What is DAST?
DAST, or Dynamic Application Security Testing, is a security testing technique that helps find various security vulnerabilities in web applications while they are active and running. Unlike other testing methods, DAST doesn’t need insight into the application’s internal code or structure.
It operates like a “black box” test, meaning it observes the application’s behavior and interactions from the outside, simulating real-world attack scenarios. By observing the application’s reactions, DAST helps pinpoint vulnerabilities that might allow a hacker to break in. This method is crucial because it helps identify security gaps that could be exploited, ensuring that the application is robust enough to withstand real threats in the wild.
How Does DAST Work?
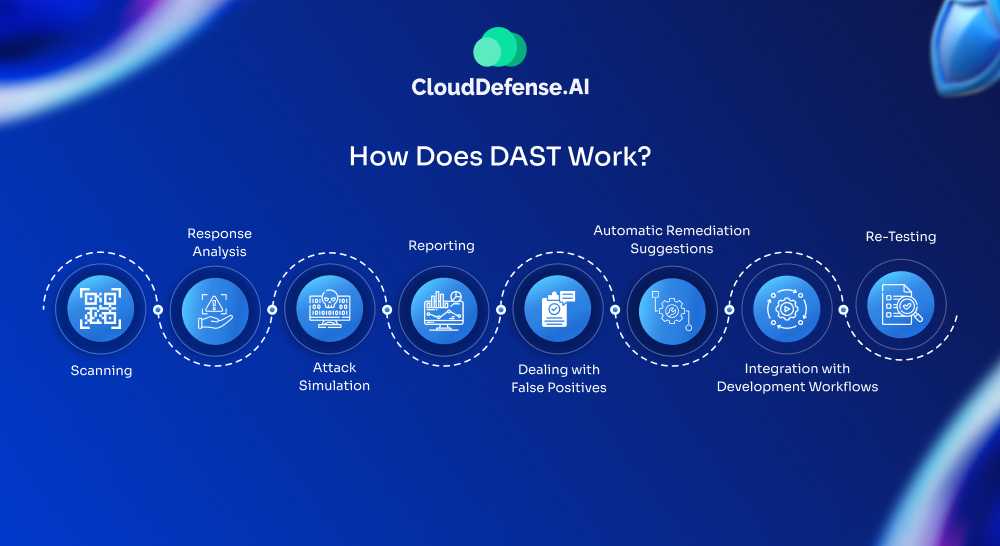
DAST, taking a “black box” approach, mimics how an attacker might probe a web application for weaknesses. Here’s a simplified breakdown of the process:
1. Scanning
DAST tools kick things off by interacting with the running application just like a user would—sending HTTP requests, crawling through every page, and mapping out links, functions, and entry points (especially for single-page apps). This first step helps the tool understand how the app works, based on an API document, without touching the code.
2. Response Analysis
Once the requests are sent, DAST closely examines how the application responds. It looks for odd behaviors, unexpected error messages, or anything out of place that might hint at a vulnerability. If the tool finds something suspicious, it flags the location and details for developers to review, allowing for manual testing where needed.
3. Attack Simulation
This is where DAST tools really put the app to the test. They simulate attacks, like SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF), to spot security weaknesses. Whether it’s a misconfiguration, a data leak, or an authentication flaw, the goal is to uncover risks that attackers could exploit.
4. Reporting
After scanning and attack simulations, DAST generates a detailed report. It outlines the vulnerabilities it found, how severe they are, and potential attack scenarios that developers should be aware of. Keep in mind that DAST doesn’t fix anything—it just points out where the issues are for developers and security teams to address.
5. Dealing with False Positives
Sometimes, DAST tools might flag something as vulnerable when it’s really not. When this happens, manual checks are needed to sort out the real risks from the false positives and make sure the right issues are prioritized.
What Problems Does DAST Solve?
