What is a Cyberattack?
A cyberattack is an intentional and malicious action carried out by cybercriminals to compromise the confidentiality, integrity, or availability of digital systems, networks, or data.
These attacks often aim to steal sensitive information, disrupt operations, cause financial harm, or gain unauthorized control over systems. Attackers employ various tactics, including malware deployment, phishing schemes, ransomware, denial-of-service (DoS) attacks, and exploitation of software vulnerabilities.
Why Do Cyberattacks Happen?
Threat actors launch cyberattacks for various purposes, from financial gain to geopolitical motives. They use techniques such as phishing scams, ransomware, malware injections, and brute-force attacks to compromise target systems and gain unauthorized access to sensitive data.
The impact of cyberattacks can be devastating, often resulting in disrupted operations, financial losses, and reputational damage. According to IBM, the global average cost of a data breach reached an all-time high of $4.88 million in 2024, marking a 10% increase over the previous year.
The data from IBM included expenses like breach detection, incident response, downtime, and diminished customer trust. These figures underline the heavy financial burden businesses face after an attack.
Some attacks are notably more damaging. For instance, ransomware demands have reached staggering heights. The highest known ransom payment to date is $75 million, made to the Dark Angels ransomware group.
Business email compromise scams continue to wreak havoc, with individual attacks costing businesses upwards of $25 million. Additionally, breaches exposing personally identifiable information (PII) lead to regulatory penalties and legal challenges and erode customer confidence, potentially harming long-term business viability.
With global cybercrime costs expected to grow by 15% per year, reaching $10.5 trillion annually by 2025, businesses must prioritize cybersecurity measures to defend against these escalating threats.
Who is Behind Cyberattacks?
Cyber attacks can be initiated by various entities, including criminal organizations, state actors, and private individuals. Threat actors can be categorized as outsider threats or insider threats.
Outsider threats involve organized criminal groups, professional hackers, state-sponsored actors, amateur hackers, and hacktivists. These entities gain unauthorized access to networks or devices to carry out malicious activities.
On the other hand, insider threats involve users with legitimate access to a company’s assets who misuse their privileges intentionally or accidentally. This category includes employees, business partners, clients, contractors, and suppliers with system access.
Popular Hacking Groups
Recent warnings from cybersecurity agencies highlight the activities of Chinese state-sponsored hackers targeting critical infrastructure in the United States. Groups like Volt Typhoon, also known as Vanguard Panda and BRONZE SILHOUETTE, have breached IT environments in sectors such as communications, energy, transportation systems, and water and wastewater systems.
Politically motivated cyber attacks are also prevalent, and various countries have been identified as sources of such attacks. China, Russia, Iran, and North Korea are among the countries currently associated with politically motivated cyber incidents.
What do Cyberattacks Target?
Cyberattacks target a wide array of physical and digital resources, exploiting vulnerabilities to compromise an organization’s security. These assaults are designed to undermine the confidentiality, integrity, or availability of critical systems and data, with devastating consequences.
Threat actors often extend their focus beyond obvious vulnerabilities to encompass entire ecosystems, including Wi-Fi networks, social media accounts, operating systems, and sensitive information such as credit card details or bank account credentials. This broad reach makes it imperative for organizations to maintain robust security measures.
One high-profile example is the SolarWinds supply chain attack, where Russian hackers inserted malware into a routine software update. This breach enabled access to multiple U.S. government agencies, exposing confidential communications and setting a new benchmark for sophisticated cyber espionage.
Common Cyberattack Targets:
- Financial data: Credit card information, payment records, and banking details.
- Customer data: Personally identifiable information (PII), including names, addresses, and contact details.
- Login credentials: Usernames, passwords, and two-factor authentication codes.
- Intellectual property: Trade secrets, product designs, and proprietary software.
- IT infrastructure: Servers, databases, and network systems.
Modern cyberattacks are increasingly insidious, often mimicking legitimate system processes to evade detection by firewalls and traditional defenses. Their complexity also makes tracing perpetrators a challenge for law enforcement.
