What is Cloud Security Monitoring?
Cloud Security Monitoring is about ensuring your cloud environment stays safe. It means keeping an eye on your systems, spotting threats, and quickly acting to protect what matters most.
-
- Detects threats instantly—data breaches, unauthorized access, anything out of the ordinary.
-
- Scans cloud configurations to find weaknesses and keep things locked down.
-
- Tracks user activity for signs of misuse or harmful behavior.
-
- Finds misconfigurations that could put your cloud at risk.
-
- Offers visibility into your security posture for quick decisions.
-
- Sends alerts when something goes wrong—so you can act fast.
In a world where speed and scale matter, cloud security monitoring is the only way to stay ahead. Keep things tight, stay proactive, and reduce the risk of a breach before it even starts.
| Read More: Curious to learn about cloud security monitoring? Read our article on what is CSPM to understand its crucial role in protecting your cloud environment. |
How Does Cloud Security Monitoring Work?
Cloud security monitoring is all about staying on top of your cloud environment, watching for threats, and making sure everything stays secure. It’s a continuous process that uses smart systems to keep an eye on everything, detect issues, and respond fast when something goes wrong. Here’s how it works:
1. Data Gathering:
The first step is collecting data. This includes everything from network traffic to application logs and system behavior. All this information is pulled from across your cloud infrastructure and brought into one place, giving a big-picture view of what’s happening at any given moment.
2. Threat Detection:
Once the data is collected, tools kick in to start analyzing it. They’re designed to spot anything unusual—like a spike in traffic or someone trying to access things they shouldn’t. Using machine learning, these tools get better over time at identifying what’s “normal” and what isn’t, so they can catch threats faster.
3. Real-Time Alerts:
When a threat or odd behavior is spotted, the system immediately sends out alerts. Whether it’s through dashboards, emails, or even messaging apps, security teams are notified instantly. This rapid response time is key to preventing issues from escalating.
4. Ongoing Compliance Checks:
Cloud security doesn’t stop at monitoring for threats—it also involves making sure your setup complies with industry standards and regulations. Automated checks ensure everything is up to code, and if anything falls out of line, it’s flagged for review.
5. Quick Remediation:
If something goes wrong, the system acts fast. Whether it’s automatically patching a vulnerability or isolating a compromised system, swift remediation is essential to keeping operations running smoothly without much downtime.
6. Visibility & Reporting:
Finally, all of this activity is tracked and reported. Security teams get a clear picture of what’s been happening, what’s improved, and what still needs attention. Regular reports help decision-makers stay informed and continuously refine their cloud security approach.
Why Cloud Security Monitoring Matters in 2025
Cloud security monitoring in 2025 isn’t about if you need it, but how fast you can deploy it and how well it works. The threats are real, and they’re not slowing down. Keeping a constant watch on your cloud infrastructure isn’t just smart; it’s essential.
Here’s why it’s more important than ever:
-
- Breach Incidents Are Up: In 2023, cloud breaches grew by 25%. That’s a massive jump. As organizations move more of their operations to the cloud, they also open themselves up to more attack surfaces. Monitoring is critical to catch these threats early before they become costly disasters.
-
- Data Breaches Are Expensive: The cost of a data breach reached $4.88 million on average in 2024. That’s a lot of money—money that businesses can’t afford to lose.
. The longer it takes to detect and contain a breach, the more it costs. Fast detection through continuous monitoring can prevent that.
- Data Breaches Are Expensive: The cost of a data breach reached $4.88 million on average in 2024. That’s a lot of money—money that businesses can’t afford to lose.
-
- Ransomware Is Growing: Ransomware attacks are a nightmare. They’re on the rise, and they’re expensive. Breaches tied to ransomware cost almost $1 million more when the attacker discloses the breach first. This is why speed matters. The faster you detect a breach, the less time the attacker has to wreak havoc.
