What is Dark Web Monitoring?
Dark web monitoring indicates the process of searching, identifying, and tracking the sensitive information of your organization on the dark web. This monitoring tool works like a search engine, looking for stolen or leaked sensitive data like breached credentials, banking data, an organization’s sales data, or compromised passwords that are being sold on the dark web.
It can be described as a form of threat intelligence that also serves as an integral part of modern security strategy and identity theft protection to help organizations address leaked data. Many cyber criminals get the organization’s data from the dark web to carry out further attacks, sell them to competitors, or use them for reputational damage.
Suppose cybercriminals get your organization’s financial data; they can use it for malicious tasks. So, dark web monitoring helps organizations search for particular confidential data lost due to cyberattacks on the dark web and reduces the impact of attacks.
The dark web stays on the overlay network, and the user requires a specific configuration to access the dark. The solution scans multiple sources from the dark web and indexes them so that the organization can take corrective measures before it’s too late.
Dark Web vs Deep Web
Dark web and deep web serve as the hidden part of the internet that are not indexed by search engines and they can be only accessed through special configuration or software. Even though both dark web and deep web serve as an encrypted part of the internet, they are both different from each other.
The primary difference between the two is that the deep web carries 96% of the content on the web and can only be accessed using special access permission. You can use a web browser to search for non-indexed content on the deep web.
Whereas the dark web is a typical web section that is not accessible using traditional search engines and you require specialized browsers like Tor Browser to access them.
The deep web covers a large scope of the dark web, containing many contents that are not easily available on the clean web. Whereas the dark web forms only 1% of the deep web and covers only a limited number of contents.
The contents of the deep are not explicitly hidden from the general users, they are not indexed by the popular search engines. Standard web browsers can help you access the deep web by putting the specific URL.
The content of the deep web usually comprises pirated content, research papers, private databases, internal organization’s websites, and other information that are legal but not meant for public consumption.
However, the content of the dark web is explicitly hidden as it contains illegal information and is mostly used by criminals. The contents found on the dark web are drug trafficking, child exploitation, hitman hiring, cartel transactions, identity theft, and many other illicit information.
The deep web is primarily legitimate, and it is mostly used by users who need privacy or need to maintain restricted access. The dark web, on the other hand, is mostly used for illegal activities, and they help users find illicit content that is not available on the clean web. Usually these contents are completely risky to access and can incur legal actions.
How Does Dark Web Monitoring Work?

Dark web monitoring can come as a standalone solution or they are often embedded as a tool in particular security SaaS products. This tool continuously searches multiple sources on the dark web and pulls in reports of stolen data or exposed information in real time. The tool scours through millions of sites to search for specific organization’s information like corporate email credentials, bank details, health status, and others.
When the particular information is discovered, it provides an alert to every team member that the particular information has been exposed. Most of the dark web monitoring tools offer the option to customize the alert so that it notifies about exposed information to relevant teams like marketing, legal or security teams.
This tool often works along with a threat intelligence platform that enables organizations to archive hackers’ tactics, motives, and threat data and use it for monitoring purposes. Moreover, the intelligence database also helps in a quicker incident response and assessment of security posture.
Dark web monitoring works by accessing a huge variety of data types to help organizations track which contents are exposed during an attack. The data types include:
- Business Data- A large amount of leaked data found on the dark web is business data, and it usually contains trade, employee records, business deals, intellectual property, and other sensitive information.
- PII- This tool also finds personally identifiable information stolen by hackers, and it includes names, addresses, social security numbers, health insurance numbers, etc.
- Medical Information- A lot of attackers sell health records on the dark web, which mainly contains medical records, prescriptions, health insurance numbers, and other critical data.
- Financial Data- Financial data of organizations like business transactions, bank details, pin codes and others are widely sold on the dark web.
- Credential Data: Dark web monitoring tool is highly effective in searching credentials like login details, username & pass, API keys, security question & answers and others.
- Communication Data- Information of calls, chat histories and business emails can be tracked through dark web monitoring tools.
- Educational Data- Educational data like financial aid and admission records can be found on the dark web.
