What is an Attack Surface?
Before we step deeper into Attack Surface Management, let’s get one thing straight – what exactly do we mean by an “attack surface”? In cybersecurity lingo, your attack surface refers to the total sum of all the entry points, vulnerabilities, and exposed areas that cyber attackers could potentially exploit to gain unauthorized access or cause harm to your systems, applications, or networks.
To put it simply, think of it like this:
Every piece of hardware, software, and online service you use is essentially a door or window into your digital world. The more “things” you have connected to the internet or running on your devices, the more potential entry points you’ve created for bad actors to try and break in.
These entry points can be technical or social. For example:
- Technical vulnerabilities might include unpatched software or misconfigured systems that leave you open to attacks.
- Social vulnerabilities can come from employees who might be susceptible to phishing attacks or other deceptive tactics.
Understanding your attack surface in this way sets the stage for why managing it is so crucial.
| Read More: Looking to deepen your understanding of attack surface analysis? Explore our “What is Attack Path Analysis” article to uncover how it can strengthen your security posture. |
What is Attack Surface Management?
Attack Surface Management (ASM) is all about the continuous monitoring and analysis of an organization’s vulnerabilities and potential entry points for cyberattacks. The goal is to identify these weak spots and take proactive steps to secure them before they can be exploited by malicious actors.
With a holistic ASM in hand, organizations can:
- Identify vulnerabilities and potential attack vectors within your digital landscape.
- Monitor your systems continuously to stay ahead of emerging threats.
- Implement remediation measures to address identified weaknesses.
What makes ASM really stand out is its unique perspective: it encourages organizations to think like attackers. Instead of just focusing on their own defenses, companies learn to view their systems through the eyes of someone trying to break in.
This means using the same techniques, tools, and technologies that cybercriminals use to find and exploit vulnerabilities. By adopting this mindset and approach, organizations can improve their security posture significantly.
Why Is Attack Surface Management Important?
What if I told you that every single app, system, device, and online service you use is a potential entry point for cybercriminals to wreak havoc on your digital ecosystem? Sounds scary, right? Well, that’s the harsh reality we’re facing in today’s hyperconnected world. The more technology we adopt, the more surfaces we expose to potential attacks.
Also, the cybersecurity game these days is an all-out battle to the finish. On one side, you have companies like yours adopting the latest technology to drive innovation and productivity. But, on the other side, every new app, connected gadget, and online service you roll out essentially adds another potential entry point for bad actors to sneak into your systems.
So, how do you stay ahead of these threats and protect your digital ecosystem is?
