What is a CNAPP?
A cloud-native application protection platform (CNAPP) is a complete cloud security and compliance solution that helps your team develop, deploy, and run cloud-native applications in a fully secured cloud environment.
It is a cloud-native security solution that combines CSPM, CIEM, CWPP, and elements of KSPM and CI/CD security into a unified solution to secure applications through the entire CI/CD application lifecycle.
In addition to cloud security, CNAPPs also integrate application security solutions such as SAST, DAST, and SCA, ensuring comprehensive protection across both cloud infrastructure and the application layer.
The critical roles of CNAPP in cloud security include:
- Streamline scanning processes
- Ensure comprehensive code-to-cloud security
- Enhance threat detection
- Consolidate compliance reporting into a single solution
- Reduces human error associated with managing disparate tools
- Accelerate response times to threats
Since CNAPP acts as an all-in-one solution, it gives DevOps and cloud infrastructure teams the crucial visibility needed to oversee every aspect of application development, securing every layer of your tech stack.
Gartner’s Definition of CNAPP
“Cloud-native application protection platforms (CNAPPs) offer a unified, comprehensive suite of security and compliance tools aimed at safeguarding both cloud-native infrastructure and applications. These platforms integrate proactive and reactive security measures, such as artifact scanning, security guardrails, compliance and configuration management, risk detection and prioritization, and behavioral analytics. By delivering visibility, governance, and control throughout the entire development lifecycle—from code creation to production—CNAPPs ensure full-spectrum security coverage.”
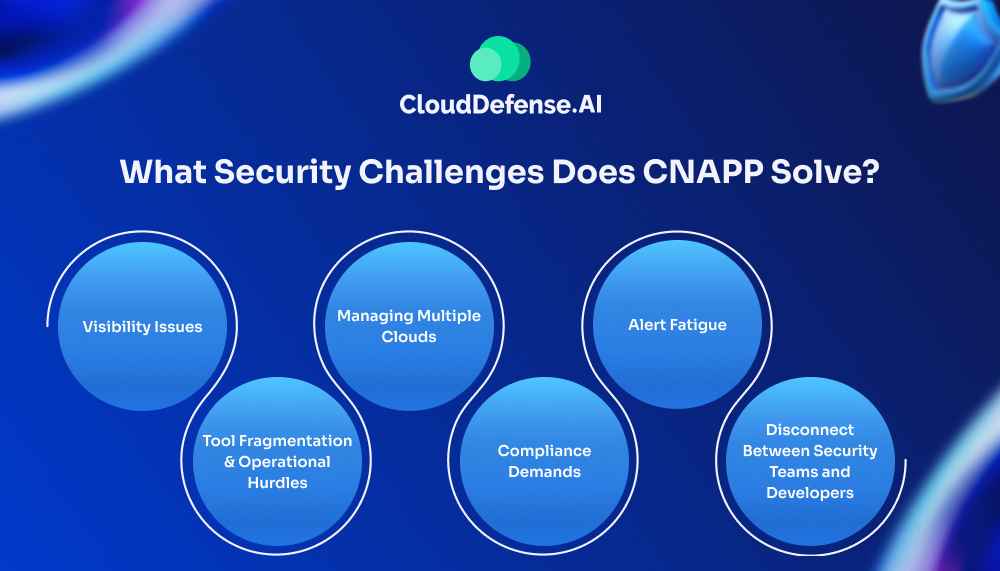
What Security Challenges Does CNAPP Solve?
The cloud has brought a new wave of security risks. Cloud environments are inherently complex and dynamic. Organizations can rapidly add resources—be it virtual machines, serverless functions, or containers. This constant influx of new services creates a terrain that’s tough to secure as it evolves almost in real-time.
Moreover, the cloud makes it easy to expose resources to the internet with just a click, increasing the risk of misconfigurations. With the variety of services and configurations available, organizations need a strong solution to maintain security amid these changes. The complexity also opens up new attack vectors, necessitating a tailored threat detection and response strategy for cloud-native threats. Here are some key issues:
Visibility Issues
Many organizations use security tools with agents to monitor their cloud infrastructure. However, relying on these agents can create blind spots—resources without the agent remain unmonitored. These gaps in visibility can leave critical vulnerabilities unnoticed, potentially leading to security breaches.