Features of Dark Web Monitoring
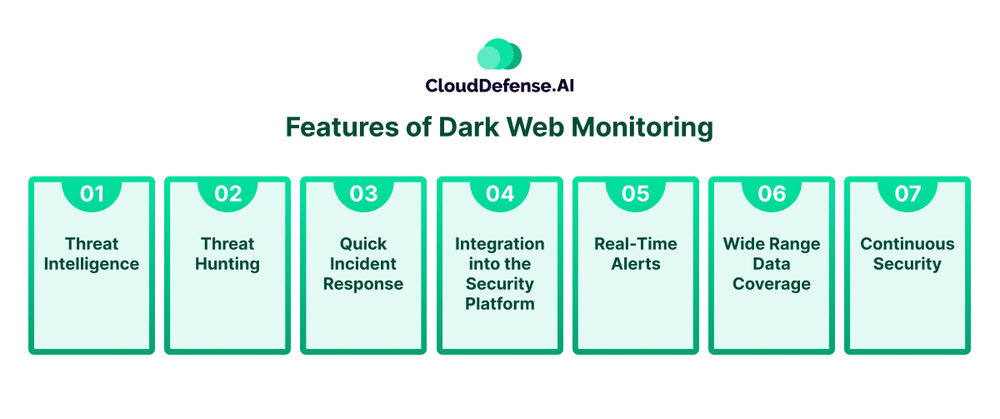
Dark web monitoring is a vital solution in today’s cybersecurity landscape as it helps organizations secure various data and prevent them from getting exploited.
However, dark web monitoring is not only about finding information on the dark web, as it has more to offer. Let’s take a look at all the features it has on offer:
Threat Intelligence
Dark web monitoring identifies the area of the dark web that will be useful for searching and captures all the data that are fed directly into automated threat intelligence systems. As a result, the security can understand which data is exposed and take mitigation steps accordingly. This tool enables you to stay integrated into a feed of threat intelligence, which will help prevent any exploitation.
Threat Hunting
Threat hunting is another aspect of dark web monitoring tools that helps in understanding attackers’ different attacking methods and emerging threats. Threat hunters utilize this solution to speed up the threat-hunting process and look for unusual behavior that might indicate the presence of malware or a looming threat.
Quick Incident Response
Dark web monitoring enables quick incident response through a strategic investigation and response workflow. It continuously monitors the dark and helps in identifying that your organization’s sensitive information is available on the dark web. When it alerts the security team, they are able to take necessary steps to prevent exploitation or sale.
Integration into the Security Platform
This tool also allows you to integrate the data collected during monitoring with other security platforms. As a result you not only get a detailed and more accurate insight of security posture but also inputs for devising the security strategy. Moreover the integration helps the security team in developing a multilayered protection against most online threats.
Real-Time Alerts
To effectively identify stolen data on the dark web, this solution continuously scans every section and notifies in real time when a particular dataset of the organization is discovered. With real-time alerts, security teams can quickly respond to possible threats and take necessary mitigation steps to prevent any exploitation.
Wide Range Data Coverage
Apart from traditional personal data and email addresses, dark web monitoring solutions cover a wide range of data. Ranging from login credentials, organization financial result, contact details and social security numbers to gamers tag, and health details, it scans for a wide variety of data on the dark web.
Continuous Security
This security solution continuously scans the forum, sites and other sections of the dark web to look for sensitive information of your organization. It quietly runs in the background and offers alerts whenever it identifies any specific information.
Why Use Dark Web Monitoring?
