Modern businesses have used recent technological developments to shift the majority of their operations online. Remote work is more common than ever before, and companies separated by vast distances can share sensitive data instantaneously.
But these advantages also come with risks as the majority of these businesses are connected using web applications. Web applications are vulnerable to a variety of cyber threats. Reportedly, 26% of cyberattacks target web applications and many organizations are not equipped with the strategies or technology necessary to counter them.
Understanding and practicing good web application security is necessary if your organization is to survive and thrive in the lucrative but sometimes dangerous digital environment. Read on as we explore this niche of cybersecurity and point out effective best practices and strategies for you to get going with your web application journey.
What is Web Application Security?
To be short and precise, web application security is a methodology that involves protecting websites or online services against digital security threats. In most cases, digital security threats can exploit web application vulnerabilities found in said application’s code.
In general, web application attacks target content management systems like WordPress, SaaS applications that provide software to large-scale organizations or enterprises using the cloud, and database administration tools such as phpMyAdmin.
Why is Web Application Security Important?
Web application security has a direct impact on protecting sensitive data. The potential exposure of information like passwords, usernames, financial records, and medical data poses a significant risk to your company. Poor security measures allow attackers to commit fraud, leading to severe consequences such as identity theft.
According to Positive Technologies, about 48% of web apps have very low security measures. Failing to protect your web application not only puts user data at risk but also introduces financial vulnerabilities. The aftermath of a security breach may result in great financial loss and take away users who trust your company with the safety of their data.
Security issues can disrupt the timely deployment of your application, especially if identified late in the development cycle. Delays may exert pressure on developers to meet delivery deadlines, potentially leading to the release of applications with exploitable vulnerabilities, which can be hazardous for your company.
How Does Web Application Security Work?
Web application security can have multiple approaches to address different vulnerabilities. One key strategy is the use of Web Application Firewalls (WAFs), which help defend against a wide range of attacks. WAFs monitor and filter the traffic between a web application and users. Configured with policies, they can differentiate between safe and malicious traffic, blocking unauthorized access and preventing the release of sensitive data.
Security measures often include user authentication and access management to control who can access certain parts of an application. App vulnerability scanners identify and mitigate potential weaknesses, while cookie management ensures the secure handling of user data. Traffic visibility tools monitor and analyze web traffic patterns, aiding in the early detection of anomalies. IP denylists further improve security by blocking traffic from known malicious IP addresses.
What Are Common Web Application Security Vulnerabilities?

Web applications are often very complex. While this has allowed web applications to serve a variety of important purposes in business and entertainment, it also means that web attackers have a wide range of ways in which they can harm your organization.
Cross-site scripting (XSS)
XSS vulnerabilities allow attackers to inject client-side scripts into web pages. This allows the attacker to access important information quickly and easily, as well as impersonate different users or authorities
SQL injection (SQLi)
SQL injections are attacks that occur when cybercriminals exploit vulnerabilities within search queries executed by a host database. This allows attackers to get access to sensitive information or even change authorizations or user permissions. They can also destroy or manipulate sensitive data found in that database
Distributed Denial-of-Service (DDoS) Attacks
These infamous cyberattacks occur when hackers overload a target server with junk data or other digital bombardments. Servers can eventually behave slowly or shut down entirely (denying service to legitimate users) when they can no longer process all the incoming requests.
Memory Corruption
Memory corruption vulnerabilities occur when a specific spot in a computer’s memory is modified which can allow for unanticipated or unsafe behavior in installing the software. Hackers can then exploit the memory corruption to gain access to connected networks or programs.
Buffer Overflow
Buffer overflows are anomalous vulnerabilities that happen when software overwrites data in data storage locations adjacent to the target memory space. Malicious code can be injected into memory through this exploit, creating more vulnerabilities to manage. Evaluating your code properly can add an extra layer of protection to your app so make sure to have objective quantifiers for your code as that is one of the top 10 best practices for software testing projects.