-
- Regulations Are Tougher: Compliance isn’t optional anymore. With regulations like GDPR and CCPA, the stakes are high. Failing to meet these standards can cost you big time—both financially and reputationally. Ongoing cloud security monitoring ensures you’re always compliant, reducing the risk of penalties
Benefits of Cloud Security Monitoring
Cloud security monitoring is all about enhancing the security posture of an organization and helping the organization mitigate possible security threats. However, there are many other benefits this security solution has on offer, and they are:
Identifying Vulnerabilities
One of the primary benefits of cloud security monitoring is its capability to identify vulnerabilities through automation. Through automated monitoring, it can detect issues and provide alerts to security and also help the team to discover malicious patterns. It provides a deep insight into the cloud environment.
Compliance Maintenance
Cloud security monitoring is instrumental for organizations in maintaining compliance with all the key industry regulations like PCI DSS, GDPR, and HIPAA. Organizations are using this solution to cater to the requirement of constant monitoring and prevent legal issues.
Complete Customizability
Most cloud security monitoring solutions can seamlessly integrate with existing infrastructure, and that too, without hindering security capabilities. Since this solution fits seamlessly with most of the cloud solutions and local compliance, this makes it a safe option for every organization.
Quick Response to Threat
Another huge advantage of this monitoring solution is that it utilizes real-time scanning and assessment to provide quick response to threats. Once it detects any anomaly or malicious behavior, it quickly provides an alert to the team and enables the organization to mitigate quickly.
Safeguard All Vital Data
Implementing cloud security monitoring allows organizations to perform audits at regular intervals and get a complete view of the security posture, which ultimately helps protect all vital data. It helps the team to keep track of all the security systems and provide recommendations if any area needs to be improved.
Complete Automation
Automated assessment and monitoring of the cloud security posture of these solutions helps every organization as it saves them a lot of resources. Automation, not only allows the team to save time but also utilizes resources for other productive work.
Better Decision-Making Capabilities
Cloud security monitoring solutions utilize various tools to provide real-time assessment of data and allow organizations to gain deep insight into the data. This ultimately helps the top brass of the organization get accurate information and improve their decision-making capabilities.
Enhances Security Maturity
When an organization integrates cloud security monitoring into their existing infrastructure it helps them to enhance their security approach. It allows organizations to include an additional layer of security to the overall security system and get complete visibility into the whole cloud environment.
Challenges of Traditional Cloud Security Monitoring Approach
While cloud security monitoring is essential, it’s not without its challenges. As a security professional, you’re no stranger to the complexities that come with safeguarding a cloud environment. Let’s break down some of the biggest hurdles you might face—and why they matter to your job:
Visibility Across Complex Environments
Do you ever feel like you’re trying to monitor a cloud environment that’s constantly changing? Cloud infrastructures today are dynamic and multi-faceted, often spread across public, private, and hybrid clouds. With so many moving parts, it can be incredibly difficult to get a clear, unified view of everything happening in your environment. How do you ensure nothing slips through the cracks when your cloud landscape is constantly evolving?
Why this matters: Without clear visibility, security issues can go undetected for longer periods, leaving your organization exposed to threats. You need a monitoring system that can keep up with these rapid changes and give you a complete picture of what’s going on.
Volume of Data
Think about the sheer amount of data you’re dealing with daily—logs, network traffic, user behavior, application activity. Are you even able to make sense of all this in real time? With modern cloud systems generating vast amounts of data, trying to sift through it all can be overwhelming. How do you know what to focus on without drowning in noise?
Too much data can lead to alert fatigue, where you become desensitized to alarms. Worse, the critical information might get lost in the flood of alerts, leading to delayed responses when it matters most.
Evolving Threats
Every time you think you’ve got a handle on security, new threats emerge, right? Attackers are constantly evolving their tactics, finding new vulnerabilities, and exploiting them in creative ways. Can your monitoring solution keep up with this fast-paced environment and detect these novel threats?
