What is the ARP?
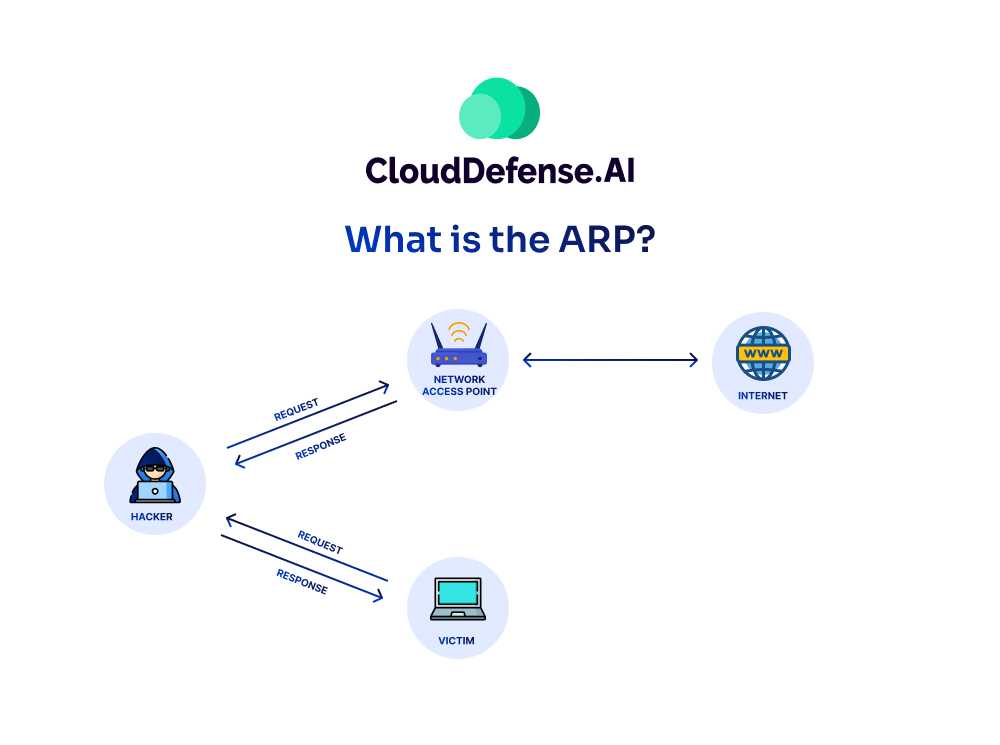
ARP, or Address Resolution Protocol, bridges the gap between IP and MAC addresses in a local network.
Operating at the OSI model‘s Data Link layer, ARP translates 32-bit IP addresses to 48-bit MAC addresses and vice versa, enabling devices to communicate effectively. It simplifies data transmission by resolving IP addresses to corresponding hardware addresses, which is essential for network functionality and efficient data routing.
What is ARP Spoofing (ARP Poisoning)?
ARP Spoofing, also known as ARP Poisoning, is a cyber attack tactic executed within a LAN. By sending malicious ARP packets to the LAN’s default gateway, attackers manipulate the IP to the MAC address table, altering the mappings.
Exploiting the inherent vulnerabilities in the ARP protocol, attackers associate their MAC address with legitimate IP addresses, intercepting and redirecting network traffic meant for other devices.
This enables unauthorized access to sensitive information and poses serious security threats within the network. ARP spoofing attacks exploit the trust-based nature of ARP, undermining network integrity and confidentiality.
Purpose of an ARP Spoof Attack
The purpose of ARP spoofing can include various malicious intents, including spying, man-in-the-middle attacks, and other cyber assaults such as DoS attacks. In spying, attackers intercept and read communications between hosts without modification, while in man-in-the-middle attacks, they alter the transmitted information before forwarding it.
These actions may be part of broader cyberattacks involving lateral movement. DoS attacks are executed to disrupt communications between hosts, often accompanied by the transmission of malicious files. ARP spoofing has been utilized by hackers since the 1980s for planned or opportunistic attacks due to its ease of execution and potential impact. However, it can also serve legitimate purposes, such as network debugging and ethical hacking for security testing.