Tool Fragmentation and Operational Hurdles
Many organizations use separate security tools for different functions, like vulnerability management or Kubernetes security. While these tools have their strengths, they can create silos and complicate operations, as each one requires its own expertise and processes. Such a level of fragmentation often means manually correlating risks from different tools, adding to the operational burden. CNAPP integrates various security functions into a single platform, reducing complexity and streamlining security management.
Managing Multiple Clouds
As organizations increasingly adopt multi-cloud strategies, managing security across different cloud providers becomes more complex. They all have their own tools, rules, and settings, making it challenging to maintain a sound security posture while monitoring and managing them on assorted platforms.
Compliance Demands
Figuring out compliance stuff in the cloud is tough since the rules and standards are always changing. Making sure all your cloud resources hit the right compliance marks can be a struggle, especially when companies grow and roll out new services. If you don’t stick to those compliance rules, it could lead to legal trouble and hurt the organization’s reputation.
Alert Fatigue
Standalone security tools often lack context, which can make it difficult to assess the severity of risks. For instance, a tool might flag a vulnerable machine but won’t necessarily indicate whether it’s exposed to the internet or has high privileges. This lack of context leads to a flood of alerts, many of which may not be critical, causing alert fatigue and making it hard for teams to prioritize real threats. CNAPP provides contextual insights, helping teams focus on what truly matters.
Disconnect Between Security Teams and Developers
A common challenge is the disconnect between security teams and developers. Security teams are tasked with safeguarding the cloud environment, while developers are responsible for deploying resources. This divide can slow down innovation and make it harder for developers to see and address risks associated with their resources. CNAPP helps bridge this gap by providing developers with actionable insights and integrating security measures into the development process, enabling faster, more secure deployments.
“Alarmingly, a staggering 45% of data breaches now originate from cloud environments. Even more concerning, a whopping 69% of organizations have confessed to suffering data breaches or exposures because of flawed multi-cloud security setups. The scale of vulnerability is staggering—are you prepared to face it?”
– IBM Cost of Data Breach Report 2024
Key Benefits of CNAPP
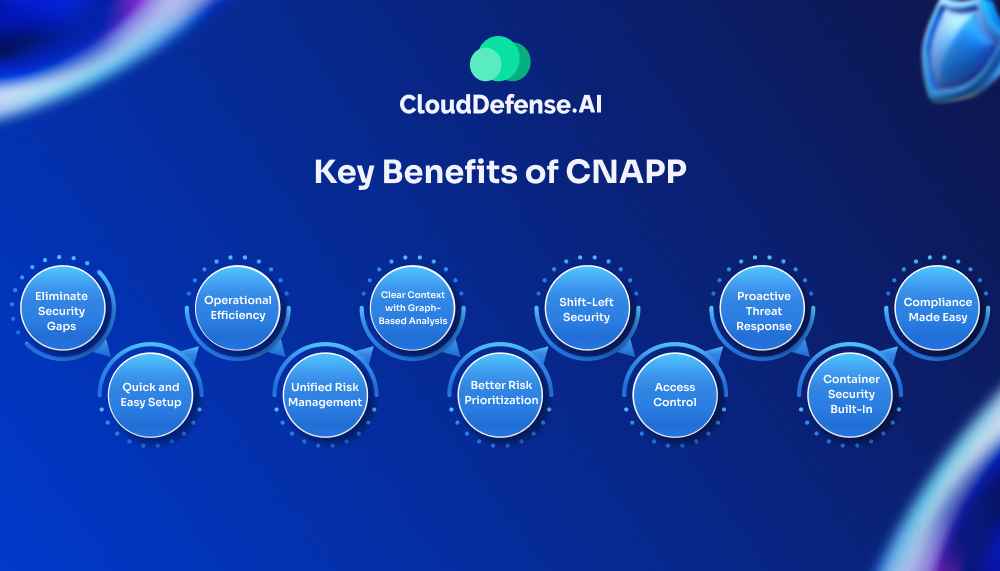
Eliminate Security Gaps
One of the best things about CNAPP is that it gives you full visibility over your cloud setup without any complicated agent installs. As soon as you add new workloads, CNAPP automatically spots them and starts securing everything. So, you’ll never have to worry about missing something important.
Quick and Easy Setup
You want protection, and you want it fast. CNAPP makes that happen by connecting directly to your cloud provider’s APIs. This means you can scan and secure everything in just a few minutes—no slow, painful setup processes. It’s all handled quickly, so you can focus on the bigger stuff.