Cloud environments are often targeted by advanced persistent threats (APTs) and zero-day exploits that traditional security tools may miss. Your monitoring system needs to be equipped to detect both known and unknown threats—and adapt quickly as new ones arise.
Integration with Existing Tools
How many different security tools are you currently using? A typical organization relies on various monitoring and protection systems, from firewalls to endpoint security, from intrusion detection to vulnerability scanners.
Integrating all these tools into a cohesive cloud security monitoring strategy can feel like trying to fit square pegs into round holes. Are your tools talking to each other, or are you juggling multiple dashboards and systems without a centralized view?
Poor integration means that important signals may get lost, and you’ll have to manually correlate data across platforms, which can slow down your response time and increase the chances of missing a critical event.
Alert Fatigue
You know the drill. Your team is getting bombarded with alerts all day, every day. Some are critical, but most are false alarms or low-priority issues. Over time, you and your team get desensitized, right? You start ignoring alerts, thinking they’re just more noise. This is alert fatigue, and it’s one of the biggest problems in cloud security.
If your team is overwhelmed by constant alerts, they’ll miss the important ones. A key threat could get buried under a pile of meaningless notifications. The more alerts you get, the harder it becomes to distinguish between “nothing to worry about” and “we’ve got a serious problem.”
Compliance Complexity
Do you ever wonder if your cloud environment is truly compliant with industry standards? Compliance regulations like PCI DSS, GDPR, and HIPAA are complex and constantly evolving. Keeping up with these requirements, while ensuring continuous monitoring, can feel like trying to hit a moving target. How do you ensure your cloud security monitoring system stays aligned with changing regulations?
Non-compliance can result in hefty fines and damage to your organization’s reputation. It’s essential to continuously audit and monitor your cloud setup to ensure you’re meeting regulatory requirements at all times.
Cost of Security
Let’s talk budget: How much are you willing to spend to secure your cloud environment? With so many threats emerging, it’s tempting to throw more resources at security tools. But is your organization willing to invest the right amount? Finding the balance between robust security and budget constraints is no easy task. Are you stretching your resources thin, or are you underinvesting in cloud security?
Over-spending on security tools can eat into other critical areas of the business, while under-spending leaves your environment vulnerable. It’s all about finding the right balance—an effective cloud security monitoring strategy that delivers value without breaking the bank.
Best Practices for Cloud Security Monitoring
When it comes to cloud security monitoring, the key isn’t just setting up a system and hoping for the best. You need a proactive, efficient, and adaptive strategy. Here’s how you can optimize your approach:
Align Security Monitoring with Organizational Goals
Cloud security can’t just be a checkbox you tick off. It needs to be built into everything you do from the start. Don’t just monitor for the sake of it—make sure the security objectives are tied to what you’re trying to achieve with your overall business. If you’re just going through the motions, you’re wasting time. Define your goals early, and refine as you go.
Pick the Right Cloud Provider
Picking a provider isn’t just about the price tag. It’s about security. Does the provider have the monitoring tools that make sense for your setup? Can they integrate with your existing systems seamlessly? You want real-time alerts, deep visibility, and the ability to respond quickly if things go south. Don’t settle for anything less.
Monitor from Day One
Security shouldn’t be an afterthought. Don’t wait until things are in full swing to start monitoring. Get your systems in place as soon as you start building. This way, you can identify issues before they become problems, and you’re not scrambling later on when it’s harder to fix things.
Automate Everything You Can
Cloud environments are complex. Trying to do everything manually will burn you out. Automation is your best friend here. Set up automated monitoring for things like data collection, anomaly detection, and alerting. Let the tools handle the repetitive stuff so your team can focus on more critical, higher-level tasks.
Manual Checks Matter
Automation is essential, but it’s not infallible. There’s always going to be something it misses, whether it’s a small vulnerability or a strange behavior that doesn’t match patterns. That’s why you still need manual checks. Do regular audits, penetration tests, and vulnerability assessments. Think of it like taking your car in for a tune-up—it’s good to check things over, even if the engine is running fine.
