Definition — What is CI/CD Security?
CI/CD Security means integrating security checks and controls directly into the continuous integration and delivery pipelines. It’s about protecting every step of the software development process without slowing things down.
Here’s what it does:
- Keeps your code safe by preventing unauthorized changes during integration.
- Checks third-party tools and dependencies for vulnerabilities before they’re added.
- Runs automated security scans at every stage to catch issues immediately.
- Validates configurations to ensure infrastructure setups are correct and secure.
- Aligns your pipeline with compliance rules to avoid legal or operational risks.
The goal is simple: secure the pipeline so teams can build and release software faster, without leaving any gaps for threats to slip through.
| Did you know? Gartner predicts that by 2025, 45% of organizations will fall victim to software supply chain attacks, highlighting the critical need for robust CI/CD security measures. |
Why is CI/CD Security Critical?
Let’s imagine a company developing a new e-commerce platform. Their CI/CD pipeline automates every step: pulling code from repositories, building it, testing it, and then deploying it to staging and production.
Now, picture this: an attacker finds a vulnerability in a third-party library that’s unknowingly integrated into the code. Without strong security checks in place, this vulnerability slips through unnoticed. As the code moves through the pipeline, the flaw gets embedded in the application. Once the code hits production, the attacker exploits the vulnerability, gaining access to sensitive customer data like credit card information.
This exact scenario shows how important security is in CI/CD processes. If companies don’t pay attention to security inside their pipelines, they can face big issues such as:
- Rising Cyber Threats: Attackers increasingly target software supply chains to exploit vulnerabilities, which can compromise entire systems.
- Speed vs. Security: The faster development moves, the more crucial it is for security to keep up. Otherwise, every new update or deployment risks introducing vulnerabilities.
- Cost of Breaches: A single breach can cause financial and reputational damage. Early detection and prevention cost far less than dealing with the aftermath.
- Regulatory Compliance: Industries have strict data protection and privacy rules. Without secure pipelines, meeting compliance standards is nearly impossible.
When companies implement strong CI/CD security practices, they can proactively identify and address vulnerabilities early in the development process, preventing them from reaching production and mitigating the potential consequences outlined above.
What are common CI/CD security risks?

Building on the previous example, where a vulnerability in a third-party library compromised sensitive customer data, let’s look at some common security risks that can occur in CI/CD pipelines. These risks are often overlooked but can lead to significant issues if not addressed.
- Unsecured Third-Party Dependencies: Many pipelines integrate third-party libraries and tools. Without proper vetting, vulnerabilities in these dependencies can be introduced into your codebase, just like in the earlier example.
- Inadequate Secrets Management: Hard-coding credentials or API keys directly into the code or configuration files is a serious risk. If these secrets are exposed, attackers can gain unauthorized access to systems and data.
- Weak Access Control: If the CI/CD pipeline doesn’t enforce strict access controls, unauthorized users or attackers can potentially alter code or configuration, introducing malicious changes or vulnerabilities.
- Misconfigured Environments: Incorrectly configured staging or production environments can lead to security holes. This could range from exposing sensitive data to giving too much access to non-essential users.
- Lack of Automated Security Testing: Without automated security checks, like vulnerability scans and code reviews, you risk deploying insecure code. Manually reviewing everything is time-consuming and often not thorough enough.
- Weak code review practices: Inadequate code review processes can miss security vulnerabilities before they are integrated into the pipeline, allowing them to persist through production.
- Supply chain attacks: Malicious actors can compromise third-party libraries or tools used within the pipeline to inject vulnerabilities into the software being built.
- Lack of visibility and monitoring: The inability to monitor the pipeline for suspicious activity makes it difficult to detect and respond to security incidents on time.
- Code Injection: This occurs when an attacker inserts malicious code into an application, often via input fields, scripts, or unvalidated data. Without proper validation and sanitation, this code can be executed during the CI/CD process, leading to unauthorized actions or access.
Each of these risks can easily slip through the cracks in a fast-moving development cycle. However, addressing them early in the CI/CD pipeline can drastically reduce the chances of a major security incident.
| Want to dive deeper into CI vs CD? We have curated an exclusive article about Continuous Integration vs Continuous Delivery. Read more to discover how these practices differ and how they work together to speed up your development process. |
Why is CI/CD the backbone of DevSecOps?
