What is Crypto Ransomware? Crypto Malware Defined
Crypto ransomware, often referred to as crypto-malware, is a form of malicious software designed to encrypt files or hijack a victim’s computing resources for unauthorized purposes.
There are two primary ways this malware is typically utilized:
- Ransomware Attacks: In this scenario, crypto-malware encrypts critical files on a victim’s device and demands a ransom payment, usually in cryptocurrency, for the decryption key. Victims are pressured to pay because cybercriminals are the only ones with access to the decryption key necessary to restore the data.
- Cryptojacking: This involves the unauthorized use of a victim’s computing resources to mine cryptocurrency. Unlike traditional cryptomining, where miners solve complex mathematical problems to earn cryptocurrency legally, cryptojacking leverages malware to exploit another user’s processing power. This drains resources, slows down systems, and provides no benefits to the device owner while enriching the attacker.
While cryptocurrency itself is legitimate and offers secure, decentralized transactions, it has become a popular tool for cybercriminals due to its anonymity and difficulty to trace. Crypto-malware, therefore, represents a significant cybersecurity threat, as it exploits both individuals and organizations for financial gain, often leaving behind operational and financial damage.
How does Crypto Ransomware Work?
Crypto ransomware is one of the most destructive types of malware, designed to exploit victims by encrypting their data and demanding payment for its release. Unlike traditional malware, which may steal data or cause disruption, crypto-ransomware focuses on holding your files hostage, effectively locking you out of your systems until a ransom is paid—usually in cryptocurrency.
Step-by-Step Process of Crypto Ransomware
1. Infection and Entry: Crypto ransomware typically enters a system through phishing emails, malicious downloads, or vulnerabilities in software. These infection vectors disguise ransomware as legitimate files or links, tricking users into unknowingly downloading and executing the malware.
2. Execution and Encryption: Once inside, the ransomware executes its payload, scanning the victim’s system for valuable files, including documents, images, databases, and backups. It uses advanced encryption algorithms to lock these files, rendering them inaccessible without the corresponding decryption key.
3. Ransom Note Deployment: After encryption is complete, the ransomware generates a ransom note, often displayed as a pop-up or saved as a text file on the victim’s desktop. This note typically includes:
- Details of the attack (e.g., which files were encrypted).
- Instructions on how to pay the ransom, often via cryptocurrency, to maintain anonymity.
- A deadline for payment is sometimes accompanied by threats of permanent data loss or increased ransom amounts if the victim delays.
4. Optional Data Theft: Some modern variants of crypto-ransomware also exfiltrate sensitive data before encrypting it. This “double extortion” tactic pressures victims into paying not only to unlock their files but also to prevent the public release of stolen information.
5. Payment and (Potential) Decryption: Victims are instructed to transfer cryptocurrency to the attacker’s wallet. After payment, the attacker may (or may not) provide a decryption key to unlock the encrypted files. No guarantee paying the ransom will recover all data, and some victims are targeted multiple times.
