What is Cloud Detection and Response (CDR)?
Cloud detection and response, or CDR, is a fast-paced threat detection and mitigation standard that has been growing in popularity among cloud-based companies. CDR can help to rapidly identify, assess, and mitigate any threat to your cloud-based environment in real-time.
CDR tools are solely developed to cater to cloud infrastructures and are capable of continuously monitoring and handling all cyber attacks in a cloud environment. Cloud Detection and Response has a lot of features that other threat detection tool standards, such as XDR, NDR, and EDR, possess. However, it comes with a range of other features that help it to counter any threat targeted at a cloud system.
It provides you with greater visibility on your cloud infrastructure and every other workload that is connected to it.
Importance of Cloud Detection and Response
Cloud Service Providers do not provide complete visibility to companies that are using their services, which creates challenges when it comes to ensuring security and tackling misconfigurations. An ever-changing range of cloud assets and inexpertise in cloud security lead to cloud-based companies facing major risks of getting attacked by cybercriminals.
While companies are scrambling to install cloud security tools to protect themselves, most of them need the capabilities to provide the deep visibility that is required for cloud environments.
There are existing D&R solutions that are catered towards serving the cloud. However, they fall short when it comes to solving cloud issues due to their complexity. A good example of this is Kubernetes and container clusters, which require a D&R solution that can work on par with its deployment and scalability parameters. Cloud environments, being dynamic, require cloud-native detection and response solutions that can handle critical parameters.
Key Components of Cloud Detection and Response Tools
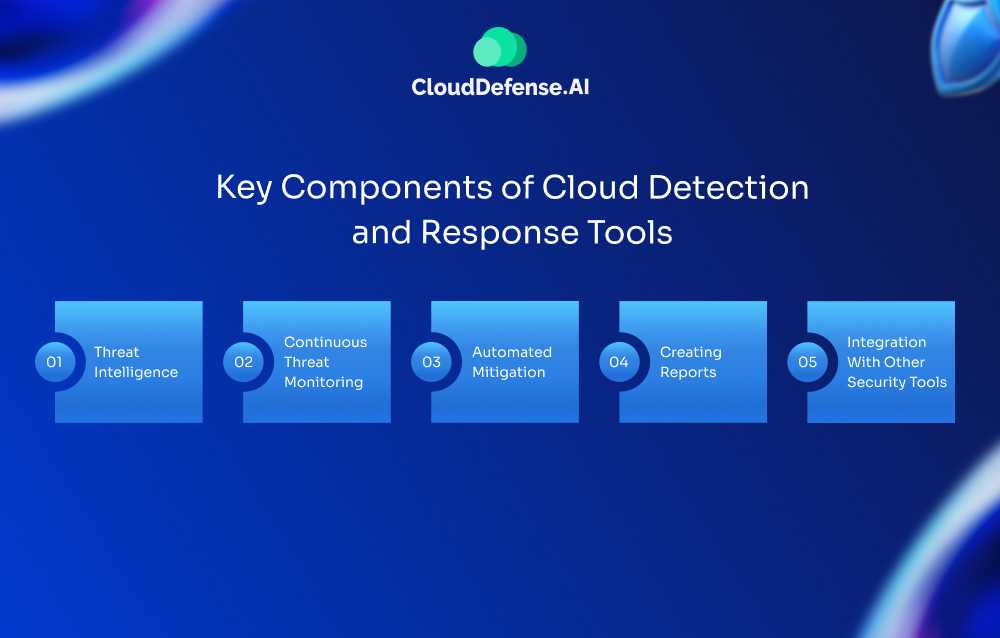
We have outlined some of the key components of Cloud detection and response tools that can help you strengthen your cloud system.
- Threat Intelligence: Threat intelligence helps an organization invest its resources and time in the most important threats that are identified and analyzed by the system.
- Continuous Threat Monitoring: CDR enables companies to detect threats continuously and assist you in mitigating them. Proving around-the-clock security for your cloud infrastructure.
- Automated Mitigation: CDR is capable of providing automated responses to any threat that is detected. Helping to isolate the affected components and mitigate them in time.
- Creating Reports: Keeping track of your security activities helps you to find out key areas that require more attention. CDR provides you with real-time reports that can be used to do the same.
