What is a Backdoor Attack?
Backdoor attacks are a type of cyber assault where threat actors exploit or create hidden entry points within a system to gain unauthorized remote access.
These backdoors allow attackers to bypass standard security mechanisms and perform a range of malicious activities, including gaining control of system resources, conducting network reconnaissance, and installing various forms of malware.
How Does a Backdoor Attack Work?
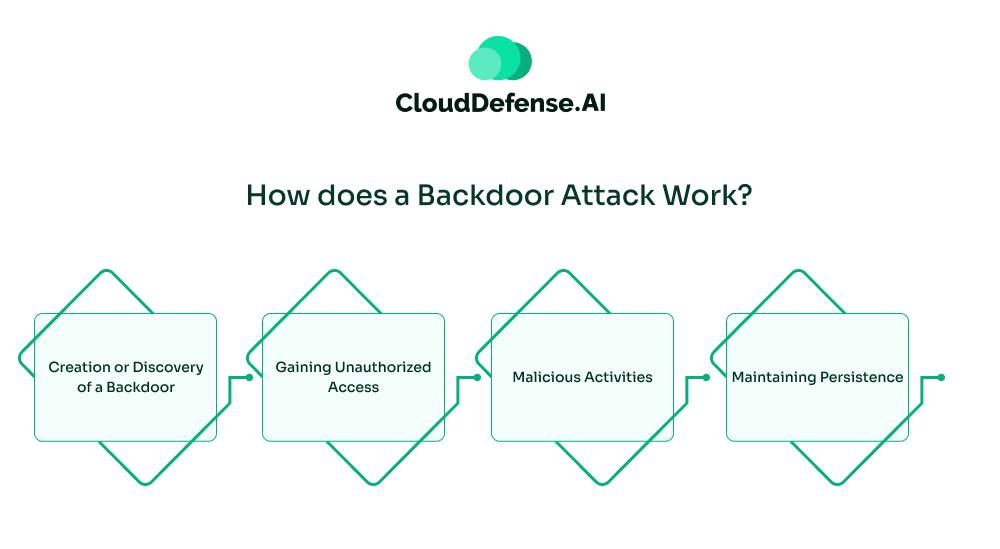
Backdoor attacks typically involve the following working method.
Creation or Discovery of a Backdoor
Attackers may exploit software vulnerabilities to insert a backdoor, or they may take advantage of preexisting backdoors left by developers, either intentionally for maintenance purposes or unintentionally through security oversights.
Gaining Unauthorized Access
Once the backdoor is established, attackers can gain remote access to the system without triggering security alarms. They can then execute arbitrary commands, exfiltrate sensitive data, or manipulate system settings.
Malicious Activities
With access granted, attackers can conduct various malicious activities, such as installing additional malware (e.g., ransomware, spyware, or Trojans), performing network reconnaissance to identify further vulnerabilities, and expanding their control over the network.
Maintaining Persistence
Attackers often implement measures to ensure long-term access through the backdoor, making it difficult for security teams to detect and remove their presence. This can include altering system files, modifying user permissions, or installing rootkits.
Types of Backdoor Attacks
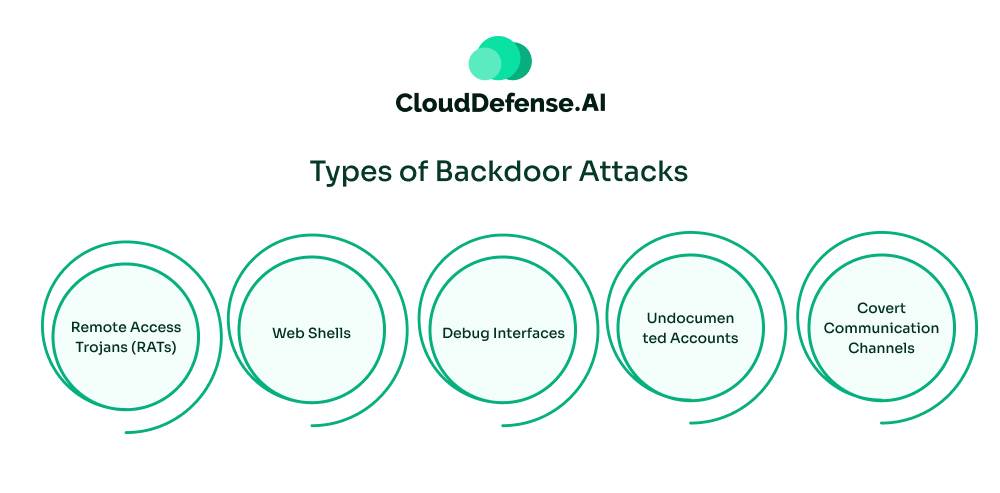
These are some backdoor attacks that can be executed through various methods:
Remote Access Trojans (RATs)
RATs are malicious programs that provide unauthorized remote access to a victim’s computer. Once installed, they allow attackers to control the infected system as if they were on the keyboard. This control can be exploited for various purposes, such as stealing data, monitoring activity, deploying malware, or launching further attacks.