- Acknowledge that every connected device or application adds to your attack surface, increasing your risk.
- Stay aware that cyber threats are always evolving, so it’s crucial to keep your defenses up.
- Adopt proactive measures like ASM to spot and fix vulnerabilities before they can be exploited.
Therefore, by taking ASM seriously, you’re not just responding to threats; you’re also working to strengthen your defenses.
| Did you know? Global data breaches surged by 72% in 2023 alone, representing a significant jump from 2022. This rise clearly indicates that our attack surfaces are becoming increasingly vulnerable each day. |
Types of Attack Surfaces
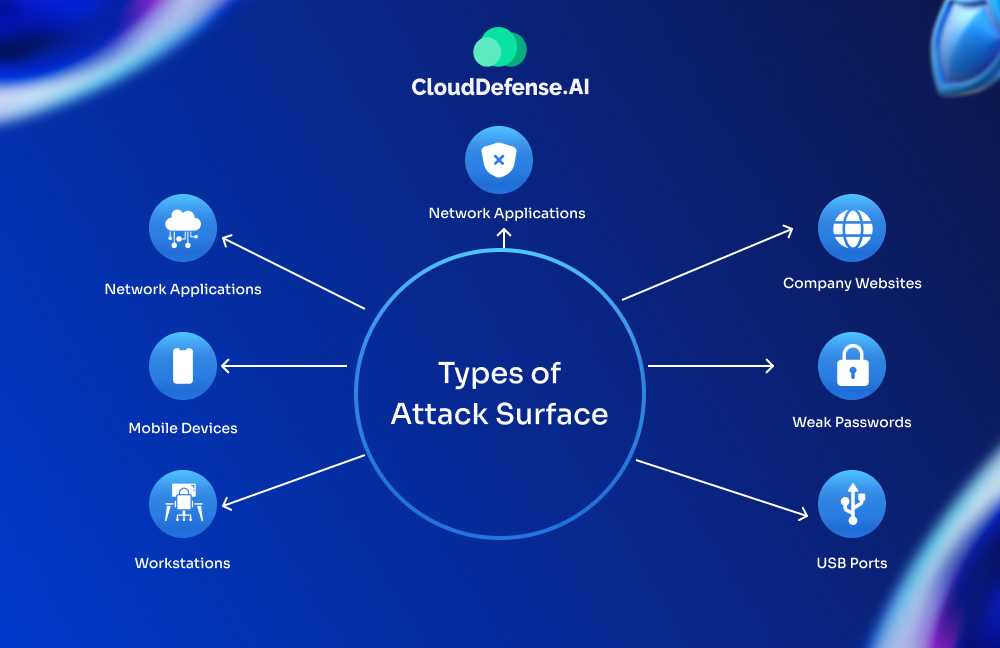
When we talk about Attack Surface Management, it’s helpful to know that there are different types of attack surfaces, each focusing on specific assets and their vulnerabilities. Grasping these types is essential for keeping your organization’s assets secure. Let’s break them down:
| Type | Description | Key Characteristics |
| External ASM (EASM) | This focuses on managing assets that are exposed to the outside world. | Includes elements like websites, public-facing cloud services, and servers. |
| Internal ASM (IASM) | This looks at assets that exist within your organization. | This includes your internal networks, devices, and applications. |
| Cyber Asset ASM (CAASM) | This is all about managing your digital assets. | It covers software, data, and intellectual property. |
| Open Source ASM (OSASM) | This focuses on the management of open-source software. | It involves libraries, frameworks, and tools that are publicly available. |
How ASM Protects from Cyberattacks
Attack Surface Management (ASM) acts as a multi-layered shield against cyberattacks by offering a proactive approach to cybersecurity. Here’s how it strengthens your defenses:
- See what attackers see: Gain a hacker’s-eye view of your vulnerabilities, so you can fix them before they’re used against you.
- Prioritize threats: Not all weaknesses are created equal. ASM helps you identify the most critical issues to patch first.
- Stay on top of your defenses: The digital world is constantly changing. ASM ensures your security measures keep pace.
With ASM, you’re not just reacting to attacks – you’re proactively preventing them. It’s a smarter way to defend your valuable data and keep your digital castle safe.
How ASM Works: The Five Stages of Attack Surface Management
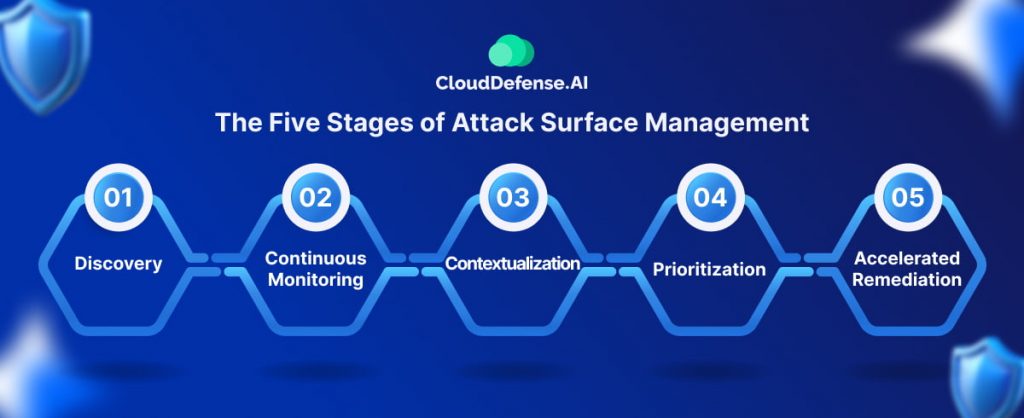
Attack Surface Management (ASM) isn’t a one-time fix; it’s an ongoing process that enables you to proactively manage your digital security posture. Let’s delve into the five core functions that form the foundation of an effective ASM strategy:
1. Discovery
The first step is akin to surveying a vast territory. In the initial “Discovery” phase, organizations identify and meticulously map all digital assets across their entire attack surface – both internal (on-premise devices and applications) and external (cloud-based resources and connected third-party systems).
Modern ASM solutions go beyond traditional methods, mimicking the attacker’s toolkit to uncover even unknown, rogue, or external assets that might harbor vulnerabilities. This comprehensive view ensures no potential entry point goes unnoticed.
