What is the DevSecOps Lifecycle?
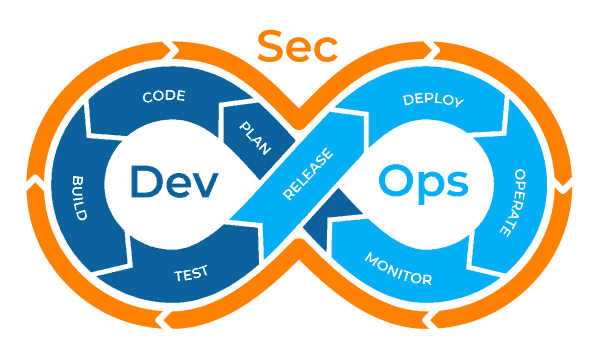
The DevSecOps lifecycle integrates security throughout every stage of software development, embedding security practices into the planning, coding, building, testing, releasing, deploying, operating, and monitoring phases.
This approach shifts security “left,” addressing potential vulnerabilities early when they’re easier and more cost-effective to fix. By automating security scans, tests, and vulnerability assessments within CI/CD pipelines, DevSecOps ensures faster, more secure releases while maintaining the agility of DevOps.
It promotes collaboration between development, security, and operations teams, aiming for a proactive approach to risk management and compliance that safeguards production environments and enables resilient, secure software delivery.
Steps in the DevSecOps Lifecycle
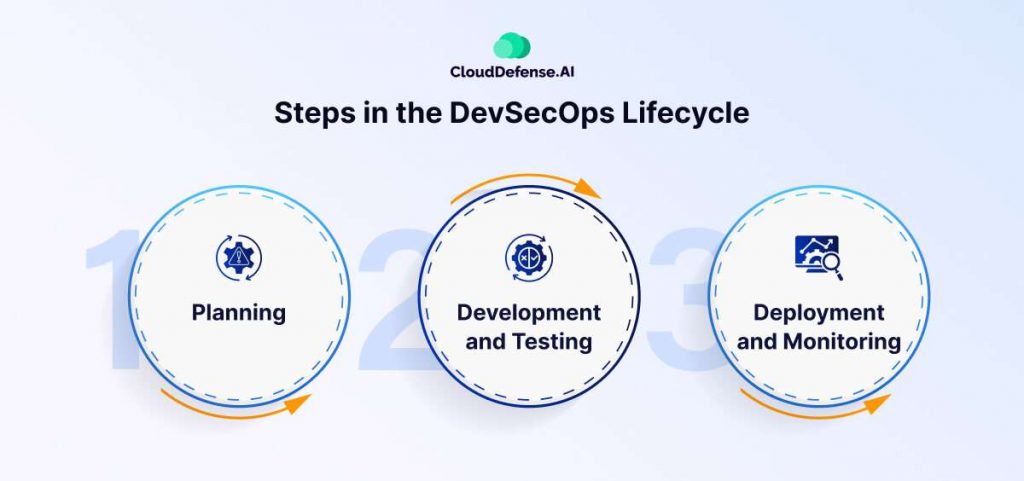
DevSecOps lifecycle comprises multiple steps, and most of the steps are repeated in a loop as the organization deploys new updates and features. Here are the steps that we are talking about;
Planning and Security Integration
In the planning phase, development, security, and operations teams collaboratively define security objectives and identify potential risks early on. Effective planning helps outline clear security requirements and the necessary policies that will guide secure coding practices.
Tools like CSPM come into play by helping to define and monitor security benchmarks for cloud environments, ensuring foundational configurations are secure from the start.
Development and Continuous Integration
During the development phase, teams start building the application and integrate automated security testing directly into their CI/CD pipelines. Here, SAST plays an important role, enabling code scanning to catch vulnerabilities within the source code before it reaches production.
Additionally, SCA assesses any open-source or third-party libraries for known vulnerabilities, which is especially important for managing dependencies and minimizing risk from external components.
Deployment and Configuration Security
As code is deployed, security checks need to be applied to ensure configurations and infrastructure settings remain secure. In this stage, DAST comes into the workflow to perform runtime analysis.
DAST simulates attacks on the deployed application to uncover vulnerabilities in real-time, providing insights into how the application might respond to live threats. IaC practices also improve deployment consistency and security by automating infrastructure setup with predefined security configurations.
Monitoring and Incident Response
Once the application is live, real-time monitoring detects potential security incidents or anomalies that could indicate threats. Regular scanning using CSPM tools identifies any misconfigurations or compliance issues in the cloud environment, while periodic DAST scans and runtime monitoring help keep applications resilient to emerging risks.
Additionally, incident response protocols allow teams to react swiftly to detected threats, and post-incident reviews provide insights that can be used to strengthen future security practices.
