Let’s start with an alarming statistics from University of North Georgia which shows that cyberattacks occur every 39 seconds! The frequency of cybercrime is on the rise, with projected costs expected to reach $10.5 trillion by 2025.
In the face of such threats, including data breaches, ransomware attacks, and security breaches, implementing a threat intelligence platform is a must-have for companies of all sizes.
In this article, we’ll explore the workings of threat intelligence platforms. We will cover:
- What is a Threat Intelligence Platform?
- How it Works?
- Importance of Cyber Threat Intelligence Platform
- Use Cases of Threat Intel Platforms and much more!
Keep reading to learn how you as a company can protect yourself more effectively with the extensive capabilities of a Threat Intelligence Platform.
Threat Intelligence Platform Definition
A Threat Intelligence Platform is a sophisticated technology solution designed to streamline and enhance the management and utilization of threat intelligence data within cybersecurity operations. It serves as a centralized hub for the collection, aggregation, organization, and analysis of diverse threat data from a multitude of sources and formats.
At its core, a TIP acts as a comprehensive repository for all forms of threat intelligence, including IOCs, known malware signatures, vulnerabilities, attacker tactics, techniques, procedures, and other relevant contextual information. By consolidating this wealth of data into a single platform, security teams gain unprecedented visibility into emerging threats and ongoing cybersecurity risks.
How Threat Intelligence Platforms Work?
Cyber Threat Intel Platforms optimize the complex process of gathering, processing, analyzing, and distributing threat intelligence data within cybersecurity operations. Beginning with requirements planning, TIPs identify the organization’s specific needs and outcomes desired from the intelligence. They then automatically collect raw data from a multitude of external sources, including security vendors, open-source feeds, and dark web forums.
This data undergoes processing to convert it into analyzable formats, followed by rigorous analysis to transform it into actionable intelligence reports tailored for various stakeholders. TIPs ensure clear and concise dissemination of intelligence insights, avoiding technical jargon and presenting information in accessible formats such as single-page reports or slide decks.
Use Case of Threat Intelligence Platforms
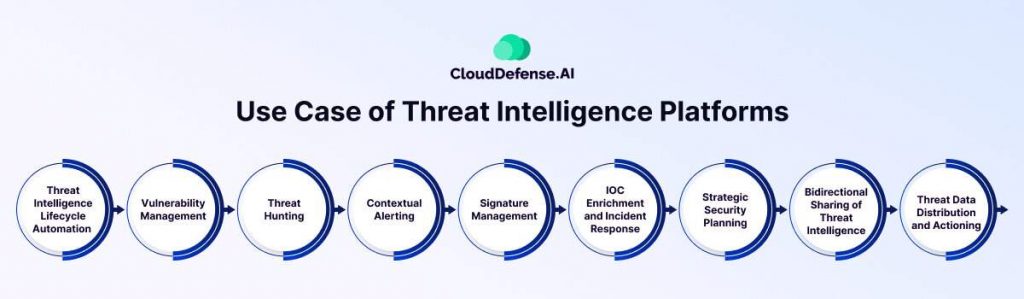
In today’s date, Threat Intelligence Platforms, or TIPs, are used everywhere in modern cybersecurity operations. It serves as a pillar for enhancing threat detection, response, and mitigation capabilities across various domains. Let’s dissect the key roles and contributions of a TIP:
Threat Intelligence Lifecycle Automation
TIPs automate the collection, integration, and analysis of threat intelligence data, relieving security teams from manual data processing tasks. By extracting actionable insights from disparate sources and providing context on indicators of compromise, or IOCs, and attacker tactics, TIPs enable security teams to focus on decision-making and threat response activities rather than drowning in data overload.
Vulnerability Management
TIPs empower security analysts to prioritize vulnerabilities effectively by using threat intelligence insights. By identifying critical vulnerabilities and recommending optimal mitigation strategies, TIPs enhance the efficiency and effectiveness of vulnerability management programs, enabling organizations to proactively reduce their exposure to cyber risks.
