What is a Brute Force Attack?
A brute force attack is a method employed by hackers to crack passwords, login credentials, or encryption keys through relentless trial and error. Hackers systematically attempt various combinations until they successfully breach a system or gain access to sensitive information.
This method, though simplistic, remains effective due to its ability to exploit weak passwords or insufficient security measures. Whether targeting individual accounts or organizational systems, the attacker employs automated tools or scripts to rapidly test numerous combinations.
Despite being an age-old technique, brute force attacks persist as a significant cybersecurity threat due to their potential to compromise data integrity, steal sensitive information, or disrupt services.
Motives Behind Brute Force Attacks
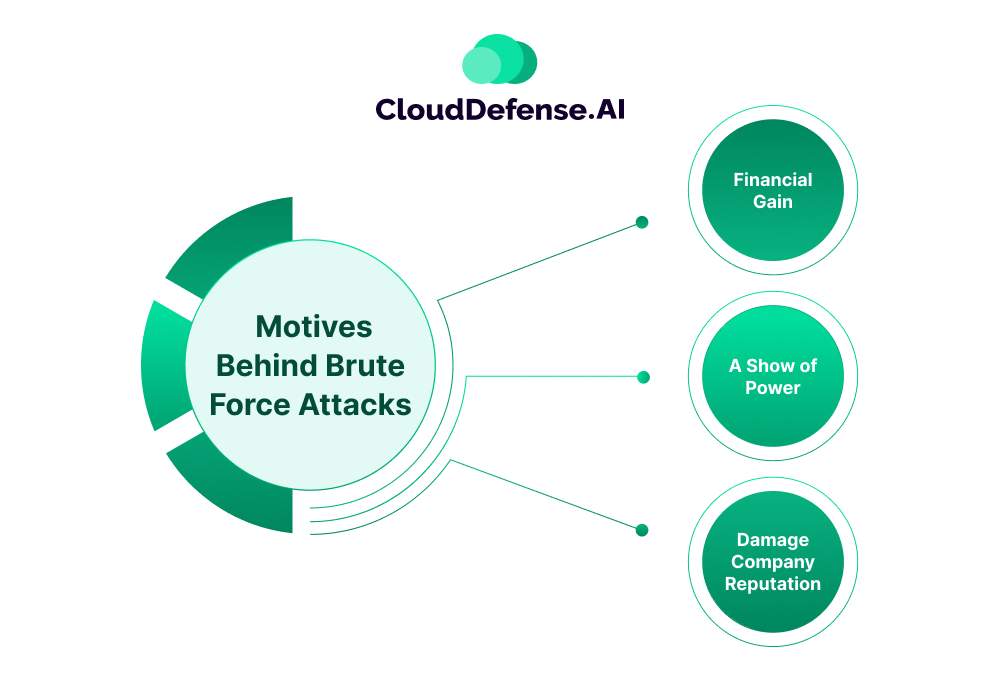
The motives behind a brute force attack can include diverse objectives, we have discussed the motives in detail below.
Financial Gain
Hackers may use these attacks to reap financial rewards by exploiting compromised systems or websites. By deploying spam ads, redirecting traffic, or selling collected data, attackers generate advertising commissions or profit from illicit activities, such as identity theft or data brokering.
A Show of Power
Some hackers use brute force tactics to exhibit their prowess or sow chaos in digital ecosystems. Through malware spread, system hijacking, or botnet creation, attackers disrupt operations, compromise security, and potentially extort victims for monetary gain.
Damage Company Reputation
Attacks may serve as a means to tarnish reputations. By disseminating offensive content or pilfering sensitive data, attackers undermine the credibility and trust of individuals or organizations, resulting in financial losses and diminished stakeholder confidence.