DevSecOps is about embedding security into every stage of the software development lifecycle. It’s about breaking down silos and creating a culture of collaboration, where security is everyone’s responsibility.
CI/CD is crucial here because it automates the integration, testing, and deployment of code, making it easier to integrate security at every step.
Here’s how CI/CD drives DevSecOps:
Shifting Left Security: In DevSecOps, security isn’t something you check at the end—it’s part of the process from the start. CI/CD helps achieve this by adding security checks early in the pipeline. Identifying vulnerabilities early saves time, reduces costs, and prevents issues from reaching production.
Faster Feedback Loops: CI/CD allows developers to get real-time feedback on the security of their code. This lets them fix issues quickly and keep improving, which is a core principle of DevSecOps.
Streamlined Deployment: By automating deployment, CI/CD reduces the chances of human error and ensures consistency. Security teams can then focus on defining policies rather than checking each deployment manually.
Collaboration and Shared Ownership: The automated nature of CI/CD promotes collaboration between development, security, and operations teams. Security checks become an integral part of development, reinforcing the DevSecOps mindset of shared responsibility for security.
Faster Time to Market: CI/CD speeds up development and deployment, allowing companies to deliver updates quickly. In today’s competitive environment, speed is crucial, but it should never compromise security. When integrated with DevSecOps, CI/CD ensures that security is built in without slowing things down.
Securing Your CI/CD Pipeline: A Step-by-Step Guide
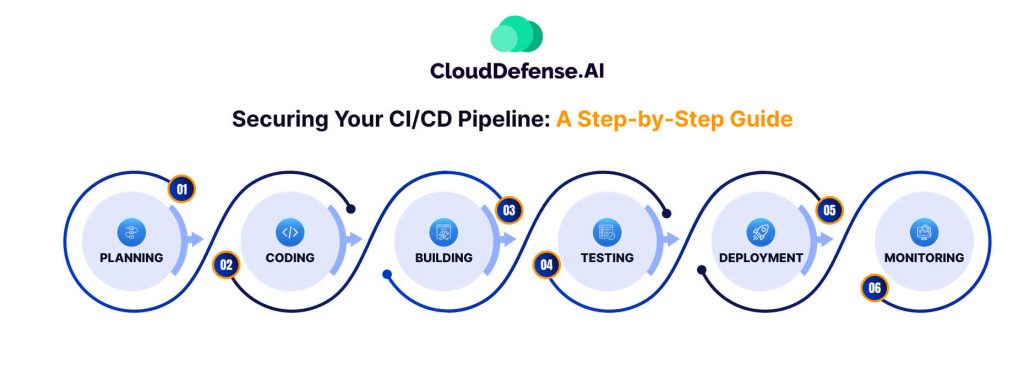
Building a secure CI/CD pipeline isn’t a one-size-fits-all process. It’s about ensuring security at every stage, from planning to deployment. Here’s a practical guide to making sure your pipeline doesn’t become a weak link in your development process.
1. Planning Phase:
- Threat Modeling: Begin by thinking ahead. Identify potential risks early in the planning process. This will help you take action before vulnerabilities become major issues.
2. Coding Phase:
- Secure Coding Practices: Set a clear expectation for secure coding. Have your team follow standards that avoid common mistakes and build in code reviews to catch issues early.
- Static Code Scanning (SAST): Add automated tools that check for vulnerabilities as your code is written. These tools highlight problems early so they can be fixed before they snowball.
3. Building Phase:
- Software Composition Analysis (SCA): You rely on third-party libraries—so make sure you understand their security risks. Use SCA tools to scan for known vulnerabilities and address them before they’re part of your code.
4. Testing Phase:
- Unit Testing and Integration Testing: Run tests at every level. Catch both functional issues and potential security flaws early in the cycle.
- Dynamic Application Security Testing (DAST): Integrate DAST tools to check for vulnerabilities while the app is running. This step finds issues that static analysis tools might miss.
5. Deployment Phase:
- Least Privilege Access: Make sure only the necessary users and systems have access to the pipeline. The less exposure you create, the fewer opportunities for exploitation.
- Secret Management: Don’t hardcode sensitive data into your pipeline. Use tools designed to securely store and handle credentials, API keys, and other secrets.