2. Continuous Monitoring
The digital landscape is constantly in flux. New devices are added, users come and go, and the business itself evolves. The “Testing” phase addresses this dynamic nature by employing continuous attack surface monitoring and testing.
A modern ASM solution acts as a vigilant surveillance system, relentlessly reviewing and analyzing assets 24/7. This vigilance helps prevent the introduction of new security weaknesses, identify security gaps before they become critical breaches, and eliminate misconfigurations that could be exploited.
3. Contextualization
While any IT component could theoretically facilitate an attack, some assets inherently pose graver risks than others due to their context. Sophisticated ASM provides this critical contextual intelligence about each exposed asset – its purpose, owners, usage patterns, network connections, and overall business role.
In other words, factors like how, when, and where an asset is used, who owns it, its IP address and network connection points all contribute to determining the severity of the cyber risk it poses to the business. With this rich context, organizations can prioritize remediation efforts effectively.
4. Prioritization
Imagine having a never-ending to-do list. The “Prioritization” phase tackles this challenge by providing a clear roadmap for addressing vulnerabilities. Once comprehensive visibility is achieved, the next challenge is prioritizing remediation efforts across hundreds or thousands of vulnerabilities.
ASM solutions objectively prioritize using data-driven risk scoring derived from factors like exploit complexity, public disclosure, remediation difficulty, and up-to-date threat intelligence. Unlike subjective pen-testing approaches, these empirical risk calculations remove the guesswork.
5. Accelerated Remediation
The final piece of the puzzle is taking decisive action. Based on the insights gleaned from the previous phases, the “Remediation” phase empowers IT staff to identify the most severe risks and prioritize efforts to address them.
Since remediation often involves collaboration between IT and security teams, clear communication and alignment across all functions are crucial. By leveraging the information gathered throughout the ASM process, organizations can effectively patch vulnerabilities, tighten configurations, and implement additional security measures to create a more robust defensive posture.
How to Mitigate Attack Surface Risks

Now that we’ve covered what attack surface management involves, the next logical question is – how do you actually go about reducing your exposures? Here are some key strategies:
- Continuous Visibility Monitoring —The first step is maintaining persistent visibility across your entire attack surface through continuous discovery and monitoring. By automating this process, you ensure no new risk blind spots emerge as your environment evolves.
- Prioritize Based on Risk — With full visibility, you can then prioritize remediation efforts based on data-driven risk scoring that accounts for exploit complexity, asset value, and threat context. This lets you focus on the highest-severity exposures first.
- Prompt Patching — Many successful breaches stem from a failure to promptly patch known vulnerabilities. Leverage your ASM’s risk scoring to identify matching priorities and automate patch verification to harden your environment.
- Secure Configurations — Misconfigurations are a leading cause of preventable data breaches each year. Use security benchmarks to scan for insecure configurations across your apps, cloud services, network devices, and more.
- Limit Attack Paths — Reduce attack surface complexity by limiting inbound/outbound connectivity, segmenting networks, disabling risky ports/protocols, and removing unnecessary software and functionality.
- Enforce Least Privilege — By limiting user permissions to only what’s absolutely required, you prevent minor vulnerabilities from being avenues for full control and lateral movement.
- Manage Digital Supply Chain — Extend your ASM program’s visibility to map out risks across your digital supply chain and supply chain attack surface. Third-party code and connections can be a major risk.
How CloudDefense.AI Can Help You Mitigate Attack Surface Risks?
Now that you understand the importance of attack surface management (ASM) and the strategies to reduce risk, let’s see how CloudDefense.AI can be your partner in fortifying your digital security posture.