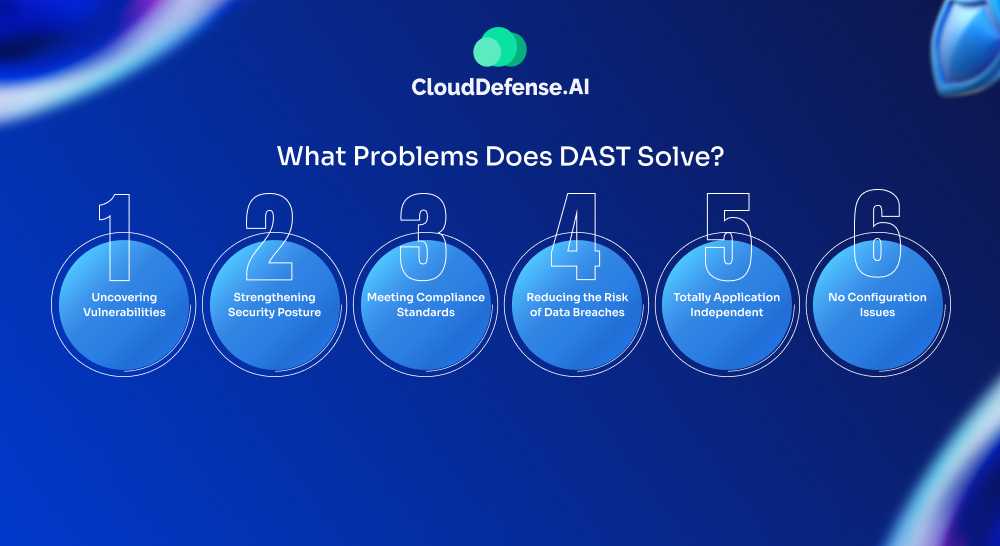
DAST is a game changer in web application security, tackling several important challenges that organizations face. Here’s how:
Uncovering Vulnerabilities
One of the biggest advantages of DAST is its ability to find vulnerabilities that attackers could exploit. By mimicking real-world attack scenarios, DAST reveals issues like SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF) that might slip under the radar.
Strengthening Security Posture
Regular scans using DAST tools help improve an organization’s security stance. By highlighting areas for improvement, it ensures that defenses are robust and that the application is less likely to fall victim to an attack.
Meeting Compliance Standards
For many businesses, staying compliant with industry regulations is a must. DAST assists in this by identifying potential vulnerabilities that could lead to data breaches, helping organizations adhere to necessary security protocols.
Reducing the Risk of Data Breaches
By pinpointing security gaps before they can be exploited, DAST greatly reduces the risk of data breaches. Addressing these issues early helps safeguard sensitive information and maintain trust with customers.
Totally Application Independent
Because DAST tools don’t delve into an app’s source code, they can be used regardless of the platform or language you’re working with. As a result, a single DAST tool can run on all your applications, and can even be utilized for applications that are different from one another but may nonetheless interface frequently.
No Configuration Issues
When your application is fully operational, DAST does a great job of finding security vulnerabilities. Since it looks at your application from an outside perspective, a DAST scanner is perfectly positioned to discover configuration mistakes that might be missed by other types of security scanning tools.
Pros and Cons of DAST
Pros
DAST tools play a crucial role in web application security, bringing several key advantages:
- Identifies Runtime Issues: DAST excels at finding vulnerabilities that only emerge when an application is running, such as session management flaws or data exposure vulnerabilities.
- Flexibility: This method can be applied throughout the software development lifecycle, allowing assessment of both active web applications and legacy systems without requiring changes.
- Automation: Many DAST tools integrate seamlessly into DevOps and CI/CD pipelines, enabling early detection of security issues, which can significantly reduce remediation costs.
- No Source Code Required: DAST doesn’t need access to the source code, making it suitable for a wide array of applications, including those developed by third parties or legacy systems.
- Language Neutrality: Since DAST operates from an external perspective, it’s not tied to any specific programming language, allowing it to test various frameworks and APIs effectively.
- Reduced False Positives: DAST generally produces fewer false positives compared to other methods, as its simulations closely mirror real user interactions.
- Realistic Testing: By simulating actual attack scenarios, DAST provides valuable insights into how vulnerabilities might be exploited and allows for repeated testing as applications evolve.
