What is Endpoint Security?
Endpoint security is an essential part of modern security that helps organizations implement security control that protects endpoints from varying types of cyber threats. It can also be described as a security practice that protects endpoints which are usually internet-facing devices, and containers from malware, data theft, and unauthorized access.
Cybercriminals are always modifying their methodologies to exploit endpoints through vulnerabilities and get access to sensitive data. Modern endpoint security is constantly evolving so that it can protect the confidentiality and integrity of sensitive data across all endpoints from a range of threats.
Endpoint security has evolved from being just an antivirus program to a comprehensive solution that can protect the endpoints from advanced malware and zero-day attacks. For every organization, endpoint security is considered the frontline defense because it serves as an access point to the whole network.
Most of these security solutions mostly involve endpoint detection and response functionality that proactively identifies threats and neutralizes them. Nowadays, they are also implemented with other cloud security technologies to get visibility into advanced cyber threats and enhance the detection time.
The Importance of Endpoint Security
An endpoint is an important part of an organization because it hosts digital services needed for business workflow, stores sensitive information, and helps teams perform different tasks.
Plus, they also serve as an entry point to any network, making them the most favorable choice for attackers. Since it is often considered the weakest link in an organization’s network, a cyberattack on the endpoints can impact the integrity, availability, and confidentiality of stored data and workflow of the organization.
Endpoint security is critical for an organization’s security strategy because it safeguards against cyber threats, prevents breaches, secures remote workforces, protects sensitive data, minimizes downtime, and complies with regulations.
The increasing number of endpoints due to the rise of remote work has made endpoint security more crucial because the higher the endpoint count, the higher the risk of attacks. The rise of endpoints has led to a rise in different types of endpoints.
Since remote users are not protected by network security controls and they often use personal devices to connect to business networks, it is vital for organizations to utilize endpoint security.
The modern threat landscape is becoming more complicated as hackers are coming up with innovative ways to breach endpoints or manipulate users to provide access and steal information. To navigate such complex situations, endpoint security has become a must-have solution for every enterprise.
The lack of employee commitment towards security and knowledge regarding endpoints’ security makes many endpoints vulnerable to attack. Most of the employees are focused on accomplishing their job rather than their security of the endpoint. So it is important for organizations to implement endpoint security and prevent any vulnerability.