Effects of ARP Spoofing
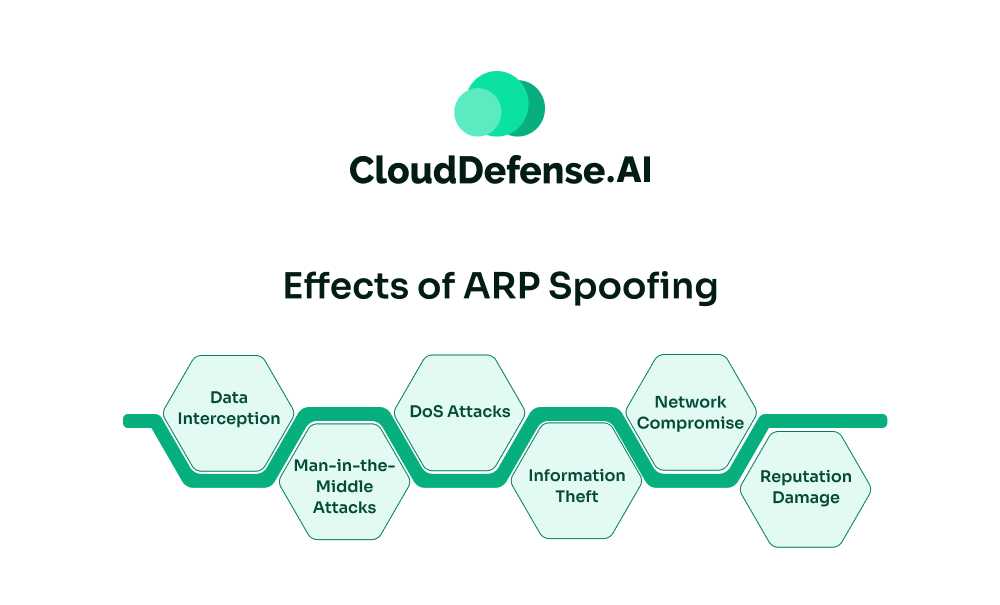
ARP spoofing can severely impact IT infrastructure, leading to security breaches, data theft, and operational disruptions. Below are the key effects of ARP spoofing, explained in greater depth:
Data Interception
Attackers use ARP spoofing to intercept and monitor network traffic, allowing them to capture unencrypted sensitive information such as login credentials, financial data, and confidential communications. This is especially dangerous in environments without strong encryption protocols, making espionage and insider threats a significant concern.
Man-in-the-Middle (MITM) Attacks
An MITM attack occurs when an attacker secretly intercepts and alters communications between two parties. With ARP spoofing, hackers can:
- Modify data packets to alter messages, inject malicious commands, or manipulate transactions.
- Redirect users to fraudulent websites that mimic legitimate platforms, leading to credential theft or malware infections.
- Hijack ongoing sessions, allowing unauthorized access to critical systems, email accounts, or financial platforms.
Denial-of-Service (DoS) Attacks
Attackers can use ARP spoofing to overwhelm or disrupt network operations by:
- Redirecting traffic to non-existent addresses, causing delays and failures in communication.
- Flooding networks with spoofed ARP replies exhaust switch or router resources, leading to network slowdowns or outages.
- Disconnecting users from critical services leads to business downtime and lost productivity.
Information Theft
Sensitive corporate or personal data is at high risk due to ARP spoofing. Attackers can:
- Extract login credentials from intercepted traffic, compromising user accounts.
- Steal financial details, leading to fraud, unauthorized transactions, or identity theft.
- Capturing confidential corporate data, including intellectual property, trade secrets, or strategic plans, can result in financial and competitive losses.
Network Compromise and Lateral Movement
Once an attacker infiltrates the network, they can escalate privileges and move laterally across systems. This can lead to:
- Unauthorized access to internal applications, databases, and servers.
- Install malware, backdoors, or keyloggers to maintain persistent access.
- Launching additional attacks, such as ransomware, leveraging the compromised network for broader exploitation.
