Have you ever noticed your computer running slow? Millions of devices around the world are secretly controlled by hackers in shadowy botnets. A botnet is an army of compromised devices under the control of a single attacker, known as a bot-herder. Nowadays, botnets are a serious threat, capable of unleashing devastating attacks or quietly stealing your data.
But no worries! Here we’ll discuss what is a botnet, exploring how they’re formed, the havoc they wreak, and how you can protect yourself from becoming an unwitting bot.
What is a Botnet?
A botnet, short for “robot network,” is essentially an army of compromised devices under the control of a single attacker, often referred to as a “bot herder.” These devices, called bots, can be anything from your personal computer to a smart refrigerator—any internet-connected device susceptible to malware infection.
In a recent case, security researchers discovered a botnet infecting millions of smartwatches in 2020. The botnet, called FluBot, targeted Android devices and tricked users into downloading malware disguised as legitimate apps. Once downloaded, FluBot siphoned off personal information like login credentials and banking details. This case highlights how even seemingly innocuous devices can be weaponized in a botnet.
Botnets are created by malware that infects devices through various means, like phishing emails, malicious website downloads, or even infected USB drives. Once infected, the bot silently communicates with a central server controlled by the bot herder. This server then relays commands to the bots, turning them into a coordinated force for malicious activities.
How do systems get infected in botnet attacks?
To understand this, let’s consider a scenario. Imagine this: You settle down with your morning coffee, checking your inbox. An email arrives, supposedly from your favorite streaming service. The subject line screams urgency: “Action Required: Update Your Account or Risk Losing Access!”
Feeling a pang of worry, you click to open the email. It looks legitimate, with logos and familiar formatting. The email body warns of an outdated payment method and instructs you to click a link to update your billing information.
Without a second thought, you click the link. It redirects you to a cleverly designed fake login page that appears identical to the real one. You enter your username and password, eager to resolve the issue and get back to your shows. Uh oh.
Instead of a confirmation message, the page freezes. A sinking feeling creeps in. You’ve likely fallen victim to a phishing scam.
Behind the scenes, the moment you clicked the malicious link, malware in disguise infiltrated your device. This malware silently establishes a connection with the attacker’s C&C server, transforming your computer into a mindless bot within their ever-growing botnet.
Now, your device is unknowingly part of a digital army, capable of launching attacks or stealing data at the attacker’s command. All this happens while you continue your day, completely oblivious to the dark puppet master lurking in the digital shadows.