Beyond theft, some attackers aim solely to disrupt operations, causing downtime, financial losses, and reputational damage. The rise in complex, targeted cyberattacks highlights the urgent need for proactive, layered cybersecurity defenses.
What Effects Do Cyberattacks Have on Businesses?
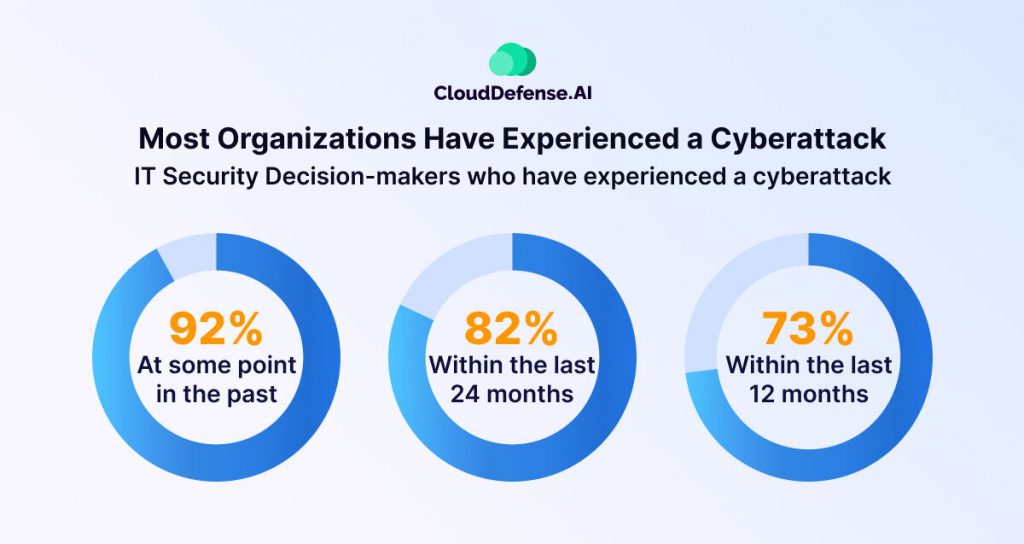
Cyberattacks can have devastating effects on businesses, impacting them financially, operationally, and in terms of reputation. Here’s an elaborate view of how cyberattacks can affect businesses:
Increased Costs
Businesses may incur significant financial losses due to cyberattacks. These costs include expenses related to cybersecurity technology, notifying affected parties, insurance premiums, public relations support, and ransom payments in the case of ransomware attacks. Legal costs may also arise from compliance efforts and civil cases resulting from data breaches.
Operational Disruption
Cyberattacks can disrupt normal business operations, leading to lost revenue and productivity. Attackers may use malware to erase valuable information or block access to essential systems, causing significant interruptions to business activities. Such disruptions can also damage reputations and diminish customer trust.
Altered Business Practices
Companies may need to reassess their data collection and storage practices to enhance security measures. Some businesses may opt to cease online operations altogether due to security concerns, while others may face increased scrutiny from customers regarding their security protocols.
Reputational Damage
Cyberattacks can tarnish a company’s reputation, decreasing customer trust and loyalty. Customers may be hesitant to share sensitive information with a company that has experienced a data breach, resulting in lost sales and revenue. Suppliers, partners, and investors may also lose confidence in the affected business, further damaging its reputation.
Lost Revenue
A significant consequence of cyberattacks is the potential loss of revenue as customers seek out more secure alternatives. Businesses may also suffer financial losses due to extortion attempts by hackers or legal settlements resulting from data breaches. Additionally, businesses may incur costs associated with repairing damaged systems and implementing enhanced security measures.
Stolen Intellectual Property
Cyberattacks can result in the theft of valuable intellectual property, including product designs, technologies, and go-to-market strategies. This stolen information can be used by competitors, resulting in lost market share and competitive advantage for the affected business.