Benefits of the DevSecOps Lifecycle
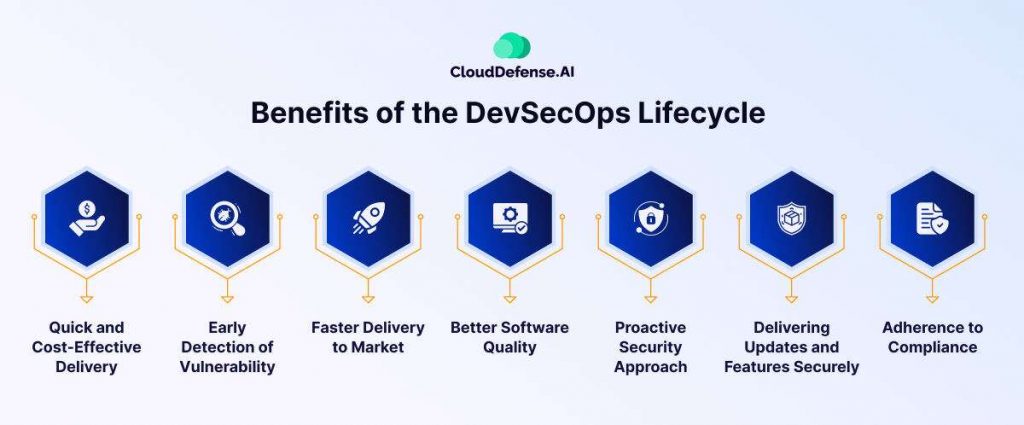
Implementing the DevSecOps lifecycle in an organization provides numerous benefits. Speed and security may be the primary benefits, but there are many other perks that make it suitable for most modern organizations. These benefits are:
Quick and Cost-Effective Delivery
In traditional application development, security problems are always fixed in the end, leading to huge costs and time delays. However, by implementing DevSecOps, organizations can save time and minimize costs as it enables quick and secure delivery. DevSecOps helps organizations to reduce the repetition of various processes for responding to security issues.
Early Detection of Vulnerability
Implementing security in the early stage of the development lifecycle enables the team to detect vulnerabilities, gaps, and other security issues at an early stage. This is highly beneficial for the team because they can quickly mitigate the issue at an early stage with limited resources and prevent them from making any significant impact.
Faster Delivery to Market
Another considerable advantage of DevSecOps is that it allows developers to automate the security testing of codes and prevents security testing from being a time-consuming process. Thus, it enables the organization to swift up the development process and deliver applications quickly with high accuracy and quality.
Better Software Quality
Since codes are continuously reviewed, audited, scanned, and tested for security issues at every stage, it helps the organization improve overall application quality by a large margin. Developers are able to mitigate the security issues early in the development stage, and it makes the application much more reliable.
Proactive Security Approach
DevSecOps brings the culture of making everyone responsible for the security of the application, so it makes every team accountable for the security of the code. Throughout the development lifecycle, all the codes are constantly evaluated, and vulnerabilities are immediately mitigated before they can make any impact.
It also curbs the time that security teams have to invest to solve security issues and helps them focus on other security aspects of the application.
Delivering Updates and Features Securely
Security, development, and operation teams in DevSecOps culture use standard security tools for automating the testing and reporting process. Every team makes an effort to add value to the application by adding new features and making updates according to customer feedback without compromising on security.
Adherence to Compliance
DevSecOps has been instrumental for organizations in complying with various regulatory requirements by implementing best security practices and policies. Integrating cyber security into the SDLC enables the organization to meet all the requirements and ensure optimum data protection.
Which Software Development lifecycle (SDLC) Approach is Most Compatible with DevSecOps?
When it comes to choosing the SDLC approach for DevSecOps, there is no particular precondition. Every team adopting DevSecOps practices will have to opt for shift left security practice.
However, it is often seen that organizations adopting Agile SDLC have benefited the most because this approach offers the best compatibility due to its emphasis on collaboration, continuous improvement, and flexibility.
Organizations can easily integrate cyber security into every phase of the Agile development lifecycle and deliver a reliable and secure application. From planning, designing, and development to deployment, the organization has benefited greatly by using the Agile approach in SDLC.
This approach allows organizations to comply with all the industry regulations and standards without compromising on speed and quality. Moreover, it also enables organizations to respond quickly to change requests and security incidents, which ultimately helps DevOps to deliver safer codes.
Organizations widely prefer the agile approach because it enables them to deliver software quickly and efficiently while eliminating the chance of any security issues or vulnerabilities.
Automate DevSecOps Testing
Automation in DevSecOps has become essential, accelerating software delivery and ensuring robust security without compromising development speed. Automating security testing allows organizations to detect and fix vulnerabilities in real-time, achieving faster, more reliable delivery cycles while enhancing overall application security.
Why Automate DevSecOps Testing?
Automating DevSecOps testing provides multiple benefits:
- Consistent Security Checks: Automation enables continuous, consistent testing as code is pushed, reducing the likelihood of vulnerabilities slipping into production.
- Reduced Human Error: By minimizing manual testing, automation eliminates human error, ensuring that tests run accurately and on schedule.
- Enhanced Efficiency: Automated testing frees up time for security and development teams to focus on strategic tasks that add value to the application.