Operational Efficiency
Agents can slow down your workloads and add complexity to operations, which is why many DevOps teams avoid them. That’s why CNAPP’s agentless approach is such a game-changer. It cuts out the extra steps, saving time and reducing costs. Your team can keep things moving quickly without being held back by slow, expensive tools.
Unified Risk Management
CNAPP brings all your risk factors into one place—whether it’s vulnerabilities, network exposure, sensitive data, or malware. It doesn’t stop with just spoting these issues; it connects the dots, showing how different risks combine to create potential threats. That means less guesswork and more focus on the problems that matter most.
Clear Context with Graph-Based Analysis
It’s rather difficult to keep track of all the interactions in your cloud; however, CNAPP makes the job pretty easy. It uses an interactive graph of how all the parts of your system interact; even a nontechnical security person can understand that pretty easily. You may get a glimpse into the relationship and risks, making the action quicker if you have to take immediate action.
Better Risk Prioritization
With everything under one roof, CNAPP lets you focus on the biggest risks first. It concentrates on what’s really necessary and critical, so you don’t have to waste time with all kinds of incoming alerts. You only receive a single, clear list of the top priorities to fix, saving time and reducing stress for everyone involved.
Shift-Left Security
One of CNAPP’s strengths is that it lets you integrate security into your development process from the start. By integrating with your CI/CD pipelines, it helps you to detect risks at the early stage, and thereby you will not be overburdened with last-minute surprises in production. This keeps your development secure and avoids unnecessary delays for the security team.
Access Control
Managing who gets access to what is a key part of security. CNAPP helps with that by giving you fine-tuned access control features. You can easily set permissions, limit access based on roles, and ensure that the right people have the right level of access—nothing more, nothing less. This keeps your cloud environment secure while ensuring your team has what they need to do their jobs.
Proactive Threat Response
Instead of waiting for problems to happen, CNAPP helps you get ahead of potential attacks. It spots weak points and closes them off before attackers even have a chance. And if something does go wrong, it quickly alerts you to the issue and helps you respond fast, reducing the impact of any security incident.
API Protection
APIs are critical for connecting your apps to external systems, and they can be a big target for attacks. CNAPP takes care of that, ensuring your APIs are protected from things like data leaks and injection attacks. So, you can keep your apps running smoothly without worrying about API vulnerabilities.
Container Security Built-In
For teams running containerized applications, CNAPP keeps an eye on those too. It ensures your container images are secure and free from risks, so your applications can run safely in any cloud environment without any extra steps.
Compliance Made Easy
CNAPP simplifies compliance with industry standards and security policies. Not only does it ensure your cloud applications meet compliance requirements, but it also generates detailed audit reports, giving you the visibility and accountability you need.
How CNAPP Works
1. Complete Visibility into Cloud Environments
See Everything, Everywhere
A CNAPP gives you a clear view across all your cloud platforms, whether you’re using AWS, Azure, Google Cloud, or any other provider. It pulls together data from all your clouds into one easy-to-use dashboard, so you’re never left in the dark.
Cover All Your Bases
From virtual machines to serverless functions and everything in between, CNAPP closely monitors and manages all your cloud resources effectively. It, therefore, allows you to hold a consistent and comprehensive view of your entire setup, irrespective of the various cloud services you are going to use in your operations.
Get the Full Picture
CNAPP addresses not just surface-level issues about security but digs deep down through every aspect of your security posture. It ranges from a thorough analysis of vulnerabilities to network exposures, secrets, and all other things that might bear relevance on your security. It also keeps one informed by offering real-time threat detection. This means one is always on know-how concerning any emerging threats or issues that might crop up.
2. Integrated Cloud Security
All-in-One Security Platform
With CNAPP, you do not need to juggle several tools. Everything will come together into one platform, streamlining security management and making the task of security management more efficient and easier—no more separate processes and systems.
Integrated Risk Management
The risk engine in CNAPP keeps an eye on all aspects of your security, from cloud posture management to container security; hence, it gives you a full picture of all the risks hanging around in your whole environment.
End-to-End Defense
CNAPP offers a multi-layered approach to security. It starts with prevention and extends through to threat detection and response. This means you get a full spectrum of protection against potential threats.
Unified Security Dashboard
Instead of hopping between different screens, CNAPP provides you with one dashboard that brings all your risk data together. This one-stop view makes it easier to see how various risks could mix and create vulnerabilities.
