What is Container Security Scanning?
Container security scanning is a method of examining container images for vulnerabilities and security risks, helping developers address threats before they lead to breaches. As containerized applications become more prevalent, container scanning plays a critical role in maintaining application integrity in modern DevOps environments.
Unlike traditional architectures, containers package application code and dependencies, creating unique security challenges. Container security scanning seamlessly integrates into CI/CD pipelines, ensuring vulnerabilities are identified early without slowing down development.
This article explores how container security scanning enhances software development processes, focusing on the tools and strategies necessary for effective DevOps integration. We’ll also discuss open-source container scanning tools and offer insights into security implementations for containerized environments.
How do Container Security Scanners Work?
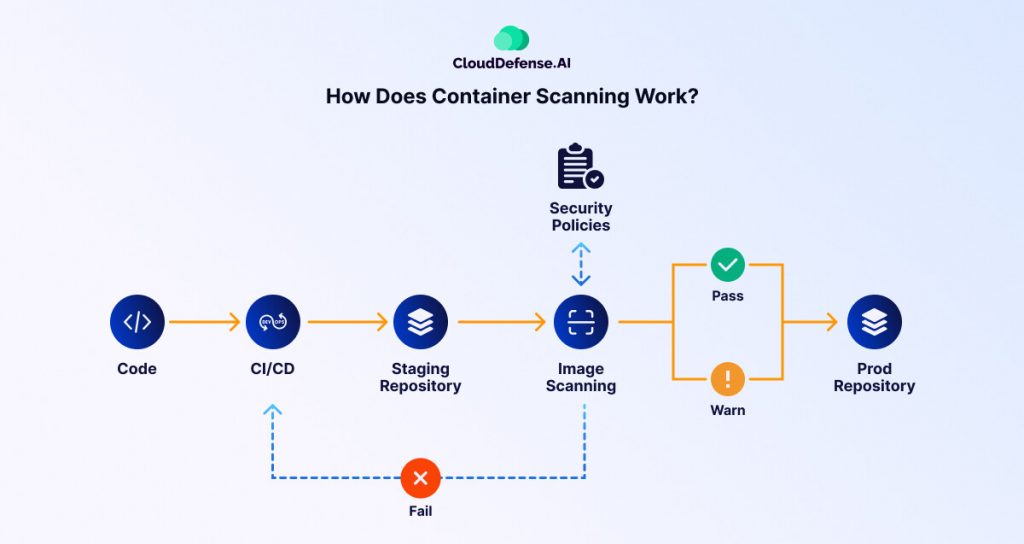
Container security scanning, or container scanning, operates in three major steps that allow it to counter threats effectively. Firstly, the base images of a container are analyzed. Base images that are used to build a container often have software libraries and packages pre-loaded in them. These packages can cause runtime errors and open up potential vulnerabilities.
Once the base images have been scanned, it is important to analyze third-party resources that are being used for your application. Third-party resources often come with vulnerabilities that can prove to be critical for you if you do not detect them on time. With runtime container scanning, all vulnerabilities are detected in real-time.
Lastly, container scanning helps to assess your application’s source code. This helps to make sure that there are no misconfigurations and other security issues that can become a potential threat in the future.
Importance of Container Security Scanning
With the risk of containers being exploited increasing, it has become very important to include container scanning tools in organizations. Container security scanning not only helps to identify vulnerabilities in a container image but also comes with many other benefits that make it ideal for a DevSecOps approach.
Container security scanning allows you to carry out compliance checks by vetting the application being developed to ensure it is adhering to industry security standards and regulations. Other than that, you can also detect misconfigurations through this tool. This is a huge plus, as misconfigurations often lead to potential vulnerabilities that can be exploited.
Types of Container Security Scanning
Container security scanning includes various approaches to thoroughly assess and secure containerized environments. Each scanning type addresses unique aspects of the container lifecycle to ensure a strong security posture. Here are the main types of container security scanning:
- Image Scanning: Image scanning identifies vulnerabilities within container images by analyzing their layers, which contain application code, dependencies, and libraries. This scanning type inspects each layer for outdated packages, misconfigurations, and known vulnerabilities. By scanning images before they’re deployed, developers can prevent vulnerabilities from entering production. Many CI/CD pipelines incorporate image scanning to catch security issues early.
- Runtime Scanning: Runtime scanning continuously monitors containers in their active environment to detect suspicious behavior, such as unauthorized access, privilege escalation, or cryptojacking. Unlike image scanning, runtime scanning focuses on real-time threats, alerting security teams to abnormal activity as it happens. This method is critical for detecting threats that may not be visible until containers are running.
- Registry Scanning: Registry scanning assesses container images stored in private or public repositories (registries) to ensure they’re secure before being pulled into production environments. Regularly scanning registries helps maintain a repository of secure images and avoids deploying vulnerable ones. Registry scanning is especially useful in collaborative environments where multiple teams access shared repositories.