What makes endpoint security more crucial? The increase in adoption of cloud-based services has made the endpoints more susceptible to attack. However traditional security methodologies won’t be sufficient as organizations have to utilize modern endpoint security with cloud-based solutions to offer a comprehensive approach.
When an organization gets endpoint security, it provides them with various functionalities like access control to business-centric devices, continuous monitoring of entry activities, preventing unauthorized users, and others.
Important this security promotes secure remote work in an organization and compels people to take a safer approach while accomplishing their tasks at remote workspace.
Types of Endpoint Devices
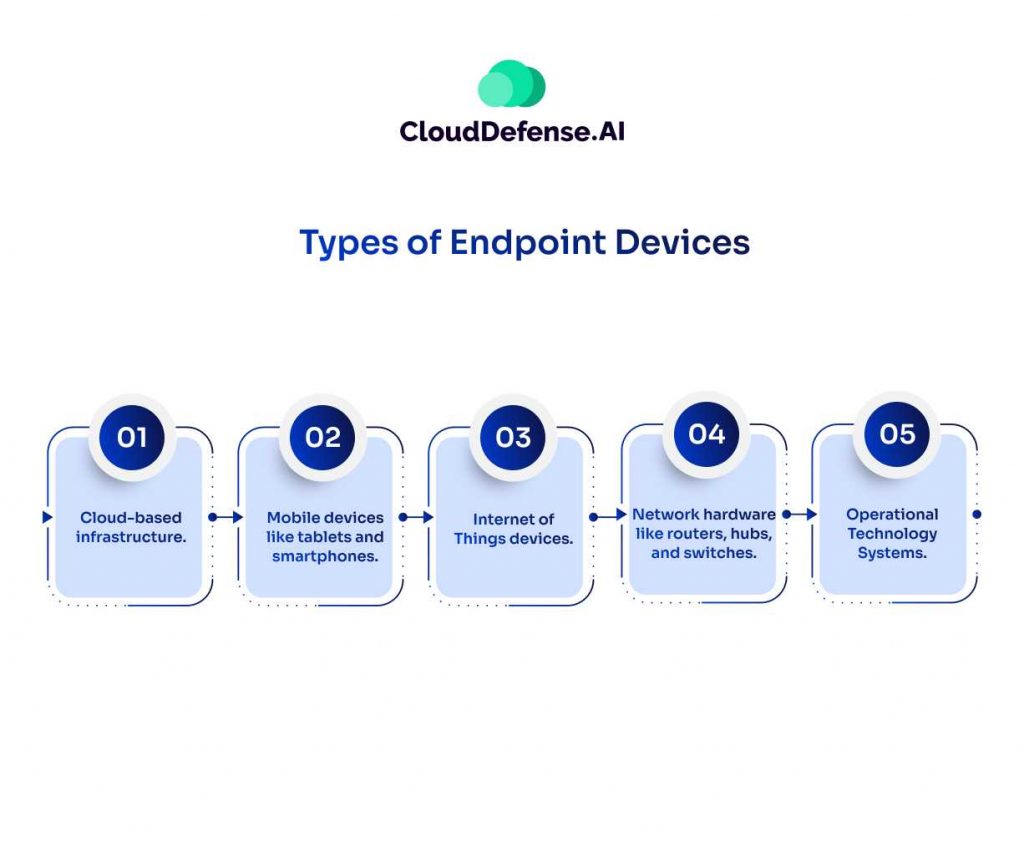
With the usage of remote work models, cloud-based services, and advanced devices to enhance business workflow, corporate networks have diversified in leaps and bounds.
Traditionally, desktops and servers were the only endpoint type that was a part of an IT network. However modern enterprises comprise a varied type of endpoint devices required for different types of tasks and they are:
- Cloud-based infrastructure.
- Mobile devices like tablets and smartphones.
- Internet of Things devices.
- Network hardware like routers, hubs, and switches.
- Operational Technology Systems.
Besides, printers, scanners, ATM machines, medical devices, and automation devices are types of endpoint devices that also serve as a part of an organization’s network that facilitates different workflows.
All the endpoints serve as entry points to networks so naturally they are the primary targets of malicious attack. Each endpoint device type has its own attack vector, adding to the security concerns.
Mobile endpoint devices have expanded beyond smartphones as they include smart wearables, voice-controlled digital assistance, and other smart devices that increase complexity. As different types of endpoint devices have come into play, it has become vital for organizations to have a comprehensive endpoint security strategy that will offer protection to every type.
What are the Different Types of Endpoint Security?
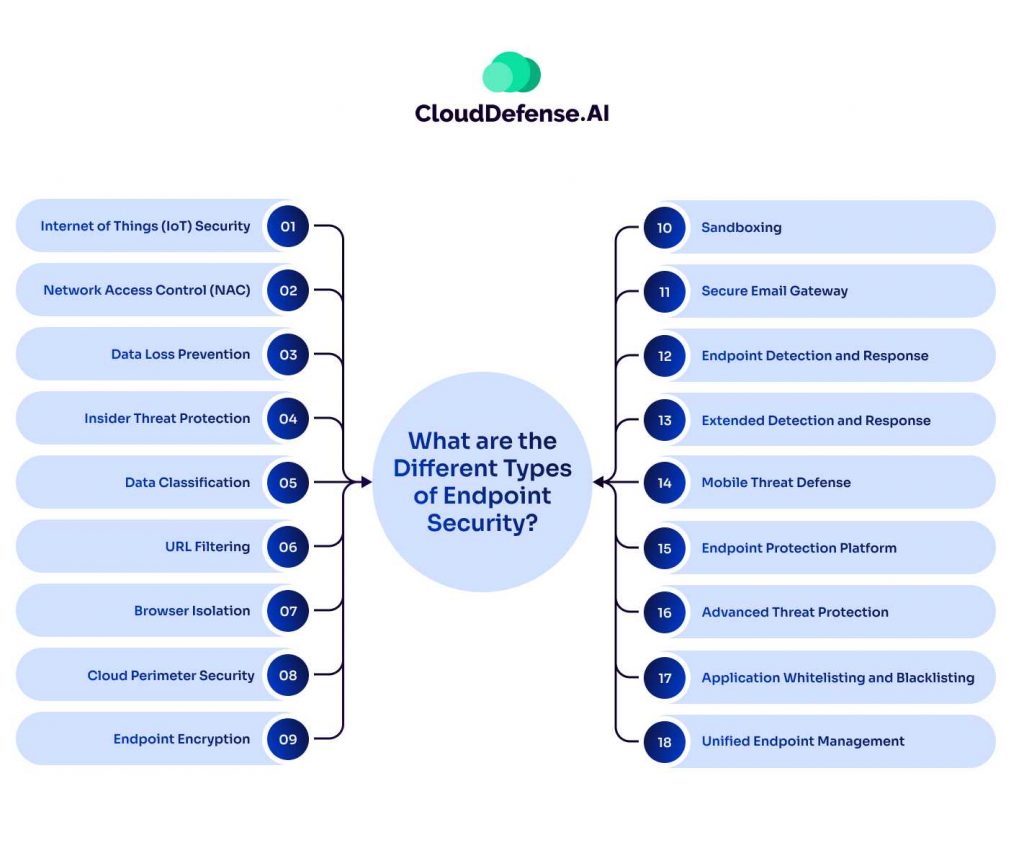
With a variety of endpoints added into modern IT networks, various types of endpoint security have come into play to address diverse sets of security concerns.
From addressing malware and mitigating vulnerability to providing threat detection and response functionality, each Types of Endpoint Security plays a vital role in providing comprehensive protection. Here are the different types of endpoint security you will come across:
Internet of Things (IoT) Security
The use of IoT devices has increased significantly including the one operated by customers connected to your network. Each IoT device can be utilized by malicious actors as an access point to gain entry into your network.
Hence, IoT security serves as an important pillar of endpoint protection strategy because it ensures IoT devices are always available and secure while maintaining data integrity during information exchange. This security type is also instrumental in mitigating IoT-focused vulnerability, malware attacks, and breaches.
Network Access Control (NAC)