3. Contextual Risk Prioritization
Understand What Matters
CNAPP makes use of a security graph to present the context of threats and their associated interconnections. This facilitates you to easily find out which ones are critical issues and how they may lead to larger problems.
Focus on What’s Important
By prioritizing risks based on their real impact, CNAPP helps you cut through the noise. It shows you which threats need immediate attention, so you can focus on the most pressing issues and not get bogged down by less important alerts.
4. Connecting Development and Security Operations
Fix Problems Early
CNAPP can seamlessly integrate with your CI/CD pipelines. This helps you catch issues, remediate them, and patch them up as soon as possible in the development process. Hence, it’s a proactive approach, wherein fewer problems enter the production environment and save tremendous time and effort in the long run.
Developers Friendly
With CNAPP, developers receive clear, actionable insights and comprehensive help that is tailored according to their needs. That kind of support helps developers to address various issues while making the development process agile as well as secure.
5. Streamlined Compliance Management
Customizable Compliance
CNAPP facilitates compliance by providing solutions tailored to your specific regulatory requirements. It guarantees that your cloud environment adheres to industry standards and security policies, eliminating the customary challenges associated with this process.
Easy Reporting
With this feature, in-depth compliance reports get generated with just a click. CNAPP keeps reporting easy and doesn’t strain you by constantly keeping track of audits or proving that your level of standards is being met.
6. DevSecOps Integration
Comprehensive Security Tooling
CNAPP integrates the most critical DevSecOps tools like SAST, DAST, and SCA at every step of the software development lifecycle. In this way, security gets built into every phase of the development process, helping catch vulnerabilities early and keeping the quality of the code up.
API Security at Every Stage
Increasing dependence on APIs has led CNAPP to place strong emphasis on securing API, protecting from common threats like injection attacks and data leaks. This keeps your microservices and all communications with your external system secure.
Shift-Left Security
With CNAPP’s shift-left approach, security moves upstream starting with the development phase. The possibility of risks is addressed even before reaching production by integrating with CI/CD pipelines to release safer code faster.
The Key Components of CNAPP
In a cloud-native environment, securing both infrastructure and applications is crucial. CNAPP is designed to provide an all-around solution to take care of everything related to cloud security and application security. Let’s explore these key components by breaking them into two sections: Cloud Security and Application Security.
Cloud Security Solutions
Cloud Security Posture Management (CSPM)
CSPM solutions continuously monitor cloud environments 24/7 to detect configuration issues, policy violations, and misconfigurations. Through the automation of security scanning across multi-cloud infrastructures like AWS, Azure, and Google Cloud, CSPM ensures that you are complying with industry standards and avoiding cloud-based risks.
Cloud Infrastructure Entitlement Management (CIEM)
One of the challenges organizations face when securing cloud environments is around how they perform identity /entitlement management within these dynamic cloud resources. CIEM is all about securing your cloud identities, monitoring permissions so both users and services have access only to what they need, and pruning away over-permissioned Identities.
Kubernetes Security Posture Management (KSPM)
As Kubernetes becomes more and more a de facto standard for orchestrating containers, securing the environment becomes crucial. KSPM scans and identifies vulnerabilities as well as misconfigurations of a Kubernetes cluster, ensuring security policies comply at all phases of the container lifecycle-from development to production.
Data Security Posture Management (DSPM)
DSPM ensures the protection and management of sensitive data in the cloud. It identifies storage locations of data, analyzes sensitivity, and ensures compliance with various data security standards, such as GDPR and HIPAA. This process empowers organizations to retain control over their data, thus preventing leaks and breaches.
Infrastructure as Code (IaC) Security
IaC enables the automation of infrastructure deployment through code, but it also introduces risks if security is not properly integrated. IaC security ensures that any cloud infrastructure deployed via code is secure by scanning for vulnerabilities and misconfigurations before it is provisioned.
Cloud Security Risk Management – CSRM
The Hacker’s View™ or CSRM simulates how attackers perceive your cloud environment, identifying potential attack vectors, exposures, and risks. That gives insights into vulnerabilities that the threat actors might exploit and empowers you to take proactive steps in securing your cloud infrastructure in advance.
Application Security Solutions
Static Application Security Testing (SAST)
SAST is a security method that scans source code or compiled code for vulnerabilities right at the beginning of the development process. It is very useful to let the developers identify and, therefore fix, security issues even before the code goes live, making it a key component of a shift-left security strategy.