Integrate Alerts into Daily Workflows
It’s easy to ignore alerts if they aren’t set up the right way. Make sure your alerts are integrated directly into your team’s workflow. If your security team is working in Slack, make sure those alerts pop up there. If you’re using Jira, have the alerts funnel into your issue tracker. If the alert isn’t easy to spot and act on, it’s useless.
Enable Cross-Team Collaboration
Security isn’t a one-person job—it’s a collective effort. Share the intelligence gathered from cloud monitoring tools across departments, not just the security team. When you integrate your monitoring systems with SIEM and SOAR tools, you break down silos, improving incident response times and fostering a unified approach to security.
Keep an Eye on Compliance and Security Simultaneously
Regulations like GDPR or HIPAA are part of the game now. But don’t make the mistake of focusing on compliance and ignoring security—or vice versa. A good cloud monitoring solution will make sure you’re meeting compliance standards and securing your data at the same time. Both matter.
Constantly Revise Your Monitoring Strategy
You’re not building a “set it and forget it” system. Cloud security monitoring should evolve. It has to. New threats pop up all the time. Review your security strategy regularly, even when things seem calm. What worked last year might not work this year, so always refine and improve your systems.
Cloud Security Monitoring with CloudDefense.AI
CloudDefense.AI provides a practical, straightforward approach to cloud security monitoring, focusing on delivering what’s essential: real-time protection, clear visibility, and effective risk management. Here’s how we tackle these challenges.
1. Real-Time Threat Detection
Given the dynamic cloud spaces and the rate at which they evolve, threats don’t wait. CloudDefense.AI is built to identify threats the moment they appear. It continuously monitors your cloud environment for suspicious activities, providing alerts when something needs attention. The goal is to give you the data you need to respond immediately, preventing threats from becoming serious issues.
2. Comprehensive Visibility Across All Assets
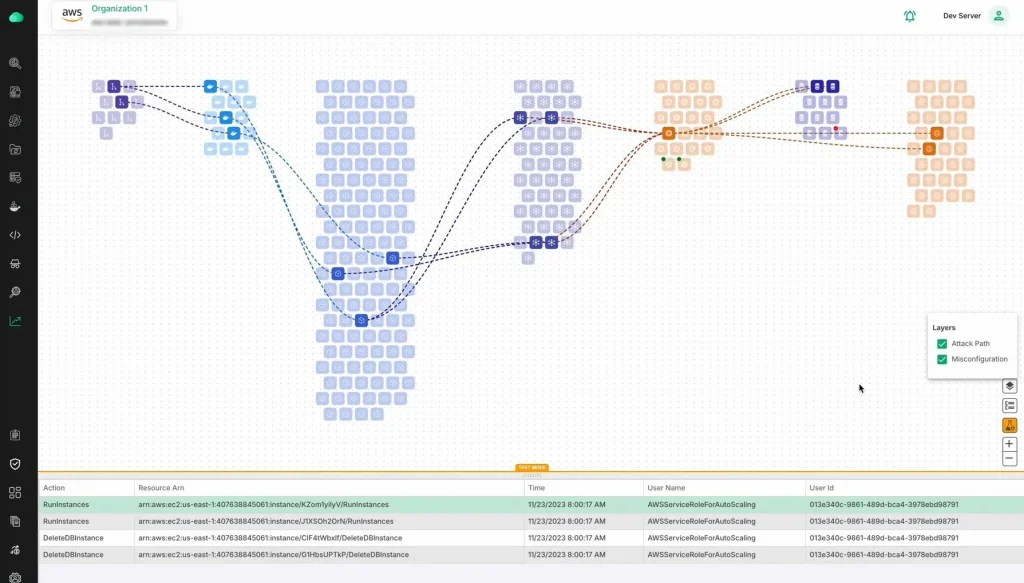
Visibility is critical. You need to know what’s happening across every part of your cloud infrastructure at all times. CloudDefense.AI gives you a full picture of your cloud environment, from servers to applications to microservices. With this level of visibility, you can make better decisions and quickly identify areas that need attention.