Types of Botnet Attacks
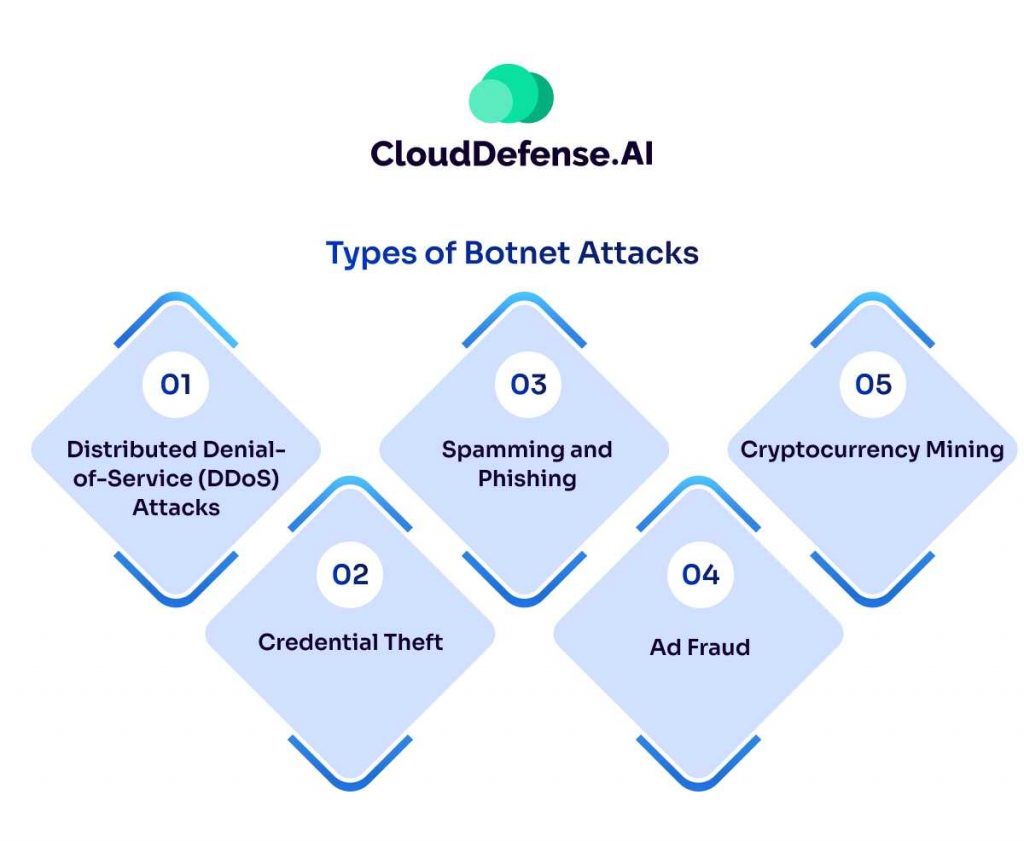
Botnets are versatile tools for cybercrime, and attackers can leverage them for a range of malicious activities. Here’s a breakdown of some common botnet attack types:
Distributed Denial-of-Service (DDoS) Attacks
This is a classic botnet tactic. The botnet floods a website or server with an overwhelming surge of traffic (like pings or data requests) from all the infected devices. This traffic overload cripples the target, making it inaccessible to legitimate users. DDoS attacks can target online businesses, critical infrastructure, or even government websites, causing significant disruption and financial losses.
Credential Theft
Botnets can be programmed to steal login credentials from compromised devices. This can be achieved through various methods, such as keylogging malware that captures keystrokes or by launching phishing campaigns where bots automatically fill in login details on fake websites designed to steal user information. Stolen credentials can then be used to access online accounts, steal identities, or commit further fraud.
Spamming and Phishing
Botnets are ideal tools for mass-scale spam campaigns. Attackers can use them to send millions of spam emails containing malicious links or attachments. These emails often appear legitimate, tricking recipients into clicking and unknowingly infecting their devices with malware, further expanding the botnet. Additionally, botnets can automate phishing attacks, sending emails that mimic real companies or services to lure users into revealing sensitive information.
Ad Fraud
In the online advertising world, clicks and views generate revenue. Botnets can be used to manipulate this system by simulating real user clicks on advertisements. This fraudulent activity generates unearned income for attackers while costing legitimate advertisers money.
Cryptocurrency Mining
Cryptocurrency mining requires significant computing power. Botnets can hijack the processing power of infected devices to mine cryptocurrency for the attacker. This can drain the victim’s device resources, slow down performance, and even increase their electricity bills.
These are just some of the most common ways botnets are used in attacks. As cybercrime tactics evolve, attackers are continuously finding new ways to exploit botnets for their malicious purposes.
How Does a Botnet Work?
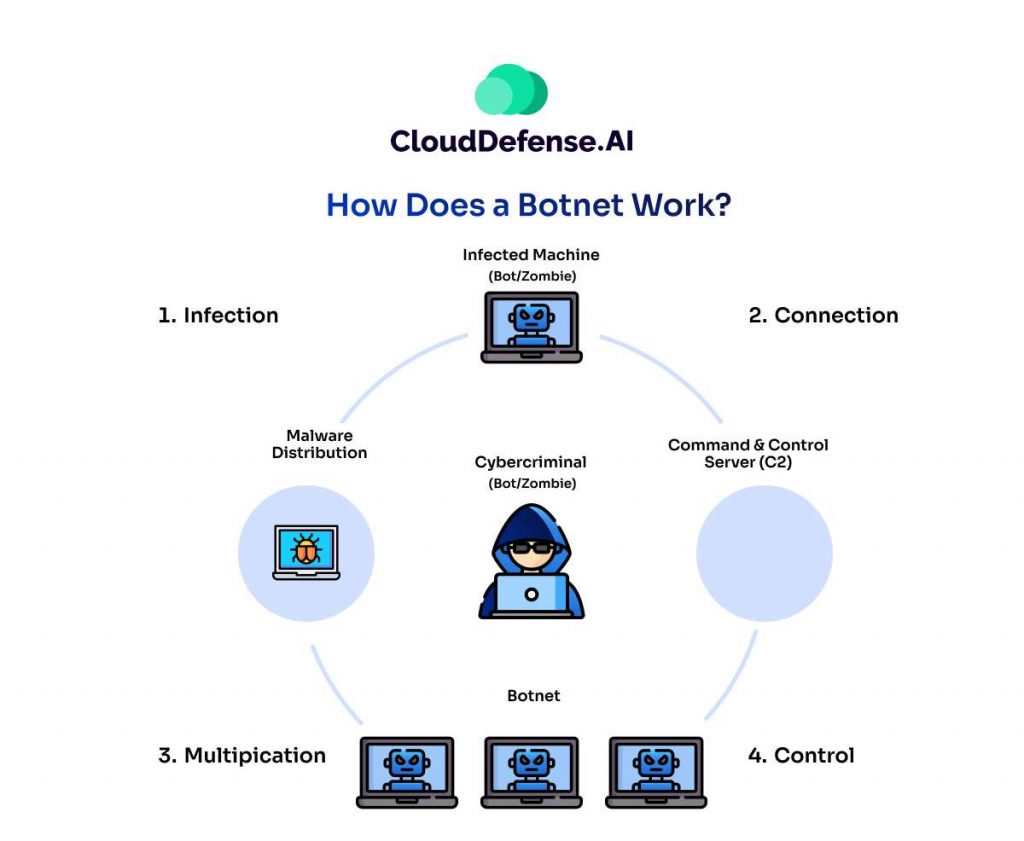
Botnets don’t appear overnight. They follow a systematic process to build a network of compromised devices. Here’s a breakdown of the key stages in a botnet’s lifecycle:
1. Infection: The first step is infecting devices with the bot malware. This can happen through various methods, such as:
- Phishing emails: Emails containing malicious attachments or links can trick users into downloading and installing the bot malware.
- Drive-by downloads: Visiting compromised websites can unknowingly infect a device with a bot if it exploits vulnerabilities in the user’s software.
- Unsecured networks: Downloading files or browsing on unsecured Wi-Fi networks can expose devices to malware attacks.
