What is CVSS?
The Common Vulnerability Scoring System (CVSS) is a standardized method for assessing the severity of security vulnerabilities in software and systems. It assigns each vulnerability a score from 0 to 10, with higher scores indicating greater risk.
Using CVSS, organizations can effectively prioritize threats, ensuring that the most dangerous flaws are addressed first. CVSS is designed to be vendor-agnostic and repeatable, allowing security teams to compare vulnerabilities across different applications and platforms.
It evaluates multiple factors, including how a vulnerability can be exploited, the level of access required, and its potential impact on confidentiality, integrity, and availability. By integrating CVSS into their security strategy, businesses can simplify risk management, strengthen defenses, and reduce overall exposure to cyber threats.
How does CVSS Work?

The Common Vulnerability Scoring System (CVSS) calculates a score by considering several interconnected factors that assess the severity of a vulnerability. While tools and calculators often handle the heavy lifting for users, understanding the components involved can help security professionals better interpret the scores and prioritize risks. Here’s a breakdown of how CVSS is calculated and what goes into the process.
To generate a CVSS score, multiple factors are evaluated and divided into three metric groups:
Base Metrics
These represent the fundamental characteristics of a vulnerability, which do not change over time or across environments.
1. Attack Vector (AV): Measures how the vulnerability can be exploited. Values include:
- Network: Accessible remotely over a network (highest severity).
- Adjacent: Requires access to the same shared physical or logical network.
- Local: Exploitable only by having local access to the system.
- Physical: Requires direct physical interaction with the system (lowest severity).
2. Attack Complexity (AC): Evaluates how difficult it is to exploit the vulnerability.
- Low: Exploitation is straightforward and requires minimal effort (higher score).
- High: Exploitation depends on specific conditions that are hard to meet.
3. Privileges Required (PR): Determines the level of access the attacker needs to exploit the vulnerability.
- None: No privileges required (highest impact).
- Low: Basic user access is required.
- High: Administrative or highly privileged access required.
4. User Interaction (UI): Assesses whether exploiting the vulnerability requires user action.
- None: No user interaction needed (higher score).
- Required: Exploitation relies on a user performing a specific action.
5. Scope (S): Measures whether the vulnerability impacts multiple security boundaries.
- Unchanged: The impact remains confined to the same security authority.
- Changed: The vulnerability affects resources outside the initial scope (higher impact).
6. Confidentiality (C): Examines the extent of unauthorized access to sensitive information.
- None: No loss of confidentiality.
- Low: Partial information exposure.
- High: Complete exposure of sensitive data.
7. Integrity (I): Evaluates the potential for unauthorized modification or deletion of data.
- None: No impact on data integrity.
- Low: Partial modification possible.
- High: Total compromise of integrity.
8. Availability (A): Assesses the likelihood of denying access to authorized users.
- None: No disruption.
- Low: Reduced performance or partial disruptions.
- High: Complete service or resource denial.
Temporal Metrics
These metrics adjust the Base score by considering factors that may change over time:
- Exploit Code Maturity: Whether exploit code is publicly available and how reliable it is.
- Remediation Level: Whether patches or workarounds are available.
- Report Confidence: How much confidence exists in the vulnerability report or analysis?
Environmental Metrics
These are customizable based on the organization’s specific context, allowing them to adapt the CVSS score to their unique environment:
- Security Requirements: The importance of confidentiality, integrity, and availability for the specific environment.
- Modified Base Metrics: Adjustments to Base metrics reflecting specific environmental factors.
The Scoring Process
CVSS scores are calculated using a formula that combines these metrics. Each metric contributes a specific weight to the final score, which ranges from 0.0 (no severity) to 10.0 (critical severity). While the formula is quite complex, it essentially considers:
- The ease of exploitation (Attack Vector, Complexity, Privileges Required, User Interaction).
- The potential impact on confidentiality, integrity, and availability.
- Adjustments based on time-sensitive or environmental factors.