Automated security testing also restricts developer access to production environments, a vital practice for protecting sensitive data. Detecting vulnerabilities early in the development pipeline not only minimizes security risks but also reduces the time and cost required to address issues down the line.
Key Areas for Automating DevSecOps Testing
Effective automation requires identifying specific areas that benefit most from automation, including:
- Code Quality Checks: Implementing automated SAST during the coding phase identifies issues within the source code, including coding errors and security weaknesses. SAST tools automate code quality checks to ensure each new version meets security standards before moving forward.
- Container Security Scanning: Containers are central to modern DevSecOps pipelines, but they introduce security risks if not managed correctly. Container scanning tools automate vulnerability assessments of container images, ensuring secure deployments without manual checks.
- Application Composition Analysis (SCA): Many applications rely on open-source libraries, which may have known vulnerabilities. SCA tools automate the scanning of dependencies, identifying outdated or vulnerable packages and suggesting secure alternatives. This helps secure the application stack without adding manual overhead.
- Automated Vulnerability Scanning: Security teams commonly deploy DAST tools to simulate real-world attacks and detect vulnerabilities at runtime. These scans help security teams validate the effectiveness of security measures in staging and production environments.
- Web Application Scanning: Automated web application scanning tools perform continuous vulnerability checks on web interfaces. This protects the organization against common web application threats, like SQL injection and cross-site scripting, which are often exploited in real-world attacks.
What Are the Challenges When Enabling DevSecOps?
Implementing DevSecOps is not simply about adopting a new methodology; it introduces complex challenges that impact development, security, and operational teams. Key challenges include:
- Cultural Shift to Security Focus: Shifting from traditional development to a DevSecOps mindset can overwhelm teams used to separate development and security roles. Higher management must bring attention to this change by providing necessary training and emphasizing security-first practices across all functions.
- Compatibility with Open-Source Tools: Many DevOps teams rely on open-source libraries and scripts that may not align with DevSecOps security standards. Here, SCA tools become essential, ensuring third-party components meet security compliance and flagging vulnerabilities in dependencies early.
- Tool Overload: Introducing numerous tools in the SDLC can overwhelm less-experienced DevOps teams. Starting with core tools like SAST and DAST for code and runtime security and gradually adding others can help ease the transition.
- Multi-Cloud Complexity: With most organizations using multiple cloud providers, maintaining a consistent security posture across cloud environments can be challenging. CSPM solutions aid by offering visibility, monitoring, and compliance checks across different cloud services, reducing the risk of configuration errors and non-compliance.
- Alert Fatigue and Prioritization: Security teams are often inundated with alerts from various security tools, resulting in alert fatigue. Noise reduction and risk-based prioritization features can help focus attention on critical threats, ensuring teams act on high-risk issues rather than low-risk alerts.
- Striving for Perfection: While trying to perfect DevSecOps, organizations can become bogged down by excessive integrations. Prioritizing essential security integrations at each stage and refining them over time will ensure smoother implementation without overwhelming the team.
FAQ
Is DevSecOps part of SDLC?
Yes, DevSecOps is a part of SDLC, and it spans the entire lifecycle, starting from planning, designing, and coding to testing and release.
SDLC serves as a framework that defines different stages of application development, whereas DevSecOps serves as a methodology that integrates security into the SDLC. DevSecOps just extends the methodology of DevOps processing by introducing security into SDLC and enabling more secure and better-quality application delivery.
What are the phases of the DevSecOps lifecycle?
The DevSecOps lifecycle is based on multiple phases, and each phase plays a vital role in ensuring secure software delivery. The phases include planning, coding, building, testing, release, deployment, operating and monitoring.
Without any of the phases, the DevSecOps lifecycle won’t be complete. These phases provide the detailed guidelines that every organization must follow while implementing DevSecOps in their organization.
Is DevSecOps agile?
Even though DevSecOps and Agile are relatively similar concepts, they aren’t exactly the same thing.
Agile is all about bringing flexibility and readiness in application development, whereas DevSecOps is about integrating security as part of the development process. However, DevSecOps is most compatible with the Agile framework in SDLC as both of them follow the principles of continuous improvement and flexibility.
What is the core principle of DevSecOps?
The core principle of DevSecOps is to enable quick development processes with a secure code base. DevSecOps tries to implement security in every phase and ensures the application is reliable and secure.
The core principle of DevSecOps also involves delivering frequent releases of updates or features using agile methodologies. It also embraces the culture of automating security testing wherever possible in the development phase.
In which phase of the DevSecOps lifecycle do we do threat modeling?
The initial phase, especially the architecture and design phase of the application development, is ideal for threat modeling. Ideally, the threat modeling should be defined at an early phase, and then it should be refined throughout the development lifecycle.
Conclusion
It is vital that every organization should understand the DevSecOps lifecycle as it can benefit their application development process in a lot of ways. It is one of those methods that ensure faster and more secure delivery of applications to the market.
It extends the principles of DevOps along with the integration of security at every phase of the development lifecycle. With DevSecOps, organizations will achieve security and flexibility and also allow developers to quickly introduce updates and features according to the demand.







