What is a Smurf Attack?
A Smurf attack is a type of DDoS attack that exploits Internet Protocol (IP) and Internet Control Message Protocol to overwhelm a target system with traffic. The attack gets its name from the Smurf malware tool, which was first used to launch this type of attack.
By sending a large number of ICMP echo request (ping) packets to a network’s broadcast address, with the source address spoofed to appear as the target’s IP, the attacker can amplify the volume of traffic hitting the target.
This flood of traffic can overwhelm the target system, leading to service disruptions or complete shutdowns. To understand this better, consider the analogy of making prank calls to a large number of people, all with the same return number.
Each person called tries to call back at the same time, inundating the return number with calls, rendering it unusable. In the case of Smurf attacks, the “prank call” is the ICMP echo request, the “people” are the devices on a network, and the “return number” is the victim’s IP address.
How a Smurf DDoS Attack Works?
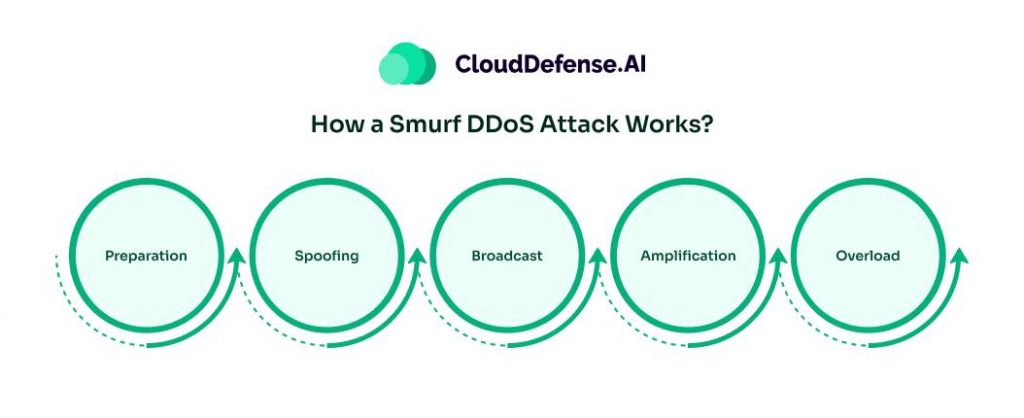
Understanding the mechanics of a Smurf attack is crucial for comprehending its potential impact. Here’s a step-by-step breakdown of how it works:
- Preparation: The attacker prepares a large number of ICMP echo request packets. These are typically standard “ping” packets used for network diagnostics.
- Spoofing: The attacker spoofs the source IP address of these packets, setting it to the IP address of the intended target. This makes the network believe that the echo request packets are coming from the target system.
- Broadcast: The attacker sends the spoofed packets to the broadcast address of a network. The broadcast address ensures that every device on the network receives the packet.
- Amplification: Each device on the network responds to the ICMP echo request by sending an echo reply to the spoofed IP address (the target). This can significantly amplify the volume of traffic directed at the target. In some cases, this amplification can be hundreds or even thousands of times the original amount of traffic sent by the attacker.
- Overload: The target system, inundated with ICMP echo replies from multiple devices, becomes overwhelmed and may experience significant slowdowns or even crash entirely. This renders the target’s services unavailable to legitimate users, achieving the attacker’s goal of a denial of service.
What is the History of Smurf Attacks?
Smurf attacks date back to the late 1990s when the Smurf malware tool was first developed. During this period, many networks were not configured to handle broadcast traffic securely, making them vulnerable to this type of attack. One of the most notable early Smurf attacks occurred in 1998, targeting a series of major corporations and causing significant disruptions. This incident brought widespread attention to the vulnerabilities associated with ICMP and broadcast addressing.
In the early days of the Internet, many networks were designed with minimal security considerations, making them easy targets for Smurf attacks. The widespread adoption of broadband and always-on Internet connections in the late 1990s and early 2000s further exacerbated the issue, as attackers could launch Smurf attacks from multiple compromised systems, increasing the scale and impact of these attacks.
The prevalence of Smurf attacks has decreased over the years due to increased awareness and improved network configurations. Modern networks often have measures in place to prevent the misuse of broadcast addresses, making them less susceptible to Smurf attacks. However, the attack technique remains a relevant part of cybersecurity history and continues to inform modern defense strategies. Understanding the history of Smurf attacks helps underscore the importance of evolving cybersecurity practices to address emerging threats.
