The cloud has completely changed the way we access and utilize computing resources. But with the rise of this technology comes a new vocabulary, and “cloud workload” is often tossed around without a clear explanation. This article aims to demystify this term and provide a clear understanding of what it entails.
In simple terms, a cloud workload includes the resources and processes required to run an application or service within a cloud environment. This includes the software itself, the underlying infrastructure (like virtual machines or storage), and the network connections that enable it to function.
Keep reading as we explore what a cloud workload is, the different types of cloud workloads, their benefits, how to secure them, and the considerations involved in managing them effectively.
What is a Cloud Workload?

At its core, a cloud workload is an aggregation of computing resources and processes required to run an application or service within a cloud computing environment. These resources can be broadly categorized into three main components:
- Virtual Machines (VMs): These are simulated computers within the cloud, providing a dedicated environment for running specific software and applications.
- Storage: This refers to the data storage solutions offered by cloud providers, allowing applications to store and access critical information.
- Networking: This component ensures seamless communication between different elements of the workload, enabling data transfer and interaction within the cloud environment.
Beyond these core resources, software applications and data processing tasks also constitute essential parts of a cloud workload. These work in conjunction with the underlying infrastructure to deliver the desired functionality of the application or service.
Types of Cloud Workloads
Just as different engines power various vehicles, cloud workloads come in diverse forms, each suited to specific needs and functionalities. Here’s a glimpse into the diverse range of cloud workloads:
1. Based on Resource Needs:
- General Workloads: These are the most common types of cloud workloads. They are used for a wide range of applications that don’t need specialized hardware, such as websites, email servers, and basic database applications. They typically run on standard virtual machines.
- GPU-Intensive Workloads: These workloads handle tasks that demand a lot of processing power, particularly those involving complex calculations or graphics rendering.
For example, machine learning model training, video editing, and scientific simulations. These utilize specialized virtual machines equipped with Graphics Processing Units (GPUs).
- High-Performance Computing (HPC): These are the most demanding types of cloud workloads. They deal with extremely complex tasks and massive datasets that require huge computing power, often across many interconnected machines.
Examples include weather modeling, pharmaceutical research, and financial risk analysis.
2. Based on Usage Patterns:
- Static Workloads: These workloads run continuously with a consistent level of demand for resources. They are ideal for applications that should always be available, such as a company’s website or an internal email system.
- Periodic Workloads: These workloads run on a predictable schedule, with spikes in resource usage at certain times. Example: a monthly report generation process or a daily data backup task.
- Real-Time Workloads: These workloads process data and respond immediately. Examples: live chat applications, financial trading platforms, or online games.
3. Based on Deployment Model:
- Infrastructure as a Service (IaaS): Gives users the highest level of control but also the most responsibility. Users manage everything from the operating system, networking, and storage up to the application layer.
- Platform as a Service (PaaS): The cloud provider takes care of the lower-level infrastructure, allowing users to focus on developing and deploying their applications.
- Software as a Service (SaaS): In SaaS, applications are offered as fully managed services, accessed over the Internet. Users don’t need to worry about any underlying infrastructure or software maintenance.
4. Based on Cloud Native Technology:
- Virtual Machines (VMs): The traditional building block of cloud infrastructure; each application is deployed within a self-contained virtual machine, providing a high level of isolation and control.
- Containers: Offer lightweight and portable packaging for applications, enabling faster deployment and greater scalability. They are ideal for microservices-based architectures where applications are broken down into smaller components.
- Serverless Computing: Focus shifts to code only, with the cloud provider managing all underlying infrastructure. Best suited for unpredictable workloads with short, event-driven tasks like image processing or responding to API requests.
