What is Vulnerability Assessment?
A vulnerability assessment is a systematic process of identifying, analyzing, and prioritizing security weaknesses in an organization’s IT systems, applications, and network infrastructure.
It aims to detect vulnerabilities that could be exploited by attackers, allowing organizations to address potential security risks before they can be used maliciously.
This assessment helps improve an organization’s security posture by uncovering flaws that could lead to unauthorized access, data breaches, or other cyber threats.
Threats that Vulnerability Assessments Help Prevent
Here are some common threats that vulnerability assessments help organizations prevent:
- Malware and Ransomware Attacks: Vulnerability assessments can detect unpatched software or outdated systems that may be targeted by malicious code, minimizing the risk of malware infiltrations and ransomware exploits that could lead to data loss or system downtime.
- Unauthorized Access: By identifying weak access controls, vulnerability assessments help prevent unauthorized users from gaining entry to critical systems and sensitive data, reducing the risk of data theft and insider threats.
- SQL Injection and Cross-Site Scripting (XSS): Application vulnerabilities like SQL injection and XSS are frequent entry points for attackers. Assessments uncover these issues, allowing development teams to secure applications and prevent data breaches.
- Denial of Service (DoS) Attacks: Identifying misconfigurations and outdated systems can help organizations defend against DoS attacks, which aim to overload network resources and disrupt business operations.
- Privilege Escalation Attacks: Assessments reveal privilege escalation risks within a system, where users could exploit permissions to gain higher access levels, thus preventing unauthorized control over sensitive areas.
- Unencrypted Data Exposure: Data transmitted or stored without encryption is vulnerable to interception. Vulnerability assessments highlight unencrypted channels or repositories, prompting remediation efforts to secure sensitive data from potential exposure.
- Configuration Errors: Misconfigurations in cloud services, servers, or devices are common security gaps. A vulnerability assessment detects these errors, helping to prevent attackers from exploiting misconfigurations to access resources or inject malicious scripts.
Regular vulnerability assessments help organizations address these and a range of other threats, ensuring a resilient security posture in the face of evolving cyber risks.
Importance of Vulnerability Assessment
