In 2025, the Open Web Application Security Project (OWASP) released its updated list of the OWASP API Security Top 10 Vulnerabilities. As APIs continue to be the heart of modern web applications, ensuring their security has become a priority. The updated list highlights the most significant risks and threats that organizations need to address to protect their APIs from exploitation.
What is API Security?
API security involves protecting APIs from vulnerabilities and attacks, ensuring secure data exchange between applications. With APIs serving as critical connectors for sharing sensitive data, they have become prime targets for hackers.
Modern API security goes beyond basic username-password authentication, employing advanced measures like security tokens, API gateways, and multi-factor authentication (MFA) to safeguard against threats.
By regularly monitoring and testing APIs, organizations can identify vulnerabilities and apply best practices to mitigate risks. As APIs drive web-based interactions, robust API security is essential to prevent breaches and maintain application integrity.
Now, let’s take a look at all the OWASP top API security risks;
OWASP API Security Top 10 Vulnerabilities
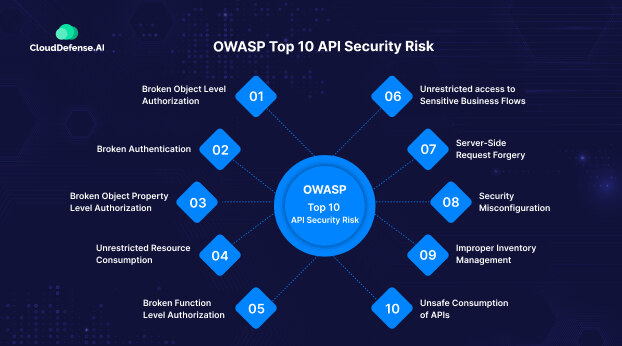
Here is the OWASP API security top 10 risks list that showcases all the high-priority threats that you should be aware of during 2025:
API 01:2023 – Broken Object Level Authorization
Broken Object Level Authorization (BOLA) occurs when an API fails to enforce adequate permission checks on object identifiers. This allows attackers to manipulate object references and access unauthorized data or perform actions on resources they shouldn’t have access to.
How It Works:
An attacker can modify an object identifier in an API request—such as a user ID or resource ID—to point to a different resource. If the API doesn’t verify the user’s permissions for the requested resource, the attacker gains unauthorized access.
For example:
- A legitimate API request to retrieve user data might look like this:
GET /api/user/123/profile - An attacker replaces the ID with another user’s ID:
GET /api/user/456/profile
If the API doesn’t check whether the requester is authorized to access user 456, the attacker can view or manipulate sensitive information.
Example Scenario:
Imagine an e-commerce platform where users can retrieve order details via: GET/api/order/{order_id}
- A logged-in user requests GET /api/order/101 to view their order.
- The attacker changes it to GET /api/order/102, trying to access another customer’s details.
- If the API doesn’t enforce authorization checks, the attacker gains access to private information such as billing details or shipping addresses.
Prevention Strategies for BOLA:
To secure APIs against BOLA vulnerabilities, organizations should adopt the following measures:
- Enforce Authorization: Ensure every API endpoint verifies user permissions for accessing or modifying resources.
- Use Server-Side IDs: Rely on session-based IDs instead of client-provided ones to maintain secure access control.
- Secure Object References: Replace guessable IDs with random, unique identifiers like UUIDs to prevent enumeration attacks.
- Apply Role-Based Access: Use role-based controls to limit resource access based on user roles, such as admin or customer.
- Test for Vulnerabilities: Regularly test APIs for authorization flaws using automated tools and manual reviews.
- Monitor API Activity: Log and review API usage to detect unusual patterns, like sequential ID access attempts.
API 02:2023 – Broken Authentication
OWASP lists broken authentication as a critical API security risk due to improperly implemented authentication mechanisms. These flaws allow attackers to exploit authentication tokens, steal credentials, or impersonate users to gain unauthorized access to sensitive data. Poor authentication practices destabilize overall system security and can lead to significant breaches.
How It Works:
- Unsecured APIs are mistakenly considered “internal.”
- Weak or unrotated API keys.
- Poor password practices: plain text, weak hashing, or default passwords.
- Susceptibility to brute force and credential stuffing attacks.
- Credentials or keys included in URLs.
- Lack of validation for access tokens and JWTs (e.g., unsigned or non-expiring JWTs).
Prevention Strategies for Broken Authentication:
- Secure All Authentication Methods: Ensure every API authentication process, including password reset and one-time links, is protected against vulnerabilities.
- Adopt Standardized Token Practices: Use industry-standard techniques for generating and storing authentication tokens and passwords to prevent exploitation.
- Enforce Multi-Factor Authentication (MFA): Add an extra layer of security by requiring multiple verification steps for user authentication.
- Use Short-Lived Access Tokens: Minimize risk by implementing tokens with limited lifespans, reducing their utility if compromised.