- Thorough Vulnerability Detection: DAST effectively identifies a wide range of vulnerabilities, including SQL injection and cross-site scripting (XSS).
- Compliance Support: Many organizations use DAST to comply with industry standards and regulations, often leveraging resources such as the OWASP Top 10 and SANS 25.
Cons
While DAST is powerful, it has its limitations. It may miss vulnerabilities that rely on specific sequences of actions, making it wise to combine it with other testing methods like SAST, IAST, or manual penetration testing.
- Limited Insight: DAST doesn’t provide information about code quality or architecture, making it harder to trace the root causes of vulnerabilities.
- Authentication Challenges: Complex authentication processes can confuse DAST tools, although many modern DAST tools like CloudDefense.AI are designed to handle these scenarios better.
- Dependency on Test Environment: The effectiveness of DAST can be influenced by the testing environment; if it doesn’t accurately reflect production, the results may be misleading.
- Impact on Performance: Improperly configured DAST tests can affect application performance or disrupt normal operations. For this reason, it’s often better to run tests in staging environments rather than in live settings.
Differences Between DAST and SAST
When it comes to testing web applications for vulnerabilities, two primary approaches are often discussed: DAST and SAST. Both methods serve important roles in application security but operate quite differently. Here’s a breakdown of their key differences:
Refer to this table for a clearer understanding of both these application security testing methods.
| Aspect | SAST | DAST |
| Type of Security Testing | White box | Black box |
| How is the Scan Carried Out? | From a developer’s point of view | From a Hacker’s point of view |
| Scanning Requirement | Source code of the application | Running application |
| SDLC | Early stage | Later stage |
| Remediation Cost | Less expensive | More expensive |
| Type of Issue Discovered | Can’t detect runtime issues. | Runtime issues are detected. |
| Scope of Scan | Language or platform specific | Multiple languages and platforms are supported |
| Software Supported | All of them | Both software and hardware |
As “white box” testing tools, SASTs scanners can look through the source code architecture of applications so long as they are at rest rather than currently operating.
In a way, SAST tools are the opposite of DAST scanners – they look at an application from the inside out instead of from the outside in. They also have many of the opposite benefits and drawbacks.
How to Implement DAST into Your SDLC?
Implementing DAST into your CI/CD pipeline requires careful planning and execution to ensure its effectiveness in identifying security vulnerabilities. Here’s a structured approach based on the provided information:
Start Early and Keep DAST in the Loop
To really make the most of Dynamic Application Security Testing (DAST), bring it into the picture as early as you can in the software development process. This way, you can catch potential vulnerabilities in critical web applications right from the design phase.
If you wait too long to implement DAST, it can cost more in terms of time and money to fix issues that could’ve been identified sooner. Nobody likes the stress of scrambling to resolve problems that could have been avoided!
Team Up with DevOps
DAST tools are great for spotting vulnerabilities, but the next step is making sure your DevOps team can tackle those issues effectively. A smart move is to integrate your DAST tools with their bug-tracking systems.
This helps developers get the precise information they need to fix vulnerabilities quickly. By cultivating a collaborative environment, you not only prioritize security but also work towards a DevSecOps mindset, where security becomes part of everyone’s job.
Make DAST Part of a Bigger Security Picture
While DAST offers valuable insights, it shouldn’t stand alone. Combine it with other testing methods like SAST and application penetration testing. SAST helps you see potential vulnerabilities in the source code early on, while penetration testing simulates real-world attacks to show how an attacker might exploit your application.
Generate and Review Reports
Create detailed reports summarizing the DAST scan results. Share these reports promptly with relevant stakeholders, including developers and security experts. Prioritize the vulnerabilities based on severity and potential impact to enhance application security effectively.
Remediate Vulnerabilities
Quickly tackle the vulnerabilities pinpointed during the DAST scan. Work closely with development teams to deploy suitable fixes. Continuously track the progress of vulnerability remediation and validate the efficacy of implemented solutions.
Incorporate Regression Testing
Add regression tests to your suite to prevent old vulnerabilities from coming back. Keep updating the suite with new usage scenarios and security checks to boost your app’s security. This proactive approach ensures continued protection against threats.