Web Shells
A web shell is a malicious script that runs on a vulnerable web server. It gives attackers a command-line interface to the operating system and turns it into a backdoor. This enables command execution, file manipulation, persistent access, data theft, or malware deployment.
Debug Interfaces
Debug interfaces are built-in tools in software that help developers troubleshoot code. If left exposed or misconfigured, they can be entry points for attackers, allowing them to bypass security and gain unauthorized access.
Undocumented Accounts
Undocumented accounts are user accounts with administrative privileges that are not officially recognized or managed by the system administrator. Malicious actors can create these accounts inadvertently or intentionally. Attackers may use them to bypass authentication mechanisms and gain unauthorized access to sensitive system resources.
Covert Communication Channels
To evade detection, attackers often employ covert communication channels to interact with compromised systems. These channels can involve hidden network ports, encrypted traffic, or data encoded within seemingly normal network traffic. By using these clandestine methods, attackers can maintain persistent control over the infected system without raising suspicion.
Backdoor Installation Methods
These are some installation methods that Backdoor attackers use.
- Exploiting Vulnerabilities: Attackers often use software vulnerabilities to install backdoors. This might involve exploiting flaws in web applications, operating systems, or other software components.
- Social Engineering: Attackers can gain access to systems by manipulating users into revealing sensitive information or downloading malicious files.
- Malware Infection: Some malware includes backdoor capabilities as part of their payload.
Risks of Backdoor Attacks
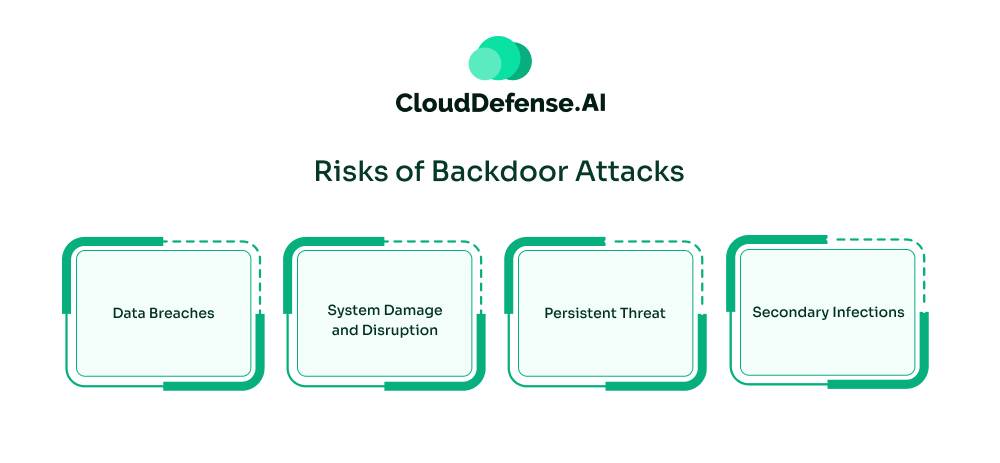
Backdoor attacks pose a formidable threat to individuals and organizations alike. These insidious breaches compromise the fundamental security of systems, enabling attackers to operate with impunity.
- Data Breaches: The most immediate and apparent risk is the theft of sensitive information. From financial data to intellectual property, backdoors provide a direct pathway for cybercriminals to exfiltrate valuable assets. This can result in substantial financial loss, reputational damage, and legal consequences.
- System Damage and Disruption: In addition to data theft, backdoors can harm systems directly. Attackers may manipulate system configurations, delete critical files, or even render systems inoperable. This can cause significant operational disruptions, leading to downtime, productivity losses, and financial setbacks.
- Persistent Threat: The most alarming aspect of backdoor attacks is their stealthy nature. Unlike other cyber threats that may trigger alarms or leave evident traces, backdoors can lie dormant for extended periods. This persistent threat allows attackers to maintain covert access, potentially escalating their activities over time and expanding their impact.
- Secondary Infections: A compromised system with a backdoor is often used as a staging ground for further attacks. Attackers may leverage the compromised system to spread malware, launch distributed denial-of-service (DDoS) attacks, or target other systems within the network. This creates a cascading effect, amplifying the overall risk and damage.
Detecting and Preventing Backdoor Attacks
By their nature, backdoors are designed to evade detection. Hidden within the intricate architecture of systems or masked by complex code, they pose a significant challenge to security professionals. However, a combination of tools, strategies, and vigilance can help mitigate this threat.