- Validate Access Tokens Properly: Strictly validate tokens, including thorough checks on JWTs for expiration, signatures, and structure.
- Implement Rate Limiting and Lockout Policies: Protect against brute force and credential stuffing by limiting login attempts, locking accounts after repeated failures, and enforcing strong password rules.
API 03:2023 – Broken Object Property Level Authorization
Broken Object Property Level Authorization occurs when APIs fail to validate user permissions for specific object properties, leading to unauthorized access and exploitation. This issue often manifests in two ways: excessive data exposure, where APIs reveal more data than necessary, and mass assignment, where APIs inadvertently accept and process unauthorized data.
How It Works:
APIs may return entire data objects from backend databases, trusting the client-side application to filter sensitive information. An attacker can bypass the client-side filter, directly access the API, and retrieve sensitive data. Similarly, APIs that automatically bind incoming data to internal objects without validation allow attackers to exploit hidden or unauthorized fields by crafting malicious payloads.
Prevention Strategies for Broken Object Property Level Authorization
Restrict Data Exposure:
- Avoid relying on client-side filtering; limit API responses to necessary data.
- Review and carefully define response schemas, including for error messages.
- Identify and justify the use of sensitive data with robust governance processes.
Prevent Mass Assignment:
- Avoid automatic data binding; explicitly define acceptable parameters and payloads.
- Use schema properties like readOnly for fields that should not be modified.
- Validate schemas, types, and patterns during design and enforce them at runtime.
API 04:2023 – Unrestricted Resource Consumption
APIs require significant resources, including CPU, memory, storage, and network bandwidth, to handle requests efficiently. Attackers often exploit APIs by causing resource overuse, leading to denial of service (DoS), service downtime, and inflated operational costs. This risk intensifies when APIs are not protected against excessive calls or large payload sizes, making them vulnerable to brute force or overload attacks.
How It Works:
Attackers flood an API with an excessive number of requests, surpassing its processing capacity. Alternatively, they send requests with oversized payloads or overly complex queries, causing server bottlenecks. These attacks can slow down or crash the service, disrupt legitimate users, and significantly increase resource costs.
Prevention Strategies for Unrestricted Resource Consumption
Implement Rate Limiting:
- Apply rate-limiting policies to all endpoints, especially authentication-related ones.
- Customize limits based on API methods, clients, or user roles.
- Use tokens or fingerprints to limit rates instead of relying solely on IP addresses.
Control Resource Usage:
- Restrict payload sizes and query complexity to prevent overloading.
- Limit pagination sizes and data retrieval amounts.
- Set CPU and memory usage caps for compute resources.
Use External Protections:
- Use DDoS protection services from cloud providers to mitigate large-scale attacks.
API 05:2023 – Broken Function Level Authorization
Broken Function Level Authorization is a critical API security risk identified by OWASP. It arises when API endpoints lack proper authorization checks, particularly for administrative functions. Poor segregation between regular and admin-level APIs or overly complex access control policies make APIs vulnerable to unauthorized access. Attackers can exploit these weaknesses to perform sensitive actions, such as modifying or deleting data, without proper permissions.
How It Works:
- Administrative functions are exposed as public APIs.
- Non-privileged users access sensitive operations by altering parameters or URLs.
- Unauthorized users invoke hidden admin APIs.
Prevention Strategies for Broken Function Level Authorization
- Deny by Default: Block all access unless explicitly authorized.
- Role-Based Access Control (RBAC): Limit API access based on user roles.
- Separate Admin APIs: Isolate administrative functions from user APIs.
- Enforce Authorization Checks: Validate all API requests on the server side.
- Audit and Test: Regularly review and test access control mechanisms.
API 06:2023 – Unrestricted access to Sensitive Business Flows
Unrestricted Access to Sensitive Business Flows occurs when APIs expose business-critical functions, which attackers can abuse through automation. This can lead to significant harm, such as data exfiltration or market manipulation, without the need for a specific implementation bug.
How It Works:
- Automated bulk purchasing on e-commerce sites to resell products.
- Scraping real-estate price data for competitive advantage.
- Speeding up actions on auction sites using bots to gain an unfair advantage.
Prevention Strategies for Unrestricted access to Sensitive Business Flows
- Identify Sensitive Flows: Recognize and protect critical business functions with additional security layers.
- Authentication: Implement strong authentication methods, like OAuth flows, for sensitive APIs.
- Rate Limiting: Apply robust rate-limiting to control excessive API usage.
- Monitor Access: Track API usage, blocking suspicious devices or IPs.
- Human Detection: Use CAPTCHA or similar techniques to identify and block automated access.
API 07:2023 – Server-Side Request Forgery
Server-side request Forgery (SSRF) occurs when an API makes requests to remote resources via user-supplied URLs without validation, allowing attackers to send crafted requests to unauthorized destinations.