CloudDefense.AI’s DAST Approach
When it comes to securing applications, we don’t believe in complexity for the sake of it. CloudDefense.AI’s Dynamic Application Security Testing (DAST) platform is all about simplicity, depth, and speed. We’ve designed it to make security as straightforward as possible without compromising on power. Here’s how we do it:
User-Friendly Interface for Easy Configuration
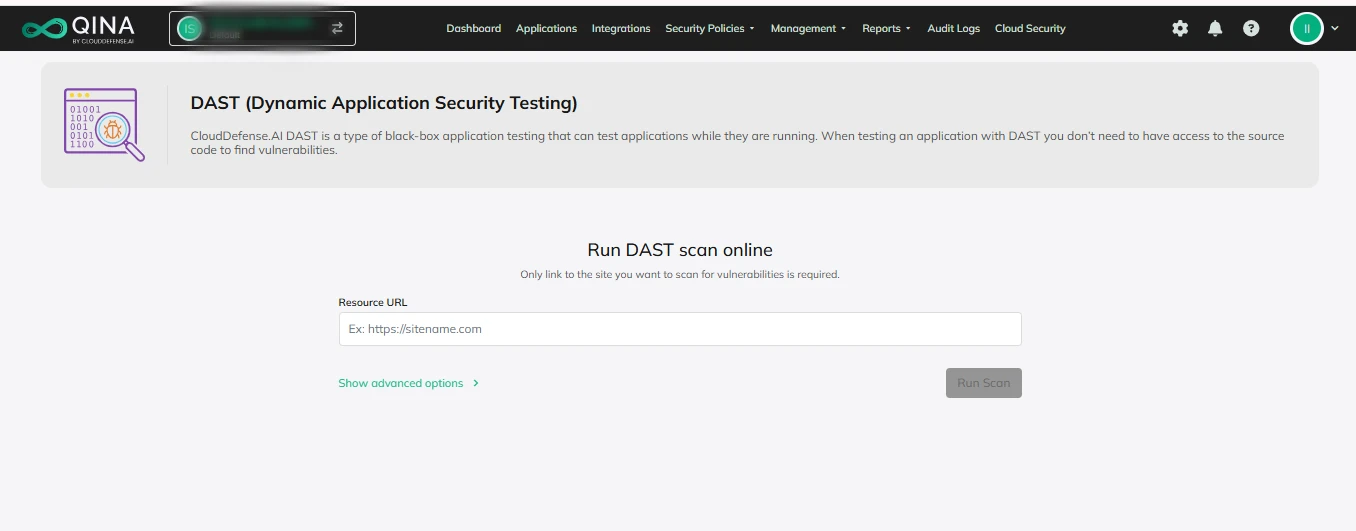
Security shouldn’t be a hassle. Our DAST platform was built with usability in mind. You won’t need to spend hours figuring out how to get it up and running. The interface is clean, intuitive, and designed for anyone—whether you’re a seasoned security pro or someone just getting started. As shown in the screenshot, users can easily input target URLs, configure scan parameters, and run scans with just a few clicks. This ensures that even non-security experts can initiate comprehensive scans effortlessly.