- Configuration Scanning: Configuration scanning evaluates container settings and configurations to ensure they follow security best practices. This type of scanning verifies permissions, network settings, and access controls, which can prevent common issues like exposed ports, excessive privileges, or insecure storage. By addressing configuration risks, teams can reduce the likelihood of privilege escalation attacks or unauthorized access.
- Secrets Scanning: Secrets scanning identifies sensitive information, like API keys, tokens, and passwords, that may be embedded within container images or configuration files. Exposing these secrets is a common security risk that attackers can exploit. Secrets scanning tools ensure credentials are stored securely outside of images, protecting critical access points within the container environment.
- Dependency Scanning: Dependency scanning identifies vulnerabilities in third-party dependencies used within containers. Many containerized applications rely on external libraries, which can introduce risks if they’re not updated. By scanning for issues in dependencies, organizations can prevent attacks that exploit outdated or insecure libraries and frameworks.
- Network Scanning: Network scanning assesses the containerized environment’s network configurations to identify any misconfigurations, open ports, or excessive access permissions that could lead to unauthorized access. This scanning type helps secure the network layer of containers by ensuring network policies are properly configured, which reduces the attack surface and prevents lateral movement.
Common Container Vulnerabilities
Containerized applications streamline development and deployment, yet they also bring unique security risks. Here’s a breakdown of the most significant vulnerabilities impacting containerized environments:
Outdated Software in Container Images
Container images are designed to be immutable, but they often contain outdated software or libraries that leave them vulnerable. Although secure when first created, images become susceptible as components age without updates. Regular vulnerability scans are essential to identify issues in images, allowing teams to roll out updated, secure versions.
Excessive Privileges and Privilege Escalation
In container environments, granting excessive privileges is risky, as attackers may exploit these permissions to access the root operating system. Privilege escalation often targets flaws in container runtimes, such as runC, which powers Docker and other container systems. Past vulnerabilities have allowed attackers to overwrite files on the host, gaining root access. Limiting privileges, regularly updating runtimes, and using secure access policies can prevent these risks.
Cryptojacking Attacks
Cryptojacking occurs when attackers use compromised container resources to mine cryptocurrency. A known Docker vulnerability (CVE-2018-15664) allows attackers to gain root access to a host and harness its CPU and GPU for mining. Attackers can also steal sensitive data or launch phishing attacks. Securing API endpoints and ensuring access controls can significantly reduce the risk of cryptojacking.
Vulnerable Networking Configurations
Containers often use default networking configurations, which may lack isolation, allowing unauthorized traffic to access sensitive container environments. Attackers can exploit open ports and misconfigurations to intercept traffic or access containers directly. It’s essential to configure network policies, isolate critical containers, and limit open ports to secure container networks.
Misconfigured Secrets Management
Containers often rely on credentials and secrets to function. Storing these secrets in plaintext within the container image or configuration files is a major security risk. If accessed, attackers could exploit sensitive data or gain control of other parts of the infrastructure. Using secure secrets management tools and ensuring that credentials are stored outside the container image can safeguard these assets.
Poisoned or Malicious Images
Public repositories may contain images that appear legitimate but are injected with malicious code. Using unverified images or dependencies introduces the risk of running compromised software. Verifying images from trusted sources, implementing image-signing, and scanning before deployment can help prevent poisoned image threats.
Insecure API Endpoints
Exposed API endpoints, especially when unsecured, can leave containers vulnerable to unauthorized access. Attackers can exploit exposed APIs to gain entry into container environments, modify configurations, or even shut down services. Implementing API authentication, authorization, and rate-limiting, along with firewall protection, can secure container APIs from unauthorized access.
Benefits of Container Security Scanning
Container security scanning is essential for maintaining secure, reliable applications in modern development environments. By integrating scanning tools into DevOps workflows, organizations can detect vulnerabilities early, reduce costs, and ensure compliance, all while building trust with users and stakeholders through proactive security measures. Here are the key benefits of container scanning:
- Vulnerability Detection: Container security scanning enables early detection of vulnerabilities within the development cycle. By identifying risks before production, it helps prevent breaches and ensures a more secure deployment process.
- Cost-Effective Security Measures: Addressing security issues early is far cheaper than post-deployment fixes. Container scanning reduces long-term costs by identifying vulnerabilities during the build phase, minimizing the risk of expensive security incidents.
- Promoting Trust with Users and Stakeholders: Adopting container security scanning demonstrates a commitment to protecting sensitive data, which increases trust among end users and stakeholders, reassuring them that security is always a priority.
- Ensuring Compliance and Reducing Risks: For industries with strict regulations, container security scanning ensures compliance by detecting vulnerabilities that could result in non-compliance, helping to meet security standards consistently.
