Cyber attackers are reinventing themselves every day to find new techniques that can help them to exploit a system. The highly increasing number of data breaches and other forms of cyber-attacks are a result of companies not preparing themselves to counter these new methods employed by cybercriminals.
One such widely used attack method is known as a port scan. What is a port scan? It is a common technique used by hackers to determine vulnerable ports in a system. They then use it to access the infrastructure to harm it. Port scans also help a threat actor to get information on the type of cybersecurity detail the victim organization uses to protect itself.
Keep reading to learn more about what are port scans and how you can protect your company from this vulnerability.
What is a Port Scan?
Hackers use port scanning attacks to identify open ports in a network. These open ports work as unlocked doors that they further exploit and gain access to a company’s system. Threat actors use port scanning tools to carry out these attacks, and they also allow them to determine whether the company uses a firewall to protect its network.
Port scanning in cybersecurity also helps enterprises detect any vulnerable ports by mimicking a cyber attacker. This helps in taking care of any open ports and mitigating the risk of future attacks. Open port scanning allows a person to determine who owns a network, what services are running on it, and if random logins are allowed.
Different Types of Port Checkers or Scanners
There are several types of port scanning techniques. The most commonly used ones are:
- XMAS Scans: These scans are used to send several information packets that help in determining whether a port is open or not. Packets are bounced back from closed ports. Packets that do not come back help the scanner to know that the port is open.
- SYN Scans: SYN or half-open port scans allow the detection of an open port without establishing a connection with it. These are the most popular port scans out there, being very sneaky and effective.
- Ping Scans: Ping scans are used to verify whether a network packet can reach an IP problem-free.
- TCP-Connect Scans: These scans are used to fulfill a TCP handshake.
- Vanilla Scans: A very effective port scan, that targets all ports in a system. This scanning technique uses SYN-ACK packets to establish a full connection with a system. However, full-port scans are easily detected by firewalls even if they are very effective.
How does a Port Scan Work?
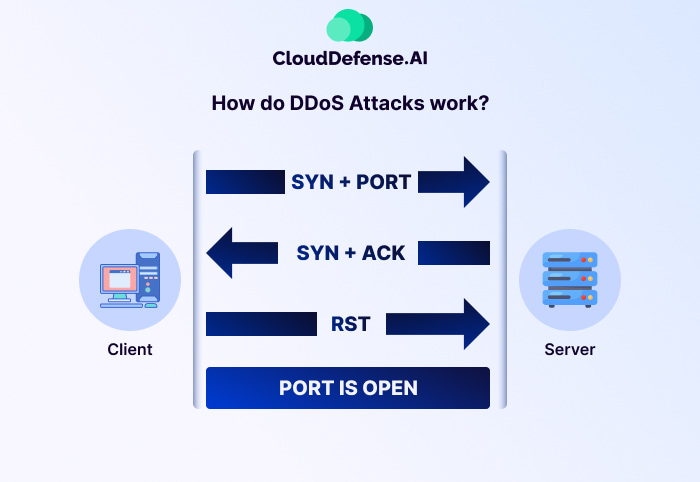
Different ports have different functionalities. In general, all ports are labeled from the number ‘0’ to ‘65535’. Out of these, ports between the numbers ‘0’ to ‘1023’ are the most widely used ones. These well-known ports are used by common Internet Services. A standard reference for which port is used by which service is popularly known as, Internet Assigned Numbers Authority.
A port scan is a tool that was created to detect weaknesses in this port and to strengthen the network. However, hackers turned it into a recon method that they use before launching a cyber attack. You may already know how port scans send packets toward a port to determine whether it is open or not. While some port scanning software targets the most common ports in a system, a more advanced port scanner would scan all 65536 ports.
How Do Cybercriminals Use Port Scanning as an Attack Method?
Port scanning is commonly used by all cyber attackers as a preparatory method. It provides them with essential information about a system and what software is being used. The type of data that can be obtained using port scan attacks include:
- If the port is open or not.
- If a firewall is being used to secure the network.
- If there is any vulnerable software that the company is using.
- If there is a way to log in without having your identity known.
- How many machines are only?
- Owner of the network
- If data can be accessed without any privileges required.
Information like this can help a cyber attacker to prepare themselves for the main attack when they know what machine they are running and the type of software the company uses. They can then concentrate on finding vulnerabilities in those software to gain access to the primary system.