Network access control (NAC) is another vital Type of Endpoint Security whose main aim is to provide access to only authorized devices in the network. NAC effectively manages the devices and users who can access your network and what activities they perform after getting access.
It places firewalls between sensitive data, devices, and users and ensures the integrity of the network by constantly verifying the identity and compliance of devices and users.
Data Loss Prevention
Data loss prevention or DLP is an Type of Endpoint Security whose main purpose is to completely safeguard your essential data resources against any kind of threat, breach, or exploitation.
It promotes employee awareness where it focuses on informing employees regarding various cyberattacks including phishing techniques and asking them to install anti-malware programs.
The anti-malware program helps the employee to prevent any malicious attackers place any malware on the endpoints and exploit the data. DLP also utilizes data inspection and monitoring data transfer activity to find out any unusual behavior. By leveraging contextual analysis, it can identify and prevent potential security breaches at the endpoint.
Insider Threat Protection
Insider threat is a serious issue that originates from within the organization and they can be intentional or unintentional. However proper access control to the network and monitoring all the activity of users through insider threat detection tools can help in minimizing insider threat.
You must implement a Zero Trust Network Access tool to control which devices or users can access sensitive data or areas in your organization. Organizations can monitor user behavior to identify malicious intent or mistakes and take mitigation steps accordingly before the threat can cause any damage.
Data Classification
By making use of data classification, your organization can easily quarantine all the vulnerable data and then look for endpoints that can lead to unauthorized access. If your organization is using a remote working model, then your employees will have access to numerous vital information. In such a situation, data classification comes really useful as it helps in identifying the attack surface.
URL Filtering
Uniform Resource Locator or URL filtering is another vital Type of Endpoint Security whose main aim is to shield all the employees in your organization from potential malicious websites. URL filtering is usually performed using software or hardware firewalls where it blocks all malicious websites that can introduce malware at the endpoints.
Browser Isolation
Browser isolation serves as a highly useful Type of Endpoint Security as it runs browser sessions run by employees at endpoints in an isolated environment. Whenever your employees use the browsers, it is completely isolated so that any malicious code entering the endpoint during the browsing session won’t be able to affect the digital assets.
Cloud Perimeter Security
With modern organizations utilizing cloud-based services at endpoints, they require specialized security measures to protect the cloud resources. Cloud perimeter security makes sure all the cloud resources are protected from exploitation by users and devices that are authorized to access them.