6. Monitoring Phase:
- Security Monitoring: Keep a constant watch on your pipeline. Set up tools to monitor for unusual activity and provide alerts so you can respond quickly.
Further Considerations:
- Regularly patch and update your CI/CD tools and infrastructure.
- Train your team on security best practices to ensure everyone is on the same page.
- Automate security checks wherever possible to keep things consistent.
- Create a feedback loop to constantly identify and address new security risks.
By putting these steps in place, your CI/CD pipeline won’t just be more secure—it’ll also be more efficient. Security should be built into the process, not bolted on later. Keep it simple, integrate it early, and keep it consistent.
How CloudDefense.ai Helps Protect Your CI/CD Pipelines?
Given the quick-paced development environment, security can’t be an afterthought—it needs to be integrated throughout the CI/CD pipeline. CloudDefense.ai offers a next-gen application security platform designed to secure every stage of your pipeline, from development through to deployment and cloud operations.
With our comprehensive, scalable approach, CloudDefense.ai helps businesses like yours proactively manage security and stay ahead of potential threats.
Here’s how CloudDefense.ai keeps your CI/CD pipeline secure:
Static Application Security Testing (SAST)
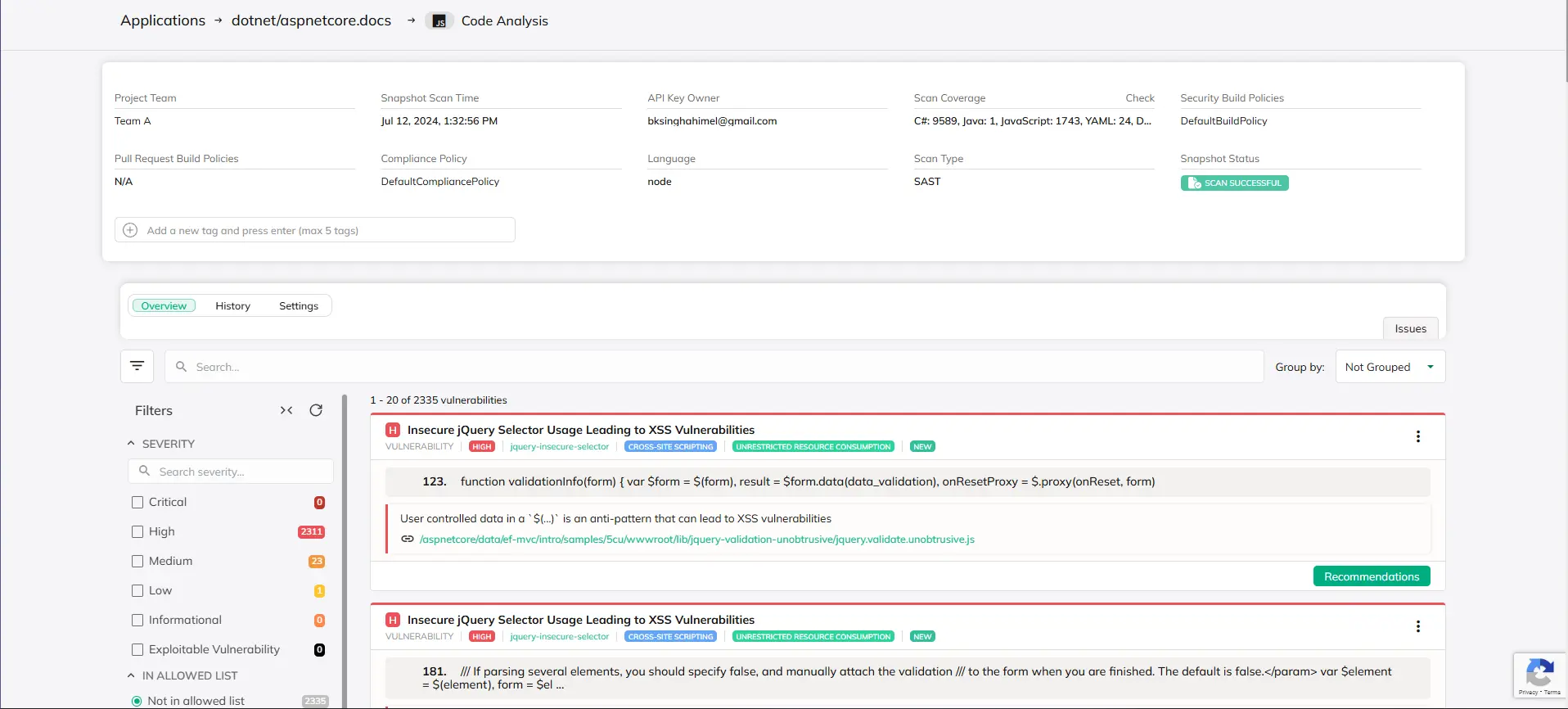
Catch vulnerabilities early with automated code scanning tools that analyze your source code before it ever reaches the build phase. With SAST, you can spot weaknesses in your code—like insecure libraries or poor coding practices—before they turn into real threats. By addressing these issues early, you save time, reduce risks, and streamline development.