Types of Crypto Malware
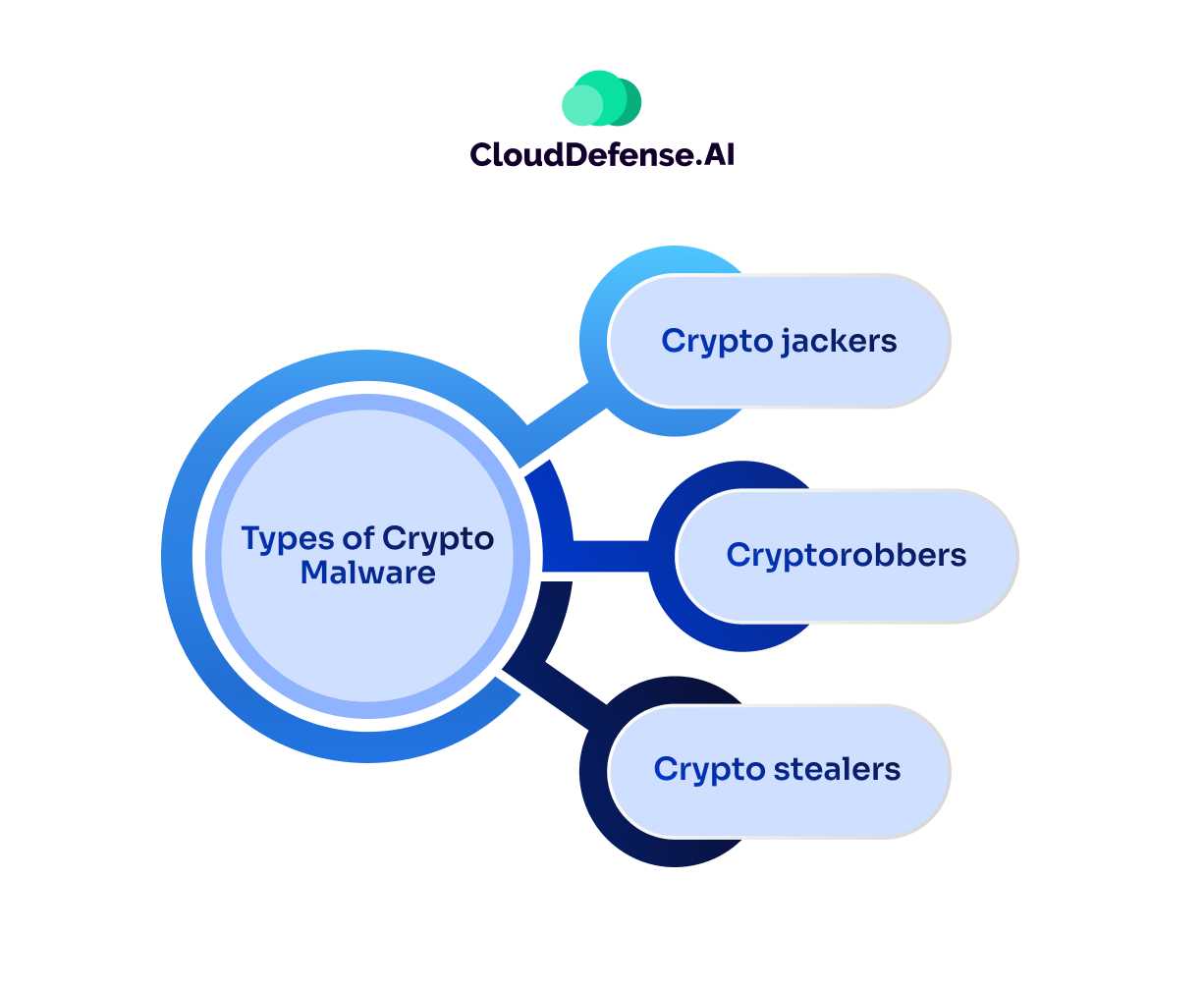
Crypto malware includes various malicious programs, each designed for a specific purpose in the world of cryptocurrency. The main types include:
- Ransomware: This notorious form of malware encrypts a victim’s files and demands a cryptocurrency ransom in exchange for the decryption key. It is one of the most financially damaging types of crypto malware.
- Crypto Jacking: Attackers use crypto jacking to hijack a victim’s system and leverage its resources for cryptographic tasks like generating wallets or verifying transactions. This allows cybercriminals to mine cryptocurrency without the victim’s consent, often leading to a drain on system resources.
- Crypto Robbers: Crypto robbers specifically target crypto wallets, platforms, and applications. Their goal is to steal cryptocurrency by gaining unauthorized access to private keys, enabling them to withdraw funds directly from the victim’s wallet.
- Crypto Stealers: Designed to extract sensitive information like wallet files, credentials, and private keys, crypto stealers are often used in large-scale attacks. They frequently target trading platforms and mining software, stealing data that is either sold on the dark web or used for further malicious activities.