DAST – Dynamic Application Security Testing
Unlike SAST, where testing is done on static code, DAST tests applications in runtime. It simulates real attacks from real attacks like injection attacks, cross-site scripting, and so on. DAST helps find live application vulnerabilities during runtime, which helps secure applications before going into production.
Software Composition Analysis (SCA)
SCA tools check out the codebase for any third-party libraries and open-source stuff to spot vulnerabilities or licensing issues. Since modern apps are all about that open-source code, SCA makes sure those outside dependencies are safe and up to standard.
API Security
APIs are super important for today’s apps, especially in cloud stuff. API security keeps those APIs safe from usual threats like the data leak, injection attacks, and unauthorized access. It secures communications between microservices and external systems, safeguarding sensitive data.
Shift-Left Security
Shift-left security is all about bringing security into the picture earlier in the development process, like mixing it right into how we work on projects. By adding security checks straight into CI/CD pipelines, developers can spot vulnerabilities sooner, which means fewer problems get to production and we can roll out updates faster and more securely.
CloudDefense.AI’s CNAPP Approach
At CloudDefense.AI, we’re committed to offering a CNAPP that covers all bases—both cloud infrastructure and application security. Here’s a breakdown of our approach:
Securing Your Entire Cloud and Apps
Rather than making you juggle separate solutions for your cloud environment and your applications, we keep things simple by securing both in one go. Our unified approach makes sure every part of your digital infrastructure is covered, so you can rest easy knowing your infrastructure and apps are fully protected, all the time.
Customized Compliance
Compliance can be tricky—different industries and regions have their own specific requirements. At CloudDefense.AI, we make sure your CNAPP is customized to meet the unique compliance standards relevant to your business. Whether it’s GDPR, HIPAA, or another set of rules, we ensure your cloud and apps stay compliant, helping you avoid penalties and maintain the trust of your stakeholders.
Attack Path Analysis
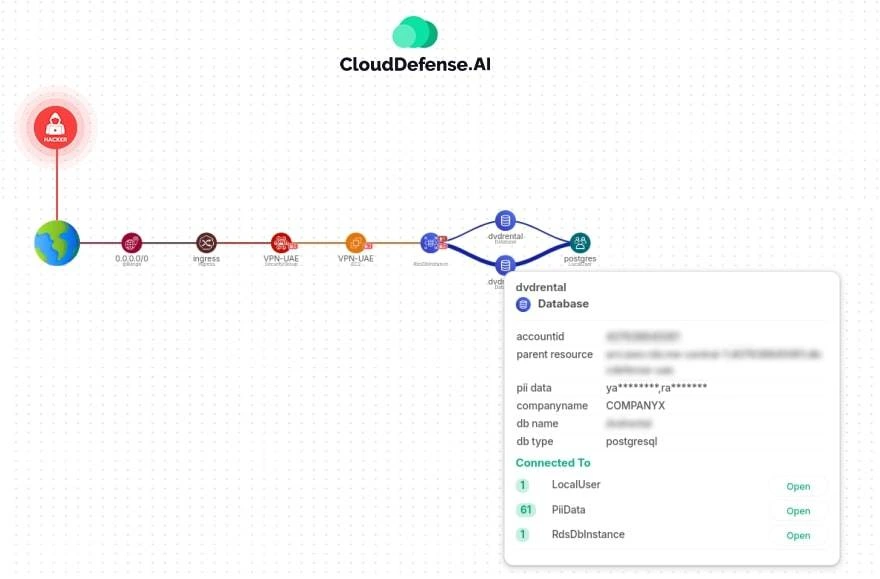
When it comes to security, waiting for problems to happen isn’t an option. We use advanced techniques to map out potential attack paths in your cloud environment. By understanding how your resources and services interact, we can identify pathways an attacker might take and shut down vulnerabilities before they’re exploited.