Reputation and Trust Damage
A successful ARP spoofing attack can erode customer, partner, and stakeholder trust by exposing security vulnerabilities. Consequences include:
- Public relations crises due to data leaks or security breaches.
- Regulatory fines and legal consequences for failing to secure sensitive data.
- Loss of business opportunities due to damaged credibility in the market.
ARP spoofing is more than just a network nuisance—it can be the entry point for severe cyber threats. Implementing strong network security measures, such as ARP inspection, encryption, VLAN segmentation, and intrusion detection systems, is crucial for mitigating its risks and protecting IT infrastructure.
Types of ARP Spoofing
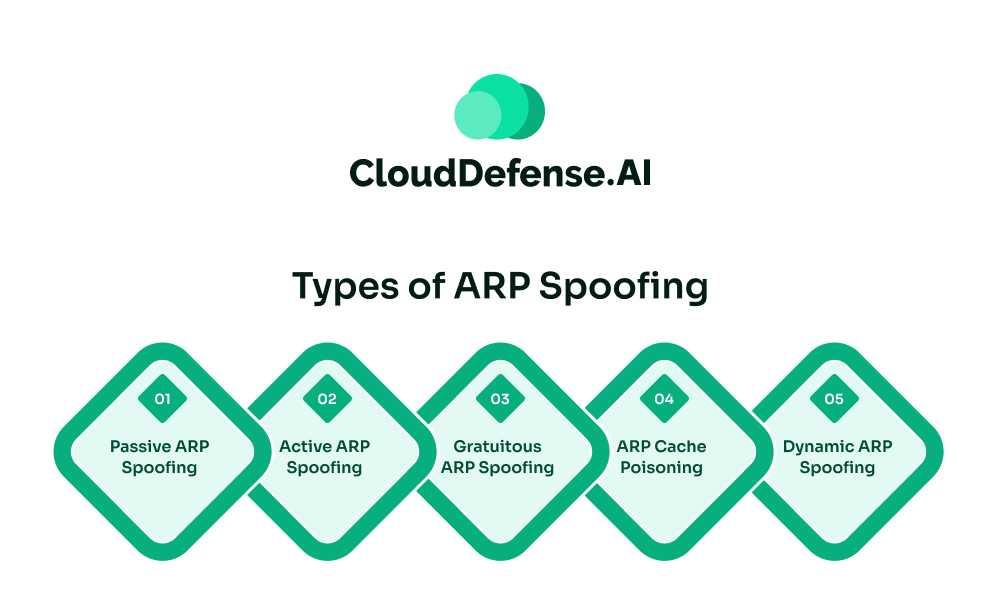
ARP Spoofing comes in various types, and a few of them are mentioned in the table below.
| Type of ARP Spoofing | Description |
| Passive ARP Spoofing | The attacker intercepts and monitors communication between two hosts without modifying data packets. |
| Active ARP Spoofing | Attackers modify or inject ARP packets into the network, impersonating legitimate hosts to redirect or manipulate traffic. |
| Gratuitous ARP Spoofing | Attackers send gratuitous ARP replies with spoofed MAC addresses to update ARP cache tables, causing network disruption or interception. |
| ARP Cache Poisoning | Also known as ARP Poisoning, attackers manipulate ARP cache tables to link their MAC address with legitimate IPs, enabling interception or redirection. |
| Dynamic ARP Spoofing | Attackers dynamically change ARP cache entries to impersonate legitimate hosts, maintaining persistence and evading detection. |
How to Detect an ARP Cache Poisoning Attack?
Detecting an ARP Cache Poisoning Attack involves several key steps. Firstly, administrators can inspect the ARP table of a device by accessing the command line and using the `arp -a` command. You should get something that looks like this:
Any instances where multiple IP addresses are mapped to the same MAC address signal a potential ARP spoofing incident. This indicates an attempt by an attacker to manipulate the ARP cache. Additionally, network traffic analysis tools can be employed to monitor and scrutinize network packets for irregularities, such as unexpected ARP requests or gratuitous ARP replies.
