What is a Web Application Firewall (WAF)?
A Web Application Firewall (WAF) is a security solution designed to protect web applications by filtering and monitoring HTTP/HTTPS traffic between a web application and the internet. It operates at the application layer to block malicious requests targeting vulnerabilities.
What it does:
- Protects against common threats like SQL injection, cross-site scripting (XSS), and DDoS attacks.
- Inspects and filters incoming traffic based on predefined security rules.
- Helps maintain application performance by mitigating bot traffic.
- Provides real-time alerts for suspicious activity.
- Supports compliance with regulations like GDPR, PCI DSS, and HIPAA.
By acting as a critical security layer, a web application firewall ensures application reliability, boosts user trust, and strengthens an organization’s overall cybersecurity posture.
WAF Security: Blocklist vs. Allowlist
We’ve discussed how WAFs act as security guards for your web applications, but there are different approaches they can take to identify and block threats. Here’s a breakdown of the two main web application firewall models: Blocklist WAFs and Allowlist WAFs.
| Feature | Blocklist WAF | Allowlist WAF |
| Approach | This model focuses on blocking known malicious traffic patterns. | This model focuses on allowing only pre-approved, legitimate traffic. |
| Effectiveness | Well-suited for blocking common attacks based on known patterns. | Offers the highest level of security by ensuring only authorized traffic reaches the application. |
| Limitations | May not be effective against zero-day attacks (new, unknown threats). Requires constant updates to the blocklist to stay effective. | Requires a comprehensive understanding of all legitimate traffic patterns, which can be complex to configure. |
| Use Case | Ideal for most businesses as a first line of defense against common web application attacks. | Suited for highly secure environments with strictly controlled access, or for applications handling extremely sensitive data. |
How Does a WAF Work?
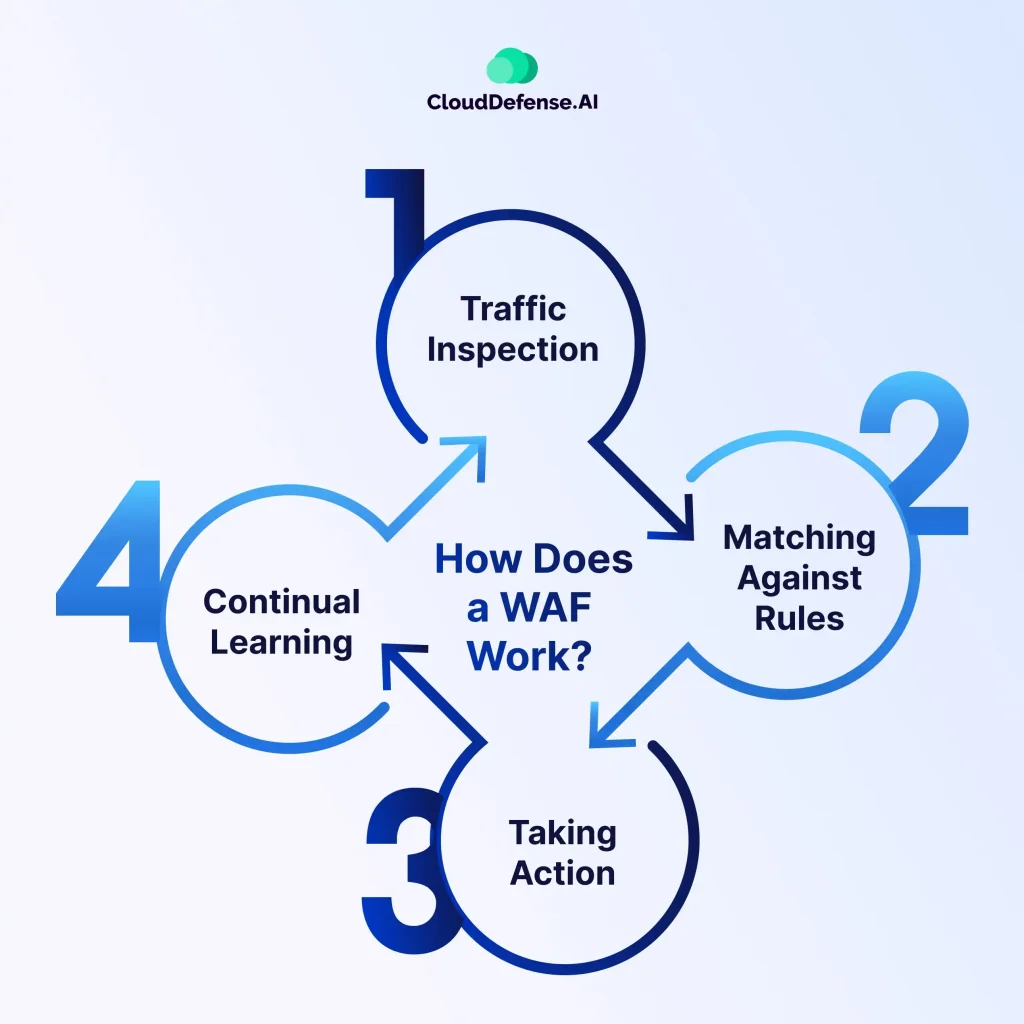
Under the hood, a web application firewall acts like a vigilant security guard, constantly inspecting traffic to and from your web application. Here’s a breakdown of its core functions:
1. Traffic Inspection: The WAF sits between your web application and the internet, functioning as a reverse proxy. This means all incoming requests from users and devices on the internet first pass through the web application firewall for inspection. The WAF meticulously analyzes each part of the communication, including:
- HTTP Request Methods: These methods specify the type of action being requested, such as retrieving data (GET), sending data (POST), updating data (PUT), or deleting data (DELETE).
- Headers: These contain additional information about the request, like the browser type or cookies.
- Query Strings: Data appended to the URL that provides specific instructions to the web application.
- Body: The main content of the request, often used to submit form data or upload files.
2. Matching Against Rules: The WAF is equipped with a set of predefined rules that act as red flags for malicious activity. These rules are based on known attack patterns, such as SQL injection attempts or cross-site scripting (XSS) vulnerabilities. By comparing the inspected traffic against these rules, the WAF can identify potential threats.
3. Taking Action: If the web application firewall detects a request that matches a security rule, it can take several actions depending on its configuration. Here are some common options:
- Blocking the Request: This is the most common response for high-risk threats. The web application firewall stops the malicious request from reaching your web application, effectively preventing the attack.
- Challenging the User: The WAF might display a CAPTCHA challenge to differentiate between a human user and an automated bot potentially carrying out an attack.
- Alerting Security Team: The WAF can notify security personnel about suspicious activity so they can investigate further and take appropriate measures.
4. Continual Learning: Modern WAFs are constantly evolving. They can learn from new attack patterns and update their rule sets to stay ahead of emerging threats. This continual learning process helps ensure comprehensive protection for your web application.
Key Benefits of a WAF
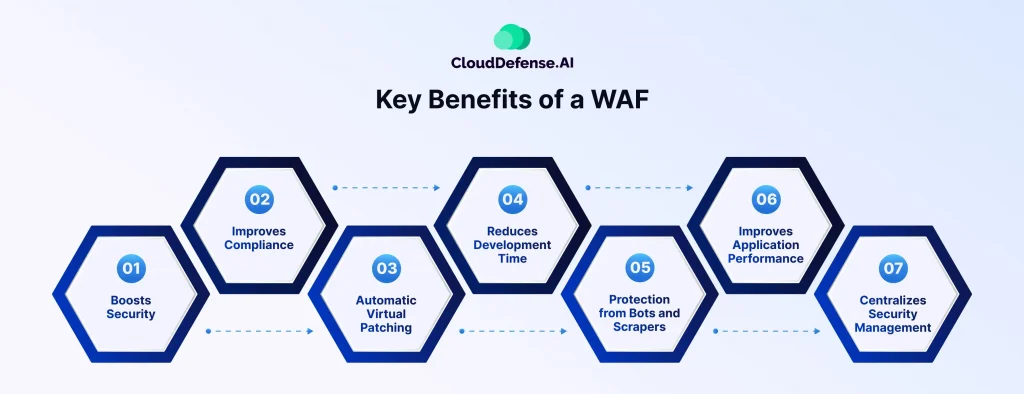
Boosts Security: The primary function of a web application firewall is to shield your web application from a vast array of threats. By filtering and blocking malicious traffic, WAFs significantly reduce the risk of data breaches, malware infections, and application downtime. They can defend against common attacks like SQL injection, cross-site scripting (XSS), and Denial-of-Service (DoS) attacks.