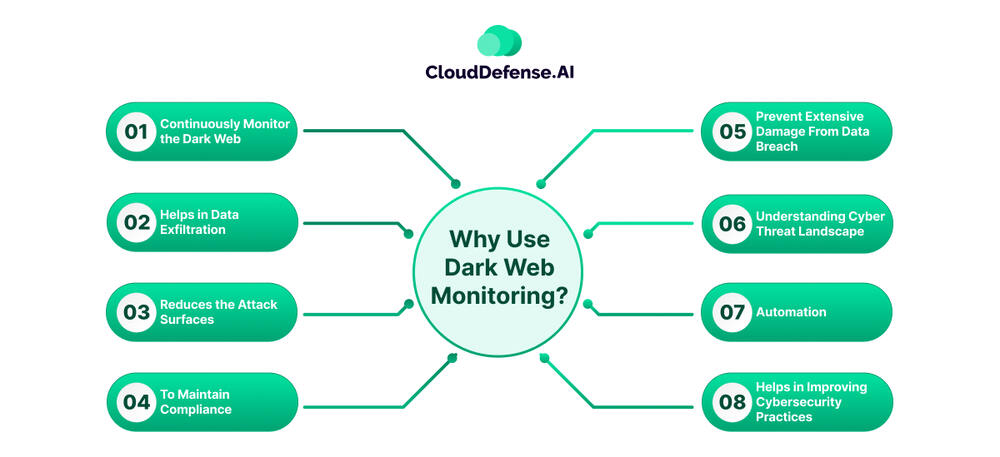
For most organizations operating in the cloud, dark web monitoring has become a necessity for everyone, and it is mainly due to several reasons. Here are the primary reasons that will clarify why you should use dark web monitoring for your organization:
Continuously Monitor the Dark Web
The dark web monitoring solution constantly examines the dark web to ensure all the sensitive data and content of the organization are safe from cybercriminals. It performs 24/7 monitoring to always assess the dark and provide a quick alert if any stolen data lands on the site, forum, or chats of the dark web.
Helps in Data Exfiltration
When a monitoring solution detects the presence of any sensitive information related to the organization, especially of users, it alerts the affected users about their compromised credentials. Organizations then take necessary steps by working alongside the user to prevent attackers from exploiting the information.
Reduces the Attack Surfaces
With dark web monitoring solutions in place, organization can greatly reduce the attack as it continuously looks for organization’s compromised data on the dark web. It quickly alerts the security when it discovers a threat and ensures the attackers can utilize the stolen data to carry out any attack.
To Maintain Compliance
Every organization that deals with customer data has to adhere to specific industry regulations. This monitoring solution helps organization in adhering to regulatory requirements by preventing data breaches. It is highly useful in adhering to strict guidelines of GDPR and SOC 2.
Prevent Extensive Damage From Data Breach
On many occasions, organizations face data breaches, and they don’t notice it until the attackers exploit the stolen data. However dark web monitoring services help in preventing extensive damage from data breach by keeping track of stolen data on the dark web.
It alerts the team in quickly patching the vulnerabilities and informs users in taking necessary steps, thus helping in reducing the effect of data infringement.
Understanding Cyber Threat Landscape
Many security teams utilize dark web monitoring services to gather intel regarding the current cyber threat landscape. Gathering insight involves understanding the attacker’s tactics, assessing current trends, and estimating motives and threats of attacks.
The security insights allow security teams to create a robust security strategy and assist other tools by helping them gather all the threat intelligence. If you use the MITRE ATT&CK framework, this solution can be useful in gathering threat feeds.
Automation
Most of the modern dark web monitoring services utilize automation to automate the scanning process across the dark web. In addition, automation is also utilized to alert the designated individuals or team regarding exposed data, enabling them to quickly mitigate any issue and prevent any impact. Some advanced solutions come with AI based risk tagging capability that helps security teams to address issues according to their severity.
Helps in Improving Cybersecurity Practices
When credentials land on the dark web, it helps in strengthening specific areas of security strategy and improve overall cybersecurity practices. When better cybersecurity practices are followed, it will curb the number of attack vectors.
How Does Personal Information Get on the Dark Web?

The dark web has become a breeding ground for cybercriminals where they peddle all the stolen data. Cybercriminals, after stealing personal information like private data and login details of users or employees of an organization, mostly sell them to bidders. These attackers utilize various methodologies or combinations of methods to steal personal information.
However, according to CrowdStrike’s Global Threat report, it shows that attackers are coming up with advanced methodologies and have gone past traditional malware attacks. They are utilizing the approach of “living off the land,” where they are using stolen data and others to carry on their malicious intent while staying off the radar of standard antivirus. Here are some methodologies that attackers utilize to steal data and put them on the dark web:
Phishing Attack
Phishing is undoubtedly one of the most useful methodologies used by cybercriminals, where they send phishing emails, messages, or notifications to the victim. The phishing email or message is crafted in such a way that it mimics legitimate email sources, and this tricks victims into giving personal information to attackers.