What are the Types of Smurf Attacks?
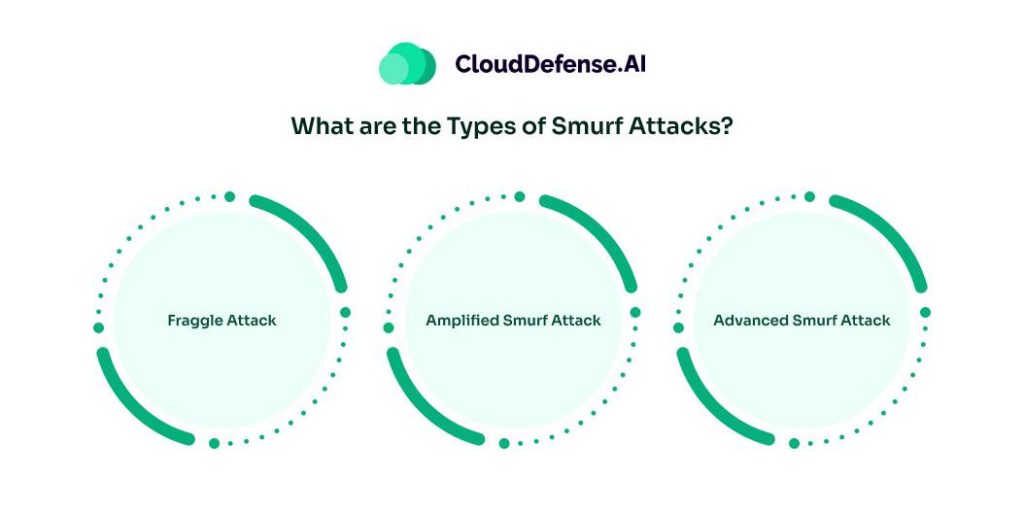
While the classic Smurf attack described above is the most well-known variant, there are a few related attack types and variations that leverage similar principles:
- Fraggle Attack: Similar to a Smurf attack, but instead of ICMP, it uses User Datagram Protocol echo packets for amplification. This variation can target different types of networks and devices. Fraggle attacks exploit the same principle of amplifying traffic through broadcast addresses, but they use UDP packets instead of ICMP packets. This can sometimes allow the attacker to bypass certain defenses that are specifically designed to mitigate ICMP-based attacks.
- Amplified Smurf Attack: This involves using multiple intermediary networks to increase the amplification effect, thereby creating an even larger traffic volume directed at the target. By leveraging several intermediary networks, the attacker can significantly enhance the scale of the attack, making it more challenging to mitigate. This type of attack can be particularly devastating if the intermediary networks are large and have a substantial number of devices that can respond to the broadcast.
- Advanced Smurf Attack: An attacker may use sophisticated techniques to evade detection and mitigation measures, making it harder to defend against. This could include techniques such as dynamically changing the source IP address to avoid rate limiting or using encrypted packets to obscure the attack traffic. Advanced Smurf attacks can be particularly challenging to defend against because they often involve a combination of different tactics and strategies to bypass existing security measures.
