2024 has been a critical year for cybersecurity. The frequency and scale of cyberattacks have reached new heights, targeting critical systems, businesses, and personal data. These attacks have exposed vulnerabilities in even the most advanced technologies.
In this article, we’ll break down the the top 10 data breaches of the year—what happened, how they worked, and why they matter. Understanding these events is critical as we navigate an increasingly digital and interconnected future.
The Current State of Cybersecurity in 2024
Cybersecurity today is one of the biggest challenges we face. It’s real, it’s serious, and it’s affecting everyone—businesses, governments, individuals. The systems we rely on are under constant attack, and the bad actors are getting smarter. We need to understand the reality. Let me break it down for you:
- The rise of AI-driven threats: Advanced artificial intelligence is being weaponized. Hackers are automating phishing campaigns, developing polymorphic malware, and even bypassing traditional security systems with AI tools that learn as they attack.
- Expanding attack surfaces: With the proliferation of IoT devices, cloud platforms, and remote work setups, the number of potential entry points for attackers has exploded. Many organizations struggle to secure these complex networks.
- Data as the ultimate target: Data remains the most valuable asset. Whether it’s customer information, intellectual property, or operational data, attackers are constantly seeking ways to monetize stolen or encrypted data.
- Nation-state conflicts spilling into cyberspace: State-sponsored attacks are blurring the lines between geopolitics and cybersecurity, targeting critical infrastructure, financial systems, and even democratic processes.
Why This Is a Big Deal
We’re not doing enough to protect ourselves. Companies and governments are reactive—they wait until something happens before they take action. That’s a bad strategy.
- Budgets are misplaced: Even with all the money being spent on cybersecurity, it’s not being used effectively. Instead of building strong systems, most organizations are just patching up problems as they arise.
- Laws aren’t keeping up: Our governments are behind on this. They’re trying, but the rules we have don’t match the speed of what’s happening out there. Hackers know this, and they take full advantage.
- Loss of Trust: Every time there’s a breach or an attack, people lose trust—in their banks, in their governments, even in the technology they use every day. And once trust is gone, it’s incredibly hard to get back.
This is where we are right now. It’s not good. But it’s also not hopeless. The top cyberattacks of 2024 will show exactly why we need to wake up and start treating cybersecurity as a top priority. Let’s dive into them.
Top 10 Data Breaches of 2024
1. National Public Data Breach
Impact: 2.9 billion (affecting 1.3 billion individuals).
In April 2024, National Public Data (NPD), a subsidiary of Jerico Pictures, Inc., experienced one of the largest data breaches in history. Hackers gained unauthorized access to 2.9 billion records containing critical personal information, including Social Security numbers, addresses, email IDs, and phone numbers. This breach was not a minor incident; it exposed the identities of 1.3 billion individuals and put their data at significant risk.
The breach reportedly began in late 2023, with malicious actors targeting NPD’s servers. By April, the data was circulating on dark web forums, eventually being sold for millions. The fallout is that NPD’s reputation was shattered. They now face lawsuits and investigations, and the company even filed for bankruptcy in October.
How It Could Have Been Prevented
This breach underscores the importance of robust data protection measures. Here’s how NPD could have prevented this incident:
- Stronger Perimeter Security: Enhanced firewalls and intrusion detection systems could have stopped the unauthorized access before it escalated.
- Encrypted Data Storage: Encrypting sensitive data would have rendered the stolen records useless to attackers.
- Regular Security Audits: Periodic system audits could have identified vulnerabilities and mitigated risks before the breach occurred.
- Employee Training on Security Protocols: Ensuring staff understood and adhered to strict data handling protocols would have reduced the likelihood of human error contributing to the breach.
2. Ticketmaster Data Breach
Impact: 560 million Customers
In May 2024, Ticketmaster faced one of the largest data breaches of the year. Hackers broke into their systems and leaked the personal and financial information of over 560 million customers. This included payment details, order history, names, addresses, and email accounts. The stolen data was quickly offered for sale online, putting millions of people at risk.