Dynamic Application Security Testing (DAST)
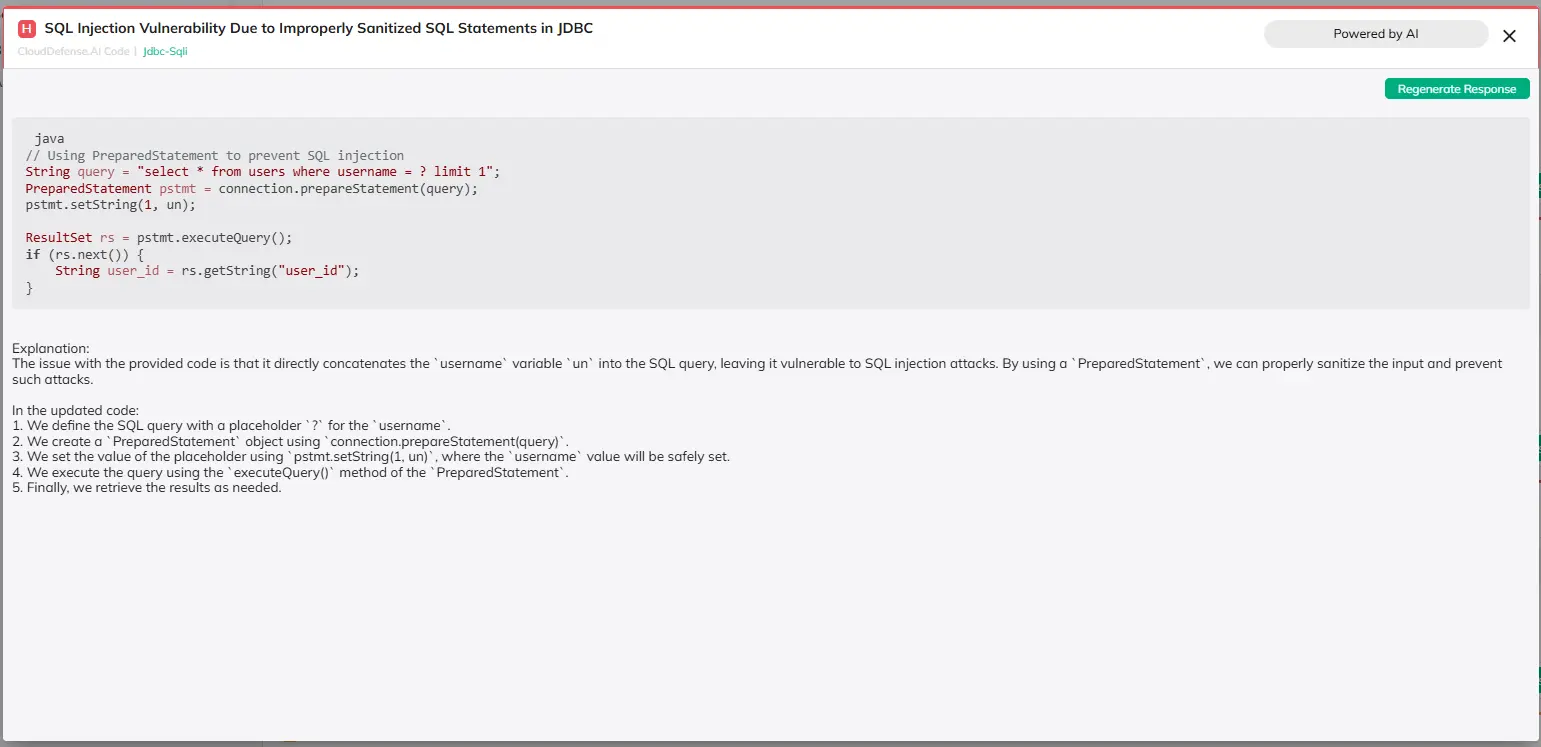
Even after code has been built, it’s crucial to scan your running application for vulnerabilities that may not have been detected in earlier stages. CloudDefense.ai’s DAST tools test applications in real time, simulating real-world attacks to uncover vulnerabilities in the live environment. With this dynamic approach, you can address issues before they impact production, ensuring your applications stay secure and operational.