- Software vulnerabilities: Unpatched software vulnerabilities can provide a backdoor for attackers to inject bot malware onto a device.
2. Connection: Once a device is infected, the bot malware establishes a connection with a Command and Control (C&C) server controlled by the bot herder. This C&C server acts as the central hub, issuing commands and instructions to the infected devices. The connection can be:
- Client-Server: In this traditional model, bots directly connect to a central C&C server for instructions.
- Peer-to-Peer (P2P): More sophisticated botnets use P2P architecture, where infected devices communicate directly with each other, making them harder to detect and disrupt by taking down a single C&C server.
3. Control: With the connection established, the bot herder takes control of the infected devices. They can remotely issue commands to the bots, instructing them to perform various malicious activities, such as launching DDoS attacks, stealing data, or spamming. The bots operate silently in the background, often without the user’s knowledge, turning their device into a digital pawn.
4. Multiplication: A critical feature of botnets is their ability to self-replicate and grow. Bot malware may be programmed to scan for vulnerabilities in other devices on the network or internet. Once a vulnerability is found, the bot can attempt to infect the new device, adding it to the botnet and further amplifying its power. This continuous growth allows botnets to become vast networks of compromised devices, significantly increasing the potential impact of their attacks.
Why Scammers Launch Botnet Attacks
Botnets are a scammer’s dream tool, offering a vast, remotely controlled army of devices for a range of criminal activities. Here’s a glimpse into how scammers leverage botnets for their malicious gains:
1. Financial Gain:
- Click Fraud: As mentioned earlier, botnets can be used to generate fraudulent clicks on advertisements. This tricks advertisers into paying for fake clicks, draining their budgets and lining the pockets of scammers.
- Data Theft: Botnets can be used to steal personal information like credit card details, login credentials, and social security numbers from compromised devices. This stolen data can then be sold on the black market or used for further identity theft and financial crimes.
- Cryptocurrency Mining: Botnets can hijack the processing power of infected devices to mine cryptocurrency for the scammer. This not only steals the victim’s computing resources but also increases their electricity bills.
2. Disruption and Chaos: As we’ve seen, botnets can be used to launch DDoS attacks, overwhelming websites and online services with traffic, making them inaccessible to legitimate users. This can cripple businesses, disrupt critical infrastructure, or even be used for political purposes.
3. Spam Campaigns: Scammers use botnets to send massive waves of spam emails. These emails often contain phishing links or malware attachments, further expanding the botnet and potentially leading to more victims.