Cross-Site Request Forgery (CSRF)
A cross-site request forgery attack occurs when a victim makes a request that leverages their willing authorization or authentication keys. The attacker in question can then masquerade as the user and gain access to sensitive information.
Data Breach
A data breach vulnerability is a general kind of threat that occurs when sensitive or confidential information is released, either by mistake or through malicious actions. There are more types of web application vulnerabilities than these, of course. But the above risks are the most common your organization is likely to face.
These are also the risks your security strategies should focus on mitigating most often.
Remember that web application security is constantly evolving. New threats arise every day, so remaining agile and adaptable is just as important as mastering the following web app security practices.
Web Application Security Best Practices
While web applications are vulnerable in a variety of ways to cyberattacks, there’s good news. Organizations can also leverage a wide range of strategies to mitigate those vulnerabilities or make them impossible entirely. Here are some of the best practices your organization can employ to mitigate any detected vulnerabilities within your systems or web applications.
Web Application Firewall
First is a web application firewall, which can serve as a first line of defense against any malicious HTTP traffic. Think of web application firewalls as filtration barriers to protect your server from any attacker. It can defend against web application threats like SQL injections. As well as cross-site scripting, and cross-site forgery.
Firewalls are not foolproof, however, maintaining good firewall protection and updating firewall virus or cyber threat definitions regularly is one of the best ways you can maximize their effects and minimize your organization’s risk of experiencing avoidable attacks.
DDoS Mitigation
DDoS mitigation strategies often involve distributing incoming malicious traffic to prevent target servers from being overloaded. For instance, the web application security service Cloudflare uses tactics like,
- Dropping volumetric attack traffic at the edge of hosted servers
- Using a proprietary network to route legitimate traffic to target servers without service loss
- This method can be advantageous for businesses that stand to lose income during a DDoS attack
DDoS attacks can usually only be withstood rather than eliminated. Therefore, practicing good web application security strategies like including backup servers or leveraging server traffic rerouting technology might be a good idea before a DDoS attack arrives.
DNS Security – DNSSEC protection
DNS stands for “domain name system” – think of it as the major address for your organization or web application’s server. Sometimes, cybercriminals can try to hijack a DNS request, taking control of a request to locate your server or web application using on-path attacks, DNS cache poisoning, and other methods.
DNS security involves leveraging DNSSEC protection. Such defenses can prevent your servers from being tricked by a bad actor by using a kind of foolproof ID system. Your DNS address will then be relatively safe from hijacking unless the would-be attacker uses another kind of disguise.
Web Vulnerability Scanners
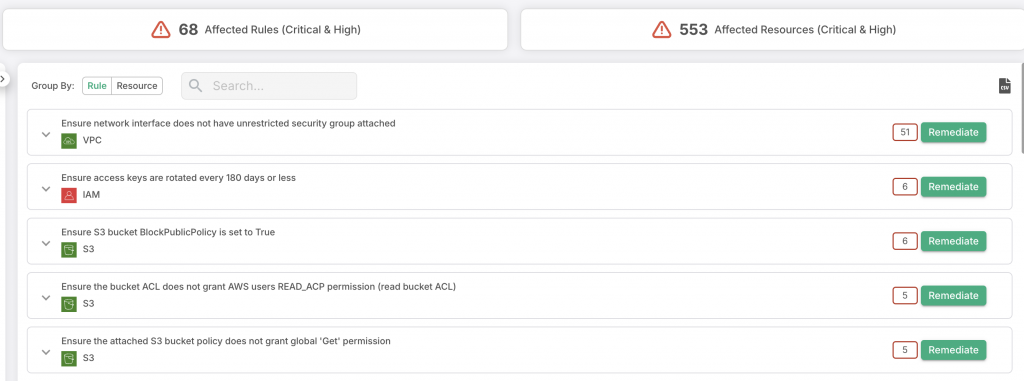
Organizations serious about protecting their web applications might also consider using a web vulnerability scanner (also sometimes called a web application security scanner). A web vulnerability scanner is software that will automatically scan web applications and various websites to identify security issues, like potential vulnerabilities to specific attacks.