Ticketmaster responded by emailing affected customers, advising them to keep a close watch on their accounts and credit statements. However, the fallout doesn’t stop there. Live Nation, Ticketmaster’s parent company, is under fire, with the Justice Department preparing a federal antitrust lawsuit.
How It Could Have Been Prevented
This breach could have been prevented with smarter, stronger security measures. Here’s what should have been done:
- Tokenizing Payment Data: Payment details should have been replaced with secure tokens. If hackers get in, they find nothing useful.
- Isolating Sensitive Data: Key customer data must be stored in separate, secured networks. It limits exposure.
- Regular Security Audits: Ticketmaster needed more frequent vulnerability checks and stricter controls.
A breach of this size is unacceptable for a company of Ticketmaster’s scale. Strong leadership and serious investments in cybersecurity are the only way to protect customers and prevent these failures in the future.
3. AT&T Data Breaches
Impact: Over 110 million individuals
In 2024, AT&T faced two major data breaches that impacted over 110 million individuals. The first breach, which surfaced in April, involved unauthorized access to customer call and messaging metadata from 2022. This information was stored on a third-party cloud platform, reportedly Snowflake. While no communication content was exposed, the stolen metadata could be used to track user locations and contact patterns.
The second breach was even more concerning. Hackers obtained 73 million customer records, which included sensitive data such as full names, addresses, phone numbers, and encrypted account passwords. In response, AT&T issued a forced reset of 7 million passwords to secure customer accounts and prevent further unauthorized access.
How It Could Have Been Prevented
This breach was preventable with more robust security practices. Here’s what could have made a difference:
- Stronger Cloud Security: A thorough vetting process and enhanced security controls for third-party cloud providers like Snowflake could have significantly reduced the risk of unauthorized data access.
- Advanced Threat Detection: Real-time monitoring of unusual activity within data storage systems could have identified the breaches earlier, minimizing the damage.
- Strong Encryption: Applying end-to-end encryption for all customer data, including metadata, would have rendered the stolen information useless to attackers.
- Faster Response: Immediate action, such as rapid password resets and public disclosures, would have minimized the impact of the breaches and maintained user trust.
4. UnitedHealth Data Breach
Impact: 100 million Individuals
In February 2024, UnitedHealth, one of the largest healthcare providers in the U.S., reported a breach that could affect up to 100 million people. This breach is on track to be one of the biggest in the country’s history.
The attack targeted UnitedHealth’s payment processing system, which is run by Change Healthcare. Hackers used ransomware to lock down the system, causing significant disruptions to patient care and financial processes. For many patients, this meant delayed treatments and payments. Beyond that, the breach exposed sensitive information, increasing the risk of identity theft.
How It Could Have Been Prevented?
- Stronger Network Security: Had UnitedHealth used better network segmentation, they could have limited the damage. If the attackers only gained access to one part of the network, they wouldn’t have been able to access everything.
- Better Ransomware Protections: More robust ransomware defense tools might have helped detect the threat before it could spread. Behavioral analysis software can identify unusual activity, stopping the attack early.
- Regular System Updates: Making sure that systems are regularly updated with the latest security patches is crucial. Vulnerabilities are often fixed with each update, which could have helped prevent this breach.
- Encryption of Sensitive Data: Encrypting sensitive data would have made it harder for hackers to use the stolen information. Even if they managed to access it, it would be less useful without the encryption key.
- Stronger Authentication: Implementing stronger access controls, like multi-factor authentication (MFA), would have made it much harder for unauthorized users to gain access to critical systems.
5. Dell Data Breaches
Impact: 49 million (first breach) and 10,000 (second breach)
Dell, a tech giant, was hit by two significant data breaches in 2024. The first breach, discovered in May, exposed 49 million customer records spanning from 2017 to 2024. While financial information and personal identifiers like social security numbers were not involved, the breach compromised sensitive customer details such as home addresses and purchase histories.
The second breach occurred in September, with hackers extracting 3.5GB of employee data. Though the number of affected individuals was smaller, with just 10,000 employees impacted, the stolen data was highly valuable for phishing attacks. Details included employee phone numbers, social security numbers, employee IDs, and their work status. The data also extended to partners, not just Dell employees.