4. Reputation Damage: Botnets can be used to target competitors or organizations with negative campaigns. This can involve flooding a website with negative reviews, spamming social media with defamatory content, or launching DDoS attacks to disrupt operations.
Protecting Yourself from Botnet Threats
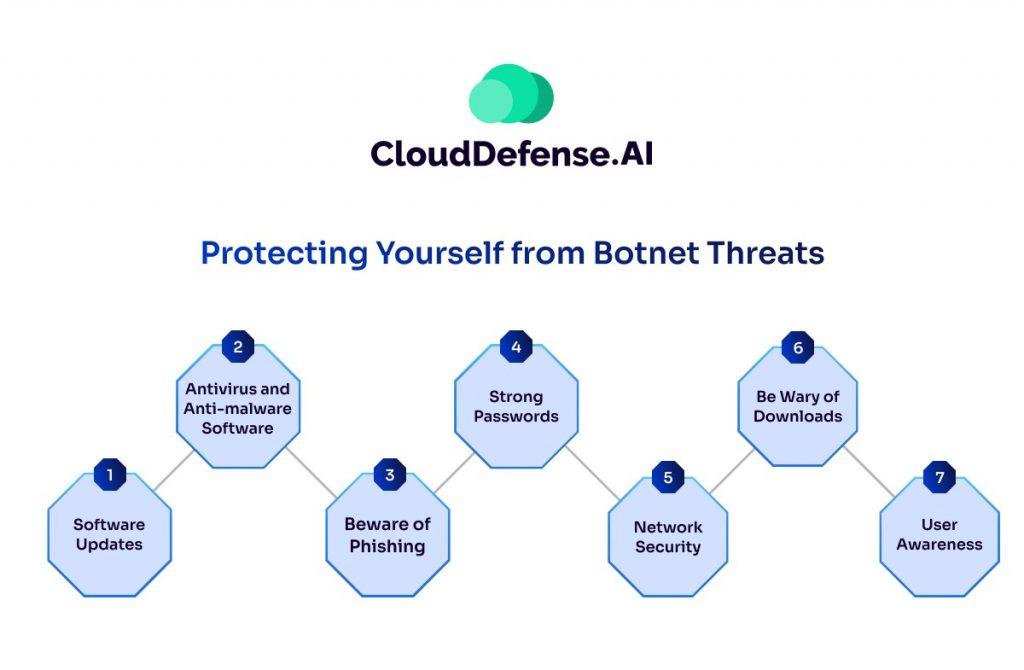
Botnets pose a serious threat, but there are steps you can take to defend yourself and avoid becoming an unwitting participant in their malicious schemes:
- Software Updates: One of the most effective ways to protect yourself is to keep your operating system, applications, and firmware up-to-date. These updates often contain security patches that fix vulnerabilities that attackers can exploit to install bot malware.
- Antivirus and Anti-malware Software: A reputable antivirus and anti-malware program can help detect and block malware before it infects your device. Regularly scan your devices for threats and keep your security software updated with the latest definitions.
- Beware of Phishing: Phishing emails are a common way for bot malware to spread. Be cautious of emails, especially those with urgent messages or requests for personal information. Don’t click on suspicious links or attachments, and verify the sender’s identity before interacting with any email.
- Strong Passwords: Use strong, unique passwords for all your online accounts. Avoid using easily guessable passwords or the same password for multiple accounts. Consider using a password manager to generate and store complex passwords securely.
- Network Security: Secure your home network by using a strong password for your Wi-Fi router and enabling encryption. Avoid connecting to public Wi-Fi networks without proper protection like a VPN.
- Be Wary of Downloads: Only download software and files from trusted sources. Be cautious of clicking on pop-up ads or downloading attachments from unknown senders.
- User Awareness: Education is key. By understanding how botnets work and the tactics scammers use, you can be more vigilant and avoid falling victim to their tricks.
Conclusion
Botnets pose a constant and evolving threat, both for individuals and organizations. Remember, even the most cautious user can fall victim to a cleverly crafted attack. Therefore, for comprehensive protection, organizations need a robust defense that goes beyond individual devices. Cloud security solutions like CloudDefense.ai offer advanced threat protection specifically designed to identify and stop botnet attacks before they can wreak havoc. Don’t wait until it’s too late; take control of your cloud security now. Book a free demo with us, and see how our comprehensive protection can give you peace of mind in a world increasingly threatened by botnets and other cyber threats.