Vulnerability assessment has transitioned from a mere optional resource to a crucial necessity for organizations. Compliance requirements, such as GDPR, PCI DSS, and HIPAA, mandate regular vulnerability assessments to uphold data security standards.
These assessments encompass various tasks, including security control checks, network analysis for password breaches, and vulnerability scanning. The resulting VA report serves as a cornerstone for organizational security policies.
By identifying security weaknesses and associated risks, vulnerability assessments empower organizations to strengthen their defenses against cyber threats, ultimately reducing the likelihood of data breaches and protecting sensitive information.
Types of Vulnerability Assessments
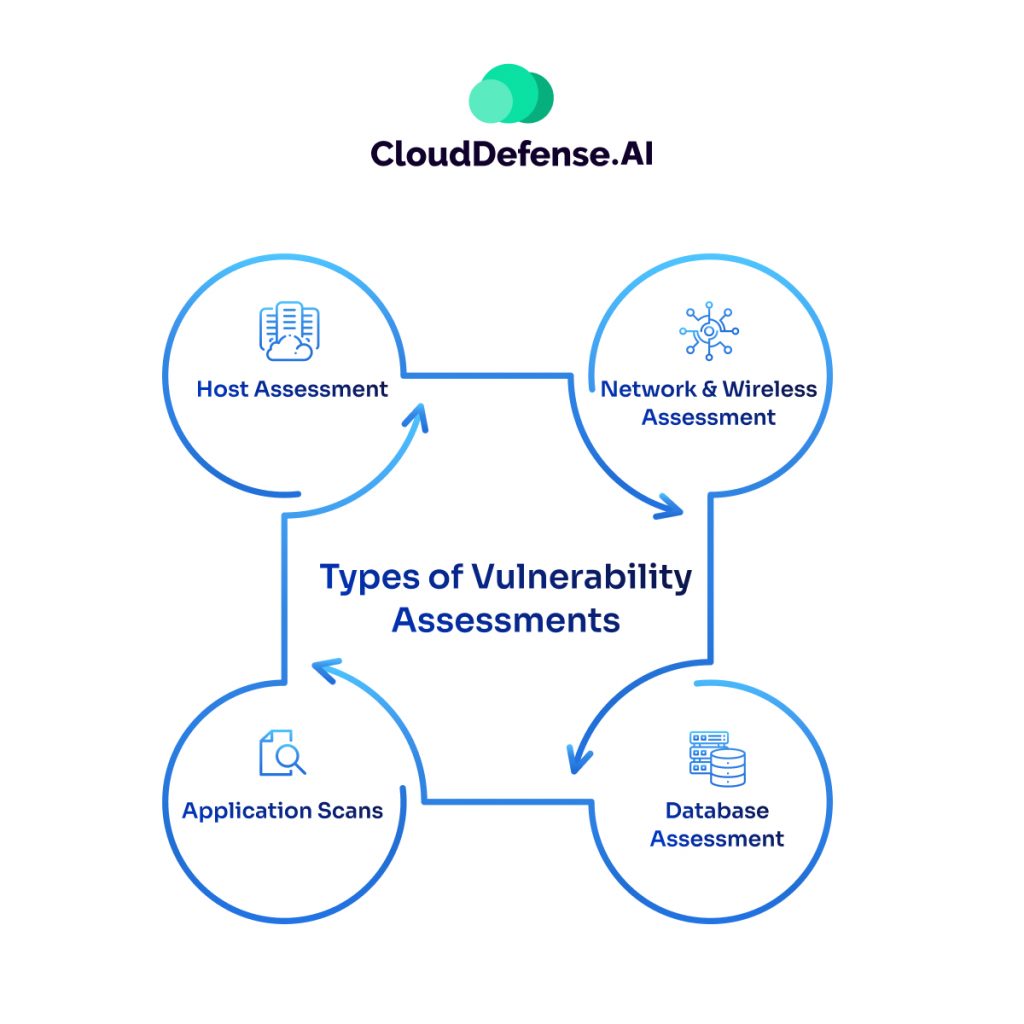
Vulnerability assessments include a range of methodologies customized to identify and address specific vulnerabilities within an organization’s infrastructure. Here are the different types:
- Host Assessment: Focuses on critical servers susceptible to attacks if not properly tested or generated from a tested machine image.
- Network and Wireless Assessment: Evaluate policies and practices to prevent unauthorized access to private or public networks and resources. This includes identifying vulnerabilities in network configurations and wireless infrastructure.
- Database Assessment: Analyzes databases or big data systems for vulnerabilities, misconfigurations, and insecure environments. It also involves classifying sensitive data across the organization’s infrastructure.
- Application Scans: Identifies security vulnerabilities in web applications and their source code through automated scans or static/dynamic analysis.
Vulnerability Assessment: Steps in the Security Scanning Process
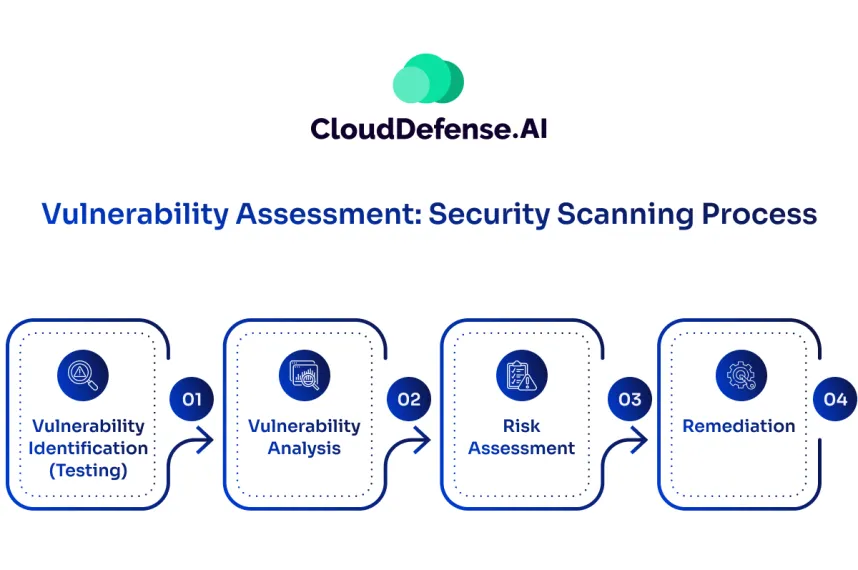
The vulnerability assessment process systematically identifies and mitigates security weaknesses across an organization’s systems, networks, and applications. Here’s an overview of each phase in this critical security process:
Vulnerability Identification
Security analysts begin by assessing the security posture of applications, servers, and systems using automated tools and manual evaluation methods. By referencing vulnerability databases and threat intelligence feeds, they gain a comprehensive view of potential security issues.
Vulnerability Analysis
In this stage, analysts investigate the underlying causes of each identified vulnerability. They pinpoint the components responsible and evaluate root causes, such as outdated software or configuration errors, which helps in formulating targeted solutions.