- Integration With Other Security Tools: Lastly, CDR is easy to integrate with your existing cloud security tools. Hassle-free security management for you.
How does CDR work?
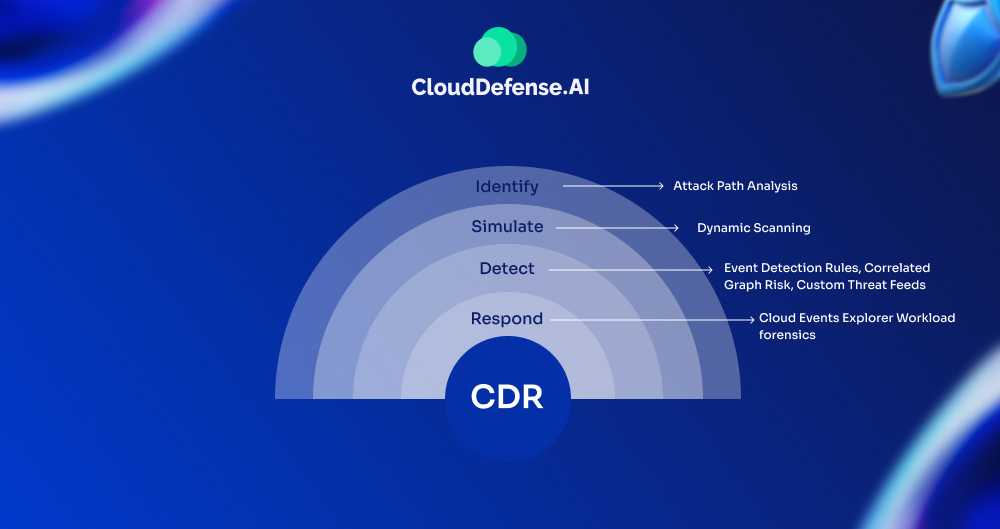
Cloud Detection and Response works on four principles: Identification, simulation, detection, and response. CDR helps in retrieving cloud configuration metadata from APIs and block storages through its agentless and agent-based approach.
To provide efficient security, a CDR tool should be able to:
Identify any exposure chains and movement paths that lead up to other cloud assets. CDRs have databases that are constantly updated with changes to the cloud environment. These help in identifying any exploitable assets and other cross-cloud threats.
Simulation of all cloud network exposures based on the database of all identified components. Providing enhanced risk severity and identification of granular-attack vectors.
Detection of all events on the cloud based on the data from the threats database. The database provides constant updates to the tool, allowing it to detect any malicious activity through its threat intelligence. Effective tools can provide real-time reports and continuous scans of the cloud environment.
Responding to all threats to the cloud using its automated mitigation processes or through security alerts. The response is generated based on the severity of the threats. Ideal CDRs should provide workload protection for containers, VMs, and serverless protection for Cloud-API, IAMs, etc.
Best practices for implementing Cloud Detection and Response
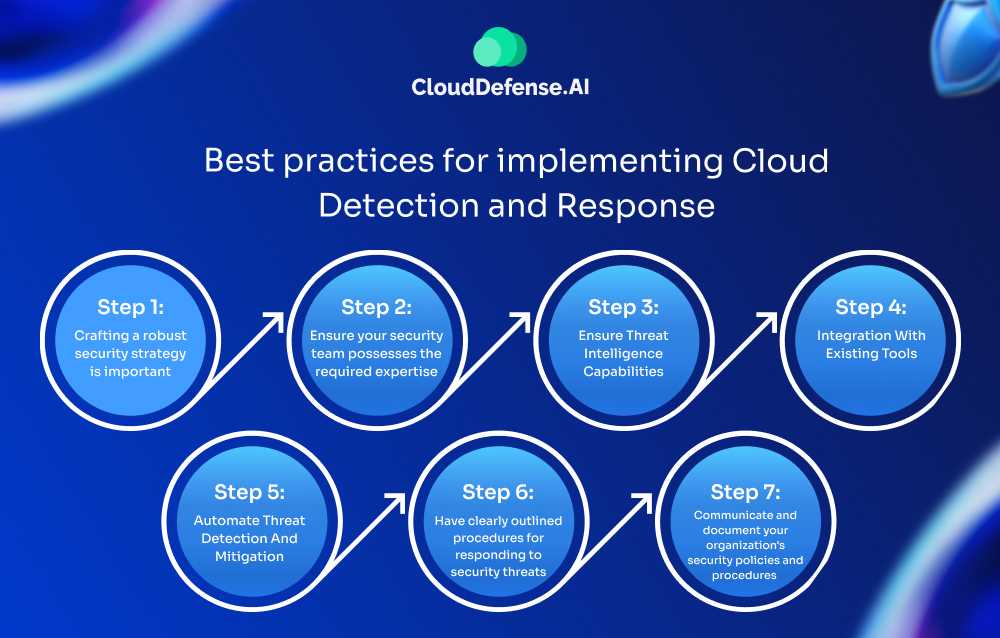
Successful implementation of cloud threat detection and response protocols relies on several key steps.
