is Hacking?
Hacking refers to the act of identifying and exploiting vulnerabilities in a computer system, network, or digital device, often to gain unauthorized access to sensitive data.
While hacking can sometimes have ethical applications—such as penetration testing conducted by security professionals to uncover weaknesses—the term is more commonly associated with malicious activities.
Cybercriminals, widely known as hackers, employ a variety of techniques to bypass security measures, infiltrate systems, and steal, alter, or destroy data. These illicit activities often target sensitive information, disrupt services, and compromise organizational security.
Understanding the methods and motives behind hacking is essential for organizations and individuals to strengthen their defenses and ensure protection against cyber threats.
How does Hacking Work?
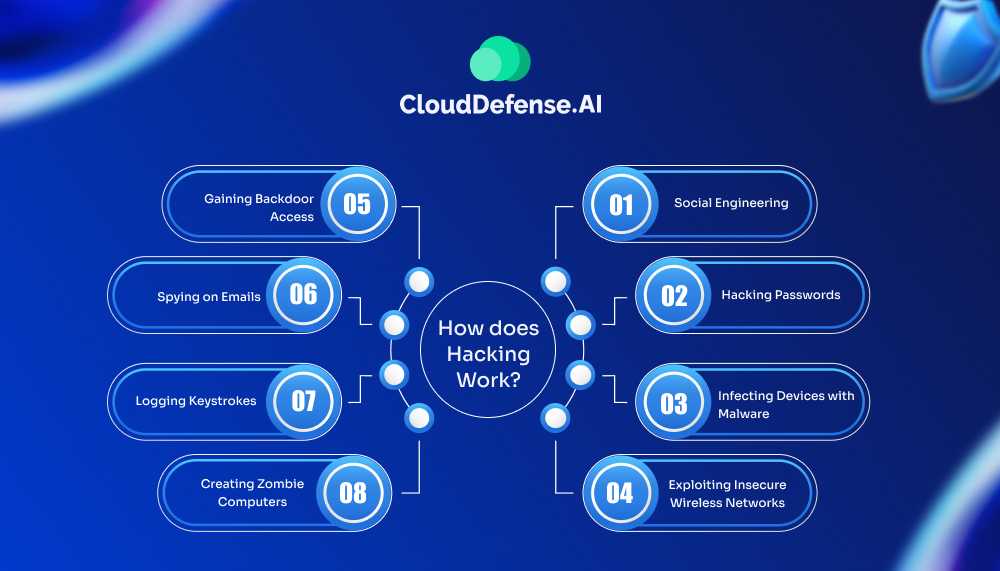
Hacking involves pinpointing and exploiting vulnerabilities in a system’s security to gain unauthorized access. This process often follows a structured approach, including the following steps:
- Information Gathering: Collecting data about the target system to identify potential entry points.
- Identifying Weaknesses: Using specialized tools to scan and detect system vulnerabilities.
- System Exploitation: Leveraging detected vulnerabilities to infiltrate the system.
- Maintaining Access: Implementing backdoors or other mechanisms to ensure continued access.
- Concealing Evidence: Erasing traces of the breach to avoid detection and prolong unauthorized access.
This systematic methodology allows attackers to breach systems, compromising sensitive information and operational integrity effectively.
History of Hacking
The concept of hacking originated in the 1960s when it was associated with the ingenuity of MIT’s Tech Model Railroad Club. These early hackers were enthusiasts who pushed the boundaries of computer hardware and software, driven by curiosity and a desire to innovate.
In 1971, Bob Thomas, a programmer at BBN Technologies, created Creeper, the first computer virus. Released on the ARPANET (the precursor to the Internet), this virus was not intended to harm but served as a proof-of-concept for self-replicating code, marking a pivotal moment in the history of cybersecurity.
By the 1980s, the rise of personal computers and the emergence of hacking groups brought hacking into the public spotlight. These groups often exploited vulnerabilities for fame, challenging corporations and governments, which spurred the development of stricter cybersecurity protocols and laws.
The history of hacking showcases its dual nature: a blend of creative exploration and, at times, malicious intent, both of which have shaped the evolution of modern computing and cybersecurity.
What’s the Difference Between Cyberattacks and Hacking?
While related, cyberattacks and hacking aren’t the same. Cyberattacks are malicious actions designed to disrupt, steal, or destroy, such as ransomware or DDoS attacks. Their sole purpose is harm.
Hacking, however, is about accessing systems and isn’t always bad. Black hat hackers exploit systems for personal gain, while white hat hackers use their skills to strengthen security.
