What is a Container Registry?
A Container Registry is a centralized repository that stores, manages, and distributes container images for containerized applications. It provides a secure, scalable platform for developers and organizations to manage containerized workloads efficiently.
Container registries support version control, access control, and automated vulnerability scanning, integrating seamlessly with container orchestration tools like Kubernetes and Docker for smooth deployments across cloud and on-premises environments.
While a registry doesn’t run containers, it acts as a central hub, storing essential application components. It streamlines DevOps workflows, enhances security, and simplifies application distribution by enabling teams to:
- Store images efficiently, organizing them by project or version.
- Manage access, track usage, and update images securely.
- Distribute images across teams or organizations.
- Deploy images directly to orchestration platforms for seamless application deployment.
A container registry is an essential tool for developers to manage containers efficiently and scale applications. It can house unlimited images.
How Does a Container Registry Work?
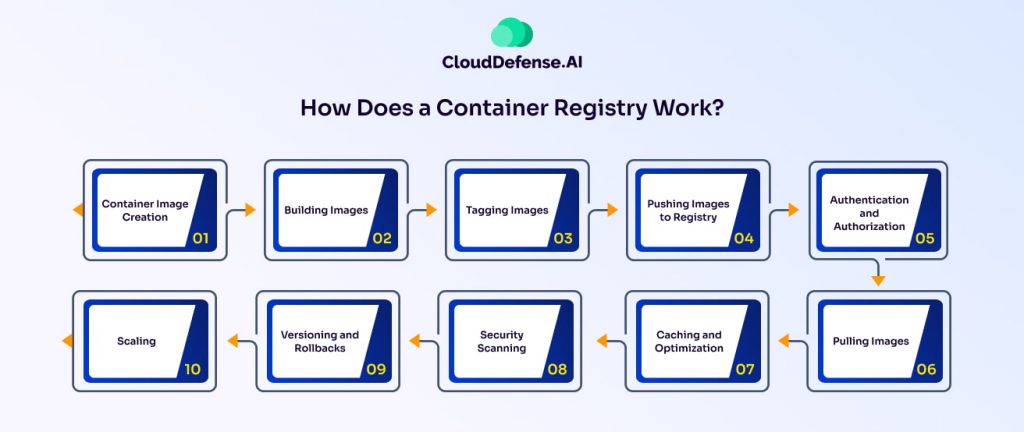
Now that we understand what a container registry is, let’s explore how it functions behind the scenes. A container registry acts as a central hub for storing, managing, and distributing container images, ensuring seamless development and deployment processes. Here’s how it works:
- Container Image Creation: Developers define a Dockerfile (or a similar configuration file) that specifies the base image, dependencies, configurations, and the application itself.
- Building Images: Using the Dockerfile, the container image is built by layering dependencies and application code onto a base image, creating a self-sufficient, executable image.
- Tagging Images: Each image is assigned a version tag or identifier, making it easier to track different application versions and maintain consistency across environments.
- Pushing Images to the Registry: Once built and tagged, the container image is pushed to a container registry such as Docker Hub, Google Container Registry, or AWS Elastic Container Registry (ECR). The registry organizes and manages these images for easy access.
- Authentication and Authorization: To maintain security, registries require authentication, ensuring that only authorized users can push or pull images. This prevents unauthorized access and protects sensitive applications.
- Pulling Images for Deployment: When deploying an application, the container runtime (e.g., Docker, Kubernetes) pulls the necessary container images from the registry, ensuring that the correct version is used in production.
- Caching and Optimization: To improve performance, container registries use caching mechanisms. They retrieve frequently used images faster by downloading only updated layers instead of the entire image.
- Security Scanning: Many registries offer security scanning features to detect vulnerabilities within container images. This helps enforce security policies before deployment, reducing risks in production environments.
- Versioning and Rollbacks: Registries support image versioning, allowing developers to roll back to previous versions if needed. This ensures stability and quick recovery in case of issues with newer versions.
- Scaling for Growth: As organizations scale their containerized applications, the registry expands effortlessly, managing an increasing number of images while ensuring efficient storage and retrieval.
Understanding these processes enables developers and organizations to enhance the benefits of container registries for efficient image management, improved security, and optimized deployments in containerized environments.
Types of Container Registries
Choosing the proper container registry depends on accessibility, security needs, deployment preferences, and integration capabilities. Container registries come in various types, each catering to different organizational and development requirements. Below are the most common types of container registries:
Public vs. Private Registries
- Public Container Registries: Public registries are open to everyone, allowing developers to push and pull container images freely. These are commonly used for open-source projects and publicly available container images. However, due to their openness, they pose potential security and access control risks.
Example: Docker Hub
- Private Container Registries: Private registries require authentication and access control, making them ideal for organizations that need secure storage for proprietary or sensitive images. They implement encryption, role-based access control (RBAC), and other security measures to protect stored images.
Examples: Amazon Elastic Container Registry (ECR), Google Container Registry (GCR), Azure Container Registry (ACR)
Open Source vs. Proprietary Registries
- Open-Source Registries: Open-source container registries are community-driven and can be self-hosted. They provide organizations with greater flexibility and customization. They allow complete control over configurations and modifications, making them ideal for those who prefer transparency and extensibility.
Example: Harbor
- Proprietary Registries: Proprietary registries are commercially developed solutions that are not open-source. While some offer free usage tiers, they are generally managed services that require organizations to rely on the provider’s infrastructure. Proprietary registries often offer advanced features, support, and an intuitive interface, making them a preferred choice for businesses that prioritize ease of use and reliability.