Hacker’s View™
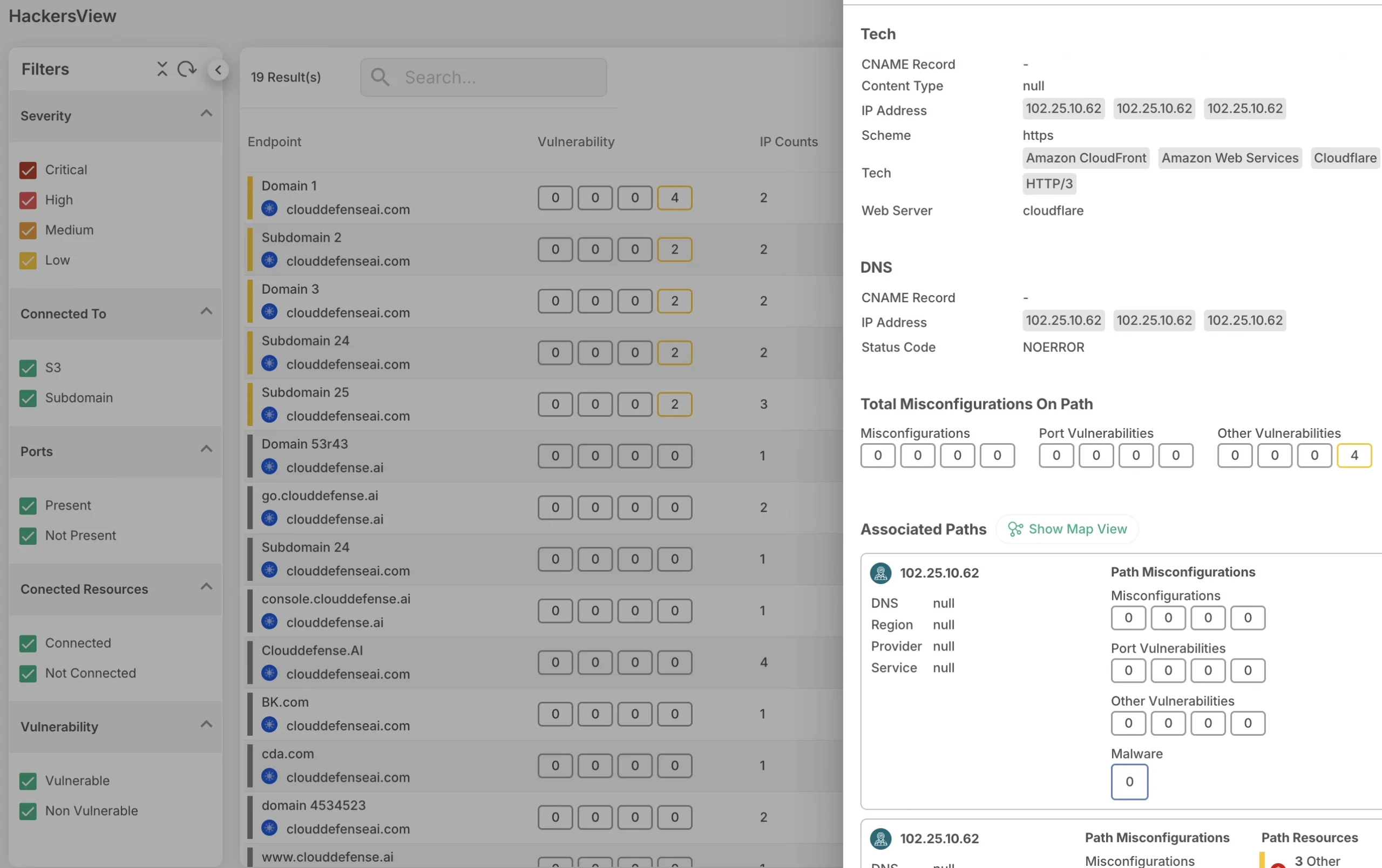
To beat hackers, you have to think like them. That’s exactly what we do. We put ourselves in their shoes, studying your cloud from the inside out. Our Hacker’s View™ solution gives us a unique perspective on how an attacker might try to exploit vulnerabilities. It’s like having an ethical hacker on your side—except we’re here to keep your system safe, not break it.
Agentless Architecture
Unlike other platforms that require you to install agents on every single resource, CloudDefense.AI makes things easy. Our agentless architecture connects directly to your cloud provider’s APIs, meaning you can skip the hassle of deploying and managing agents altogether. It’s quicker, smoother, and doesn’t slow anything down.