Once identified, organizations and their IT security teams can then leverage strategies to remediate or resolve the vulnerabilities and close any proverbial holes in their castles. Black box web vulnerability scanners are leveraged more often than white box scanners.
That’s because these web scanners can be used by almost anyone, including anyone on your IT security team, QA team, or even project managers. In contrast, white box web vulnerability scanners can only be used by developers or those who have access to the scanner’s source code.
How to Choose a Web Vulnerability Scanner
While web application scanners can be effective solutions for your organization, it’s important to know how to choose one. To this end, be sure that you test different web vulnerability scanners with your QA or IT security teams. Certain web security scanners will include features like:
- Automation tools.
- Various levels of user access or privilege.
- Regular updates.
- Additional security functions.
Typically, commercial or paid web security software is better than free web vulnerability scanners. That’s because commercial software is usually updated more frequently, lowering the likelihood of the scanner itself being exploited by a vulnerability. Furthermore, commercial web security software is usually better made and easier to use. You’ll likely benefit from more customer support, as well.
Still, a free web vulnerability scanner may be a better choice compared to no scanner at all. Or, if you are looking for something similar, try our API scanning tool and quickly analyze for known vulnerabilities.
How to Test a Web Vulnerability Scanner
Want to know whether a web vulnerability scanner is a good choice for your organization? Fortunately, there are ways to test its suitability for your systems or applications. For starters, make sure that your chosen vulnerability scanner can actually crawl through and scan your target websites.
Your web application may be built with tools like PHP or a CMS platform like WordPress. Web vulnerability scanners advertise which applications they are suitable for on their download pages, so determining this shouldn’t be too hard. Once you’ve identified a good web vulnerability scanner for your websites, begin by launching a few security scans against your target web apps. Try the scanner on as many web apps as possible to get the most varied results.
How NOT to Test a Vulnerability Scanner
However, one thing you don’t want to do is scan certain web applications known for their vulnerability with a scanner to determine their ability. These include web applications like DVWA and bWAPP, both of which are applications from the OWASP Broken Web Applications Project.
These applications are unique and are likely not at all similar to the applications you actually want to protect. So a good web for ability scanner for those sites may not actually be a good fit for your business.
What You Need to Know About Web Application Security
Web application security is about more than just running an automated scanner and calling it a day. You’ll also need to know how to use the tool effectively and how to correct any vulnerabilities it detects. Let’s break down all the different factors of web application security you need to know to leverage this technology effectively.
Identifying Logical Vulnerabilities
One of the big weaknesses of automated web vulnerability tools is that they can only identify technical vulnerabilities in your web apps. Even with their sophistication and complexity, these tools are merely programs that run based on strict code. They lack the intuition or logic that can only be provided by a supervising IT professional.
Any automated web application security scan should be followed or accompanied by an audit run by someone on your team. That team member can identify logical vulnerabilities that might be missed by the automated scan.
Example of a Logical Vulnerability
Logical vulnerabilities can have just as big an impact on your business as some of the technical vulnerabilities described above.
Here’s an example:
- Say that you have an e-commerce web application.
- Its code has the price contained in the shopping cart specified in its URL.
- For instance, “/shoppingcart/index.php?price=100”
- If a user were to change the price in the URL
- Without changing anything in the shopping cart’s interface, what would happen?
- Your IT security team member could test this possibility manually
- The Team will figure out if it will update automatically or is it a logical vulnerability
- For instance, they could see if a hypothetical user could change the price to $30 instead of $100 and get away with ripping your business off
An automated tool would never detect that vulnerability since it doesn’t have the logic to see why it’s wrong.
Switch Off Unnecessary Functionality
Your web applications’ and servers’ security can be affected by various other components as well. Since most modern technology is interconnected to a greater degree now than it ever was before, a single breach into one component connected to the others could allow a malicious actor access to your greater application network or system.
Therefore, one good web application security practice involves turning off any unnecessary functionalities. If your network service or operating system has a ton of functions running at the same time, it just opens up more doors that can potentially be exploited by a cybercriminal.