Port Scanning vs. Network Scanning
Network scanning involves identifying active hosts on a network and mapping their IP addresses, providing a broad overview of the network topology. It focuses on discovering the availability and responsiveness of hosts using protocols like ARP and ICMP. Network scanning, also known as host discovery, serves as the initial step in reconnaissance, identifying potential targets for further analysis.
In contrast, port scanning digs deeper into probing specific ports on active hosts to identify open, closed, or filtered ports and the services running on them. While network scanning lays the groundwork by identifying potential targets, port scanning provides detailed information about the services and potential vulnerabilities of those targets.
How to Prevent Port Scan Attacks?
To prevent port scan attacks effectively, businesses and individuals can implement several protective measures:
Firewall Implementation
Deploying a strong firewall is essential to protecting networks against unauthorized access. A firewall scrutinizes incoming and outgoing traffic based on predefined rules, effectively blocking port scan attempts before they can exploit vulnerabilities.
TCP Wrapper Configuration
Utilize TCP wrappers to control access to network services based on IP addresses and domain names. By configuring TCP wrappers, administrators can permit or deny connections, enhancing control over network accessibility and thwarting unauthorized port scans.
Regular Network Audits
Conduct routine network audits using port scanners or checkers to identify any unnecessary open ports. Closing unused ports minimizes the attack surface, reducing the likelihood of successful port scans and potential exploitation by cybercriminals.
Threat Intelligence Integration
Stay updated with the latest threat intelligence to understand evolving attack techniques and vulnerabilities. Incorporate this intelligence into security measures to proactively mitigate potential risks associated with port scanning and other cyber threats.
Monitoring and Alerting Systems
Implement monitoring and alerting systems capable of detecting suspicious port scanning activities in real-time. Automated alerts can notify administrators of unauthorized access attempts, enabling response and mitigation actions.
Utilization of Security Tools
Employ specialized security tools such as IP scanning, Nmap, and Netcat to actively monitor and defend against port scan attacks. These tools provide insights into network vulnerabilities and aid in strengthening defenses against potential intrusions.
Security Awareness Training
Educate employees and users about the risks associated with port scanning and other cyber threats. Promote cybersecurity best practices, including the importance of maintaining strong passwords, identifying phishing attempts, and reporting suspicious activities promptly.
Prevent Port Scan Attacks with CloudDefense.AI
CloudDefense.AI is the world’s leading CNAPP that provides you with a state-of-the-art live threat detection and response tool that can be used from a single platform. An all-around solution to all cyber threats to your system, CloudDefense.AI uses the UEBA model to provide effective threat detection and mitigation features.
Out of the many powerful security capabilities, it is also bundled with open port scan detectors and other useful features that can help secure your vulnerable ports. With our reconnaissance detection feature, you can easily detect any recon attempts in real-time allowing you to prepare yourself for an impending attack.
Further, you can use our dashboard to carry out a risk assessment of your vulnerable ports and prioritize urgent mitigations using our robust mitigation techniques. CloudDefense.AI doesn’t only safeguard your ports, but your complete IT infrastructure as a whole.
FAQ
Here you can find a few queries regarding port scans.
What is a port scanner attack?
A port scanner attack is a method used by hackers to probe a network for open ports, identifying services running on them and potential vulnerabilities for exploitation.
What ports do hackers use?
Hackers commonly target well-known ports like 80 (HTTP), 443 (HTTPS), 21 (FTP), 22 (SSH), and 23 (Telnet), as well as unassigned or less-monitored ports, to exploit vulnerabilities and gain unauthorized access to systems.
What are some common open port numbers?
Common open port numbers include 80 (HTTP), 443 (HTTPS), 21 (FTP), 22 (SSH), 25 (SMTP), 53 (DNS), 110 (POP3), 143 (IMAP), 3389 (Remote Desktop), and 3306 (MySQL). These ports host various services accessible over networks.
Conclusion
Port scans are a very innovative method adopted by cyber attackers to sneakily get information on a victim’s system before proceeding to attack them. As we move to more complex systems, company owners need to be aware of such methods and invest in equipment to protect themselves.
With security being prioritized everywhere around the world, mainly due to compliance requirements, companies are racing to buy different cybersecurity products from different vendors. CloudDefense.AI has taken a resources-saving approach by allowing companies to deal with all cyber malice through one single platform. Cybersecurity can never be so easy, book a free demo now!