Deep and Comprehensive Vulnerability Detection
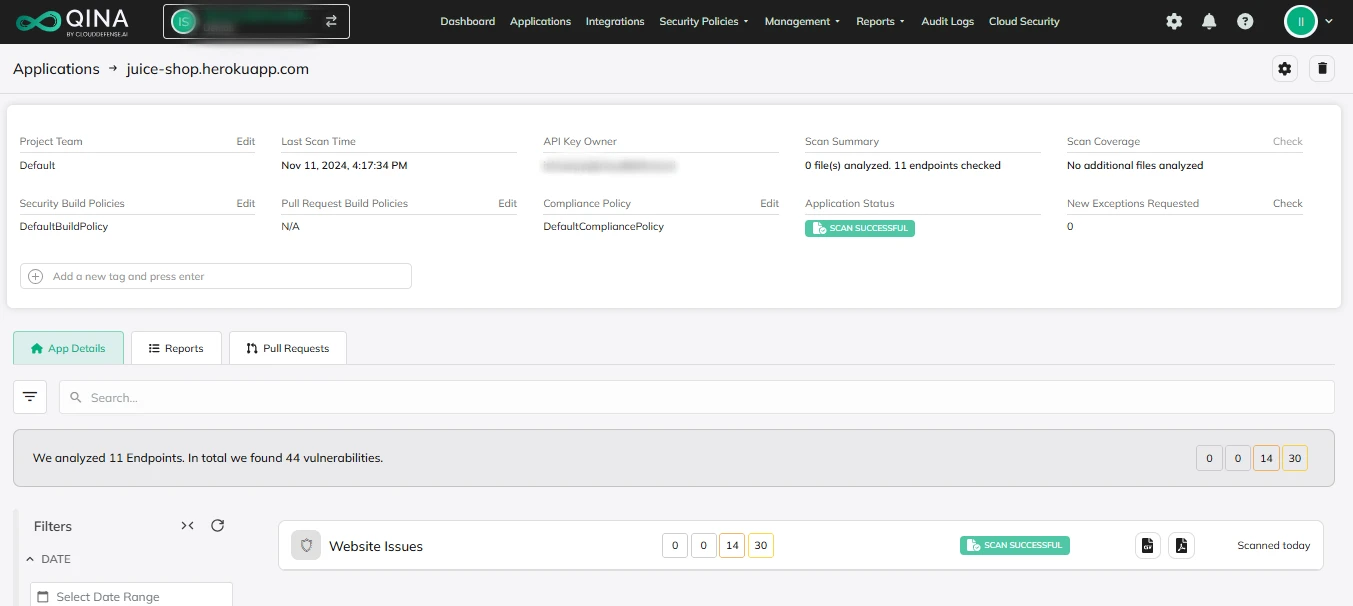
It’s not enough to catch the obvious stuff. Our platform digs deep, looking at every corner of your application for vulnerabilities, both the known ones and the hidden ones that attackers are always trying to exploit. Whether it’s SQL injection, XSS, or something more complex, our scans cover it all. We run simulated attacks in real-time so you can see exactly where your app could be vulnerable. It’s about finding problems before someone else does.
Risk Prioritization
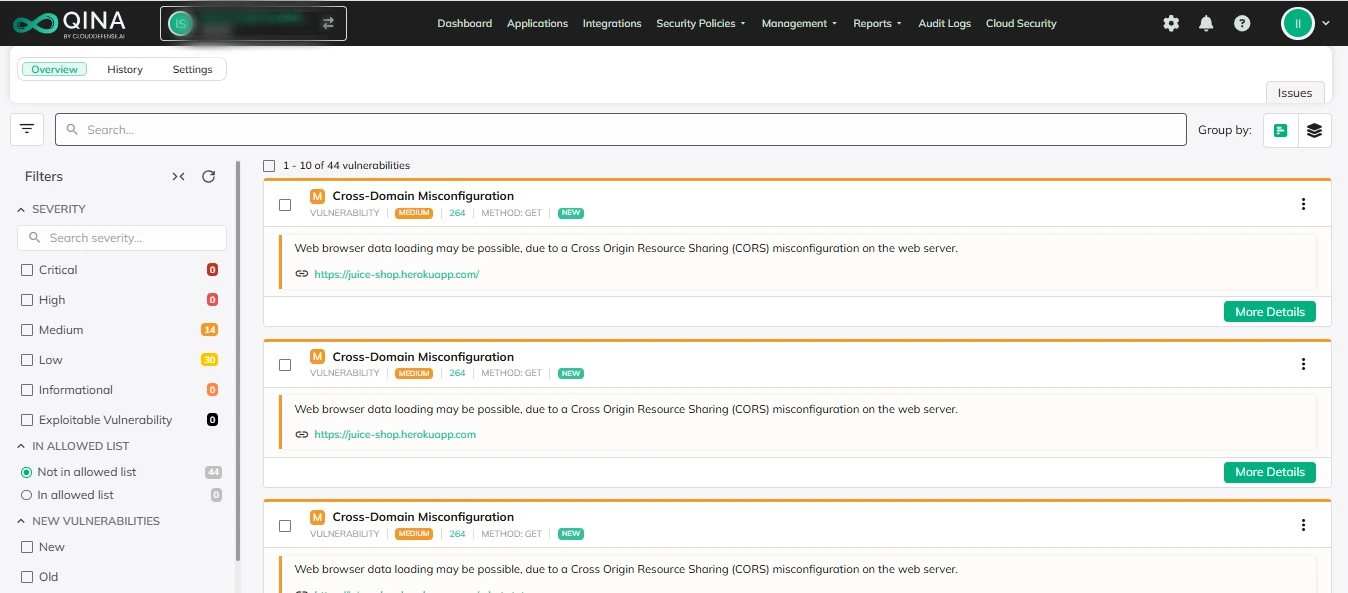
Not all vulnerabilities are created equal. That’s why our platform doesn’t just point out problems—it helps you figure out which ones need your immediate attention. We analyze each