Defending Against Smurf Attacks
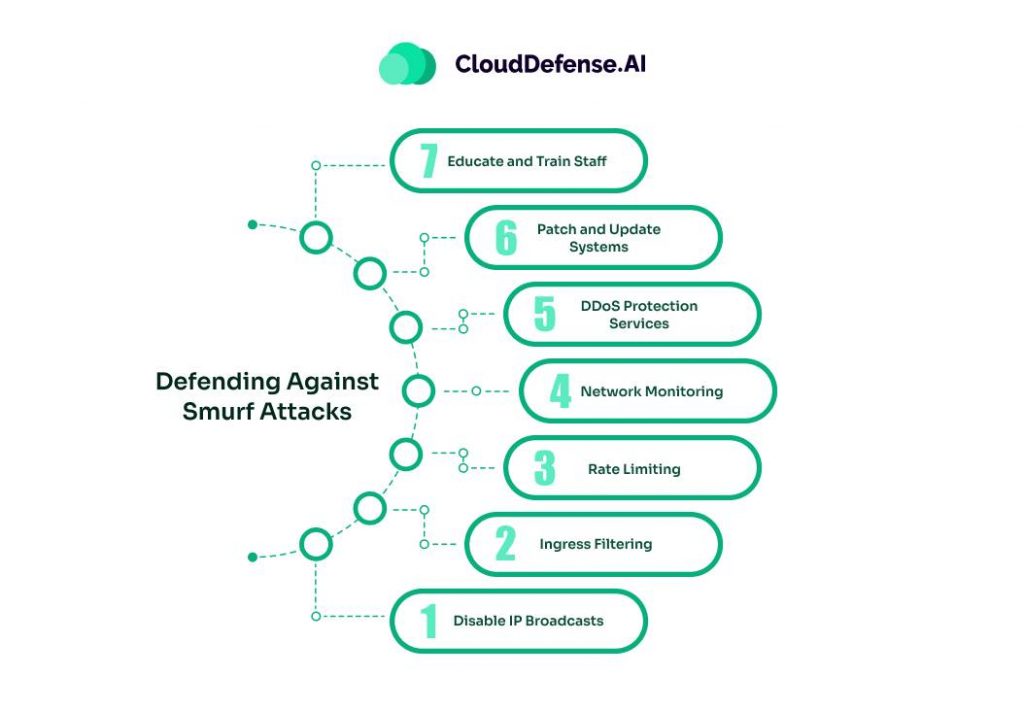
Defending against Smurf attacks requires a combination of preventive measures and responsive actions. Here are some key strategies that organizations can implement to protect against these attacks:
- Disable IP Broadcasts: Configure routers and network devices to disable IP-directed broadcasts. This prevents the network from being used as an amplification vector. By blocking directed broadcasts at the network perimeter, organizations can significantly reduce the risk of their networks being used to amplify Smurf attacks.
- Ingress Filtering: Implement ingress filtering to prevent spoofed packets from entering the network. This helps to stop the attack at its source. Ingress filtering involves verifying the source IP address of incoming packets and dropping those that appear to be spoofed. This can effectively block malicious traffic before it can reach the target.
- Rate Limiting: Use rate limiting on ICMP traffic to control the amount of echo request and reply packets that can pass through the network. By limiting the rate at which ICMP packets can be processed, organizations can mitigate the impact of a Smurf attack. Rate limiting can help to ensure that legitimate traffic can still pass through the network while reducing the volume of attack traffic.
- Network Monitoring: Regularly monitor network traffic for unusual patterns that may indicate the onset of an attack. Early detection can help in mitigating the impact. Network monitoring tools can provide real-time visibility into network traffic, allowing organizations to quickly identify and respond to potential threats. By analyzing traffic patterns, security teams can detect anomalies that may indicate a Smurf attack in progress.
- DDoS Protection Services: Employ DDoS protection services that can detect and mitigate Smurf attacks in real-time. These services can absorb and deflect malicious traffic away from the target. DDoS protection services often use a combination of techniques, such as traffic scrubbing and rate limiting, to mitigate the impact of large-scale DDoS attacks. By offloading attack traffic to a third-party service, organizations can ensure that their critical infrastructure remains available during an attack.
- Patch and Update Systems: Regularly update and patch network devices and systems to ensure they are not vulnerable to known exploits. Keeping software and firmware up to date can help to close security gaps that could be exploited by attackers.
- Educate and Train Staff: Ensure that IT staff and network administrators are aware of the latest DDoS attack techniques and best practices for defending against them. Regular training and awareness programs can help to ensure that security teams are prepared to respond to Smurf attacks and other types of DDoS attacks.
Conclusion
Smurf attacks may be less common today, but they remain a critical lesson in cybersecurity. By exploiting ICMP and broadcast addressing, these attacks can overwhelm networks, causing severe disruptions. Variants like Fraggle and amplified Smurf attacks show how attackers refine their tactics.
Organizations can mitigate risks by disabling IP broadcasts, filtering spoofed traffic, enforcing rate limits, and using DDoS protection. Regular monitoring and security training further strengthen defenses. While attack methods evolve, understanding Smurf attacks helps in combating modern threats. Proactive security measures ensure resilience against network-based DDoS attacks, keeping digital infrastructures safe from disruption.