Step 1: Crafting a robust security strategy is important
This strategy should encompass an understanding of potential threats lurking in your cloud infrastructure, as well as the specific tools and methods employed for threat identification and mitigation. Regularly reassessing and upgrading this strategy is vital to guarantee its continued efficiency against evolving threats.
Step 2: Ensure your security team possesses the required expertise
This includes providing training on the specific tools and techniques in use, as well as keeping knowledge of the latest advancements in cloud security. By investing in your team’s knowledge and skill set, you strengthen their capacity to identify and counteract cloud-related threats effectively.
Step 3: Ensure Threat Intelligence Capabilities
To be effective, a Cloud Detection and Response tool must gather contextual security data about security events in your cloud environment. This data helps the tool understand threat severity and respond appropriately. Integrating real-time threat intelligence enables organizations to stay ahead of potential threats and secure their cloud environments. Check with cloud detection and response vendors to ensure this.
Step 4: Integration With Existing Tools
An effective Cloud Detection and Response tool should possess the capability to seamlessly integrate with pre-existing security solutions operating within your cloud system. Integration guarantees a sense of continuity, upholds a uniform security stance across your entire infrastructure, and reduces the likelihood of security vulnerabilities.
Step 5: Automate Threat Detection And Mitigation
Working swiftly is necessary when it comes to identifying and countering threats due to the time-sensitive nature of the matter. This urgency applies equally to CDR tools, as they have automation features in their operations. These features serve to expedite the process of identifying and reacting to potential threats before they have the chance to escalate and infect other vulnerable workloads.
Step 6: Have clearly outlined procedures for responding to security threats
Crafting an incident response plan describes the precise actions your organization will take in the event of a security breach. This plan designates roles and responsibilities within your security team and outlines protocols for managing and responding to incidents swiftly.
Step 7: Communicate and document your organization’s security policies and procedures
This involves employees, contractors, and third-party service providers with access to your cloud environments. Ensuring that all relevant stakeholders are well-informed and adhere to these policies and procedures is fundamental to upholding the security of your cloud environments.
FAQ
Here are some queries based on Cloud Detection and Response (CDR):
How does CDR differ from EDR, NDR, and XDR?
CDR includes a lot of elements that EDR, NDR, and XDR contain, but all its features are catered to cloud-based systems. The only difference they have is CDR’s capabilities of providing security for the cloud.
What are the types of CDR tools?
The different types of CDR tools include SIEM, IDPS systems, and a range of other security features, including antivirus, firewalls, and data encryption tools.
Should CDR be a part of a cloud-native application protection platform (CNAPP)?
CDR is a crucial part of CNAPPs, as they have automated threat-countering capabilities and incidence response through their threat intelligence abilities. Being focused on securing the cloud, every CNAPP should follow these standards.
Conclusion
Cloud computing is constantly evolving, and with it, the challenges of securing cloud environments are getting more complex as well. The lower visibility of the framework and the inclusion of cross-cloud components requires an effective approach similar to Cloud Detection and Response (CDR).
By embracing CDR and its key components, companies enable themselves not only to work more proactively but also to gain more visibility on their system. CDR empowers you to protect your sensitive assets and data from the hands of malicious actors. CloudDefense.AI provides you with a CNAPP that meticulously incorporates CDR standards to provide a holistic approach to cloud security. Test our capabilities by booking a free demo now.