Threat Hunting
TIPs equip Security Operations Center teams with the automation and collaboration capabilities needed to streamline the threat-hunting process. By automating intelligence gathering and IoC searches, and supporting frameworks like MITRE ATT&CK, TIPs enhance the effectiveness of threat-hunting initiatives, reducing the mean time to detect and minimizing the impact of cyberattacks.
Contextual Alerting
TIPs provide contextualized and actionable threat intelligence by organizing and connecting threat data to relevant threats, incidents, and adversaries. By enabling security teams to identify hidden threat patterns and prioritize alerts based on their significance, TIPs allow for more informed and timely response actions, reducing alert fatigue and enhancing SOC efficiency.
Signature Management
TIPs contextualize signatures by connecting them with threat indicators and intrusion phases, thereby accelerating response times and minimizing alert confusion. By providing context-rich intelligence, TIPs enable security teams to prioritize response actions effectively and enhance the overall efficacy of signature-based detection mechanisms.
IOC Enrichment and Incident Response
TIPs enrich indicators with additional contexts, such as reputation data and threat-type information, to assist SOC analysts in assessing alerts and prioritizing response efforts. By reducing false positives, enriching alerts with relevant context, and facilitating rapid incident scoping and response, TIPs play a crucial role in improving incident response capabilities and minimizing the impact of security incidents.
Strategic Security Planning
TIPs serve as a knowledge repository for strategic security planning by providing insights into adversary activities and effective defense strategies. By identifying centers of gravity for adversary activities and informing resource allocation decisions, TIPs enable organizations to develop proactive security measures and optimize their security posture.
Bidirectional Sharing of Threat Intelligence
TIPs allow bidirectional sharing of threat intelligence with external stakeholders, including CERTs, ISACs/ISAOs, vendors, and clients. By exchanging technical and strategic intelligence in real-time, TIPs enhance situational awareness and enable collaborative defense against common threats, thereby strengthening overall cybersecurity resilience.
Threat Data Distribution and Actioning
TIPs enable the distribution and actioning of threat intelligence across security tools and teams, empowering quick response actions and mitigations. By automating the propagation of analyzed and enriched threat data to relevant security tools and teams, TIPs make it possible to response to threats fast and reduce time-to-action, ultimately enhancing organizational resilience against cyber threats.
The Value of a Threat Intelligence Platform
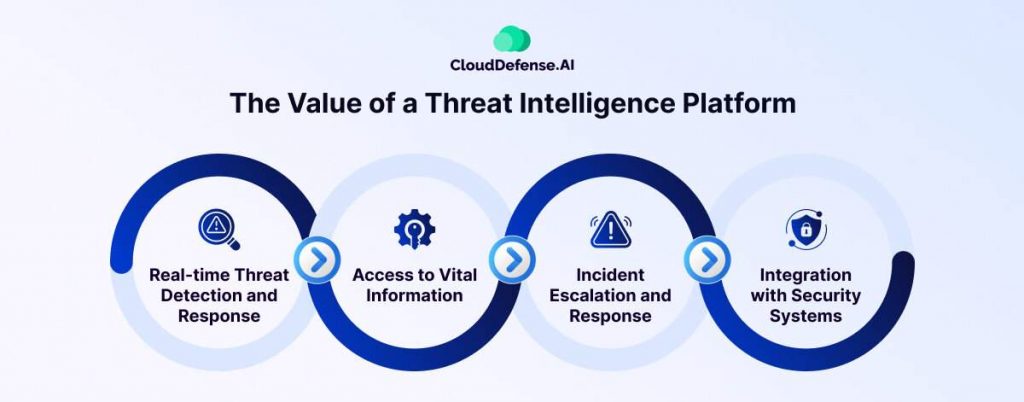
A Cyber Threat Intelligence Program delivers immense value to security and threat intelligence teams by providing powerful capabilities to enhance cybersecurity operations and strengthen defense mechanisms against threats. Let’s explore the significance of a Threat Intelligence Program:
Real-time Threat Detection and Response
With a TIP in place, security teams can monitor and quickly detect potential security threats in real-time. By using continuous monitoring capabilities and automated threat detection mechanisms, a TIP empowers organizations to respond promptly to emerging threats, minimizing the potential impact of security incidents.