3. Risk Prioritization
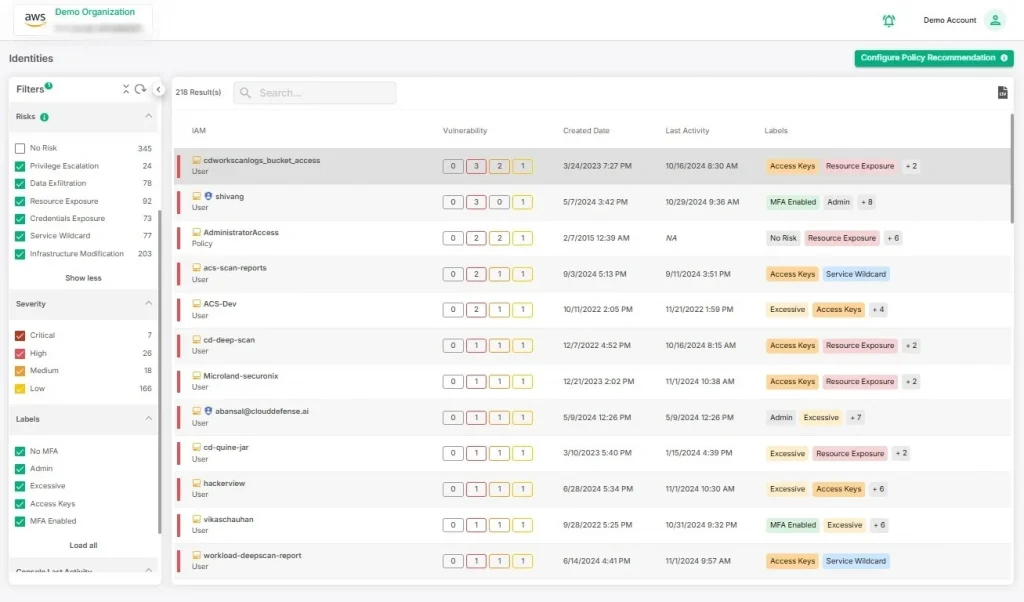
Not all risks are created equal, and wasting time on low-impact issues isn’t an option. With CloudDefense.AI, risks are ranked based on potential impact and severity. This allows you to focus your resources on what matters most. You’ll always know which vulnerabilities need immediate attention and which ones can wait, enabling smarter decision-making and faster remediation.
4. Attack Path Analysis
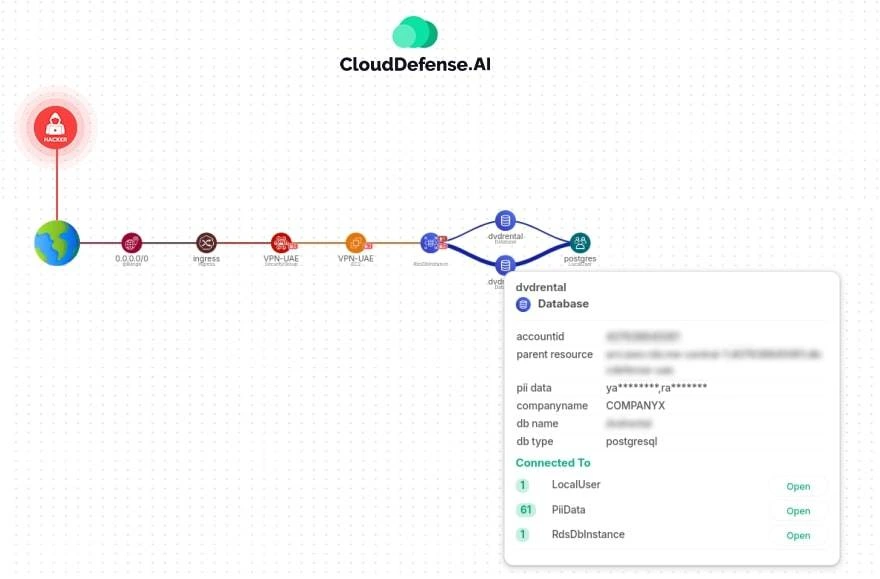
Understanding how an attacker might move through your system is critical to preventing breaches. Our attack path analysis maps out potential routes a hacker could take to exploit vulnerabilities. By identifying these pathways, you can strengthen weak spots and cut off access before it’s too late. It’s not just about defense; it’s about strategic foresight.
