vulnerability Management
Top-tier Vulnerability Management Solution
Stay Ahead of Threats, Secure Your Cloud Infrastructure!! Discover, Assess, and Fix Vulnerabilities across multi-cloud environments with our leading Vulnerability Management Solution

Cloud Security Risk Assessment
Find out which misconfigurations are lurking in your cloud
vulnerability Management
Agentless Vulnerability Management: No Agents, No Hassle
Achieve top-notch vulnerability detection and mitigation with our agentless solution, thereby fortifying your cloud infrastructure with proactive protection.

Agentless Security Assessment

AI-powered Remediation

Comprehensive Vulnerability Assessment

Developer-Centric Productivity Boost
Our Comprehensive Approach to Vulnerability Management
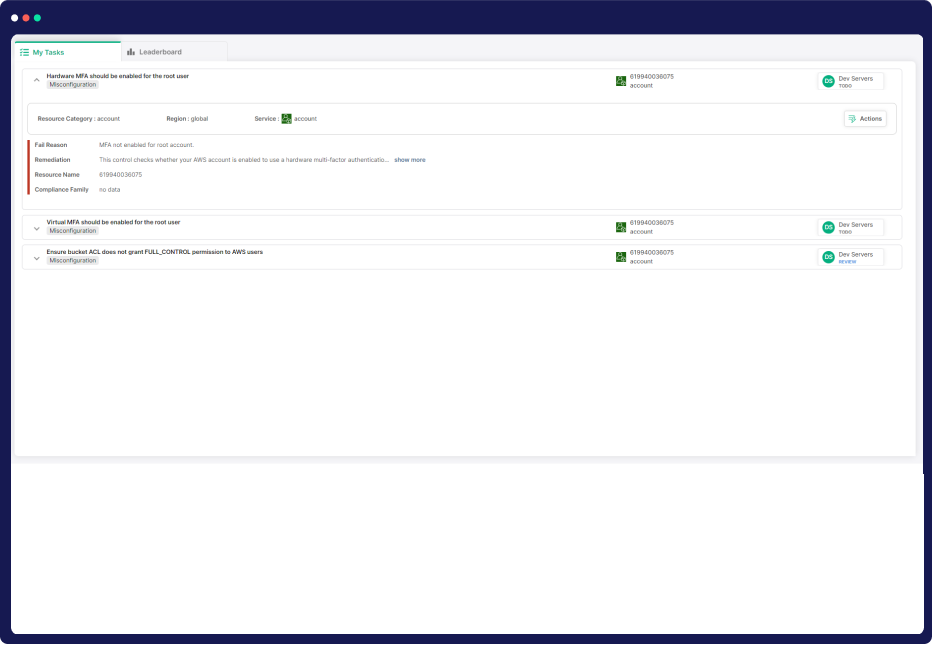
Comprehensive Cloud Vulnerability Management Suite
Full Cloud Inventory
Gain a complete overview of your cloud environment with CloudDefense.AI. We meticulously catalog your cloud assets, including OS packages, applications, libraries, and versions.
Multi-Source Vulnerability Data
CloudDefense.AI harnesses data from over 20 vulnerability sources. We ensure comprehensive coverage, enabling you to discover and address vulnerabilities across your entire cloud estate.
Context-Driven Prioritization
Unlike other solutions, CloudDefense.AI considers the context of your cloud assets, their connections, and associated risks. We empower you to focus on the vulnerabilities that pose the greatest threat to your business.
Rapid Log4Shell Response
In high-pressure situations like Log4Shell, CloudDefense.AI allows you to swiftly pinpoint vulnerable cloud assets and prioritize patching them to protect your business from imminent threats.
Modern Query Builder