Each type of crypto malware poses a significant threat to individuals and businesses involved in cryptocurrency, highlighting the need for robust security measures.
Examples of Crypto Malware
Crypto malware has gained significant popularity due to its ability to secretly leverage victims’ resources for cryptocurrency mining. Over the years, numerous crypto malware variants have emerged, each with unique features and attack methods. Below are some notable examples of crypto malware to watch out for:
- WannaMine: WannaMine is a crypto worm that targets systems to mine Monero cryptocurrency. It spreads primarily through the EternalBlue exploit and uses Windows Management Instrumentation (WMI) event subscription to maintain persistence on the system while mining in the background.
- XMRig: XMRig is an open-source crypto-jacking malware commonly integrated into other types of malware. It enables attackers to mine Monero or Bitcoin using a victim’s computing resources, making it a popular choice for widespread attacks.
- RubyMiner: Discovered in 2018, RubyMiner targets Linux and Windows servers, specifically vulnerable web servers, to install XMRig and mine Monero. It utilizes the system’s computational power to generate cryptocurrency.
- LemonDuck: Also discovered in 2018, LemonDuck is notorious for its multiple propagation methods, including exploiting vulnerabilities, using malspam, and compromising RDP credentials. While primarily used for crypto mining, it can also deliver additional malware and steal email credentials.
- Darkgate: First identified in 2017, Darkgate is a powerful crypto malware that targets Windows systems for mining and other malicious activities. It enables cybercriminals to steal sensitive credentials, launch ransomware, perform remote access tool (RAT) functionality, and more.
- Graboid: Graboid is a unique crypto malware with worm-like characteristics, capable of infecting systems through unsecured cloud containers. Once introduced, it rapidly spreads across connected devices. It has reportedly infected over 2000 Docker containers since its discovery.
- PowerGhost: PowerGhost is a potent malware used by cybercriminal organizations to target and infect systems within organizations. It is particularly dangerous due to its ability to disable antivirus software, making it difficult to detect. This allows attackers to maximize cryptocurrency mining without being noticed.
- Coinhive: Coinhive is a cryptojacker that utilizes JavaScript to mine cryptocurrency. Originally intended for use by website owners to mine coins with user consent, it was hijacked by malicious actors to exploit victims’ devices through ad clicks without their consent.
- Rakhni Trojan: The Rakhni Trojan is a versatile crypto malware that assesses the computational capabilities of a victim’s system. If the system is powerful enough, it is used for mining cryptocurrency. On weaker systems, it switches to ransomware attacks.
- Prometei: Prometei is a botnet malware that creates a network of infected computers, controlled remotely by attackers. It exploits known vulnerabilities to spread across systems, aiming to mine Monero on a large scale.
Each of these crypto malware variants demonstrates the diverse and evolving threats in the world of cryptocurrency mining. Vigilant security measures are crucial to protect against such attacks.
Why Cryptocurrencies Are Used for Ransom Payments?
Cryptocurrencies like Bitcoin and Monero are the preferred payment method for cybercriminals orchestrating ransomware attacks. Their features provide attackers with advantages that make cryptocurrencies an ideal choice for demanding ransom payments.
Anonymity and Pseudonymity
Cryptocurrencies allow transactions without revealing the real-world identities of the sender or receiver. While not completely anonymous (as some transactions can be traced via blockchain analysis), they provide pseudonymity, making it significantly harder to trace funds back to the criminal. Privacy-focused cryptocurrencies like Monero enhance this anonymity by hiding transaction details and wallet addresses.
Global Accessibility
Cryptocurrencies operate independently of centralized financial systems, allowing transactions to occur across borders without government or bank restrictions. This global accessibility makes them attractive to attackers targeting victims worldwide.
Irreversible Transactions
Unlike credit card or bank transactions, cryptocurrency payments are irreversible once completed. This eliminates the possibility of chargebacks, ensuring attackers keep the ransom without fear of the victim reversing the payment.