5. Hacker’s View™
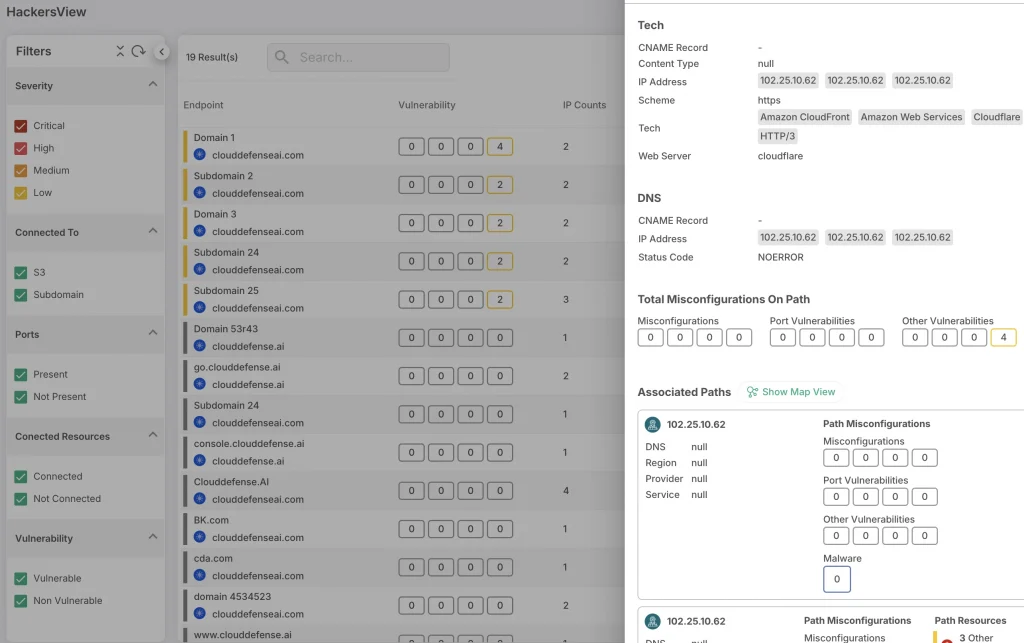
Hacker’s View™ is about understanding your cloud the way an attacker would. CloudDefense.AI looks at your system from this perspective, identifying vulnerabilities that could be exploited. By thinking like a hacker, we find weaknesses before anyone else does. This proactive approach gives you the advantage in securing your cloud infrastructure.