Access to Vital Information
A TIP provides vital information about current and future security risks, threats, attacks, and vulnerabilities. By aggregating and enriching threat intelligence data, including details about threat adversaries and their tactics, techniques, and procedures, a TIP equips security teams with the insights needed to understand and mitigate complex cyber threats effectively.
Incident Escalation and Response
A TIP facilitates the setup of security incident escalation and response processes. By providing workflows and automation capabilities for incident management, a TIP ensures that security incidents are promptly escalated to the appropriate stakeholders and responded to in a coordinated and efficient manner, minimizing the impact on organizational security posture.
Integration with Security Systems
A TIP continually feeds the most up-to-date threat intelligence data to security systems such as SIEM solutions, endpoints, firewalls, APIs, and IPSs. By integrating with existing security infrastructure, a TIP enhances the effectiveness of security controls and enables proactive threat detection and response across the organization.
Who uses a Threat Intelligence Platform?
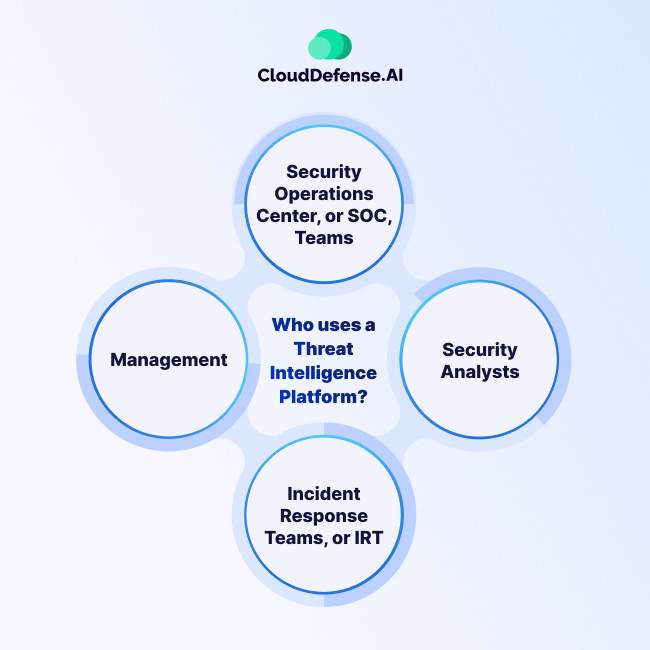
Looking at how important Threat Intelligence Platforms have become in cybersecurity teams, it is not surprising to note its use by various roles within an organization. Each of these teams benefit from its capabilities in different ways:
- Security Operations Center, or SOC, Teams: SOC teams rely on TIPs to identify potential attacks against the organization and manage incident response effectively. Threat intelligence enriches SOC teams’ abilities to detect new exploits and emerging threats in real-time, allowing them to proactively defend against cyber threats.
- Security Analysts: Security analysts use TIPs to design and configure the organization’s defense mechanisms based on insights gleaned from threat intelligence data. By understanding the types of threats that their defenses should protect against, security analysts can optimize security strategies and implement appropriate security controls.
- Incident Response Teams, or IRT: IRT members utilize TIPs during security incident remediation efforts to understand how threats operate and their effects on corporate systems. Threat intelligence provides valuable context and insights that aid in the efficient resolution of security incidents, enabling IRTs to restore normal operations swiftly.
- Management: Executive management relies on TIPs to make strategic decisions regarding the organization’s security posture and investments. A good understanding of cyber threats, supported by threat intelligence, allows management to shape the organization’s security strategy effectively and allocate resources appropriately to mitigate risks.
How to Choose a Threat Intelligence Platform?