Graph-Based Security Insights
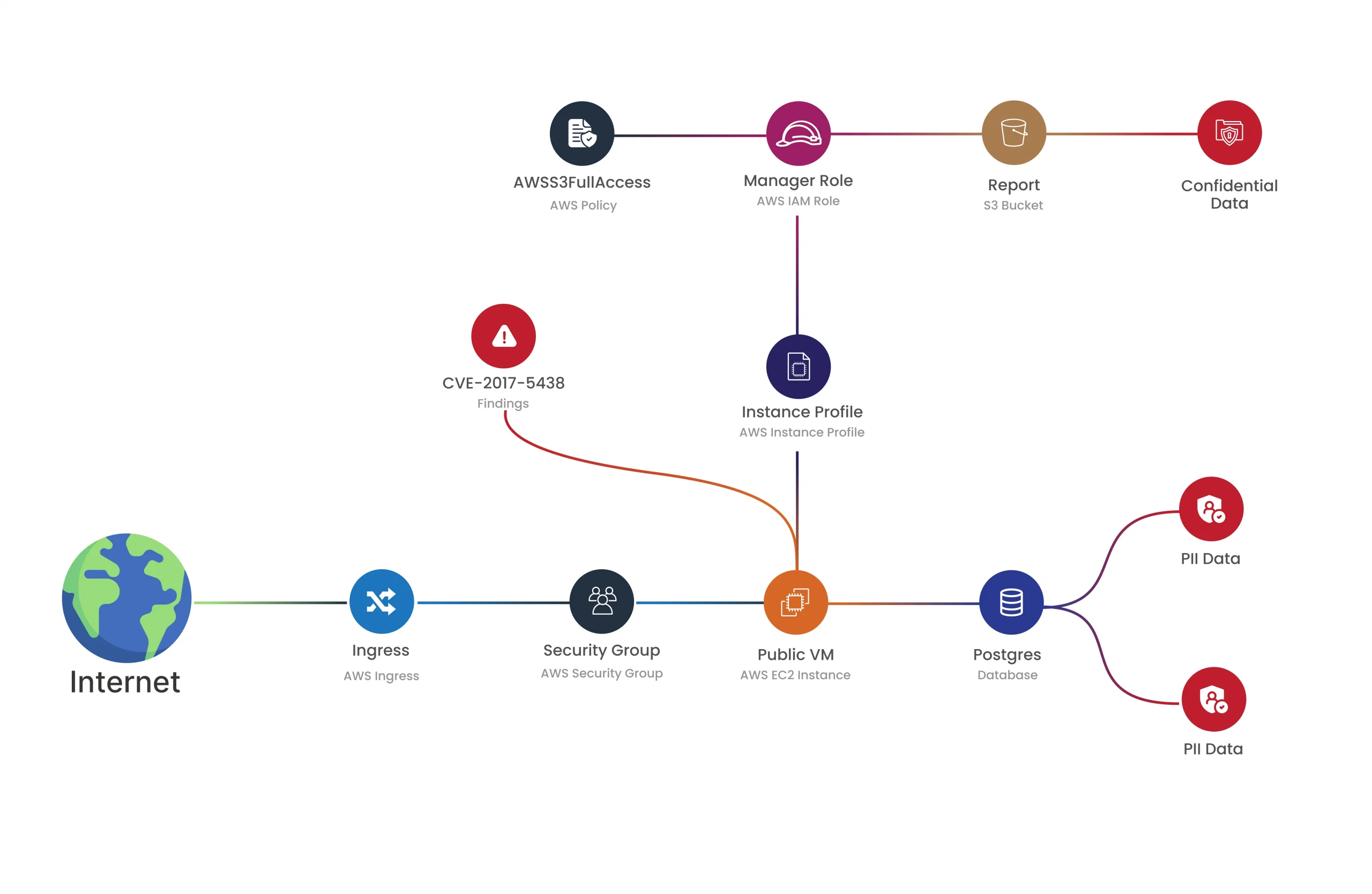
We use graph-based security to give you a clearer picture of how everything in your cloud is connected. Think of it like a map that shows how your resources interact. This lets us see complex relationships and spot risky areas faster, so we can prioritize the most critical issues and help you deal with them head-on.