Improves Compliance: If your business has to follow strict data security standards and regulations (and let’s be real, who doesn’t these days?), a WAF becomes your new best friend. Many compliance requirements mandate protective measures like input filtering, malicious bot blocking, and preventing data leaks – all things a WAF is custom-built to handle. Having that web application firewall will make your audits go way smoother.
Automatic Virtual Patching Even with regular software updates, some security holes are bound to slip through the cracks from time to time. But a WAF has you covered with its ability to create quick virtual patches. As soon as a new vulnerability is identified, the WAF can throw up a new rule to detect and block any attempts to exploit that opening until the actual patch is installed.
Reduces Development Time: Setting up intricate security measures from scratch can be a real headache for developers. Thankfully, WAFs come pre-programmed with a whole arsenal of security rules, saving your tech team valuable time and effort. They can focus on building amazing features for your website, while the WAF handles the security side of things.
Protection from Bots and Scrapers: Just like those annoying automated phone calls, there are bots that target websites. Some are harmless, like search engine crawlers. But others can be malicious, trying to steal data or overwhelm your website with traffic. WAFs can be configured to identify and block these bad bots, keeping your website running smoothly for real customers.
Improves Application Performance: WAFs can actually enhance the performance of your web application by filtering out unnecessary traffic and malicious requests. This reduces the load on your web server, leading to faster response times and a smoother user experience.
Centralizes Security Management: Managing security for multiple websites can be a juggling act. WAFs often come with a central control panel, giving you a bird’s-eye view of all your website security in one place. It’s like having a security HQ where you can monitor threats and make adjustments as needed.
Why is WAF Security Important?
Here are the reasons why WAF security matters:
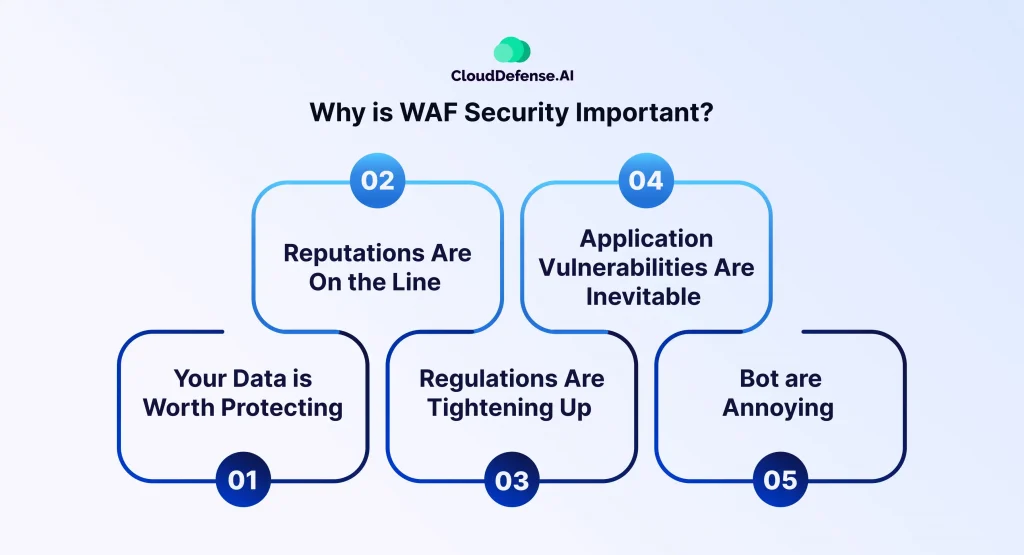
Your Data is Worth Protecting
Think about all the sensitive stuff your website or app deals with – customer info, financial records, proprietary data, you name it. That data is essentially money in the bank for cybercriminals looking to steal and exploit it. A WAF throws up a brick wall to protect that invaluable data from being pilfered.