Understanding this distinction helps us identify threats and appreciate the role ethical hacking plays in defending against cyberattacks.
Why do People Hack?
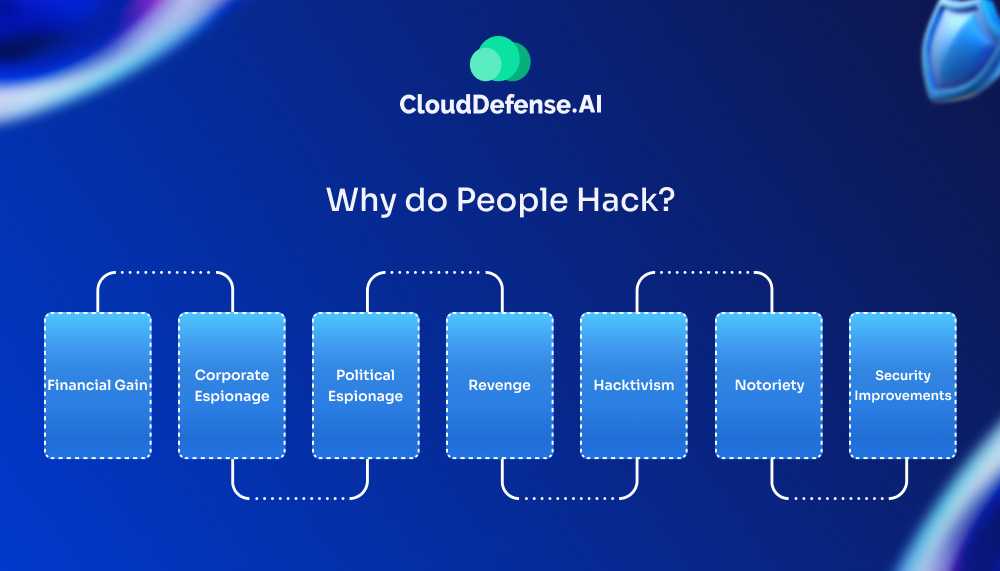
Hacking is fueled by a wide range of motivations, reflecting hackers’ diverse intentions. Understanding these drivers, from financial incentives to ideological beliefs, sheds light on the complex world of hacking.
Financial Gain
The most common motivation for hacking is money. Cybercriminals target personal and financial data—like passwords, credit card details, or bank accounts—to commit fraud, theft, or extortion. Ransomware attacks are a key example, where hackers lock data and demand payment to release it. Some even sell stolen information on the dark web.
Corporate Espionage
In the competitive business world, hackers are sometimes hired to steal trade secrets or sensitive information from rival companies. This kind of hacking, known as corporate espionage, provides companies with a strategic edge by accessing competitors’ classified data.
Political Agendas
Nation-states use hackers to advance political or geopolitical goals. These efforts often include stealing classified government information, interfering in elections, or destabilizing foreign adversaries. Cyberattacks in this sphere aim to gather intelligence or assert dominance without direct conflict.
Revenge
Personal grievances can also drive hacking. Individuals who feel wronged may retaliate by defacing websites, stealing sensitive data, or launching attacks that harm the reputation or operations of their target.
Hacktivism
Hacktivists hack to promote social or political causes. These individuals or groups use their skills to expose corruption, disrupt operations, or raise awareness for issues they believe in. For them, hacking is a tool for protest or civil disobedience.
Notoriety and Challenge
For some, hacking is about proving their skills. These individuals often target secure systems to gain recognition within the hacking community. To earn respect and notoriety, they share their exploits on social platforms or forums.
Ethical Hacking
Not all hackers have malicious intent. Ethical hackers, or “white hat” hackers, use their expertise to identify and fix vulnerabilities in systems. By conducting penetration testing and similar activities, they help organizations improve their cybersecurity defenses, making ethical hacking a force for good.