Ease of Use and Automation
Setting up a cryptocurrency wallet is relatively easy, and attackers can quickly create unique wallet addresses for each victim. This not only simplifies payment collection but also allows them to track payments efficiently. Some ransomware strains even have automated dashboards for victims, providing payment instructions and real-time updates on whether the ransom was received.
Lack of Regulation
Cryptocurrencies operate in a decentralized manner, meaning no single authority controls them. This makes it difficult for law enforcement agencies to freeze or intercept funds. Attackers exploit this lack of oversight to their advantage.
Perceived Trustworthiness for Victims
Attackers often claim that paying in cryptocurrency guarantees decryption, as it demonstrates the victim’s compliance and willingness to follow instructions. This trust-building tactic increases the likelihood of payment.
How to Detect Crypto Ransomware?
Crypto ransomware operates stealthily, exploiting your system’s resources to mine cryptocurrency for attackers. Detecting it early is crucial to prevent performance degradation and potential security risks. Here’s how you can identify its presence effectively:
Unusual System Performance
- Symptoms: A sudden drop in performance, high CPU or GPU usage even when idle, or systems running hotter than usual.
- Why It Happens: Mining malware maximizes your system’s computational power to solve cryptographic puzzles, overloading resources.
- Detection Tip: Use system monitors like Task Manager or Activity Monitor to identify processes consuming excessive resources.
Spiking Electricity Bills
- Symptoms: Noticeably higher energy consumption.
- Why It Happens: Mining operations demand significant energy, and infected systems often run continuously at full capacity.
- Detection Tip: Monitor power usage trends, especially in enterprise environments.
Browser-Based Symptoms
- Symptoms: Browser tabs becoming unresponsive, fans spinning up while visiting certain websites, or excessive memory usage.
- Why It Happens: Some malware leverages malicious scripts embedded in websites to mine cryptocurrency through browsers.
- Detection Tip: Use browser extensions like NoScript or miner blockers to detect and block such activities.
Unrecognized Processes or Files
- Symptoms: Unknown or suspicious processes running in the background.
- Why It Happens: Malware often masquerades as legitimate processes or installs files in hidden directories.
- Detection Tip: Regularly audit running processes and installed programs. Tools like Process Explorer or autoruns can help spot anomalies.
Network Traffic Anomalies
- Symptoms: Increased outbound traffic or connections to suspicious IP addresses.
- Why It Happens: Mining malware communicates with external servers to send mined cryptocurrency or receive commands.
- Detection Tip: Use network monitoring tools to analyze traffic patterns and identify connections to mining pools.
Endpoint Protection Alerts
- Symptoms: Security software flagging crypto mining behaviors or suspicious activities.
- Why It Happens: Modern endpoint detection solutions are trained to recognize mining patterns.
- Detection Tip: Keep your antivirus and endpoint protection software updated to detect the latest threats.
Battery Drain on Mobile Devices
- Symptoms: Rapid battery drain or overheating in mobile phones and tablets.
- Why It Happens: Mining malware on mobile devices exploits their processors, significantly increasing power consumption.
- Detection Tip: Check for unrecognized apps and remove suspicious ones immediately.
Detecting crypto mining malware requires vigilance and proactive monitoring. Use a combination of system performance checks, network traffic analysis, and up-to-date security tools to stay ahead. Early detection minimizes damage and ensures your resources remain secure from malicious exploitation.