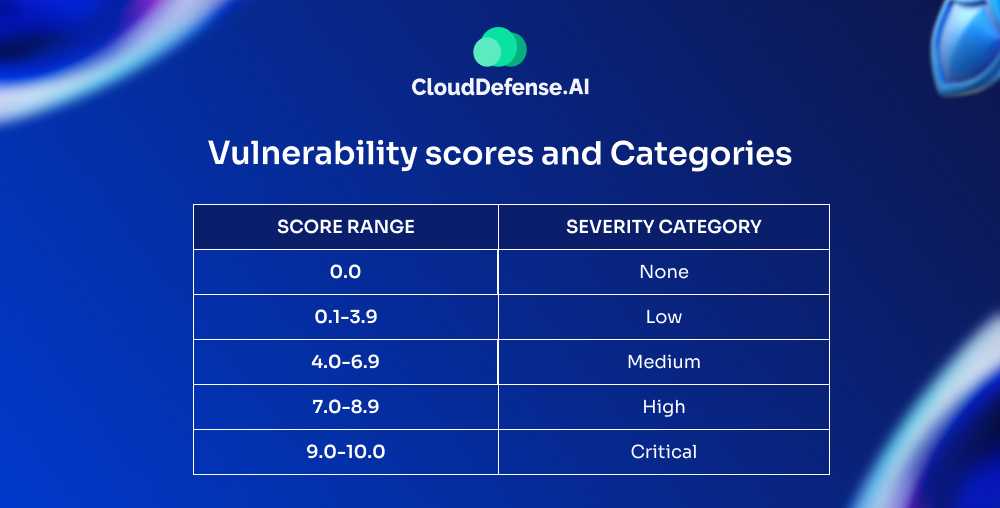
CVSS Scores and Ratings
CVSS scores range from 0 to 10, with 10 being the most severe. To make these scores more meaningful, they’re grouped into qualitative ratings:
Let’s explore how CVSS scores work and what they mean in the real world:
CVSS uses a 0 to 10 scale to rate how serious a security flaw is. Think of it like a danger meter – the higher the number, the bigger the potential problem. Here’s how it breaks down:
Low Severity (0 to 3.9)
These are your minor issues. They’re not nothing, but they’re not likely to keep you up at night, either.
For example, imagine a flaw that leaks only a tiny bit of non-sensitive information. You’d need admin access to use it, so that it might get a score of around 2.0. It’s there, but it’s not a significant worry.
Medium Severity (4.0 to 6.9)
Now, we’re getting into more common problems. These aren’t catastrophic, but they’re definitely worth fixing when you can.
Picture a cross-site scripting bug that could let someone mess with your website. It’s easier to exploit than the low-severity stuff, but it’s not going to bring down your whole system. That might score around 5.5.
High Severity (7.0 to 8.9)
This is where things get serious. These flaws could give attackers significant access or control over your systems.
If there’s a vulnerability that could let an attacker get unauthorized admin access to a key server, you’re looking at a score in this range.
Critical Severity (9.0 to 10)
These are the worst of the worst. We’re talking about vulnerabilities that could lead to massive data breaches, system shutdowns, or complete takeovers. A widespread ransomware exploit that could lock up systems across an entire organization might receive a score of 9.5.
Imagine a flaw that allows attackers to quickly spread ransomware across your entire network, locking up all your data. This thing might score a 9.5 or higher.
Remember, these scores are guidelines. In the real world, you need to consider how each vulnerability applies to your specific setup. However, CVSS gives you a solid starting point for determining where to focus your security efforts.
CVSS Calculators
Several organizations offer free CVSS calculators, including:
- FIRST (Forum of Incident Response and Security Teams)
- NIST (National Institute of Standards and Technology)
- Cisco
The calculator breaks down the scoring process into three primary categories: Base, Temporal, and Environmental. Which we have discussed before
Benefits of using CVSS
The Common Vulnerability Scoring System (CVSS) has become a vital tool for organizations worldwide, providing a standardized way to evaluate the severity of security vulnerabilities. It eliminates confusion and brings clarity to vulnerability management processes. Here’s why CVSS is so beneficial:
Standardized Scoring System
Before CVSS, every company used its method to classify vulnerabilities, creating confusion and inefficiencies. CVSS gives everyone a common language to discuss and prioritize security issues. With its universal scale (0 to 10), IT teams can objectively assess and compare vulnerabilities across platforms and tools.
Transparency and Trust
One of CVSS’s key strengths is its openness. The scoring methodology is public, meaning anyone can see how scores are calculated. This transparency builds trust among teams, vendors, and customers and ensures that the process is fair and consistent.
Better Prioritization of Vulnerabilities
Not all vulnerabilities pose the same level of risk, and CVSS helps teams identify the most critical issues to address first. By assigning scores based on factors like attack complexity, required privileges, and potential impact, CVSS provides clear insights into what needs immediate attention.
Compliance with Industry Standards
Many security frameworks and compliance standards (e.g., PCI DSS and HIPAA) use CVSS scores to determine acceptable levels of risk. By adopting CVSS, organizations can more easily ensure they align with industry regulations and meet audit requirements.
Enhanced Communication
When everyone—from developers to executives—uses the same scoring system, conversations about vulnerabilities become much more straightforward. CVSS eliminates misunderstandings and enables cross-functional teams to collaborate effectively on risk mitigation strategies.
Supports Proactive Security Measures
CVSS isn’t just for fixing vulnerabilities after they’re found. Developers and security teams can use it during the software development lifecycle to identify and address high-risk issues earlier, reducing the cost and effort of patching flaws post-deployment.
Cost and Time Efficiency
With a clear understanding of which vulnerabilities are most severe, companies can focus their resources where they’re needed most. This targeted approach reduces unnecessary efforts on low-risk issues, saving both time and money.
Interoperability Across Tools
CVSS scores are widely supported by vulnerability management tools, making it easier to integrate into existing workflows. This ensures that CVSS fits smoothly into security operations without requiring additional overhead.