Tasks That Are Suitable for the Cloud Workloads
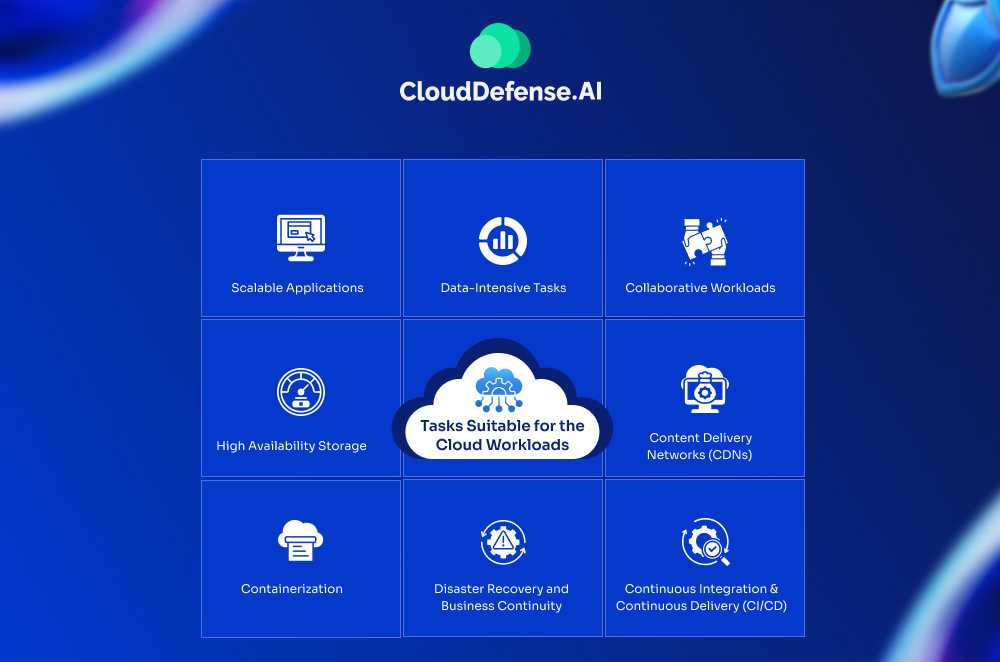
With the diverse range of cloud workloads laid out, let’s delve into the types of tasks that are particularly well-suited for this powerful technology:
1. Scalable Applications: Cloud workloads excel at accommodating fluctuating demands. Applications with unpredictable or bursty traffic patterns, like e-commerce platforms during sales or social media apps during peak hours, benefit from the cloud’s ability to scale resources up or down seamlessly.
2. Data-Intensive Tasks: Cloud environments offer vast, scalable storage solutions, making them ideal for handling large datasets and complex data processing needs. Tasks like scientific research, big data analytics, and machine learning training can efficiently leverage cloud resources.
3. Collaborative Workloads: Cloud-based applications enable seamless collaboration and information sharing in real-time, regardless of geographical location. Teams can work on documents, projects, and data simultaneously, fostering improved communication and productivity.
4. Content Delivery Networks (CDNs): Cloud workloads are instrumental in powering CDNs, geographically distributed networks of servers that deliver content like web pages, videos, and images to users with minimal latency. This, in turn, ensures a fast and smooth user experience for geographically dispersed audiences.
5. Continuous Integration and Continuous Delivery (CI/CD): Cloud platforms streamline the CI/CD pipeline, automating the process of building, testing, and deploying applications. Hence users can achieve faster development cycles, improved code quality, and quicker delivery of new features.
6. Disaster Recovery and Business Continuity: Cloud workloads come with inherent redundancy and disaster recovery capabilities, providing a protective layer for your data and applications in the event of unforeseen incidents. By doing so, they guarantee business continuity and reduce downtime, allowing your operations to maintain a seamless flow.
7. Containerization: This approach to software development packages applications and their dependencies into standardized units called containers. These containers are lightweight, and portable, and enable faster deployment, scaling, and application isolation. Cloud environments provide ideal platforms for deploying and managing containerized workloads, making them suitable for microservices architectures and modern application development.
8. High Availability Storage: Cloud storage solutions provide various configurations, including options specifically crafted for high availability. Such configurations ensure data redundancy and accessibility, even in the event of failures in individual storage components. Maintaining high-availability storage is imperative for mission-critical applications and disaster recovery plans, enabling businesses to uphold data integrity and minimize downtime.
Cloud Workload Security Challenges
While cloud workloads offer numerous benefits, they also present unique security challenges that require careful consideration and proactive measures. Here’s an overview of some key concerns:
1. Shared Responsibility Model
In the cloud, security responsibilities are shared between the cloud provider and the customer. Understanding this model and clearly defining each party’s obligations is crucial to ensure comprehensive security coverage.
2. Misconfigurations
Accidental or intentional misconfigurations of cloud resources, security settings, and access controls can leave vulnerabilities open for attackers to exploit. Implementing automated tools for configuration management and enforcing strict access controls can mitigate this risk.
3. Insider Threats
Malicious actors within an organization can pose a significant threat, as they may have authorized access to cloud resources and data. Implementing robust access control mechanisms, monitoring user activity, and fostering a culture of security awareness can help address this challenge.
4. Data Security and Compliance
Ensuring data security and compliance with relevant regulations requires careful attention to encryption, access control, and data residency requirements. Cloud providers offer various tools and services to support data security, but the ultimate responsibility lies with the customer to implement appropriate safeguards.