CloudDefense.AI leverages a powerful technique called attack path analysis to deliver a multi-faceted approach to bolstering your cloud security. Here’s how it works and the benefits it offers:
Mapping Your Vulnerabilities
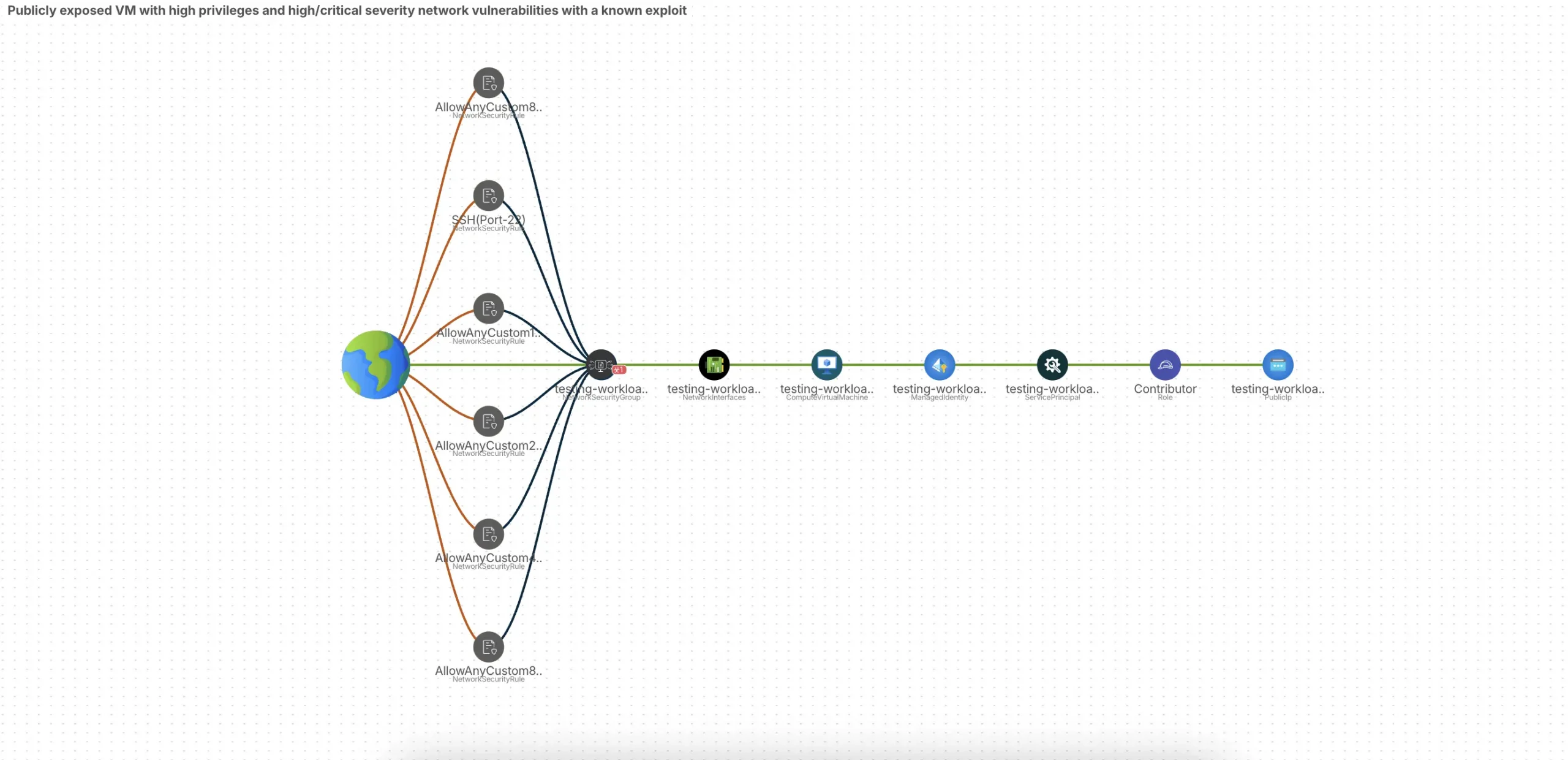
CloudDefense.AI goes beyond basic vulnerability scanning. It meticulously crawls your entire cloud infrastructure, applications, and configurations and crafts a holistic attack path analysis graph that exposes the potential attack vector. This in-depth analysis identifies all potential entry points for attackers, including vulnerabilities, misconfigured systems, exposed assets, and weaknesses in access controls.