Hacking Techniques and Tools
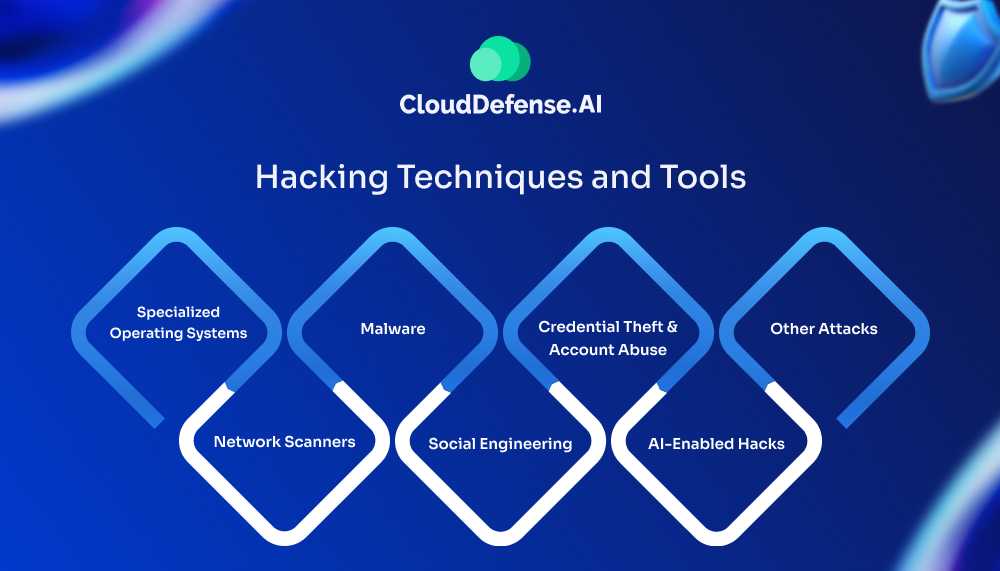
Hacking involves a wide range of techniques and tools, each customized to specific goals and targets. Whether the objective is stealing data, gaining unauthorized access, or disrupting systems, hackers use a variety of methods to achieve their aims. Below are some of the most common hacking techniques and tools:
- Specialized Operating Systems: Hackers use OS like Kali Linux for penetration testing and exploring vulnerabilities.
- Network Scanners: Tools like Nmap map networks identify active devices, open ports, and weak points.
- Malware includes viruses, ransomware, and Trojan horses, which are often deployed via tools like Metasploit to control systems or steal data.
- Social Engineering: Psychological manipulation like phishing tricks users into revealing sensitive information or compromising security.
- Credential Theft: Methods include brute force attacks, keyloggers, and account abuse to gain unauthorized access.
- AI-Enabled Attacks: Hackers use AI to craft more thoughtful phishing emails and adaptive malware and exploit vulnerabilities efficiently.
- SQL Injection & Cross-Site Scriand cross-site Scripting involve Exploiting access databases or injecting malicious injectings to hijack user sessions.
- Man-in-the-Middle Attacks: Intercept and alter communication to steal data or deploy malware discreetly.
Famous Hackers
Over the years, several hackers have gained notoriety for their exploits, whether for criminal activities or groundbreaking feats in the cybersecurity world. Below are some of the most famous hackers, each with their unique story and impact on the digital landscape.
Kevin Mitnick
Kevin Mitnick is the most famous hacker in the world. Known as the “Condor,” Mitnick’s hacking career began in the late 1970s. He was notorious for his ability to break into some of the most secure computer networks, including those of major corporations like IBM, Nokia, and Motorola.
Mitnick’s most famous hack involved the theft of software from Digital Equipment Corporation, which led to his arrest in 1995. After serving time in prison, Mitnick reformed and became a cybersecurity consultant, author, and speaker, sharing his insights on security vulnerabilities.
Adrian Lamo
Adrian Lamo, often referred to as the “Homeless Hacker,” gained fame for his ability to infiltrate high-profile networks. Lamo’s hacking exploits included breaking into systems at companies like Microsoft, Yahoo!, and The New York Times.
He was known for using public internet connections at cafes and libraries to carry out his hacks. Lamo’s most controversial act was turning in whistleblower Chelsea Manning, who had leaked classified government documents to WikiLeaks. Lamo’s role in Manning’s arrest remains a topic of intense debate.
Gary McKinnon
Gary McKinnon, a British hacker, gained notoriety for what has been described as the “biggest military computer hack of all time.” Between 2001 and 2002, McKinnon hacked into 97 U.S. military and NASA computers, claiming he was searching for evidence of UFOs.
His actions caused significant damage to the systems, resulting in the deletion of critical files and the shutdown of a U.S. Army network for 24 hours. McKinnon faced extradition to the United States, where he was charged with causing $700,000 worth of damage, but the extradition was eventually blocked due to concerns over his health.
Final Words
Hacking remains a persistent threat today. Understanding the various types of attacks and the techniques employed by hackers is essential for safeguarding your online presence. By staying informed, adopting strict security measures, and remaining vigilant, you can significantly reduce your risk of falling victim to these cybercrimes. Remember, in the battle against hacking, knowledge is your most powerful weapon.