issue based on how bad it could be, how likely it is to be exploited, and how much damage it could cause. That way, you’re not wasting time on things that don’t matter, and instead, you’re tackling the threats that could actually hurt your business.
Auto Remediation
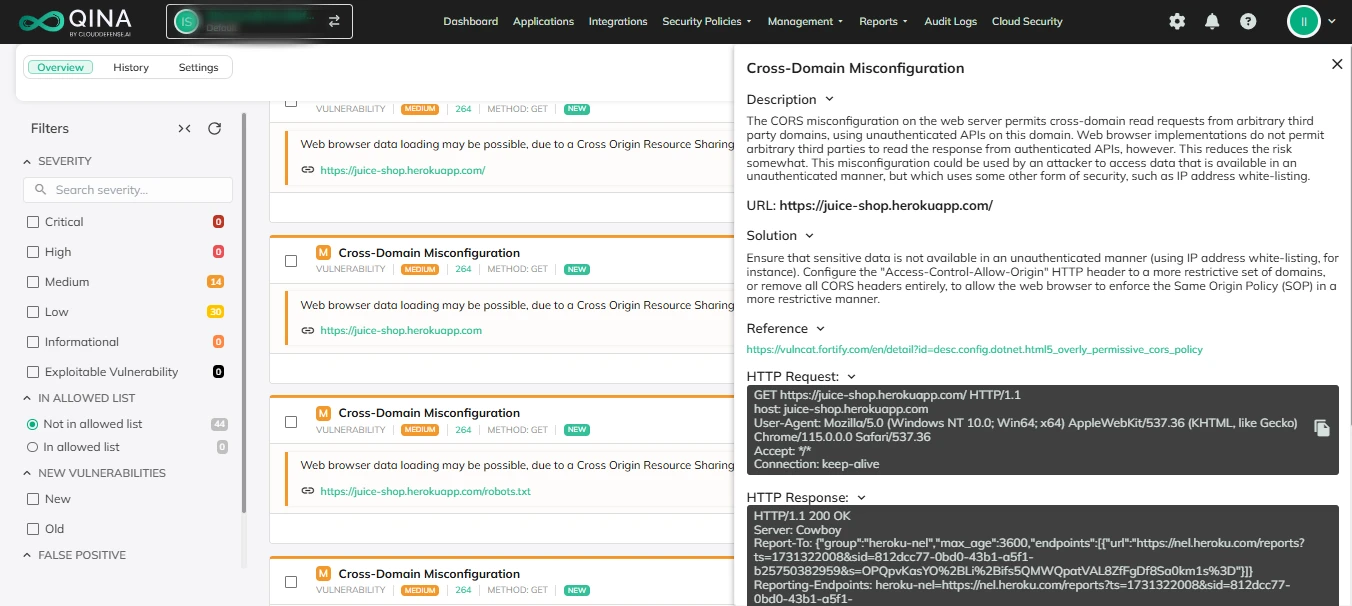
One of the biggest challenges in security is speed. The faster you fix a problem, the less chance there is of it being exploited. That’s why we’ve built auto-remediation into our platform. It means certain vulnerabilities can be fixed automatically, without you having to lift a finger. Whether it’s patching an issue or applying a pre-configured fix, it happens fast. The result? Vulnerabilities get resolved while you focus on other important tasks, without the delay.