- Seamless Integration into DevOps: Container security scanning tools fit smoothly into DevOps workflows, automating security checks without slowing down development. This ensures continuous security while maintaining speed and efficiency in the pipeline.
Best Practices for Container Image Scanning
Just like any other technology, there are a few best practices that can help you improve the efficiency of container image scanning.
Using Minimal Images:
Reducing base images helps in contracting the attack surface for a cyber attacker. It is advisable only to use light images. The lighter an image is, the lesser the probability of it containing a vulnerability that can be exploited.
Scan Parent Images Thoroughly:
Docker images are created by building over a base image. Therefore, if the base image contains a vulnerability, all the other images built over it will be prone to attacks as well. It is necessary to ensure that the parent image doesn’t contain any known vulnerabilities by scanning it a few times.
Infuse Container Image Scanning In The CI/CD Pipeline:
Continuous scanning of images is very important before building a container. The best and most efficient way to do this is by embedding the scanning process in the CI/CD pipeline. Implementing all the processes through a CI/CD pipeline helps in identifying vulnerabilities early on; this mitigates any chances of the vulnerabilities reaching the production environment.
Scanning For Vulnerabilities In Third-party Resources:
Just as much as it is important to scan local libraries and frameworks, you also need to prioritize scanning third-party resources.
Automating The Container Scanning Process:
To achieve a complete DevSecOps development environment, you must automate all container scanning processes. Other than that, consider enforcing policies that require all images and third-party resources to undergo screening. This helps in creating a healthy habit for your system security.
Updating Base Images And Monitoring For New Vulnerabilities:
With time, base images can get outdated and open up vulnerabilities. It is important to keep checking for new updates so that the base images are at their most secure version. New vulnerabilities keep showing up in the industry as well. Always ensure that your security team is continuously updating the vulnerability databases with any vulnerability that pops up.
Challenges in Container Security Scanning
Container scanning can pose various challenges that organizations need to address:
- Quality of Machine Learning: Modern container scanning tools resort to Machine Language models to leverage their efficiency. However, the effectiveness of these scans is highly dependent on how effective the ML model is. To achieve reliable results, organizations need to train these models with updated data, which again requires a lot of financial involvement.
- Scanning Depth and Tool Variability: Not all container scanning tools provide the same level of analysis. Most container scanning tools that are available in the market only scan the images and do not check for misconfiguration or other underlying vulnerabilities. Before selecting a tool, it is important to check whether it is sufficient for the company’s needs.
- Dealing with “Noise”: The issue of false positives and false negatives can introduce challenges in container scanning. False positives occur when a scanner incorrectly identifies a vulnerability that isn’t a real threat, potentially causing unnecessary concern and effort. Conversely, false negatives happen when a scanner fails to detect a genuine vulnerability, which can lead to significant security incidents.
Conclusion: Container Scanning with CloudDefense.AI
Containers are constantly evolving within IT infrastructures, introducing new security challenges that can be exploited by malicious actors. To stay ahead of these threats, you need a solution that adapts to dynamic environments.
CloudDefense.AI offers a complete, all-in-one container security platform, providing continuous scanning, securing, and monitoring of your containers at every stage of the development lifecycle.
- Precise Vulnerability Assessment: CloudDefense.AI uses an up-to-date vulnerability database, reducing false positives and ensuring reliable threat detection.
- Shift-Left Security Integration: With shift-left security, you can embed vulnerability checks early in the CI/CD pipeline, identifying and fixing issues before deployment.
- Protection for Third-Party Resources: Secure base images, Docker files, and all dependencies to mitigate risks introduced by third-party resources.
- AI-Driven Real-Time Monitoring: The platform’s AI-driven engine detects vulnerabilities in real-time, empowering security teams to take immediate action.
- Holistic Insight for Vulnerability Management: CloudDefense.AI provides detailed security information, helping your team prioritize vulnerabilities and focus on the most critical risks.
Take Control of Your Container Security
CloudDefense.AI equips your organization with 100% container coverage, providing continuous protection and reducing the likelihood of breaches. Don’t wait for a security incident—proactively defend your containerized environments with CloudDefense.AI.
Start today and see how CloudDefense.AI transforms your security posture, enhancing development efficiency while ensuring comprehensive container protection.
FAQ
What is the significance of container scanning?
Containers often have vulnerabilities that threat actors can exploit to steal data or gain access to a system. Companies that develop containerized applications should carry out container scans to ensure a secure development environment.
Can container scanning tools be integrated into the CI/CD pipeline?
Yes, an automated approach to container scanning can help in integrating the whole process in a CI/CD pipeline. Tools such as CloudDefense.AI’s container scanning tools help in achieving that. Integrating container scanning into the CI/CD pipeline helps in identifying threats early on in the development process.
How often should containers be scanned for security vulnerabilities?
Container images should be scanned daily. Once while they are in the development pipeline, and again when they are in the production environment. Automating container image scans is the best way to address this process.