How It Works:
- API redirects to a malicious site to steal sensitive data.
- Attackers force the API to fetch resources from their server, enabling attacks like key injection in JWTs.
- Local resources are accessed via malformed requests, exploiting the local network.
Prevention Strategies for Server-Side Request Forgery
- Schema Validation: Define and enforce strict schemas and patterns for acceptable request URLs at design and runtime.
- Block Redirects: Prevent the API from following HTTP redirects to avoid redirection to malicious sites.
- Allowlist URLs: Use an allowlist to restrict the destinations for outbound requests.
- URL Restrictions: Limit allowed URL schemes, ports, and protocols to minimize exposure.
- Sanitization: Ensure the resource-fetching library is standard and URLs are sanitized to block access to internal resources.
API 08:2023 – Security Misconfiguration
Security misconfiguration is a prevalent API vulnerability caused by improper setup of API stacks, often resulting from neglecting best practices or misconfigured permissions. Attackers exploit these gaps to breach systems, steal data, or abuse functionality. Regular security updates and effective configuration management can mitigate these risks.
How It Works:
- Unpatched Systems: APIs running on outdated frameworks or libraries, making them susceptible to known exploits.
- Exposed Admin Interfaces: Attackers discover admin panels or management consoles left publicly accessible without authentication.
- Improper TLS Setup: APIs using outdated TLS versions (e.g., TLS 1.0) or weak cipher suites, exposing communication to interception.
- Missing Security Headers: Lack of critical headers such as Content-Security-Policy or X-Frame-Options makes APIs prone to attacks like clickjacking or injection.
- Leaky Error Messages: API error responses include stack traces or sensitive debug information, aiding attackers in reconnaissance.
- Enabled Debugging Tools: Leaving developer debugging tools active in production environments allowing attackers to access sensitive data or test configurations.
Prevention Strategies for Security Misconfiguration
- Automate Hardening and Updates: Use automated processes to patch and harden the API stack, including libraries and containers.
- Regular Endpoint Testing: Continuously test endpoints for misconfigurations, such as improper TLS versions or unsupported HTTP methods.
- Disable Unnecessary Features: Remove or deactivate services that are not critical for functionality.
- Restrict Admin Access: Limit administrative privileges to essential users only.
- Secure Error Outputs: Define error outputs to avoid exposing stack traces or sensitive details.
- Enforce Security Policies: Apply robust security headers and comprehensive CORS policies to ensure secure communication.
API 09:2023 – Improper Inventory Management
Improper API inventory management occurs when organizations fail to document and regularly update their API endpoints. With multiple APIs across diverse environments, outdated or undocumented endpoints expand the attack surface. Attackers often exploit unprotected non-production APIs or legacy versions, gaining unauthorized access to sensitive data.
How It Works:
- APIs in staging or testing environments need proper security controls.
- Deprecated APIs remain active for backward compatibility, making them vulnerable.
- Non-production APIs share access to production data, enabling pivot attacks.
- Poor visibility across environments leads to security gaps.
Prevention Strategies for Improper Inventory Management
- Inventory Management: Maintain an updated record of all APIs and their environments.
- Access Control: Limit access to non-production APIs and segregate production data.
- Enhanced Security: Use API gateway firewalls and enforce strict CORS policies.
- Version Retirement: Promptly retire old APIs or secure them with backported fixes.
- Authentication and Monitoring: Enforce authentication and actively monitor API activity to spot anomalies.
API 10:2023 – Unsafe Consumption of APIs
Unsafe consumption of APIs occurs when web applications trust and process data from external APIs without proper validation. Developers often overlook security standards for third-party APIs, assuming their integrity. This creates vulnerabilities that attackers exploit, such as SQL injection, deserialization, and entity injection, leading to sensitive data breaches.
How It Works:
- Data Governance Risks: Upstream APIs unintentionally store sensitive data, violating consumer policies.
- Compromised APIs: Attacked upstream APIs pass malicious data to consumers, exposing them to vulnerabilities.
Prevention Strategies for Unsafe Consumption of APIs
- Validate Upstream Data: Apply strict filtering and sanitization to all external API data.
- Enforce API Contracts: Use runtime mechanisms to validate upstream API compliance with defined contracts.
- Supply Chain Verification: Treat upstream APIs as part of your supply chain, auditing their security practices.
- Secure Communication: Always use encrypted channels to minimize data interception risks.
Conclusion
The OWASP API Security Top 10 Vulnerability list provides an overview of the highly critical API security risks and vulnerabilities that all organizations should be aware of. This list is highly vital for developing and maintaining APIs.
By monitoring these risks, organizations can quickly identify potential weaknesses in their APIs and enhance the overall security posture of their applications. This list was made after careful research by top security teams and organizations, so all organizations make these risks a high priority.