Prioritizing Risks
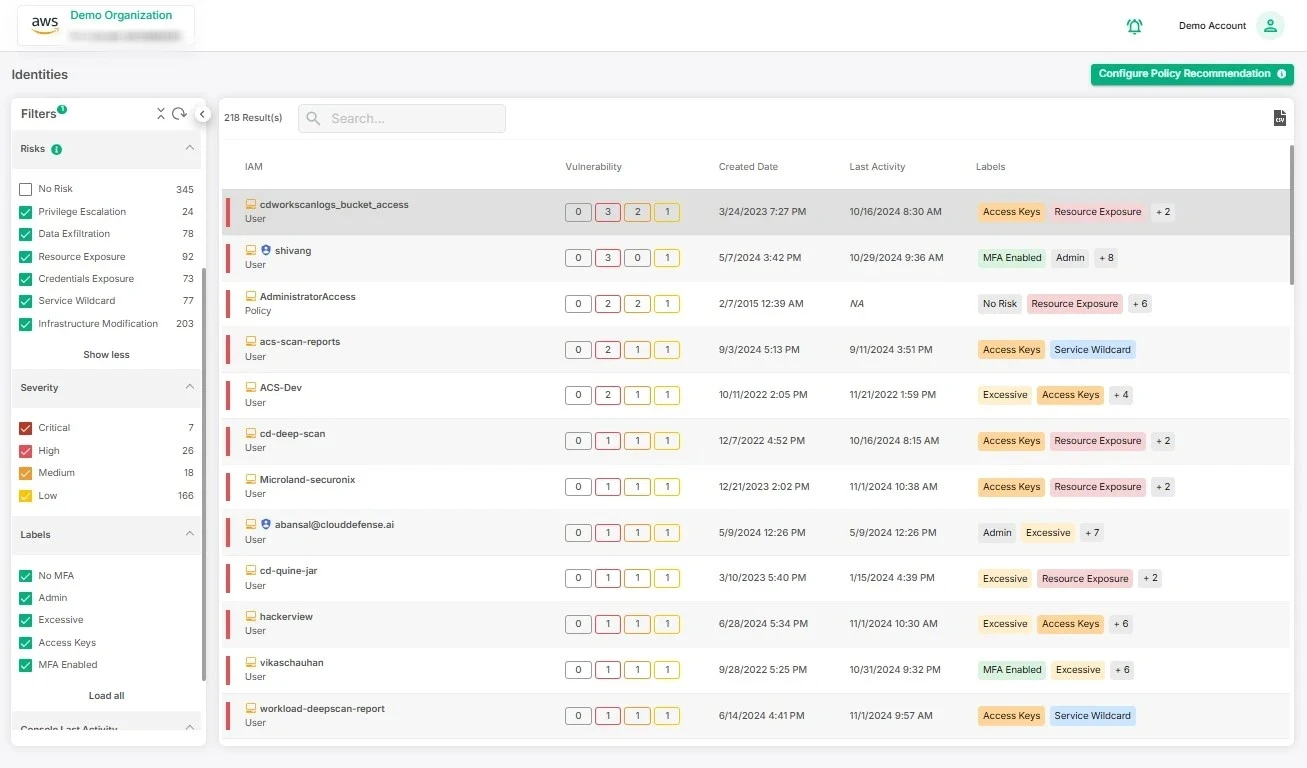
Not all risks are created equal, and we know that. Our platform helps you focus on what really matters by pinpointing the biggest threats first. This way, you’re not wasting time on low-level issues. Instead, you’re handling the most significant risks, keeping your security efforts laser-focused and effective.
FAQ
1. Can a CNAPP solution integrate with my existing security tools and systems?
CNAPP solutions can easily integrate with your existing tools and system as they are designed with that aspect. CNAPP can integrate with any cloud infrastructure and security tools to ensure a comprehensive security posture.
2. What does CNAPP stand for?
CNAPP stands for cloud-native application protection platform, and it serves as an all-in-one security solution to help organizations build and run cloud applications securely. CNAPP is widely used in modern cloud-native application development and cloud computing.
3. What is CNAPP, according to Gartner?
Gartner defines CNAPP as an integrated and combined set of security tools and compliance capabilities whose primary work is to protect the cloud-native application through its lifecycle. It combines multiple separately used security capabilities into one platform and offers a holistic approach toward application security.
4. What is the difference between CNAPP and SASE?
CNAPP focuses on securing cloud-native applications and their infrastructure, while SASE combines network security and wide-area networking for comprehensive protection.
Conclusion
With cyber threats becoming increasingly sophisticated, failing to implement a CNAPP puts your organization at risk. The stakes are higher than ever—don’t wait for a breach to realize the necessity of comprehensive protection. Invest in a CNAPP solution now to safeguard your assets and maintain trust in your cloud environment. The clock is ticking—act before it’s too late.