CloudDefense.AI's modern query builder simplifies the process of querying your entire environment. Easily access insights on vulnerabilities, risk levels, and contextual information, enhancing your security posture.
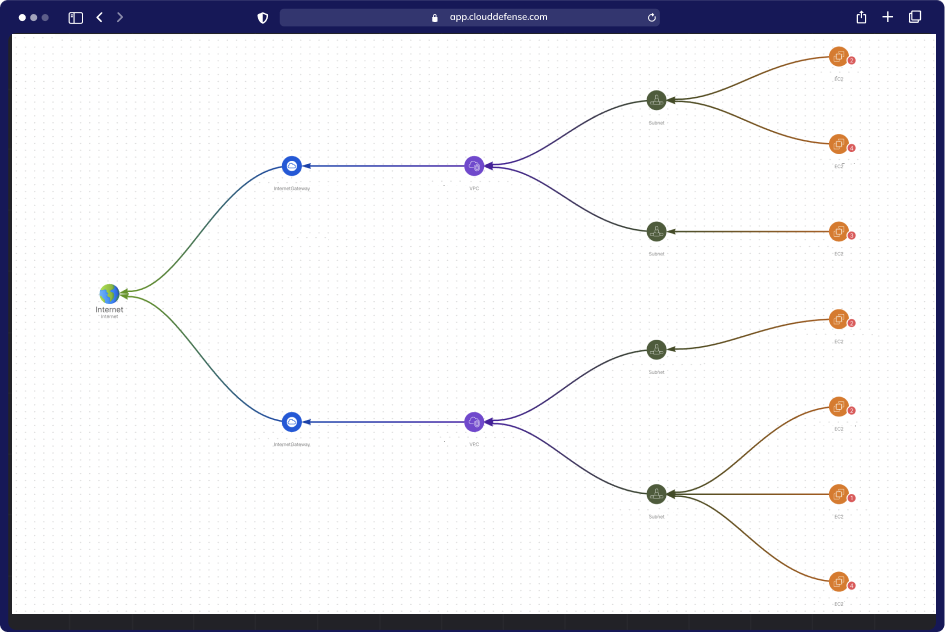
Uncovering Complex Risk Interdependencies
Attack Path Analysis
CloudDefense.AI employs Attack Path Analysis to unveil interconnected risks, pinpointing the most perilous combinations. Our advanced algorithm assigns business impact scores, streamlining your security strategy.
Prioritization & Focus
Score and prioritize attack paths with ease. Our system helps security teams concentrate on the most dangerous paths, eliminating the need to sift through countless alerts. Maximize efficiency.
Visual Graphs
Gain clarity with visual graphs. Each attack path is presented visually with contextual data about cloud entities (IAM, compute, storage) and their relationships. Understand vulnerabilities at a glance.
Remediation Guidance
CloudDefense.AI provides clear guidance on the risks that must be addressed to disrupt attack paths. Streamline your remediation efforts by focusing on issues that impact multiple paths. Boost your cloud security.
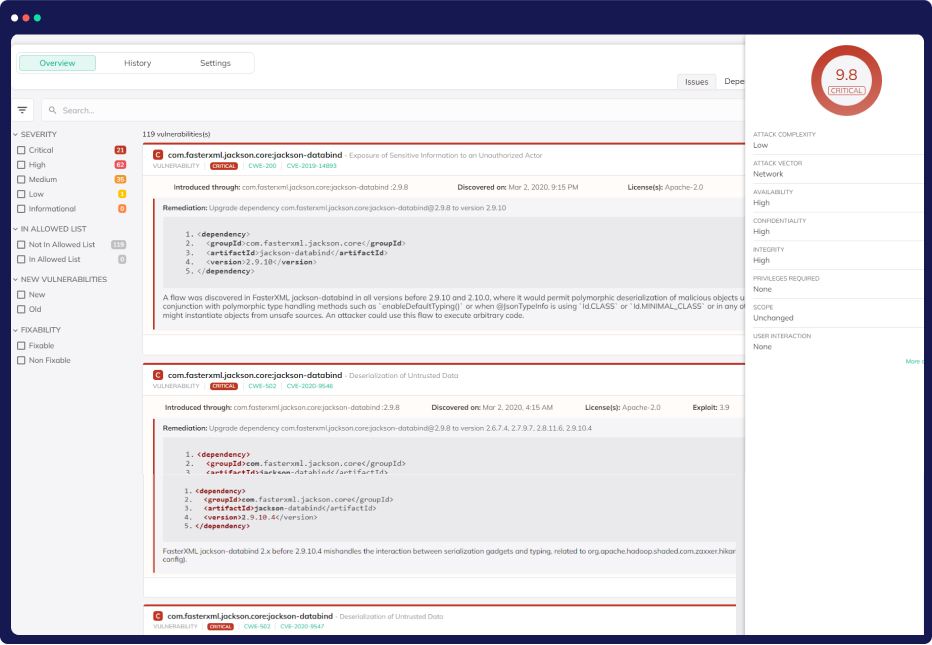
Streamlined CVE Impact Analysis
Unified Asset Visibility
CloudDefense.AI provides a comprehensive view of all assets, workloads, identities, and data, allowing you to quickly locate and understand the impact of new CVEs on your environment.
Real-time CVE Insights
Stay ahead with our "From the News" widget, which automatically highlights breaking and trending CVEs while offering instant analysis of their presence and impact in your environment.
Effortless Querying
Easily query your environment to access detailed CVE information and contextual insights, including Internet exposure and configuration status, enhancing your risk assessment.