Risk Assessment and Prioritization
Each vulnerability is then assessed for risk based on factors like the severity of potential attacks, ease of exploitation, and the potential impact on critical systems and data. This prioritization enables organizations to focus on the most urgent vulnerabilities first, optimizing resource allocation.
Remediation Planning and Execution
Security, development, and operations teams collaborate to remediate vulnerabilities. Actions may include implementing security updates, changing configurations, applying patches, or deploying additional security tools. Clear communication across teams ensures that remediation efforts are both efficient and comprehensive.
Continuous Monitoring and Reassessment
A vulnerability assessment is most effective when integrated into an ongoing security program. Continuous scans, automated tools, and cross-departmental collaboration—often enabled through DevSecOps—support real-time monitoring and regular reassessment, helping to address new vulnerabilities as they arise preemptively.
Vulnerability assessment tools, such as web applications and network scanners, automate many of these tasks, enabling organizations to scan critical IT systems regularly.
How can I tell if my Organization Requires a Vulnerability Assessment?
Determining whether your organization requires a vulnerability assessment involves assessing the effectiveness of security initiatives conducted throughout the Software Development Life Cycle. Here’s how to evaluate:
- Effectiveness of Security Initiatives: Evaluate whether security measures implemented during the SDLC, such as developer training in secure coding and reviews of security architecture and source code, have been successful. Organizations that prioritize these activities are likely to have fewer vulnerabilities compared to those that do not.
- Frequency of Vulnerability Testing: Consider the frequency of vulnerability testing. Annual vulnerability assessments are essential for organizations developing applications or utilizing third-party applications. Additionally, conducting assessments after significant changes to applications or application environments ensures ongoing security efficacy.
- Nature of Application Development: Assess the nature of your organization’s application development. If your organization develops applications internally or relies on third-party applications, vulnerability assessments become critical to identify and mitigate security risks.
- Risk Management Approach: Evaluate your organization’s risk management approach. If your organization prioritizes proactive risk mitigation and maintaining a robust security posture, vulnerability assessments are indispensable for identifying and addressing potential vulnerabilities.
- Regulatory Compliance Requirements: Consider regulatory compliance requirements. Industries such as finance, healthcare, and government often have stringent compliance standards mandating regular vulnerability assessments to ensure data protection and regulatory compliance.
Defeat Vulnerabilities with CloudDefense.AI
CloudDefense.AI offers a cutting-edge vulnerability management solution that goes beyond traditional scanning tools, delivering complete protection and proactive threat mitigation for organizations of all sizes.
Key Features:
- Continuous, Agentless Assessment With continuous agentless scanning, CloudDefense.AI monitors cloud environments in real time, ensuring that vulnerabilities are identified and remediated before they can be exploited. The platform’s AI-powered remediation addresses threats automatically, staying ahead of evolving risks.
- Asset Inventory CloudDefense.AI provides a detailed inventory of all assets, including libraries and packages across multi-cloud environments. This complete visibility enables more effective vulnerability discovery and risk management across diverse cloud setups.
- Context-Driven Prioritization Using context-driven prioritization, the platform helps organizations focus on the most critical vulnerabilities. By analyzing the potential business impact, CloudDefense.AI ensures that teams address the vulnerabilities that matter most, optimizing resource allocation.
- Attack Path Analysis & Visual Graph CloudDefense.AI offers attack path analysis with visual graph capabilities to help security teams identify interconnectivity vulnerabilities. This feature makes it easy to visualize and prioritize vulnerabilities based on their risk to the overall infrastructure.
- Real-Time CVE Insights Stay updated on the latest CVE trends. CloudDefense.AI provides insights into threats, enabling faster responses to trending vulnerabilities with potential business impact.
- CI/CD Integration Smoothly integrate CloudDefense.AI into your CI/CD pipelines to automate vulnerability scanning throughout the development cycle. By identifying and resolving vulnerabilities before they reach production, your organization can maintain speed without sacrificing security.
- Compliance Management CloudDefense.AI simplifies compliance management by aligning with key security standards and frameworks. The platform ensures continuous compliance and provides automated reporting to streamline audits.
- Exclusive Advanced Features Features like a rapid response to critical threats and an advanced query builder further enhance CloudDefense.AI’s capabilities, setting it apart as a leader in vulnerability assessment.
Ready to transform your vulnerability management? Book a free demo today to experience firsthand how CloudDefense.AI can strengthen your security posture and safeguard your organization against emerging threats.