Building the Attack Graph
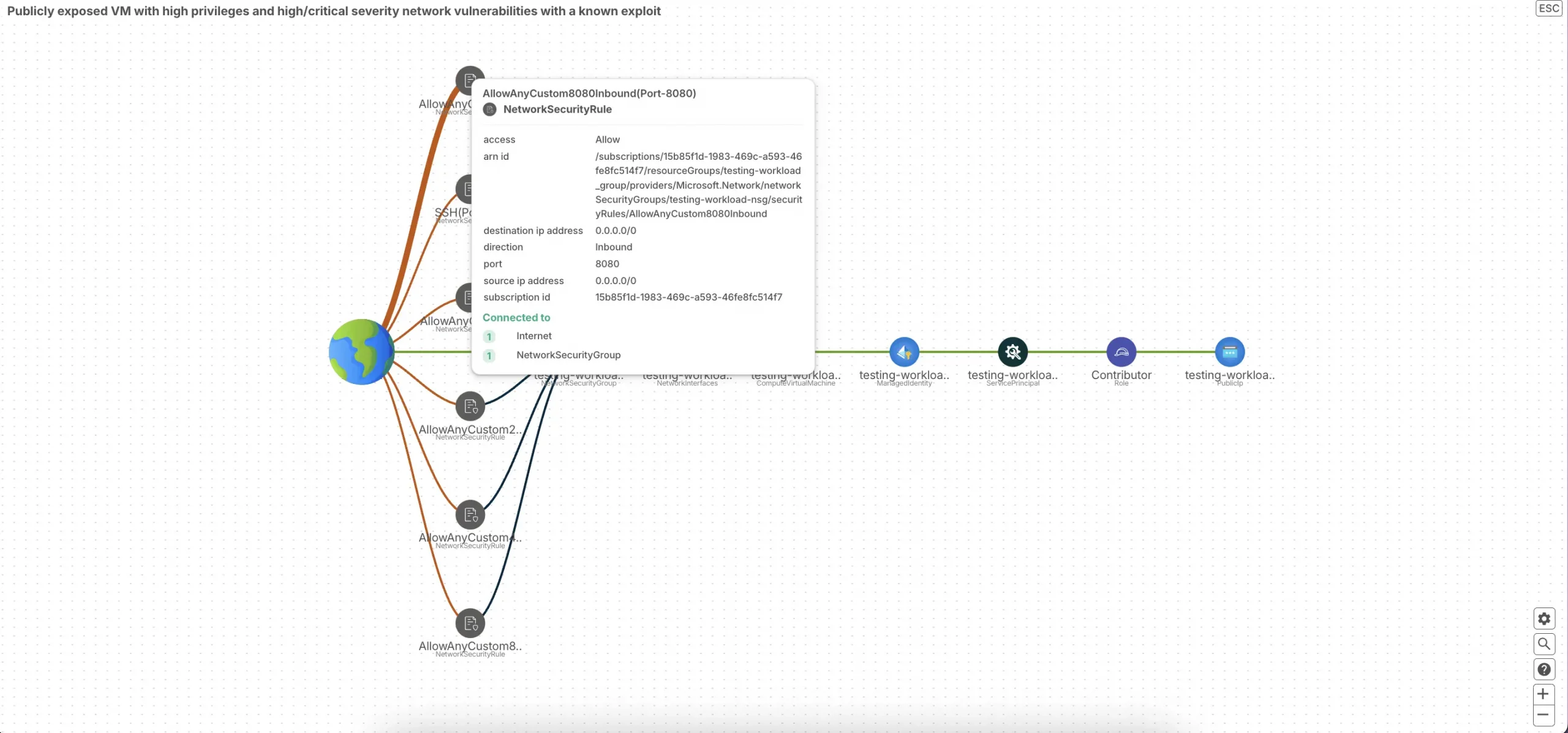
Imagine a map that not only shows individual vulnerabilities but also how they connect, creating potential pathways for attackers to infiltrate your systems. CloudDefense.AI constructs a comprehensive attack graph that visualizes these interconnected vulnerabilities and assets. This allows you to see the bigger picture and understand how a seemingly minor weakness could be exploited as part of a larger attack.