How It Could Have Been Prevented
Preventing future breaches requires a sharp focus on training employees to identify phishing attempts and social engineering attacks. It’s equally critical to keep systems secure by promptly patching vulnerabilities in widely used platforms like Atlassian. Adding multi-factor authentication for VPNs strengthens defenses, while enforcing least-privilege access ensures that no one has unnecessary access. By actively monitoring network activity for anomalies, businesses can detect threats early and reduce the impact of data breaches.
6. Evolve Bank Data Breach
Impact: 7.6 million individuals
In May 2024, Evolve Bank, a banking-as-a-service provider, fell victim to a devastating ransomware attack, which was later disclosed in July. The attackers infiltrated the bank’s network, exfiltrated sensitive data, and then threatened to sell it. When Evolve refused to comply with the ransom demands, the cybercriminals followed through and exposed millions of accounts. However, the attackers did not directly target customer funds, which is a common feature of ransomware attacks in 2024.
The exposed data included sensitive personal information, such as social security numbers, financial account details, and postal addresses. This breach, attributed to the notorious LockBit group, once again demonstrated the growing sophistication of cyberattacks in the financial sector.
How Could It Have Been Prevented
To prevent the such breaches, strengthening insider threat management through employee monitoring and vetting is crucial. Regular security audits, penetration testing, and continuous network monitoring could have detected unusual activities early. Additionally, hardening VPNs and cloud infrastructure, along with implementing a Zero Trust security model, would limit lateral movement and access to sensitive data, making it harder for cybercriminals to succeed.
7. Infosys Data Breach
Impact: 6 million Individuals
Infosys McCammish Systems, an outsourcing giant, revealed a major data breach, affecting around 6 million individuals. The breach occurred between October and November 2023, but there was a significant delay in detection.
The breach exposed critical data from several financial and insurance partners, including Wells Fargo and the Teachers Insurance and Annuity Association of America (TIAA).
Sensitive data compromised included SSNs, birth dates, medical treatments, email passwords, state IDs, and driver’s license numbers, posing a serious risk for identity theft.
The LockBit group, a Russia-linked ransomware gang, was behind the attack, using ransomware to lock over 2,000 devices across the Infosys network.
How Could It Have Been Prevented
- Stronger Endpoint Protection: Infosys should have implemented more robust endpoint security measures, preventing ransomware from infiltrating and locking devices.
- Faster Incident Detection: Faster detection mechanisms and continuous network monitoring would have helped identify and stop the breach earlier, minimizing the impact.
- Regular Security Audits: Conducting more frequent vulnerability assessments and audits would have enabled the company to identify weaknesses in their infrastructure and patch them before the breach.
- Data Encryption: Encrypting sensitive data, especially insurance-related information, would have limited the damage from the exposed records, even if attackers gained access to the system.
8. Patelco Credit Union Data Breach
Impact: 1 million individuals records breached
In June 2024, Patelco Credit Union, a well-established financial institution in the Bay Area, suffered a significant data breach. The attack exposed the personal and financial information of over 1 million individuals, with over 1 million records possibly compromised. Data like names, addresses, Social Security numbers, and financial account details were among the stolen information.
The breach happened after attackers infiltrated Patelco’s network in late May and gained access to critical databases by June. The attack was followed by a ransomware event that crippled the organization’s online banking, mobile app, and customer service systems. This caused major disruption, leaving many customers unable to access their accounts for nearly two weeks.
Patelco did not identify the attackers, but the ransomware group RansomHub has been linked to the breach. They have listed Patelco on their dark web marketplace, suggesting they might have been responsible for the attack.
How It Could Have Been Prevented
- Ransomware Detection Tools: Advanced tools designed to detect ransomware earlier in the attack chain could have stopped the hackers from spreading the malware through the network.
- Network Segmentation: Isolating sensitive data within different network segments would have limited access for the attackers, making it harder for them to steal large amounts of information.
- Regular Security Reviews: Conducting regular security assessments could have identified weaknesses in the system and helped the team patch them before they were exploited.