How to Prevent Crypto Malware Attack
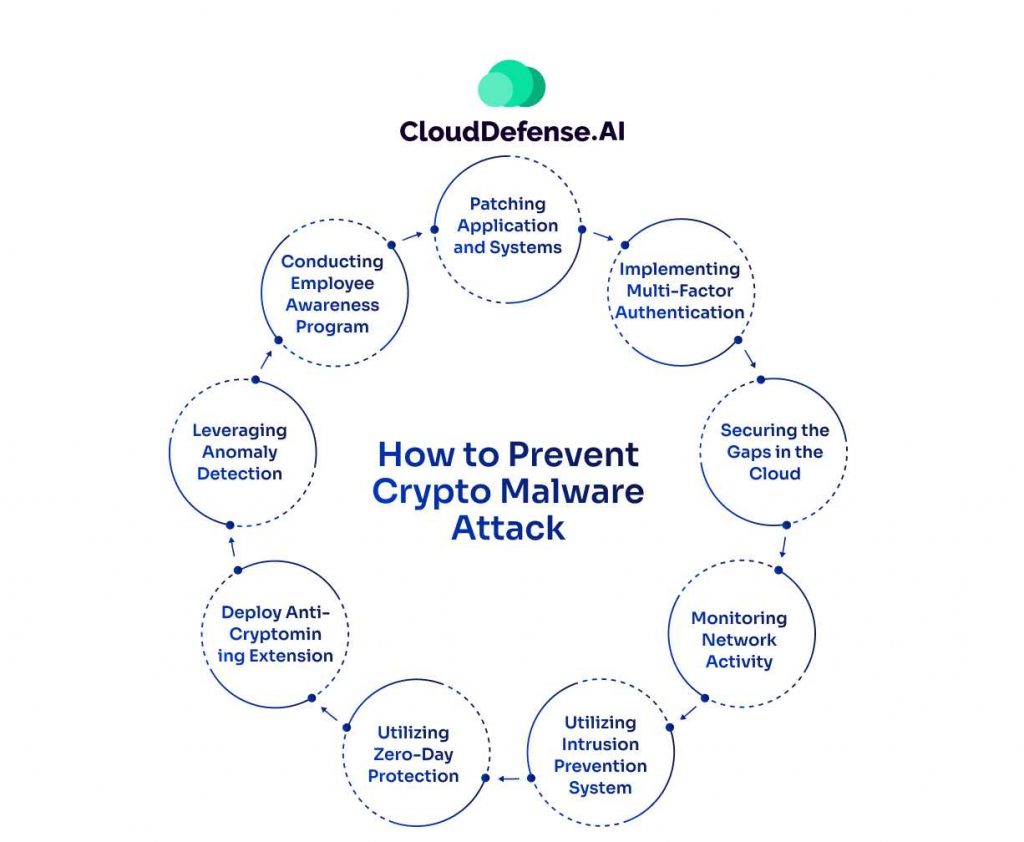
To defend against crypto ransomware, organizations and individuals must adopt a proactive security posture:
- Backup Data Regularly: Maintain offline backups to ensure you can recover data without paying a ransom.
- Keep Software Updated: Regularly patch vulnerabilities in operating systems and applications.
- Enable Endpoint Protection: Use advanced anti-malware tools capable of detecting and neutralizing ransomware threats.
- Employee Training: Educate users to recognize phishing attempts and avoid suspicious downloads.
- Network Segmentation: Limit the spread of ransomware by isolating critical systems and sensitive data.
Crypto ransomware is a formidable cyber threat, but understanding its workings and implementing strong defenses can minimize the risk and impact of an attack.
How CloudDefense.AI Can Help?
CloudDefense.AI is a top-tier CNAPP platform that is known for offering comprehensive protection against malware threats. CloudDefense.AI provides a comprehensive set of security measures that include secret management, IaC scanning, container vulnerability management, and ransomware protection to help you fight against crypto-malware attacks.
With this platform, not only will you get centralized control, but you will also get complete visibility into your entire IT infrastructure. CloudDefense.AI will help you to prevent all the loopholes, exposed secrets, and vulnerabilities that crypto malware can utilize to gain entry into the system.
It secures the cloud infrastructure from every endpoint and ensures continuous monitoring to ensure none of the attackers can exploit loopholes to place crypto malware. To learn more about how CloudDefense.AI can protect your organization against crypto malware, you should request a free live demo.