Types of Brute Force Attacks
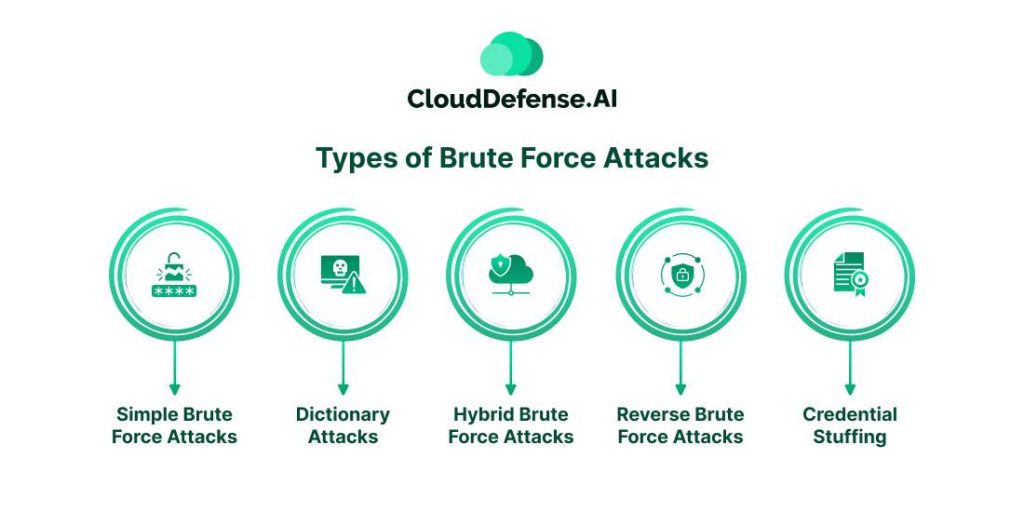
Brute force attacks come in various forms, each with its own strategy to exploit weaknesses and increase the chances of success:
1. Simple Brute Force Attacks
These attacks rely on systematic guessing without any fancy tricks. They’re effective for cracking basic passwords like “guest12345”.
2. Dictionary Attacks
Hackers use a list of common passwords or phrases to guess login credentials. While simple, they’re often the first step in cracking more complex passwords.
3. Hybrid Brute Force Attacks
These attacks blend dictionary methods with logical guessing to crack passwords that mix common words with random characters, like “NewYork1993”.
4. Reverse Brute Force Attacks
Hackers start with a known password and try it against a large number of usernames until they find a match. They often use leaked passwords from previous data breaches.
5. Credential Stuffing
This method relies on the fact that many people reuse the same login details across multiple sites. Hackers try known username-password pairs on different platforms, exploiting this habit to gain unauthorized access.
Popular Brute Force Attack Tools
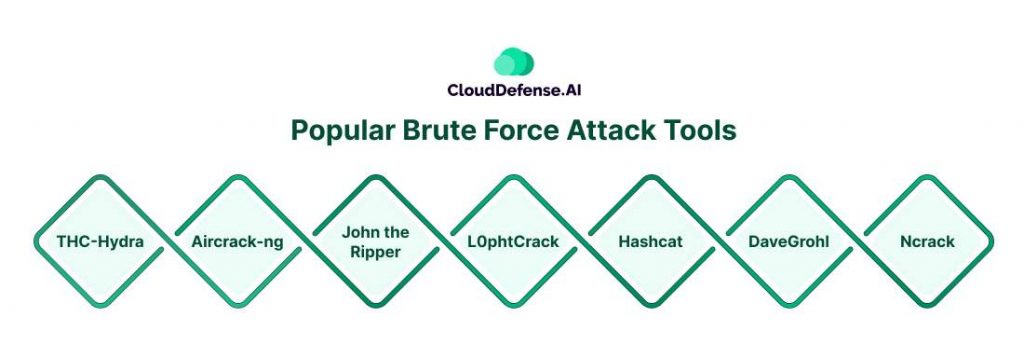
Popular brute force attack tools are widely utilized by hackers and security analysts alike to assess and exploit vulnerabilities in various systems and networks. These tools offer sophisticated functionalities tailored to crack passwords and gain unauthorized access efficiently:
| Name of Tools | Description |
| THC-Hydra | Renowned for its versatility, Hydra is utilized by security analysts to rapidly test a plethora of password combinations, employing both simple brute force and dictionary-based approaches. With support for over 50 protocols and compatibility with multiple operating systems, Hydra remains a go-to tool for identifying vulnerabilities. |
| Aircrack-ng | Primarily targeting Wi-Fi network security, Aircrack-ng employs a dictionary of commonly used passwords to breach wireless networks. Its cross-platform compatibility extends to Windows, Linux, iOS, and Android, making it a versatile option for attackers seeking access to various systems. |
| John the Ripper | This open-source password recovery tool boasts support for a vast array of cipher and hash types, enabling the cracking of user passwords across macOS, Unix, and Windows platforms. Its versatility extends to database servers, web applications, network traffic, and encrypted files, making it invaluable for security assessments. |
| L0phtCrack | Specifically designed for Windows password cracking, L0phtCrack utilizes rainbow tables, dictionaries, and multiprocessor algorithms to efficiently crack passwords. While focusing on Windows systems, its comprehensive approach ensures thorough testing and identification of vulnerabilities. |
| Hashcat | Operating across Windows, Linux, and macOS, Hashcat offers a suite of attack methods including simple brute force, rule-based, and hybrid approaches. Its versatility and efficiency make it a popular choice for cracking passwords and strengthening network security. |
| DaveGrohl | An open-source tool specifically designed for cracking macOS passwords, DaveGrohl can be distributed across multiple computers, enhancing its effectiveness and scalability. |
| Ncrack | Customized for cracking network authentication, Ncrack is compatible with Windows, Linux, and BSD systems, providing attackers with a comprehensive toolset for assessing network security. |
Weak Passwords that Enable Brute Force Attacks
Today, the proliferation of online accounts has led to the use of numerous passwords, often reused or overly simplistic, exposing individuals to brute force attacks. Weak passwords not only jeopardize the security of email accounts but also serve as entry points for hackers to exploit interconnected accounts.