Detection
- Anomaly Detection: Unusual patterns in network traffic, system behavior, or user actions can indicate a backdoor. Advanced analytics and machine learning can help pinpoint these anomalies.
- Intrusion Detection Systems (IDS) monitor network traffic for suspicious activity, including potential backdoor communications. When anomalous behavior is detected, IDS can generate alerts.
- Behavior-Based Detection: Observing how software behaves can reveal hidden malicious activities. This approach focuses on identifying deviations from normal program behavior.
- Regular Auditing: Conducting thorough audits of system logs, configuration files, and user accounts can help uncover unauthorized modifications or suspicious activity.
Prevention
- Strong Access Controls: Implementing proper access controls, such as multi-factor authentication and role-based access, limits unauthorized access to systems.
- Software Updates: Keeping software and operating systems up-to-date is crucial to patch vulnerabilities that could be exploited to install backdoors.
- Network Segmentation: Isolating sensitive systems and data can limit the potential damage if a backdoor is compromised.
- Employee Training: Educating employees about the risks of social engineering and phishing attacks can help prevent the initial infection that often leads to the installation of a backdoor.
- Incident Response Planning: Having a well-defined incident response plan in place can help minimize the impact of a backdoor attack if it occurs.
- Threat Intelligence: Staying informed about the latest threats and attack techniques can help organizations proactively defend against backdoors.
The SolarWinds Supply Chain Attack: A Prime Example of a Backdoor Attack
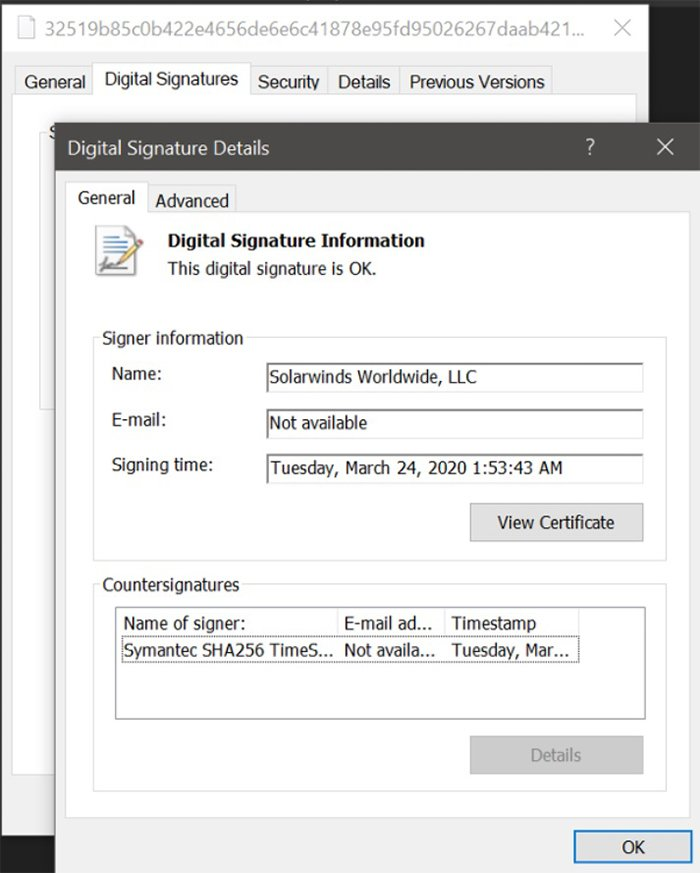
The SolarWinds cyber attack was a highly sophisticated supply chain attack that compromised SolarWinds Orion, a widely used IT management software. Attackers injected a backdoor (Sunburst malware) into Orion’s software updates, allowing them to gain unauthorized access to over 18,000 organizations worldwide, including government agencies, major corporations, and critical infrastructure providers.
The financial impact of this attack was huge! For damage control, 11% of the companies affected lost their annual revenues. The effect was more significant in the United States than abroad. Here, the average impact accounted for 14% of annual revenue, whereas companies in the U.K. faced losses of 8.6%. Meanwhile, businesses in Singapore suffered a financial setback of 9.1% of their annual revenue.
Attackers used a trusted software vendor to evade standard security measures and gain prolonged access to sensitive networks. This incident highlighted the escalating risk posed by supply chain vulnerabilities. It emphasized the necessity for ongoing monitoring, a zero-trust security model, and rigorous management of third-party risks in companies.
Final Words
Backdoor attacks represent a significant and persistent threat to cybersecurity. By understanding the various types of backdoors, how they operate, and the potential damage they can inflict, individuals and organizations can better protect themselves.
You need to implement strong security measures, stay informed about emerging threats, and remain vigilant in the face of evolving attack techniques. By adopting a proactive approach to security, you can minimize the risks associated with backdoor attacks and protect sensitive information.
Remember, prevention is always better than cure.