Reputations Are On the Line
Besides the data risks, security breaches can utterly demolish a company’s reputation and credibility in a heartbeat. Imagine the public relations nightmare if you had to confess that Timmy’s little league fundraising website got hacked and compromised. Not a good look! Having robust WAF protection helps you avoid those cringe-worthy headlines.
Regulations Are Tightening Up
These days, businesses have to follow a ton of data security regulations and compliance requirements like PCI DSS, HIPAA, GDPR, and more. Failure to meet those standards can result in hefty fines and penalties. Well, guess what? Having a robust WAF is practically mandatory for checking most of those compliance boxes.
Application Vulnerabilities Are Inevitable
No matter how secure your applications aim to be, they’re software built by humans – vulnerabilities will always exist and be discovered. WAFs give you a fallback emergency measure by virtually patching those holes on the fly until they can be properly fixed in updates.
Bot are Annoying
Having your sites constantly bombarded by aggressive bots trying to scrape data, spread malware, launch DDoS attacks – it’s just the worst. WAFs can identify and squash those rampant bot threats, freeing your servers from unnecessary traffic congestion.
At the end of the day, the internet isn’t all sunshine and rainbows. There’s a whole dark underworld of cyber threats and malicious actors constantly looking to exploit websites for profit or chaos. Implementing a robust Web Application Firewall solution is just smart security that could save you from catastrophic headaches down this road. It’s the bodyguard your virtual assets deserve!
Deploying a Web Application Firewall (WAF)
Here’s a breakdown of the deployment process and some key questions to ask before making a decision:
Web Application Firewall Deployment Steps:
- Choosing a Deployment Model: WAFs come in various deployment flavors, each with its own advantages and considerations. Here are the main options:
- Cloud-based WAF: Offered as a service by cloud providers, this option is easy to set up and manage but may come with limitations on customization.
- On-premise WAF: Installed on your own hardware, this approach offers more control but requires additional IT resources for management and maintenance.
- Hybrid WAF: A combination of cloud-based and on-premise deployment, offering a balance between flexibility and control.
- WAF Configuration: Once deployed, you’ll need to configure the Web Application Firewall to match your specific needs. This involves tailoring security rules, defining which web applications to protect, and specifying how the WAF should respond to detected threats.
- Integration and Testing: The web application firewall needs to integrate seamlessly with your existing application infrastructure. Rigorous testing is crucial to ensure the WAF doesn’t inadvertently disrupt legitimate traffic flow.
- Ongoing Monitoring and Maintenance: WAFs require ongoing monitoring to ensure they remain effective. Security rule sets need periodic updates to reflect evolving threats, and the WAF’s performance should be monitored for any signs of impact on application performance.
Choosing the Right WAF: Questions to Ask Before Deciding
- What are my security needs and priorities? Consider the types of attacks you’re most vulnerable to and the level of customization required.
- What is my IT infrastructure and resource availability? Cloud-based Web Application Firewalls might be ideal for limited IT resources, while on-premise solutions offer more control.
- What is my budget? Cloud-based WAFs typically have subscription fees, while on-premise solutions require upfront hardware and software costs.
- What are my compliance requirements? Certain regulations might mandate specific web application firewall features or deployment models.
- Do I have the expertise to manage a WAF? Cloud-based options often come with managed services, while on-premise solutions require in-house web application firewall expertise.
By carefully considering these factors and following a well-defined deployment process, you can ensure your WAF effectively safeguards your web applications from a wide range of threats.
Final Words
Throughout this article we discussed how WAFs work, the benefits they provide, and the different deployment options available, you can make informed decisions about securing your web applications.
Remember, WAFs are not a silver bullet, but a vital layer in your overall security strategy. When combined with other security measures and best practices, WAFs can help you achieve peace of mind, knowing your valuable online assets are protected.