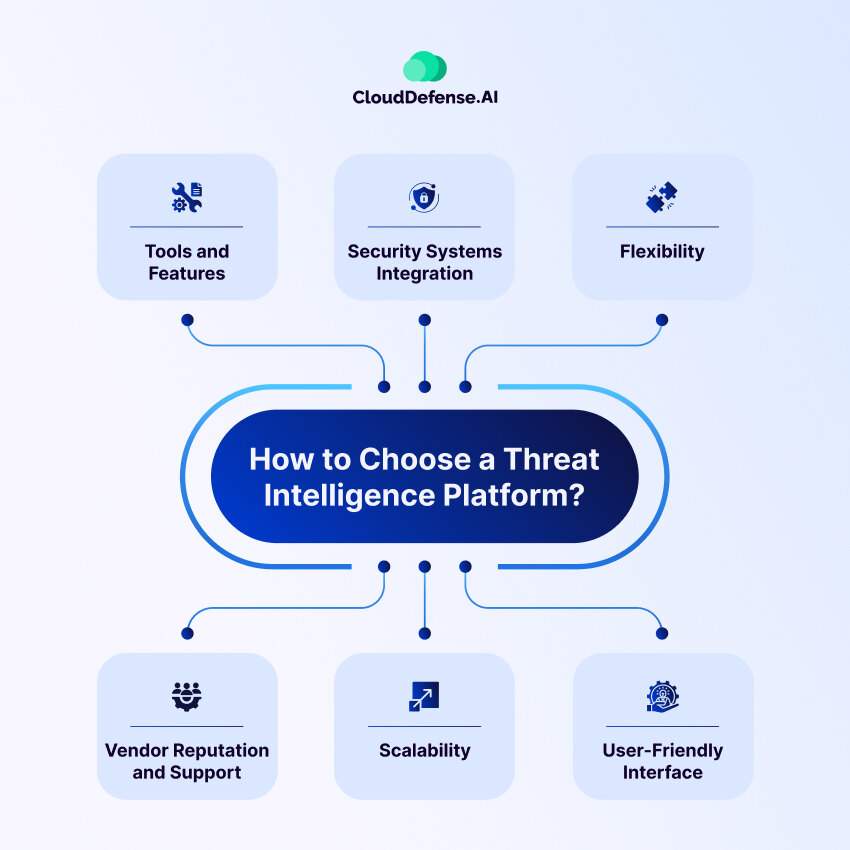
When choosing a cyber threat intelligence platform for your business, several key factors should be carefully evaluated to ensure that the chosen platform meets your organization’s specific needs and requirements effectively.
Tools and Features
Evaluate the tools and features included with the platform to understand its capabilities in gathering, analyzing, and managing threat intelligence data. Look for features such as data collection from various sources, data analysis capabilities, incident ticketing systems, integration with security systems like SIEM, SOAR, and endpoint security solutions.
Security Systems Integration
Consider the platform’s ability to integrate with existing security systems within your organization. A TIP that seamlessly integrates with SIEM systems, SOAR platforms, and endpoint security solutions can enhance the effectiveness of your cybersecurity operations by simplifying data sharing and analysis across different tools.
Flexibility
Choose a threat intelligence platform that offers flexibility to adapt to changing requirements and evolving threats. As your business grows and your network expands, the TIP should be able to scale and accommodate new requirements without significant disruptions to your cybersecurity operations.
User-Friendly Interface
Evaluate the user-friendliness of the platform’s interface to ensure ease of navigation and usability. A user-friendly TIP enables security teams to quickly analyze and act upon threat intelligence data, enhancing overall efficiency and effectiveness in threat detection and response.
Scalability
Consider the scalability of the TIP to handle growing volumes of threat intelligence data and expanding organizational needs. A scalable platform can grow with your business and accommodate increased data processing requirements without compromising performance.
Vendor Reputation and Support
Research the reputation of the TIP vendor and assess the quality of customer support offered. Choose a vendor with a track record of delivering reliable and effective threat intelligence solutions and providing responsive support to address any issues or concerns.