5. Evolving Attack Surface
Cybercriminals are constantly developing new methods to exploit vulnerabilities. Staying informed about the latest threats, implementing regular security assessments and vulnerability scanning, and patching vulnerabilities promptly are crucial for maintaining a strong security posture.
6. Lack of Visibility and Control
Compared to on-premises environments, cloud workloads may present challenges in terms of visibility and control. Implementing cloud security posture management (CSPM) tools and leveraging cloud provider security services can help organizations gain better visibility into their cloud workloads and streamline security management.
Best Practices for Cloud Workload Security
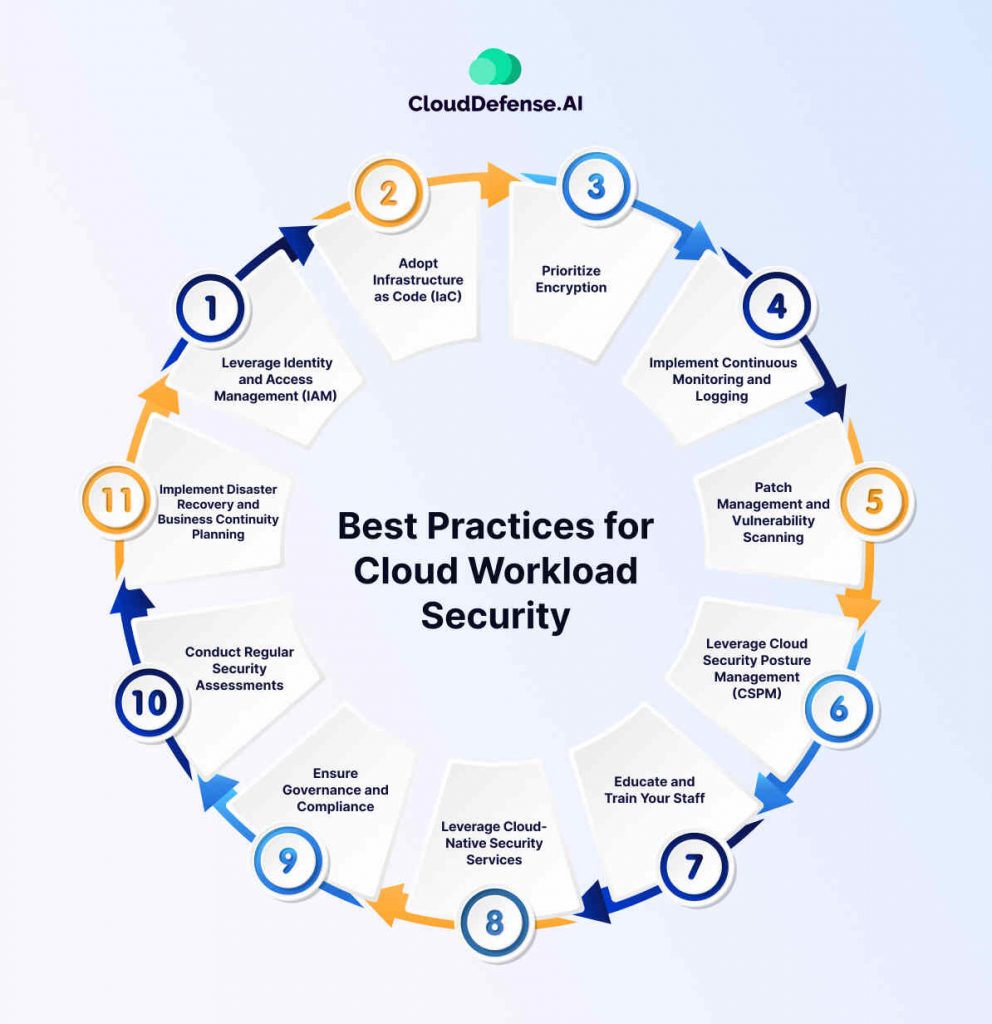
1. Leverage Identity and Access Management (IAM): Implement IAM controls to grant users and applications least privilege access to cloud resources. Utilize multi-factor authentication (MFA) for added security and regularly review and update access permissions.
2. Adopt Infrastructure as Code (IaC): Automate infrastructure provisioning and configuration management using IaC tools. This ensures consistency, reduces the risk of human error, and simplifies security enforcement across your cloud environment.
3. Prioritize Encryption: Encrypt data at rest and in transit to safeguard sensitive information, even in the event of a security breach. Utilize cloud provider encryption tools and explore additional encryption options for enhanced protection.