Neglecting to change default router passwords leaves local networks vulnerable to intrusion, enabling attackers to compromise entire networks easily. Commonly encountered passwords in brute force attempts include personal information like birthdates, common phrases, and simple sequences like “123456” or “qwerty.”
Strengthening passwords is vital for thwarting identity theft, data breaches, and unauthorized access. By using strong, unique passwords, individuals can significantly enhance their online security posture, minimizing the risks of cyber threats and protecting sensitive information.
How to Protect Against Brute Force Password Hacking?
Brute Force attacks can be prevented by following strong security practices. Here are a few methods that can be used by both companies and individuals to protect themselves from brute-force attacks.
For Individuals:
- Strong Password Practices: Avoid predictable information such as family names and use longer passwords with a mix of characters. Create unique passwords for each one of your accounts. Lastly, steer clear of common patterns like “123456” or “password.”
- Passphrase Usage: Employ complex passphrases to prevent dictionary attacks. Incorporate truncation or unique word combinations for added security.
- Avoid Common Password Pitfalls: Refrain from using easily guessable passwords. Ensure uniqueness across all accounts to prevent credential stuffing.
- Password Management Tools: Use password managers to generate and securely store complex passwords. Allows easy access to multiple accounts without compromising security.
For Organizations:
- Enforce Strong Password Policies: Implement rules for password complexity and regular updates. Educate users on creating and maintaining robust passwords.
- Use Multi-Factor Authentication (MFA): Augment password-based authentication with additional verification factors. Reduce reliance on passwords alone for account access.
- Limit Login Attempts: Implement lockout policies to deter brute force attacks. Gradually increase delays for successive failed login attempts.
- Utilize CAPTCHA and IP Blacklisting: Integrate CAPTCHA challenges to impede automated attacks. Maintain IP blacklists to block known malicious actors from accessing systems.
- Regular Account Maintenance: Remove unused or dormant accounts to reduce the attack surface. Conduct regular audits to identify and mitigate security vulnerabilities.
- Ongoing Security Education and Monitoring: Provide continuous training on security best practices. Monitor network activity for signs of suspicious behavior and respond promptly to potential threats.
Brute Force Attack Prevention with CloudDefense.AI?
CloudDefense.AI’s advanced bot detection and minimization capabilities can swiftly differentiate between legitimate users and malicious bots, blocking unauthorized access attempts. Using multi-stage identification processes, including behavioral analysis, attack path analysis, and signature matching, it accurately classifies bot traffic and challenges suspicious bots with cookie acceptance and JavaScript parsing tests.
Real-time threat response mechanisms enable immediate action against detected threats. The platform smoothly integrates with existing security infrastructure and offers customizable detection policies. Comprehensive reporting tools empower organizations to analyze bot traffic patterns and optimize security strategies effectively. With CloudDefense.AI, businesses can proactively mitigate the risk of brute force attacks, ensuring strong protection for their systems and data.
Consider booking a free demo right now to witness the powerful capabilities of CloudDefense.AI