Software Composition Analysis (SCA)
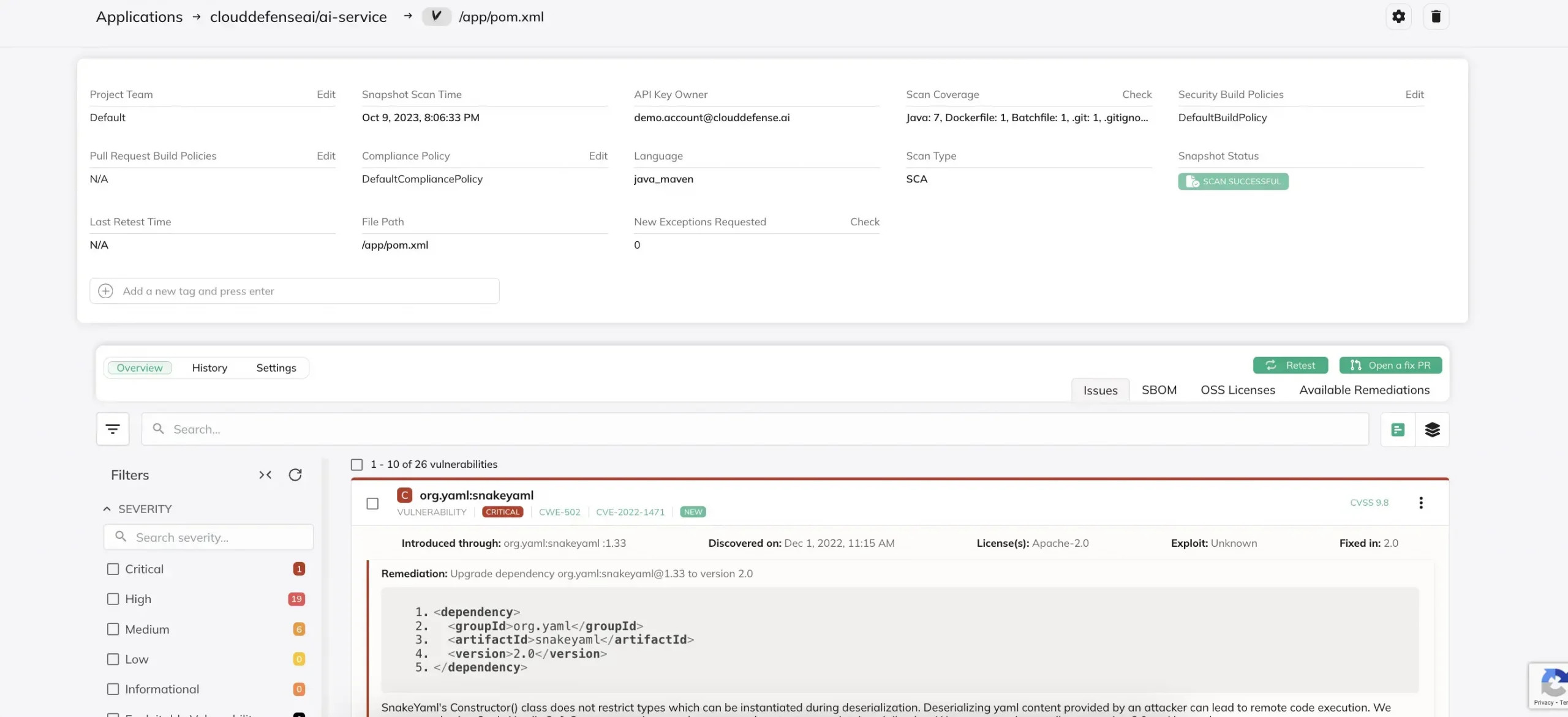
Third-party libraries and open-source components are vital to modern software development, but they can introduce security risks. CloudDefense.ai’s SCA tools identify known vulnerabilities in the third-party dependencies used in your applications, allowing you to update or replace insecure components before they make it to production. This proactive step reduces the risk of breaches from outdated or insecure libraries.