Example: Quay.io
Hybrid Registries
- Hybrid registries offer the best of both worlds for organizations seeking a combination of public and private registries., These registries integrate seamlessly with public and private repositories, offering efficient image management across on-premises and cloud environments.
Example: JFrog Artifactory
Choosing the Right Container Registry
Selecting the best container registry depends on your specific needs and priorities. Consider the following factors:
- Public vs. Private: Do you need a public registry for open-source sharing or a private one for secure, controlled access?
- Managed vs. Self-Hosted: Do you prefer a managed service for convenience or a self-hosted registry for greater control?
- Features: Does your registry need vulnerability scanning, role-based access control (RBAC), or integration with DevOps tools?
- Cost: How much are you willing to invest in a registry solution that meets your security and operational requirements?
When you consider these factors, you can select a container registry that perfectly complements your development workflow, enhances your security policies, and meets your scalability needs.
Benefits of Container Registry
A container registry plays a crucial role in modern application development by providing a centralized, secure, and efficient way to manage container images. Whether you’re working on a small project or managing enterprise-scale deployments, a container registry enhances security, collaboration, and automation. Here are the key benefits:
- Centralized Image Management: A container registry is a single, organized repository for storing, managing, and distributing container images. It streamlines development and deployment processes, making it easier for teams to collaborate and share containerized applications efficiently.
- Version Control for Seamless Tracking: You won’t have to struggle to find the correct image version anymore! Registries maintain detailed version histories, allowing teams to track, revert, and deploy specific versions as needed. This ensures consistency across different environments.
- Enhanced Security and Access Control: Container registries provide built-in security measures, including authentication, access control, and vulnerability scanning. These measures help prevent unauthorized access and ensure that only verified, secure images are deployed.
- Consistent and Reliable Deployments: Registry registries act as a single source of truth for container images, eliminating inconsistencies between development, testing, and production environments. This reduces deployment failures and eliminates the dreaded “it works on my machine” problem.
- Improved Collaboration Across Teams: Developers can easily share and reuse pre-built images, accelerating development cycles and promoting standardization across teams. This boosts collaboration and reduces redundant work.
- Scalability: As your container ecosystem grows, the registry scales alongside it, adapting effortlessly to increased storage needs without performance degradation. This ensures smooth image management for projects of all sizes.
- Integration with CI/CD Pipelines: Container registries integrate seamlessly with continuous integration and continuous deployment (CI/CD) pipelines. Developers can automatically push new or updated images to the registry, ensuring that the latest versions are always available for deployment.
- Cross-Platform Compatibility: Registries support cross-platform deployments, allowing organizations to use the same container images across multiple infrastructure providers and cloud environments. This simplifies multi-cloud and hybrid-cloud deployments.
- Cost Optimization and Resource Efficiency: Public registries (e.g., Docker Hub) provide cost-effective storage for smaller projects. Additionally, efficient image management helps reduce infrastructure costs and optimize resource utilization, ensuring that only necessary images are stored and used.
- Enhanced Visibility and Governance: Container registries provide detailed logs, audit trails, and analytics, enabling organizations to track image usage, monitor trends, and enforce governance policies. This improves overall security and operational control.
What to Look for in a Container Registry?
Choosing the proper container registry can be daunting, especially with so many options available. Whether you’re a startup looking for a cost-effective solution or an enterprise needing robust security, the correct registry can make a huge difference in your containerized workflows.
Here’s a checklist of key factors to consider when selecting a container registry:
Security First
Security should be a top priority when managing container images. A good registry should offer:
- Authentication & Authorization: Role-based access control (RBAC) to ensure only authorized users can push or pull images.
- Encryption: Protection for images at rest and in transit to prevent data breaches.
- Vulnerability Scanning: Automated scanning to detect security flaws before deployment.
- Audit Logging: Detailed logs to track user activity and flag potential security risks.
Ease of Use & Developer Experience
A container registry should be developer-friendly and integrate smoothly with your workflow. Look for:
- Intuitive User Interface: A clean and easy-to-navigate dashboard for managing images.
- CI/CD Integration: Smooth connection with CI/CD pipelines for automated image management.
- Platform Compatibility: Support for Docker, Kubernetes, and other container ecosystems.
- Comprehensive Documentation & Support: Reliable guides, tutorials, and responsive customer support.
Scalability & Performance
As your applications scale, your registry should keep up without performance issues. Consider:
- High Availability: Ensures reliable access to images even during peak loads.
- Geographic Distribution: Reduces latency with multi-region storage options.
- Flexible Scalability: Can handle increasing image volume and concurrent users.
Cost Considerations
Understanding the pricing structure helps you avoid unexpected expenses. Evaluate:
- Pricing Model: Some registries charge per image, per user, or offer flat-rate plans.
- Additional Costs: Look out for extra charges on storage, bandwidth, or premium support services.
Making the Right Choice
Selecting a container registry isn’t just about storage—it’s about security, performance, and efficiency. Whether you opt for a public registry for open-source projects or a private registry for enhanced control, ensure it aligns with your DevOps strategy.
Conclusion
Containerization has taken the development world by storm, and container registries are the unsung heroes, ensuring order and efficiency. From securing your images to streamlining workflows, they offer a plethora of benefits.
We’ve explored the what, why, and how of these registries, dissecting their benefits and key features. Remember, the “best” registry doesn’t exist in a vacuum; it’s the one that aligns with your needs and empowers your workflow.