It’s just good security practice to switch off or disable any services, daemons, or other functionalities that aren’t being used by your web apps.
But shutting off these functionalities just once may not be enough – be sure that you turn any services off permanently to prevent them from restarting and opening up the same vulnerability again.
Limit and Secure Remote Access
By default, any server administrators should be able to locally login to the web server’s control panel. This is all that’s necessary for most server functions. Therefore, try to limit or secure any remote access to your enterprise’s servers.
If you absolutely have to use remote access, try to encrypt and tunnel said remote access traffic to limit the possibility of the traffic being hijacked and your servers being breached.
But it’s always better to just limit remote traffic as much as possible.
Permissions and Privileges
Many web administrators have run into frustrating scenarios where even limited restrictions have made some tasks difficult or impossible to complete. So it can be tough to add privilege or permission restrictions to administrator accounts.
Instead of limiting your administrators, consider adding a secure web server that allows administrators to do their jobs without opening up those servers to other users. You might also consider having administrators use different accounts to perform different tasks, such as backing up data.
Furthermore, you should make doubly sure that everyone in your organization has the right privileges and permissions and that those permissions are not doled out unnecessarily. Most database users for your web application don’t need special privileges to create functions or assets, for example.
Avoid giving all new accounts all permissions even if it seems easy and simple at the time. It opens up your application to future exploitation by bad actors, and not necessarily your account users.
Segregate Development, Testing, and Live Environments
Lastly, you can practice good web application security by segregating your development, testing, and live environments. Mixing these environments can lead to complex issues that may make your web app more vulnerable to intrusion by a hacker.
That’s because many developers, without any ill intentions, often leave traces of their activity behind when developing or troubleshooting web applications they’re working on. One good example is debug panels, which may be left enabled with sensitive information that can be exploited by hackers.
It’s a much better idea to have your developers do any troubleshooting or web development in a proper staging environment that’s isolated from other environments. Administrators can apply any changes to live environments after all development and testing are complete.
As a bonus, this allows you to double-check the new version of a web app environment for security vulnerabilities or last-minute things to be fixed before launch. When combined with a security-focused SDLC (systems development life cycle), the odds of your developers accidentally leaving a security flaw behind are much lower.
Web Application Security Strategy
By now you should know how important it is to have proper web application security measures in place. However, it is best to start with a checklist that helps you create a proper strategy. Here are some recommendations to start with your web application security strategy:
- Create an application inventory
- Develop cybersecurity best practices
- Implement access management and credential security
- Hire White Hat hackers
- Regular data backup procedures
- Continuous security measure review
- Vendor monitoring
- Implement WAF
- Deploying scanning tools
- Collaboration with security experts
FAQs
What Does Web Application Security Mean?
Web application security is the practice of maintaining good operational security practices and minimizing the entry points for hackers or other cybercriminals.
How Do You Secure a Web Application?
Web applications are primarily secured using firewalls. Firewalls can be found in both hardware and software versions. However, web applications can also be secured by:
1. Gathering information, such as by using an automated web vulnerability scanner or manually
2. Using appropriate authorization to prevent people from stumbling into developer environments
3. Preventing low-level organization employees from gaining access to administrative privileges
4. Encrypting data and traffic
5. DDoS defenses, which lower the likelihood of a web application’s hosting server crashing when it comes under bombardment by a sudden high-traffic attack
Why is Security Important in Web Applications?
Web organizations need to secure their applications to lower the risk of being attacked and of any inevitable attacks being successful. If web application security is not prioritized:
1. Sensitive organization information can be stolen
2. Client relationships may be damaged
3. Client or user personal information can be stolen and sold on the black market
4. Organization licenses can be revoked, especially if the organization is found to be in breach of compliance protocols like the GDPR
Conclusion
Ultimately, web application security is a major part of modern organizational risk management. Web applications are more at risk now than ever before, so executives and managers must take the right steps necessary to secure their web applications against new threats. Leveraging technology and smart methodologies can go a long way toward minimizing the effects of even the most dangerous cyberattacks.