- Reliable Backup Systems: Ensuring robust backup systems, with secure off-site storage, could have helped the organization recover swiftly without paying the ransom.
9. Young Consulting Data Breach
Impact: 950,000 Individuals
In August 2024, Young Consulting, a financial software company, revealed that it had suffered a massive data breach earlier in the year. The breach affected nearly a million records, with sensitive data tied to its client, Blue Shield Insurance, being exposed.
The attack took place between April 10 and 13, 2024. During this period, attackers were able to access Young Consulting’s network with relative ease. They made off with a significant amount of data, including health-related information protected under HIPAA regulations.
After the breach, the attackers attempted to extort Young Consulting, but their efforts failed. Instead, the criminals made the stolen data available on the Dark Web for anyone to access.
How Could It Have Been Prevented
- Stronger Network Monitoring: By implementing more rigorous monitoring, Young Consulting could have detected suspicious activity sooner, potentially stopping the attackers before they accessed sensitive data.
- Improved Endpoint Security: Better endpoint protection would have helped prevent the malware from infiltrating their systems in the first place.
- Zero Trust Security: Adopting a Zero Trust model could have minimized the attackers’ ability to move freely across the network once they gained initial access.
- Regular Security Audits: Conducting more frequent audits and penetration testing would have helped identify and fix vulnerabilities before the attackers exploited them.
10. Community Clinic of Maui Data Breach
Impact: 123,000 individuals
In 2024, the Community Clinic of Maui (Mālama) experienced a significant cybersecurity incident, impacting around 123,000 individuals. The breach occurred over several days between May 4 and May 7, when ransomware actors infiltrated the Clinic’s systems. This attack brought down the Clinic’s operations, forcing it to close for two weeks. After reopening, staff had to rely on paper charts, while digital systems remained compromised for months as they worked to restore and secure the data.
The stolen data included personal information such as social security numbers, passport numbers, names, and sensitive medical histories. Financial details, including CVVs, were also exposed. The breach not only put individuals’ privacy at risk but also disrupted essential healthcare services.
The LockBit group, a known ransomware-as-a-service group, claimed responsibility for the attack. They targeted the Clinic’s cloud systems, extracting valuable data. The breach highlights the vulnerabilities in healthcare sector cybersecurity and the need for stronger protection of patient information.
How It Could Have Been Prevented
- Employee Awareness: Providing ongoing training to all employees on security protocols and recognizing suspicious activity could have stopped the attack before it gained momentum.
- Stronger Access Control: Implementing stricter user access policies and multi-factor authentication could have prevented unauthorized access to critical systems.
- Regular Security Audits: Conducting thorough, routine security audits would have identified weaknesses in the Clinic’s systems before the attackers could exploit them.
- Encrypted Data: Encrypting sensitive data at every stage, whether at rest or in transit, would have made stolen information much harder to use.
How CloudDefense.AI Could Have Prevented These Threats?
In 2024, we’ve seen a massive increase in high-profile cyberattacks, with breaches affecting millions of people and damaging businesses worldwide. Internet Archive, TeamViewer, Dell—these are just some of the major players who’ve been targeted this year. These breaches have proven that traditional security measures aren’t enough anymore.
Hackers are more organized, and their tactics are constantly improving. If your cloud and application environments aren’t fully secured, you’re vulnerable.
But there is hope. CloudDefense.AI is here to change the game.