Detailed Reports
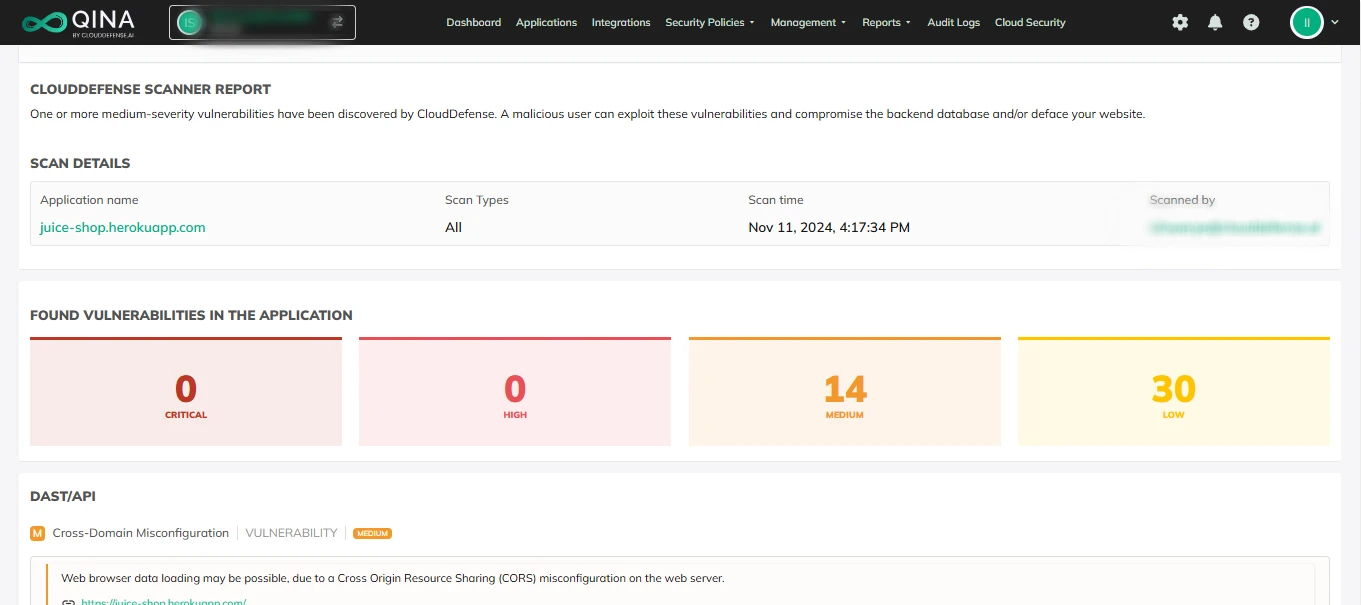
Once the scans are complete, you don’t want to be left with a bunch of technical jargon. Our reports are designed to be clear and actionable. You’ll get a breakdown of each vulnerability—what it is, how bad it is, and what you need to do about it. The reports are easy to share, so your team can work together to fix issues without confusion. Plus, they’re built to help you meet compliance requirements, so you’re always on top of your security game.
With us, you get holistic security coverage – right from your code to the cloud. CloudDefense.AI’s DAST solution easily fits into your workflow, offering a thorough look at vulnerabilities and boosting your overall security. Want to see it in action? Book a free demo and see how DAST can strengthen your application security strategy.
Conclusion
In summary, Dynamic Application Security Testing (DAST) is a powerful way to identify vulnerabilities in running applications without needing access to the source code. It excels at detecting issues in real-time, offers flexibility in how it’s deployed, and reduces the risk of false positives. However, to fully protect your applications, DAST works best when combined with other testing methods like SAST and SCA, giving you comprehensive coverage against potential threats.