6. Graph-Based Security Insights
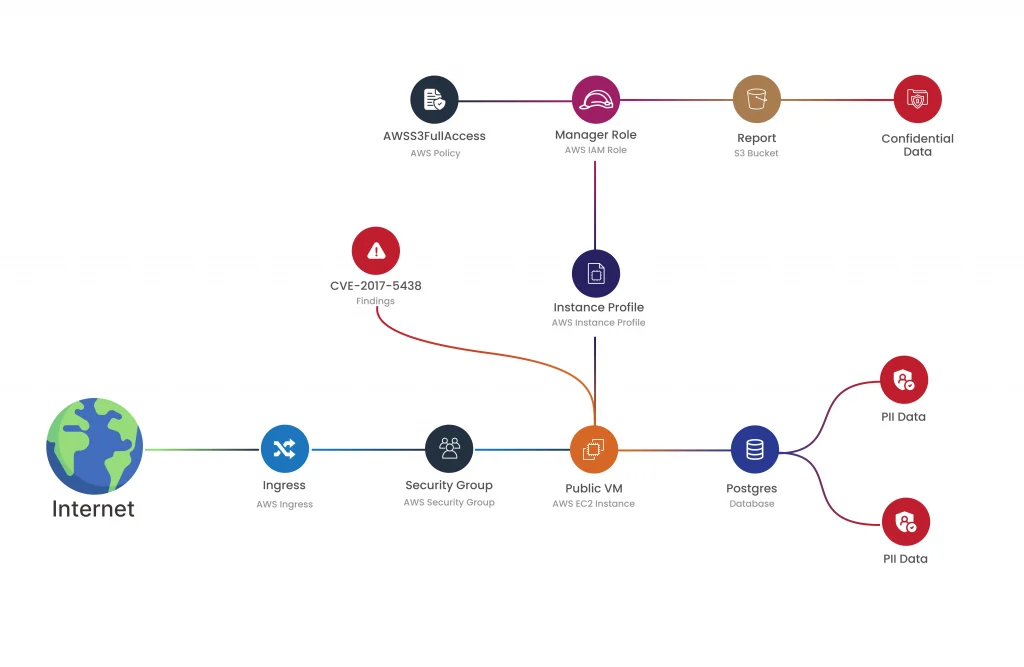
Complex cloud environments are difficult to secure without clear insights. CloudDefense.AI uses graph-based security analysis to give you a clear visual representation of your system. This makes it easier to understand the relationships between different parts of your infrastructure, helping you spot potential vulnerabilities quickly.
7. Streamlined Compliance Reporting
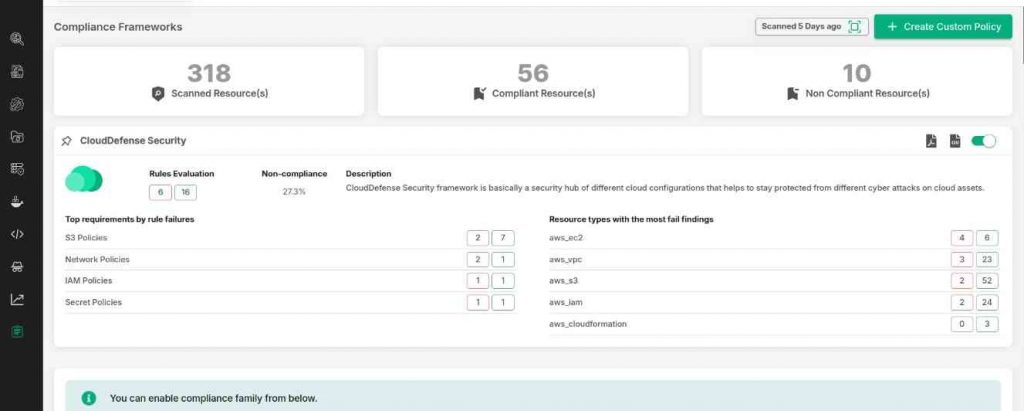
Meeting compliance requirements doesn’t have to be a hassle. CloudDefense.AI automates compliance reporting, so you can quickly generate reports that align with industry standards like SOC 2, GDPR, and HIPAA. This streamlines the process, saving you time and reducing the risk of non-compliance.
Conclusion
Cloud security monitoring is a boon for modern organizations operating in the cloud, and it has saved them from thousands of possible cyber threats. The primary key to effective cloud security monitoring is a proactive approach to cloud security and leveraging automation tools.
Cloud security monitoring platforms like CloudDefense.AI make things easy for most organizations by implementing automation in their workflow and improving their overall security posture. Want to experience it on your own? Schedule a live demo today and see how CloudDefense.AI can transform the way you secure your cloud infrastructure.