Botnets and Malware
Beside phishing, attackers are known for using a varied type of malware and botnets to trick users and steal their confidential data. These malware and botnets help in extracting a lot of PII that are later sold in the dark web.
Vulnerabilities
Every organization has some kind of vulnerability in their application or system and attackers exploit them using various techniques. By exploiting the weakness, it embeds malicious code into the application or installs malicious software in the system to obtain access.
Exploiting Poorly Configured or Insecure Network
When you connect your device, especially an endpoint device, to an insecure network, attackers use this situation to steal all your personal information. Attackers also look for poorly configured networks to gain access to the connection and extract all the available PII.
Keylogging
Attackers often, through different methods, install keyloggers into your device or system that records all the keys you press. It enables attackers to track all you type and retrieve personal information from those logs.
Screen Scraping
Another popular method that is used by cyberattackers to steal personal information is screen scraping. In this method, the malicious software records everything shown on the screen, which allows it to capture personal information.
After successfully stealing all the required personal information including name, address, DOB, banking details, social security number and others, attackers package them which is often called “fullz”. These packages are then sold to different sites or forums and their price depends upon the victim’s asset. Sometimes this information is also to rival organization or organizations looking for a large number of PII.
How to Achieve Threat Protection With CloudDefense.AI
When it comes to achieving threat protection for your organization, you need the protection of an all-round security platform, and CloudDefense.AI fills that space. It is a leading security platform that offers you real-time threat detection and protection capability to help you protect all your organization’s sensitive information.
This platform leverages cutting-edge threat and response solutions to identify any threat that might breach your infrastructure. Along with threat protection, you can also utilize vulnerability management, cloud workload protection platforms, and secret management, as it will help prevent all the data from getting exposed to the dark web.
CloudDefense.AI implements zero trust dependencies, which helps in remediating loopholes and preventing backdoor data access of attackers dealing with dark web dealers. The best part is that it will also help you in maintaining compliance with different regulatory standards by leveraging Airtight Checklists.
FAQ
Is Dark Web Monitoring Legitimate?
Dark web monitoring is completely legitimate, and many top security platforms offer this service without violating any regulations or laws. However, it doesn’t have the authorization to take any kind of remediation step to remove the stolen sensitive information from the forum or site of the dark web.
Moreover, it also doesn’t come with the capability or authority to prevent cybercriminals from selling or passing the stolen information to other bidders in the forum. Importantly, the dark web has numerous encryption layers and buyers who are mostly anonymous. As a result, dark web monitoring can’t perform any action whenever it identifies any stolen information.
Who Needs Dark Web Monitoring Services?
Every modern organization that stores sensitive customer information or processes different intellectual property must opt for web monitoring services. These organizations serve as the prime targets of cybercriminals, hacktivists, and state-sponsored attackers, so they always look for ways to steal the data.
By implementing dark web monitoring services, these organizations can discover all the stolen sensitive data of the organization that are available on the dark web and take precautionary steps accordingly. This tool provides organizations with comprehensive visibility into unknown threats by providing information about stolen data and helping them take action to prevent exploitation.
How To Protect Data Against the Dark Web?
To protect your organization’s data against dark, you need to follow certain precautionary steps. You need to follow all the BYOD policies and ensure they are never violated. You also need to browse in a safe way while using strong login credentials.
However all the login credentials should be changed at regular intervals to prevent misuse. All the employees in your organization should opt for security awareness training to make them aware of data that lands on the dark web.
What Does it Mean that Your Information is on the Dark Web?
When a user learns that their personal information is on the dark web, it means that they need to change their password, change their credit card, and block their bank accounts. The organization should take aggressive mitigation steps that would prevent cybercriminals from exploiting the stolen credentials. Users shouldn’t get worried when they find out about stolen data, as they should follow response guidelines to prevent further impact.