Builds a Stronger Security Posture
By using CVSS, organizations can make smarter decisions, allocate resources more effectively, and maintain a consistent approach to vulnerability management. This leads to reduced exposure to cyber risks and a more stronger overall security posture.
Cybersecurity threats are becoming increasingly complex, demanding more effective and efficient ways to handle them. CVSS helps organizations cut through the noise by providing a clear, structured, and standardized approach to evaluating vulnerabilities. With this framework in place, teams can prioritize threats based on severity, ensuring they focus on the most critical issues first. In other words, CVSS enables teams to work smarter, not harder when addressing vulnerabilities.
Limitations of CVSS
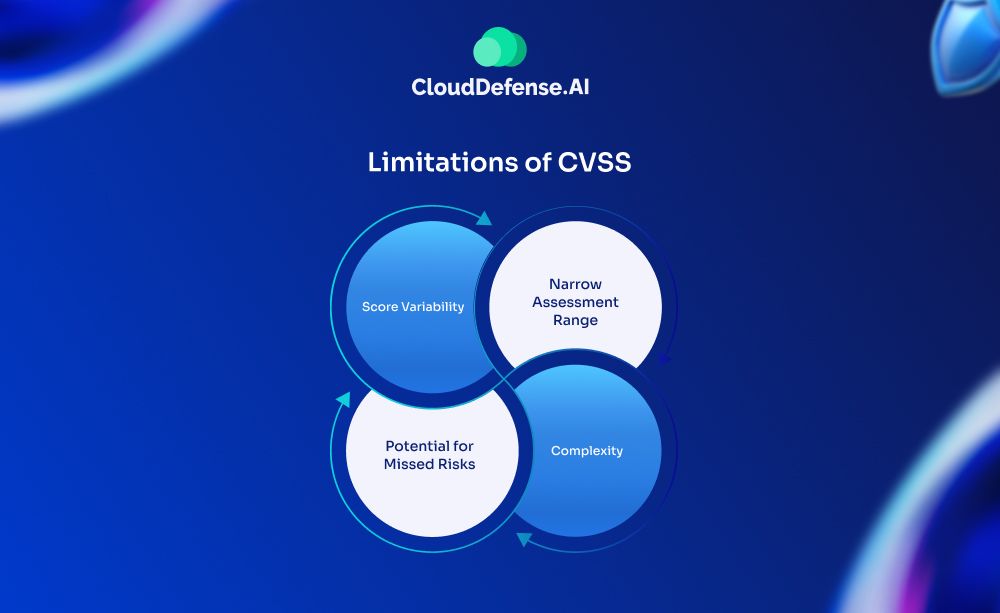
CVSS is a widely used tool for evaluating vulnerabilities. However, like any system, it has limitations. While CVSS provides a helpful starting point for prioritizing risks, relying solely on it can lead to oversimplified or inconsistent assessments. In this section, we’ll explore some of its key drawbacks and why it’s essential to integrate it into a broader, more nuanced approach to vulnerability management.
Score Variability
Look, scoring vulnerabilities isn’t an exact science. Different people might look at the same problem and come up with different scores. It’s like asking a bunch of people to rate a movie—you’ll get a range of opinions. With CVSS, the person doing the scoring might focus on different aspects depending on their experience or what they think is essential, so that you can end up with some inconsistency.
Narrow Assessment Range
Here’s the thing – CVSS doesn’t tell the whole story. It’s good at saying how bad a vulnerability is in general, but it doesn’t consider your specific situation. It doesn’t know if the vulnerable system is critical to your business or if you’ve got other security measures in place. It’s like judging a car just by its top speed without considering fuel efficiency or safety features.
Complexity
CVSS isn’t precisely straightforward. To use it properly, you need to understand all the different factors that go into a score. It’s not rocket science, but it’s not something you can pick up in five minutes, either. This complexity can be a barrier for some people or organizations.
Potential for Missed Risks
Many teams rely heavily on public databases of CVSS scores when deciding what to fix first. While that’s not a bad start, it’s not enough. These scores don’t always reflect real-world risks or available fixes. It’s like reading only the headlines without digging into the whole story—you might miss some crucial details.
In a nutshell, CVSS is a good tool, but it’s not perfect. It’s essential to use it as part of a broader security strategy, not as the be-all and end-all of vulnerability management. Remember, it’s just one piece of the puzzle when it comes to keeping your systems secure.
Final Words
CVSS is a solid tool in our cybersecurity toolbox. It provides a common language for discussing vulnerabilities, which is huge when trying to keep systems safe across different teams or even different companies. Sure, it has its limitations, but what doesn’t?
The key is using CVSS smartly. It’s not about blindly following scores but using them as a starting point. Combine CVSS with your knowledge of your systems, and you’ve got a powerful way to prioritize what needs fixing.
CVSS helps us tackle the chaos of cybersecurity. And in this digital wild west, that’s something to be thankful for.