Types of Cyberattacks
As we have seen so far, cyberattacks pose significant threats to organizations around the world. Let’s explore some of the common types of cyber attacks that enterprises face daily.
| Type of Attack | Use Case |
| DDoS Attacks | Overload systems to make them unresponsive. |
| Malware Attacks | Infected applications or links with malicious coding. |
| Phishing Attacks | Deceive users with fake emails to steal credentials. |
| MITM Attacks | Intercept and hijack unencrypted communications. |
| Password Attacks | Obtain passwords through network infiltration or social engineering. |
| Spear-Phishing Attacks | Targeted phishing attacks on specific individuals within a company. |
| DNS Tunneling and DNS Spoofing | Bypass security measures to establish communication or manipulate DNS records. |
| Ransomware | Hold systems hostage for ransom payments. |
| IoT-Based Attacks | Target vulnerable IoT devices to gain network access. |
| Spamming | Flood email systems with illegitimate emails, often carry out phishing attacks. |
Cyberattack Prevention, Detection, and Response
Preventing, detecting, and responding to cyberattacks is possible. Businesses can protect their data, their assets, and maintain operational continuity. Let’s explore how companies can prevent, detect, and respond to cyberattacks effectively:
Preventing Cyberattacks
Prevention is the first line of defense against hackers. By identifying vulnerabilities and implementing strong prevention measures, organizations can make their digital infrastructure impenetrable.
Here are a few tips on how you can do that.
- Establish Top-Down Policies: Senior management should integrate cybersecurity into corporate governance, allocating sufficient resources and demonstrating a commitment to security.
- Bottom-Up Practices: IT teams should focus on regular software updates, patching, network segmentation, and access management to minimize vulnerabilities and limit attack surfaces.
- Employee Training: Educate all employees on cybersecurity best practices, including the risks of unsecured communication, phishing attacks, and mobile device security.
Detecting Cyberattacks:
Early detection can help reflect potential attacks. Companies can apply vigilant monitoring and advanced threat detection technologies to swiftly identify and neutralize security breaches before they escalate into major incidents.
Here are a few tips on detecting cyberattacks:
- Proactive Measures: Adopt proactive approaches to threat detection and continuously monitor suspicious activities. You can use tools such as Hacker’s View™ and CloudDefense.AI’s Vulnerability Management tool to effectively detect underlying vulnerabilities that miss your eye effectively.
- Implement Security Solutions: Utilize endpoint detection and response tools, next-gen antivirus software, and entity identification tools to detect malware and other cyber threats.
- Continuous Monitoring: Regularly audit and conduct penetration testing across all systems, while monitoring incident logs and alerts for early detection of potential security breaches.
Responding to Cyberattacks:
In the aftermath of a cyberattack, a swift and effective response is crucial to minimizing damage and restoring normal operations. By implementing incident response plans and using cybersecurity expertise, organizations can mitigate the impact of breaches and swiftly recover from security incidents.
- Incident Response Plan: Develop and implement a complete incident response plan outlining procedures for responding to cyberattacks effectively.
- CNAPP Solutions: Use cloud-native application protection platforms to detect and isolate attacks, while generating detailed reports for informed decision-making. CNAPPs provide complete protection from all kinds of attacks in one package.
- Security Compromise Assessment: Conduct regular cyber security compromise and IT risk assessments to validate the existing security posture, identify vulnerabilities, and mitigate cyber risks effectively.
How can CloudDefense.AI Protect you from Cyberattacks?
CloudDefense.AI offers an all-in-one solution that secures your cloud infrastructure from code to cloud, ensuring your digital assets are safe from a wide range of attacks.
With powerful features like HackerView™ and Noise Reduction, CloudDefense.AI actively detects zero-day threats while filtering out unnecessary vulnerabilities, delivering up to five times more value than traditional tools. Its AI-driven remediation and continuous, agentless assessment ensure your applications are secure before production, smoothly integrating with your CI/CD pipelines.
CloudDefense.AI helps you prioritize vulnerabilities based on their real-world impact, so you can focus on what matters most. With real-time insights, detailed asset inventories, and context-driven threat management, you’ll stay ahead of evolving risks and meet critical compliance standards.
For simple, effective protection against cyber threats, CloudDefense.AI has you covered—allowing you to focus on growing your business with confidence. Book a free demo now!