To enhance the overall cloud perimeter security, you can implement a cloud firewall and cloud-based web filtering tools that will help you control who can get access to your cloud resources.
Endpoint Encryption
Endpoint encryption is a vital security type that helps in securing all the sensitive data at endpoints through encryption. It encrypts all the sensitive data through an encryption key and only users with decryption can access those data.
Even if attackers penetrate the endpoints, they won’t be able to read the information. Endpoint encryption not only helps employees browse sites and download sites without any worry but also access sensitive files without getting affected by malware.
You can utilize full disk and file encryption at endpoints that seal all the sensitive data and protect them from unauthorized access.
Sandboxing
Another Type of Endpoint Security that can be useful to you is sandboxing where you can create a virtual environment similar to your user operating system and this helps in isolating all the stored sensitive data. Sandboxing is mostly done by users while using specific applications so it can be utilized for various other endpoints in the network.
Secure Email Gateway
A secure email gateway can be utilized to monitor all the email activities in your system and identify any threat originating from it. SEG constantly scans all the emails for suspicious links or malicious attachments and whenever any such email is detected, it quickly prevents the email at the gateway.
Endpoint Detection and Response
Endpoint detection and response or EDR solution serves as a comprehensive security solution that helps security teams to get a complete context on security threats on the endpoints. It performs continuous monitoring and data analytics on all the data sources to get visibility into the security posture.
EDR also assists the team in threat hunting, incident investigation, and threat hunting by leveraging machine learning and together they ensure threat response in real time. It is highly useful in identifying and mitigating advanced and targeted cyberattacks that can’t be intercepted by traditional security measures.
Extended Detection and Response
Also known as the XDR solution, it helps in enhancing the overall endpoint visibility, threat prevention, investigation, and response capability by consolidating endpoint security.
Basically, it brings endpoint security management and monitoring processes into a single platform and enables the team to get complete visibility and easily detect threats.
XDR systems make use of behavioral analysis, big data analytics, and machine learning to improve visibility and analytics and enhance the detection and remediation process. It also comes with the capability to detect anomalies by analyzing patterns across data sources and endpoints and provide reports regarding breaches.
Mobile Threat Defense
Another security solution you can implement to protect your endpoint like mobile and tablet devices is mobile threat defense or MTD. This security solution is designed to implement security measures at those endpoints and prevent any threats targeted toward it. The main work of MTD tools is to constantly monitor the endpoints for suspicious behavior and security misconfigurations on mobile and tablet devices.
Endpoint Protection Platform
The endpoint protection platform serves as a first line of defense at endpoints that comes with all the necessary capabilities to keep all the threats at bay. It can not only identify a variety type of potential security issues but also prevent them from breaching the endpoint security layer.
Advanced Threat Protection
By combining advanced security technologies based on machine learning and artificial intelligence, advanced threat protection can easily detect and prevent advanced cyber attacks at endpoints. The main aim of the ATP solution is to minimize the impact of all the potential security attacks on the organization and reduce the attack surface.
Application Whitelisting and Blacklisting
Another crucial endpoint security type that should be utilized by you is application whitelisting and blacklisting. Application whitelisting enables only specific applications to run on the endpoint while blacklisting prevents other applications from running.
Application whitelisting ensures only authorized applications can be executed at the endpoints which helps in reducing the chance of malware attack and other threats.
Application blacklist blocks all the known malicious software maintained in the list from getting executed. These methodologies run on trust and you will have to maintain a pre-approved list to maintain the flow.
Unified Endpoint Management
UEM is an effective solution that is designed to solve issues related to a rapid increase in remote devices in a corporate network. UEM tools are based on MDM solutions that enable it to provide constant monitoring and management of remote devices.
Final Words
Endpoint security has become a necessary security solution for every organization operating with numerous remote devices. Endpoints facilitate business workflow in different ways, but they also serve as an entry point for attackers. So knowing about different types of endpoint security is essential for your organization because it will help you in addressing different threats and issues.
This article will take you through all the common types of endpoint security types you can utilize in an IT network and protect sensitive data from malicious usage. Apart from types of endpoint security, we have also covered many other aspects that will help you decide the endpoint security you need for optimum protection.