Prioritizing Threats
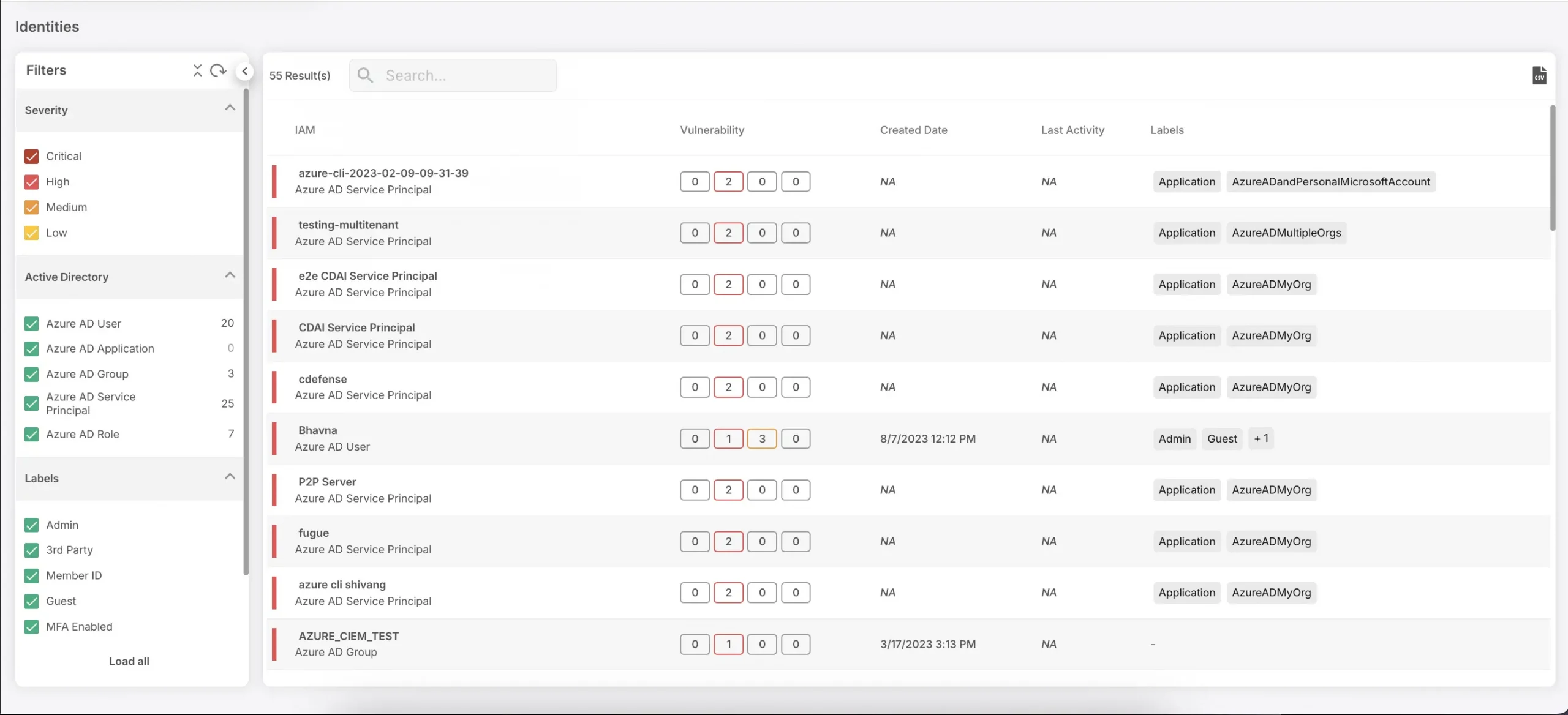
The attack graph doesn’t just reveal the paths; it also prioritizes them. CloudDefense.AI assesses the likelihood and potential impact of each attack scenario. This critical information helps you focus your remediation efforts on the vulnerabilities that pose the most significant risk. You can prioritize patching the most exploitable weaknesses that could have a devastating impact if compromised.
Continuous Monitoring
Cybersecurity is an ongoing battle. CloudDefense.AI doesn’t stop at a one-time analysis. It acts as a vigilant sentinel, continuously monitoring your cloud environment for new vulnerabilities, misconfigurations, and changes. The attack graph is updated in real-time, ensuring you always have the most up-to-date picture of your security posture.
The Benefits of Proactive Security
By implementing CloudDefense.AI’s attack path analysis, you gain a significant advantage:
- Proactive Threat Detection: Identify potential attack paths before attackers do. This allows you to take preemptive measures to mitigate risks and prevent breaches altogether.
- Prioritized Remediation: Focus your limited resources on the most critical vulnerabilities, maximizing the effectiveness of your security efforts.
- Improved Decision-Making: Visualizing attack paths provides clear and actionable insights. This empowers you to make informed decisions about security investments and strategies.
- Reduced Risk of Breaches: By addressing the most exploitable vulnerabilities first, you can significantly reduce the likelihood of successful attacks and data breaches.
- Enhanced Compliance: Understanding your attack surface and prioritizing vulnerabilities helps you comply with various security regulations and standards.
CloudDefense.AI empowers you to shift from reactive to proactive security. By anticipating attacker strategies and prioritizing vulnerabilities, you can significantly strengthen your cloud defenses and stay ahead of evolving threats.
Don’t wait for an attack to happen – take control of your attack surface and proactively safeguard your organization’s critical data and systems. Book a free demo today and find out how CloudDefense.AI can help you stay one step ahead of attackers.