4. Implement Continuous Monitoring and Logging: Continuously monitor your cloud workloads for suspicious activity and security events. Leverage logging and SIEM (Security Information and Event Management) tools to aggregate and analyze security data for timely threat detection and response.
5. Patch Management and Vulnerability Scanning: Regularly patch vulnerabilities in your cloud workloads and operating systems to address known security flaws. Automate vulnerability scanning processes to identify and remediate vulnerabilities promptly.
6. Leverage Cloud Security Posture Management (CSPM): Utilize CSPM tools to gain comprehensive visibility into your cloud workloads, identify security misconfigurations, and ensure compliance with security best practices and regulations.
7. Educate and Train Your Staff: Develop a culture of security awareness within your organization by providing regular training and education to employees on secure cloud practices, phishing attempts, and social engineering tactics.
8. Leverage Cloud-Native Security Services: Many cloud providers offer a range of security services tailored to specific needs. Explore and utilize these services to enhance your cloud workload security posture, such as web application firewalls (WAFs) and cloud workload protection platforms (CWPPs).
9. Ensure Governance and Compliance: Establish strong governance controls and implement compliance policies to ensure your organization adheres to legal and regulatory requirements specific to your industry. Partner with a trusted cloud provider that demonstrably prioritizes security and adheres to industry standards, such as ISO 27001 and SOC 2.
10. Conduct Regular Security Assessments: Schedule regular security assessments and penetration testing to identify and address potential vulnerabilities in your cloud workloads before attackers can exploit them.
11. Implement Disaster Recovery and Business Continuity Planning: Develop a good disaster recovery plan that outlines procedures for recovering your cloud workloads in case of unforeseen events. This plan should include data backup and recovery strategies, ensuring minimal downtime and data loss.
Optimizing Security with Cloud Workload Protection Platforms (CWPPs): Introducing CloudDefense.ai
While implementing the best practices outlined above is crucial, securing your cloud workloads requires a comprehensive approach. This is where Cloud Workload Protection Platforms (CWPPs) come into play.
CloudDefense.ai is a leading CWPP solution designed to empower organizations with advanced security capabilities tailored specifically for cloud environments. Our platform offers a robust set of features to address the challenges mentioned earlier and safeguard your cloud workloads:
- Unified Threat Detection and Response: Gain comprehensive visibility into your cloud environment with continuous monitoring and threat detection across various workloads. CloudDefense.ai identifies suspicious activities, analyzes potential risks, and enables swift response measures.
- Vulnerability Management: Automate vulnerability scanning and prioritization, allowing you to patch critical vulnerabilities promptly and minimize the attack surface for malicious actors.
- Workload Compliance: Maintain compliance with relevant regulations and industry standards through automated policy enforcement and continuous monitoring. CloudDefense.ai simplifies compliance efforts and minimizes the risk of non-compliance penalties.
- Workload Hardening: Our platform helps you configure your cloud resources securely by identifying and remediating misconfigurations that could create security vulnerabilities.
- Next-Gen Threat Protection: Leverage advanced threat intelligence and machine learning algorithms to stay ahead of evolving cyber threats. CloudDefense.ai proactively detects and blocks sophisticated attacks, including zero-day exploits and malware.
Beyond these features, CloudDefense.ai prioritizes ease of use and integration:
- Intuitive Interface: Our user-friendly interface empowers security teams to monitor cloud workloads, investigate potential threats, and manage security controls efficiently.
- Cloud-Native Design: CloudDefense.ai seamlessly integrates with your existing cloud infrastructure, simplifying deployment and ongoing management.
- Scalability: Our platform scales to accommodate your growing cloud environment and evolving security needs.
Conclusion
Cloud workloads are already changing the way applications are built, deployed, and managed. While utilizing the full potential of the cloud unlocks numerous benefits, it also introduces unique security considerations. However, by understanding the core components of cloud workloads, the diverse types available, and the potential security challenges, organizations can make informed decisions about leveraging this technology. Implementing the best practices outlined in this article, such as IAM, encryption, and vulnerability management, lays a solid foundation for cloud security.
However, for comprehensive protection, consider adopting a Cloud Workload Protection Platform like CloudDefense.ai.CloudDefense.AI enables organizations of all sizes to secure their cloud workloads with confidence. Our platform offers a comprehensive suite of features, including unified threat detection and response, vulnerability management, workload compliance, and advanced threat protection.
Ready to experience the power of CloudDefense.ai and safeguard your cloud journey?
Book your live demo today! We help you unlock a proactive and comprehensive security approach while ensuring the protection of your critical assets and cultivating a secure digital environment.