Risk Correlation Visualization
Explore how vulnerabilities intersect with other potential risks through our intuitive visualization tool, empowering you to make informed decisions for risk mitigation.
Pre-deployment vulnerability Assessment
CI/CD Integration
Seamlessly integrate security into your CI/CD pipeline by scanning VM and container images, preventing vulnerable resources from reaching production.
Container Registry Scanning
Detect vulnerabilities and security risks in container images with regular registry scans, ensuring secure deployments to your runtime environment. Stay ahead with CloudDefense.AI.
Automated Vulnerability Detection
Safeguard your applications by automating vulnerability detection, proactively identifying and eliminating security threats before they can compromise your deployment process.
Risk Mitigation Assurance
With CloudDefense.AI, ensure risk mitigation assurance as you prevent vulnerabilities before deployment, strengthening your application's security posture from the very beginning of the development cycle.
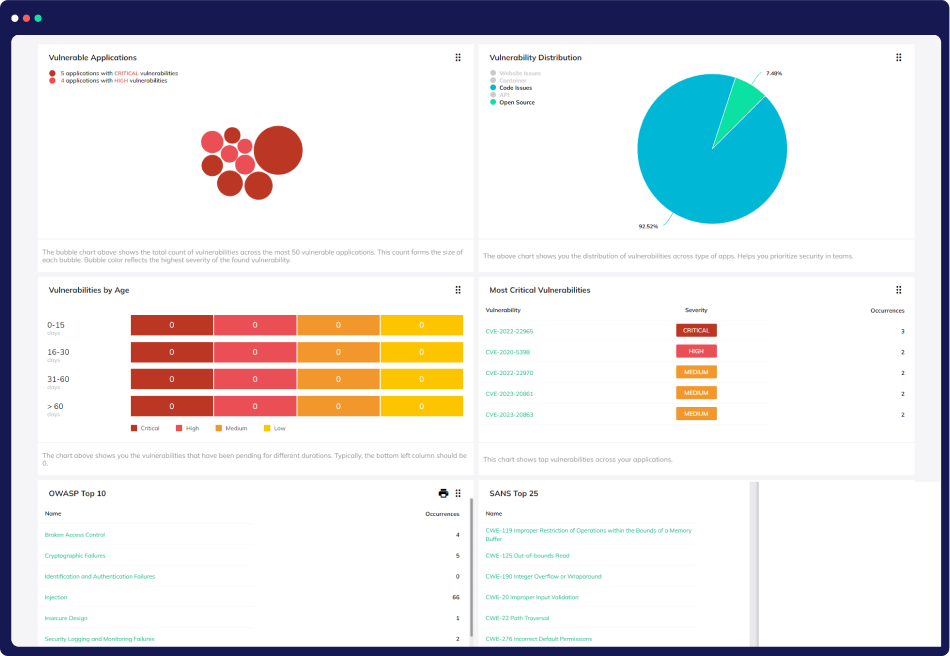
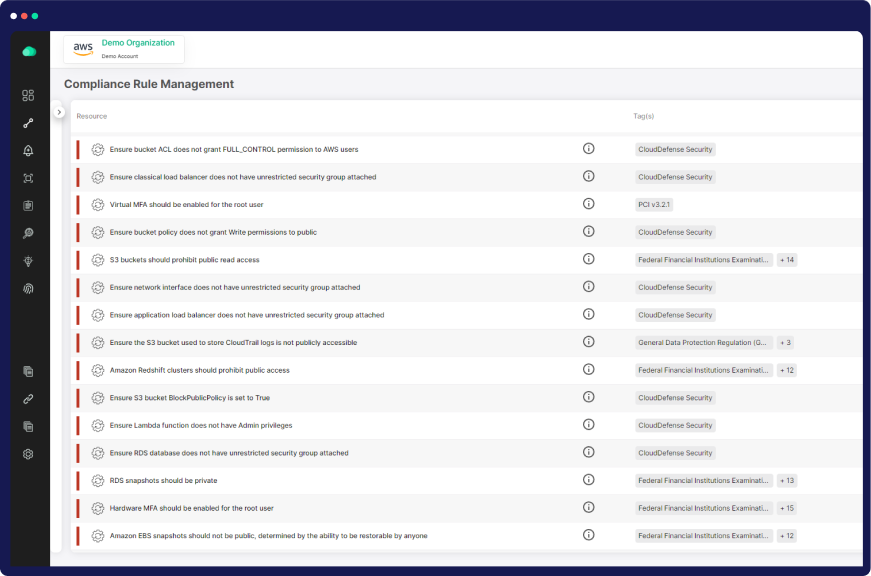
Compliance Assurance and Optimization
Proactive Threat Mitigation
Detects and proactively neutralizes cloud threats to protect sensitive data and maintain compliance.
Adherence to Security Standards
Ensure alignment with key security standards like AWS Well-Architected, CSA, NIST, ISO 27001, and SOC II.
Legal Risk Mitigation
Safeguard your organization from potential legal consequences stemming from security compliance lapses.
Compliance Workflow Optimization
Optimize compliance workflows for smoother adherence to industry benchmarks and regulatory requirements.