API Scanning
APIs are a frequent attack vector, and their security is often overlooked. CloudDefense.ai automatically scans your APIs for security weaknesses, such as improper authentication, data leaks, and other vulnerabilities. By regularly checking your APIs, we help ensure they remain secure, providing a safe bridge for communication between your applications and external services.
Container Vulnerability Management
As containerized applications become more common, security in these environments is critical. CloudDefense.ai scans your containers for vulnerabilities, helping you identify and fix security flaws before deploying to production. We make sure your containers are hardened and secure, so you can rely on them for production-level deployments.
Secret Scanning
Exposing sensitive data, such as API keys, passwords, or private keys, can be disastrous. CloudDefense.ai’s secret scanning capabilities identify hardcoded secrets in your codebase, configuration files, or deployment scripts. This ensures that sensitive information never leaks into your pipeline, reducing the risk of unauthorized access or data breaches.
Infrastructure as Code (IaC) Scanning
Misconfigurations in your infrastructure can be just as dangerous as vulnerabilities in your application. CloudDefense.ai scans your Infrastructure as Code (IaC) files for security flaws or misconfigurations that could lead to security vulnerabilities in your cloud infrastructure. By addressing these issues before deployment, you reduce the chance of exposing critical infrastructure to attacks.
A Complete CNAPP that secures both your cloud and apps
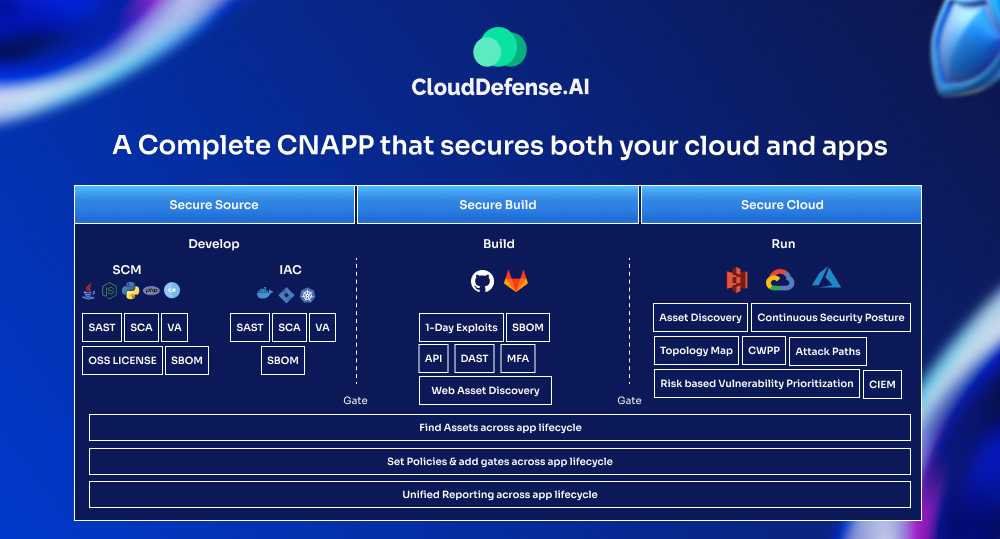
CloudDefense.AI doesn’t stop at application security—we also offer comprehensive cloud security through our next-gen Cloud-Native Application Protection Platform (CNAPP). Our solution goes beyond just securing your code and applications; it protects your entire cloud infrastructure from the ground up.
From securing your cloud environments to monitoring your deployment pipelines, CloudDefense.ai provides an all-encompassing solution to safeguard your apps and cloud infrastructure, helping you reduce risks, maintain compliance, and accelerate secure deployments. Ready to take your security to the next level? Book a free demo with us today and discover how CloudDefense.ai can help protect your CI/CD pipeline and cloud infrastructure.