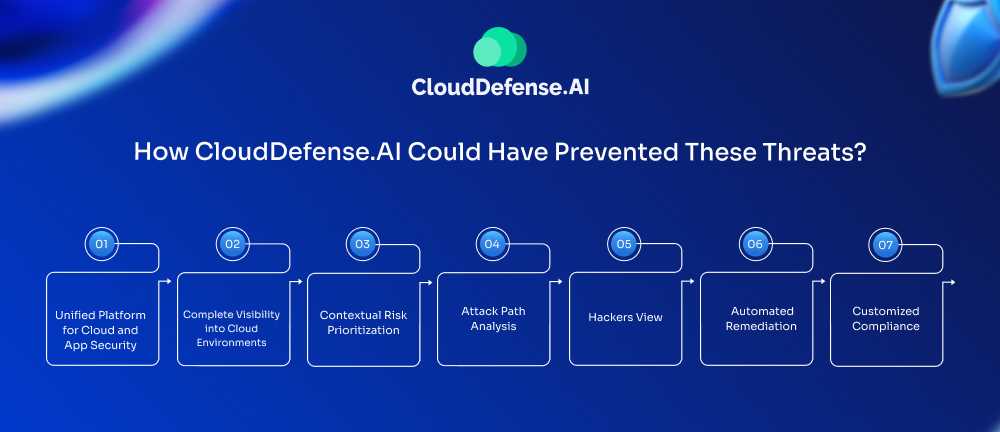
We provide a next-generation solution through our Cloud Native Application Protection Platform (CNAPP), offering the most advanced tools to prevent such devastating attacks before they happen. Here’s how CloudDefense.AI could have stopped these breaches:
Unified Platform for Cloud and App Security
At CloudDefense.AI, we combine cloud security and application security through our Cloud Native Application Protection Platform (CNAPP). This means you don’t need to rely on separate tools or systems—everything you need to protect your cloud infrastructure and applications is integrated. Our CNAPP provides ongoing protection, ensuring that your environment, from cloud infrastructure to the apps running on it, stays secure. It’s simple, efficient, and effective—one platform to keep your entire system safe.
Complete Visibility into Cloud Environments
The first line of defense against any attack is complete visibility. CloudDefense.AI ensures that organizations have a full view of their cloud infrastructure, applications, and data. No more blind spots. No more surprises. With real-time insights, businesses can quickly identify vulnerabilities—whether it’s misconfigured cloud services, unsecured storage, or exposed APIs—before attackers have the chance to exploit them.
Contextual Risk Prioritization
The biggest challenge organizations face is understanding which risks matter most. In the case of breaches like those at Snowflake and Dell, attackers exploited weaknesses that could have been prioritized and remediated with better risk management. CloudDefense.AI’s contextual risk prioritization ensures that vulnerabilities are addressed based on their potential impact, helping organizations focus on the threats that matter most and prevent exploitations before they escalate.
Attack Path Analysis
Attackers don’t just breach systems—they find their way in through various paths. CloudDefense.AI offers attack path analysis, providing organizations with a hacker’s view of their infrastructure. This helps identify all potential entry points into the system, allowing security teams to close those gaps before the attackers can exploit them. Whether it’s lateral movement or external entry, this feature ensures you’re always ahead of the game.
Hacker’s View
We simulate a hacker’s perspective, so you don’t have to wait for an actual breach to see how attackers could get in. By understanding how attackers might navigate your environment, CloudDefense.AI helps you proactively defend against the very techniques used in breaches like TeamViewer and AT&T. This proactive approach can block threats before they even appear on your radar.
Automated Remediation
Speed is crucial when it comes to responding to attacks. CloudDefense.AI’s automated remediation ensures that vulnerabilities are addressed swiftly—whether it’s patching an application vulnerability or securing a cloud misconfiguration. With automated workflows, businesses can secure their environments without delay, reducing the window of opportunity for hackers to strike.
Customized Compliance
Compliance is more than a requirement—it’s a layer of security. CloudDefense.AI ensures your organization stays compliant with the latest security regulations, providing tailored solutions that meet the specific needs of your cloud and app environment. By staying on top of compliance, you reduce your risk of breaches that stem from missing or outdated security protocols.
Wrapping Up!
The cyber threats we’ve seen in 2024 are only the beginning. Attacks are becoming more sophisticated, targeting organizations just like yours. The question isn’t if you’ll be attacked, but when—and whether or not you’ll be prepared. CloudDefense.AI offers a comprehensive, proactive solution to secure both your cloud infrastructure and applications, keeping your business safe from the growing number of cyber threats.
Take action now before your company becomes the next headline. Book a free demo today and see for yourself how CloudDefense.AI can protect your organization from the dangers lurking in the digital world. It’s time to secure your future.