You should see something like this in the table if you are being spoofed:
Continuous monitoring for duplicate MAC addresses associated with different IP addresses can also serve as a warning sign of ARP spoofing activity.
ARP Spoofing Prevention
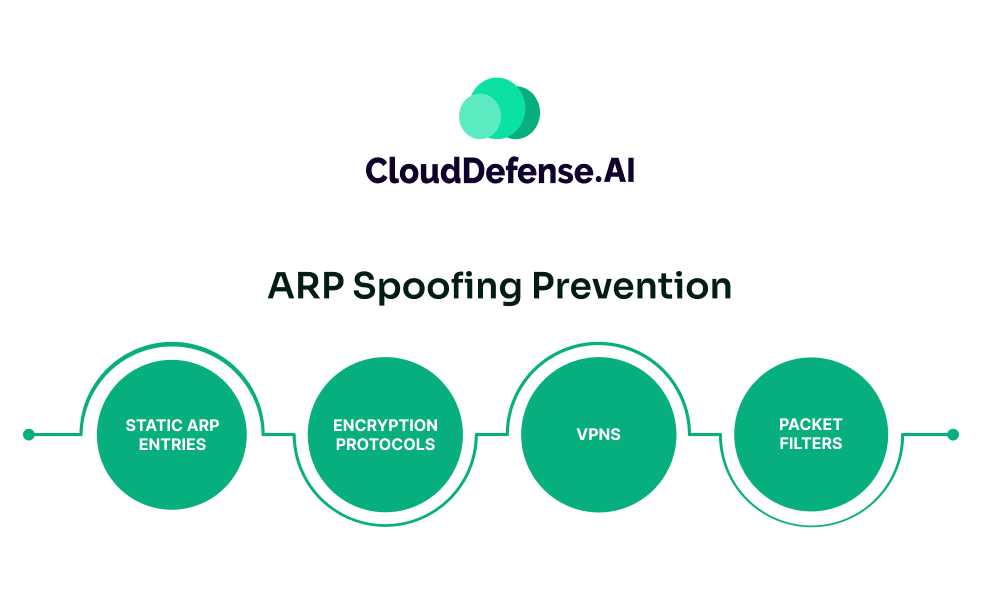
Once you have detected an ARP spoofing attack on your system, it is essential to take prompt action to prevent further damage. Consider following the prevention methods mentioned below.
Static ARP Entries
This method involves manually configuring ARP entries for each device on the network mapping MAC addresses to IP addresses. While effective in smaller networks, it requires significant administrative overhead and may only provide limited protection against more straightforward ARP spoofing attacks.
Encryption Protocols
Encryption protocols such as HTTPS and SSH add a layer of security by encrypting network traffic, making it difficult for attackers to intercept and manipulate data. However, they do not protect against all types of ARP spoofing attacks, leaving data transmitted outside of encrypted protocols vulnerable to interception.
VPNs
VPNs offer individual users protection against ARP spoofing by encrypting all data between the client and the VPN server. While effective for individual users, implementing VPNs across larger organizations can be complex and may impact network performance due to the overhead of encrypting and decrypting data.
Packet Filters
Packet filters analyze each packet sent across the network, blocking suspicious packets and those with spoofed IP addresses. This method helps prevent ARP spoofing attacks by identifying and rejecting malicious traffic, including packets that claim to originate from internal networks but actually come from external sources.
To Sum Up
Protecting networks against ARP spoofing requires a calculated approach combining both prevention and detection techniques. While prevention methods like static ARP entries and encryption offer initial defenses, their efficiency often faces questions. Hence, complementing these measures with active threat detection tools such as the ones offered by CloudDefense.AI ensures timely identification of ARP poisoning incidents.
Moreover, the transition to IPv6, where the Neighbor Discovery Protocol replaces ARP, promises enhanced security against such attacks in the future. As IPv6 adoption rates continue to rise globally, this will, in turn, cause ARP attacks to decline, benefiting from NDP’s advanced features and addressing ARP’s limitations in IPv6 environments.







